Back to blog
All about biometric authentication
Auth & identity
Feb 15, 2023
Author: Stytch Team

It wasn't too long ago that biometric authentication was the stuff of science fiction and spy films. When Back to the Future Part II premiered, paying for a cab ride with a fingerprint in 2015 seemed nearly unimaginable. But from where we’re standing in 2023, that future is just about here.

Biff, Marty McFly's nemesis across time-space, pays for a taxi ride using his fingerprint in Back to the Future Part II.
Today, biometric authentication has become a part of daily life for just about anyone with a smartphone. Unsurprisingly though, it works a little differently from how it appears in films or TV.
In this blog post, we'll take a deep dive on biometric authentication, including:
- What it is and how it came about
- Types of biometric authentication
- FIDO and the future of biometric adoption
- How it works
- Advantages and challenges compared to other authentication methods
Biometrics: definition and history
A biometric (also called biometric identification) refers to a set of physical or behavioral traits that can be used to uniquely identify a person.
In the world of authentication, a biometric authentication method refers to the process of using someone's biometric information to identify and grant (or deny) access to accounts and/or resources. Biometric authentication is considered a “what you are” form of ID (as opposed to what you have or what you know).
Note the key difference here: whereas biometrics in general are simply used to confirm someone's identity, biometric authentication specifically refers to confirming that identity for the purpose of accessing resources online. As Stytch is an authentication platform, we're most concerned with the latter.
Biometric authentication: a brief history
In the 20th century, scientists made major leaps and bounds with a variety of biometric identification factors, including iris patterns, hand geometry, and facial and voice recognition. Though the last century didn’t see widespread biometric adoption, it laid important groundwork for the momentum biometrics would gain in the new millennium. Some key events included:
- 1969: The FBI launched research into how to automate fingerprint scanning and verification, which until that time had been a laborious, manual process.
- 1976: The first prototype for a speaker / voice recognition system was developed by Texas Instruments.
- 1971: Hand geometry biometric identification was patented by Robert Miller at Stanford University.
- 1994: Iris recognition was developed and then patented by John Gustav Daugman at Cambridge.
- 1996: Hand geometry was used for admission to the Olympic Village at the Atlanta Summer Olympic games.
- 1997: The National Security Administration sponsored the Human Authentication Application Programming Interface (API) – the first standard for commercial biometric interoperability. This was a key step forward, and would help make widespread biometric adoption much more feasible.
While there have been incremental advances in biometric authentication adoption in the 21st century, perhaps the most significant milestone was 2013, in which Apple released Touch ID for the iPhone, marking the first integration of biometric authentication into a major commercial product.
Since then, biometric technology has rapidly accelerated. As of 2022, 80% of smartphones now have biometrics enabled.
Types of biometric identification methods
Biometric identification methods can generally be grouped into two categories: physical biometrics and behavioral biometrics.
Physical biometrics are what most people are familiar with in their day-to-day use, and consist of a computer gathering, storing, and comparing data relating to someone’s physical traits.
Behavioral biometrics relate to how a person behaves online, and typically deals with motor / manual actions on a computer like typing, mouse movement, etc.
Since physical biometrics are more common, we’ll start with those.
Fingerprints

A biometric fingerprint scan is used to get into one's home in Total Recall, a science fiction film.
Fingerprint biometrics are the most common form of biometric authentication today, in part because they were so widespread in identity and law enforcement before the internet.
Today, fingerprint biometric authentication relies on scanners to gather a person’s unique finger or thumbprint. While there are different types of scanners, they all rely on receiving a signal from someone’s finger that returns different values when it interacts with the ridges of the fingerprint and when it interacts with the valleys.
- Optical fingerprint scanners rely on bouncing light off of the finger.
- Capacitive fingerprint scanners discharge a very small electric charge onto the finger.
- Ultrasound fingerprint scanners rely on bouncing sonic waves off of the finger (much like ultrasounds in other medical uses).
- Thermal fingerprint scanners detect the temperature difference between the valleys and ridges.
Regardless of the type of scanner being used, once it receives the data points about the precise location of an individual's valleys and ridges, an algorithm is then used to translate that biometric data into a character string that is then stored either on the device that took the print (more common) or on a cloud or server (less common).
Importantly, the algorithm that encodes the fingerprint into a character string cannot be reverse-engineered to generate an image of the fingerprint.
Face

A thumbnail from the Bourne Identity movies, in which a face is matched using facial recognition technology.
Facial recognition is the next most common form of biometric authentication found on everyday devices today. Like other biometric authentication methods, facial recognition scanners take various measurements of the user's face to create a unique data set that is then compared against future scans.
While some facial recognition systems have been updated to detect liveness, many are still based on analyses of still images, rather than live scans of light, sound, or heat.
Hand geometry

A hand geometry scan as represented in the 2015 film Jurassic World
Hand geometry identification is composed of several measurements of different dimensions of the human hand, such as the length and width of each finger, the span of the hand at various cross sections, etc. Because hand geometries are not as unique as other biometrics like fingerprint, iris, or retina, they are not considered as secure.
For this reason, hand geometry is more often combined with other forms of identification and authentication (such as ID cards, etc.) rather than serving as the primary auth or identification factor.
Voice

In the Star Trek franchise, certain sensitive actions could only be performed once the captain's voice had been authenticated.
Voice biometric authentication analyzes the unique sound characteristics of a person’s voice, including duration, dynamics, intensity, and pitch. The uniqueness of these characteristics results from a combination of their own jaw and mouth movements, throat shape, vocal cords, etc.
Many biometric auth solutions are equipped with liveness detection capabilities, so they can distinguish between a real, live user and a mere reproduction or copy — like a photographic image or voice recording — in order to detect and prevent fraud.
Eyes

A thumbnail from the film Minority Report in which Tom Cruise performs an eye-based biometric authentication scan
While certainly less common in everyday devices, eye-based biometric scanners focus on highly unique biological characteristics that are near-impossible to fabricate – namely the retinas and irises.
Retina Scanners
Retina scanners might more accurately be called blood vessel scanners, since they’re actually mapping the network of blood vessels that feed into a person’s retina at the back of the eyeball. This blood vessel network is unique in every person, and is scanned by sending UV light into the back of someone’s eye and then registering the reflections of light sent back by the blood vessels.
While retina scanning probably sounds extreme for everyday uses, it is incredibly accurate. Retinal patterns are consistent throughout a person’s life, but certain diseases like glaucoma, diabetes, and a few select others can alter them.
Want to add passwordless auth to your app? Switch to Stytch.
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Iris Recognition
Iris patterns are also incredibly unique, but these scanners instead detect biometric data from the front of the eye to capture patterns on a person’s iris, including size, color, etc.
Unlike retina recognition, which bounces off UV light and registers the reflection, iris recognition and scanning is done with cameras (albeit UV cameras). This makes the technology required for successful iris recognition biometrics much less expensive and less complicated, and thus a bit easier to implement.
Behavioral Biometrics

Unlike physical biometrics, which are used to identify a single user, behavioral biometrics are more commonly used to distinguish fraudulent users (often bots) from human ones. While this is not the only way to mitigate malicious bot traffic, it can provide helpful signal because of the particular ways bots behave. Behavioral biometric factors include:
- Mouse activity and motion, including speed, movement patterns, scrolling behaviors. Bots tend to move multiple times faster than a human does.
- Keystrokes, including speed, use of shortcuts, and use of copy and paste functions, which bots tend to use instead of actually typing.
- Touchscreens, including the pressure and surface area that interacts with a touchscreen surface.
- Device being used, including gyroscopic movement of the device, orientation, etc. Bots don’t need the computer oriented or stable in any kind of way to operate (since they’re software-based) whereas humans have specific orientation needs for their device hardware.
What are the pros and cons of different biometric authentication methods?
At Stytch, we always believe the security provided by a given authentication method must always be measured against the amount of friction it introduces for users – what they trust, understand, are most familiar and comfortable with, etc.
This tradeoff often varies depending on a variety of factors, including the industry, user population, and product design. But really, the choice of biometric detection is often not up to the average app or product builder, but is instead a decision for hardware makers.
So if you’re building an iOS app, you’re already locked into the Face and TouchID biometrics Apple has built into their iPhone.
FIDO – popularizing biometric security
In addition to Apple's introduction of TouchID in 2013, the a group called Fast Identity Online, (or the FIDO alliance) has been instrumental in evangelizing biometric authentication systems and making them easier for companies to adopt and implement.
FIDO was originally formed in 2012 by a group of invested parties from across cybersecurity who united behind a simple goal: make the internet easier and more secure to navigate by developing a more intuitive, standardized approach to passwordless authentication.
Over the past decade, FIDO has made impressive strides in developing technical standards that improve on both security and usability. Two of the most well-known technical standards FIDO has advanced are WebAuthn and passkeys. If you’ve interacted with a web app that allows you to authenticate with on-device biometrics on your phone or a Yubikey, you’ve likely interacted with WebAuthn.
While spy thrillers often show biometric authentication being used as a primary authentication factor (think of using retinal scans to get into government buildings), in both WebAuthn and passkeys biometrics instead serve an intermediary function that safeguards access to login credentials or cryptographic key pairs. That combination is also referred to as device biometrics, on-device biometrics, or native biometrics.
It’s the combination of biometric data with public key cryptography that makes biometric authentication on one’s phone or computer so secure, and such a promising alternative to passwords.
But FIDO has recently taken device biometrics one step further. While WebAuthn solutions were historically limited to a specific device, passkeys improve on WebAuthn by leveraging a user's cloud account (e.g. iCloud) to securely log people in across devices and operating systems with biometrics. This means that a person's biometric data that's saved to their iPhone can be used to log them into an app on their MacBook, or even their PC.
Thanks to FIDO, the world of ubiquitous, secure biometrics just got a lot closer.
Because device biometrics are one of the more common implementation cases for biometric authentication today, it's worth breaking down what exactly is happening under the hood.
Let's take a look.
Device biometrics – a step-by-step guide
The first crucial component to device biometrics (besides the biometric reader itself) is public key cryptography, and how it's different from more basic cryptographic systems.
Basic cryptography
To understand public key cryptography, it’s helpful to have a basic understanding of cryptography as a whole. In cybersecurity, cryptography generally has four parts:
- Plain text message: the information being protected by encryption
- Cipher algorithm: the mathematical operation done to the plain text message to encrypt it. These algorithms are generally common and publicly known, and utilize keys in their operation.
- Cipher message: the result of encrypting the plain text message with the cipher algorithm.
- Key: This is the unique value or string used by the algorithm to encrypt or decrypt the cipher message.
To give an over-simplified example of how this works:
Let’s say you want to share the message “apple” with someone. “Apple” is your plain text message. You use the cipher algorithm of addition paired with the key of 4. In this case, “4” indicates the number of letters you move down the alphabet to create your cipher message. With this cryptographic process, “apple” would become “ettpi.” “ettpi” is then your cipher message.
In reality of course, both the keys and the algorithms are much more complex. Keys are usually randomly generated strings of letters and numbers, and the algorithms involve a bit more advanced mathematics than basic addition. But the main principle and roles as described above apply.
Now in order for this to work, both people and/or entities sending and receiving the encrypted message have to know both the cipher algorithm and the key. In cybersecurity, because the algorithms are more or less public knowledge, that makes the key an incredibly valuable piece of information. So the question of how keys are initially shared and then stored is a critical juncture in keeping data and accounts secure.
Enter public key cryptography.
Public key cryptography
Unlike basic cryptography in which the algorithm and key are shared between parties exchanging data, in public key cryptography each party possesses a different key – one to encrypt, and one to decrypt. Typically, the public key is used to encrypt the data, and the private key is used to decrypt it.
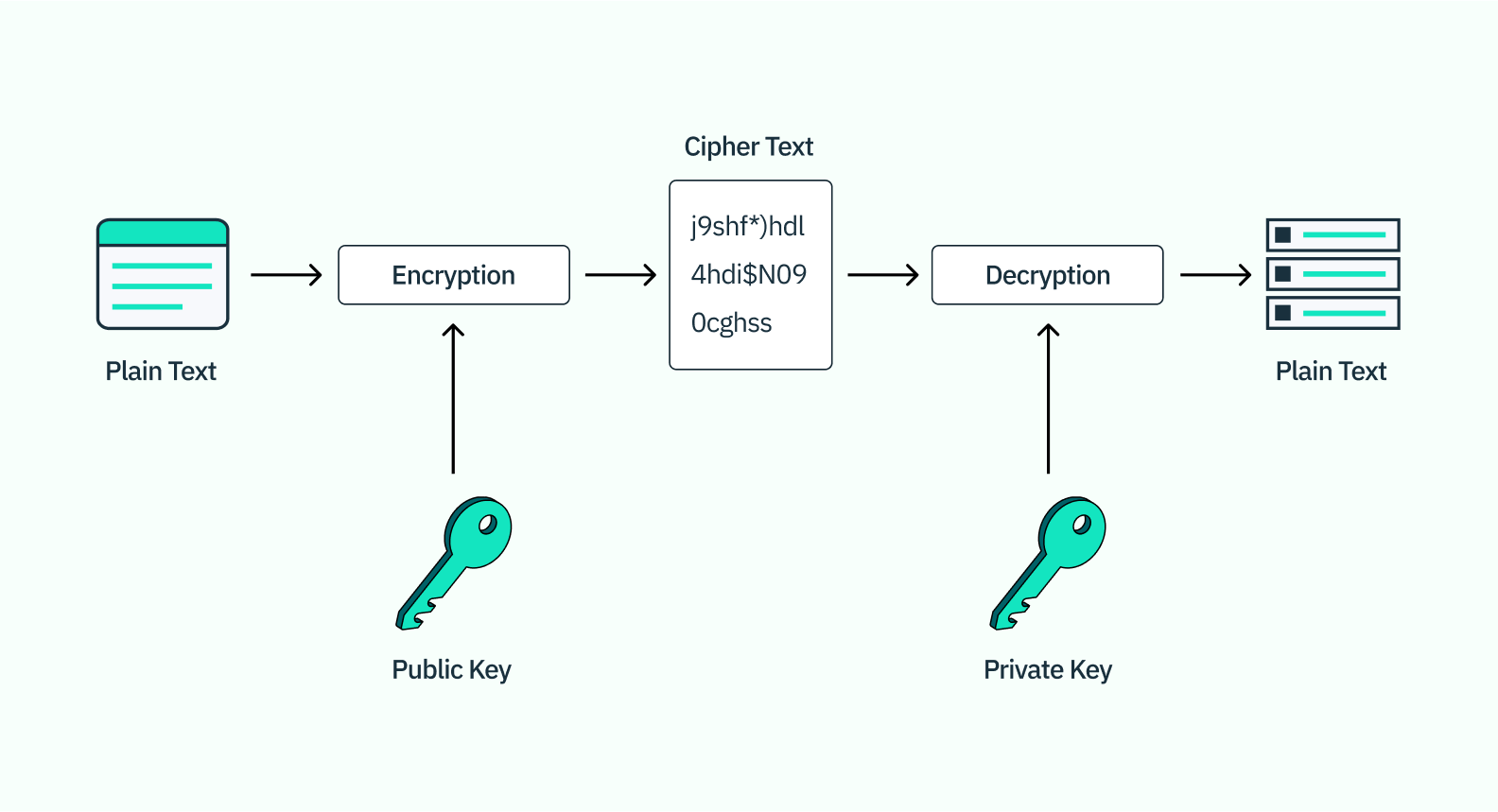
What makes this kind of cryptography more secure than regular cryptography is that while the public key is stored on the server (and thus fairly easy for others to access), the private key is stored either on the user’s device (like your iPhone) or on a hardware security module like a USB or biometric scanner. Because the keys are asymmetric and one of them is stored locally, this makes it much more challenging for hackers to access, thus helping prevent account takeovers.
Device biometrics – bringing it all together
Now that we have a good understanding of public key cryptography and biometric authentication factors, we can see how it all fits together on a day-to-day basis when we use biometric auth on our iPhones or Androids.
When you first sign up for an application or service, you may be asked if you want to use biometrics on your device, let’s say an iPhone, to log in. If you say yes, and have already saved your biometric information to your phone (be that a thumb print or a face scan), the following will happen:
Signing up with biometrics
- The app you want to access generates a key pair to be used throughout this sign-in process.
- That application notifies their authentication provider (let’s say Stytch) that you, the user, want to use biometric authentication, and register for a biometric key with Stytch. Stytch stores the public key, and sends a challenge for the device to solve with the private key to confirm ownership of the other half of the key pair.
- The app on your phone receives the challenge, solves it with the private key, and returns that puzzle answer (also sometimes called a signature) to confirm the registration process.
- After each party verifies each other, the private key registration is stored securely on your device (in the case of an iPhone, it’s stored in the Keychain), along with any other metadata that’s helpful when logging into the app.
- That’s a successful biometric authentication registration!
Logging in with biometrics
When it comes time to log into the app or service, that app or service will do the following:
- First, the app will check to make sure there’s a keypair registration on the device you’re using. Most authentication providers only allow one keypair per application per device.
- When the app asks the Keychain on your phone for the keypair, that’s when the system will ask for the biometric prompt.
- You provide your device with your biometric information, which prompts the device to unlock the keystore. Note at no point does the app have any access to your biometric data! This is only stored on your device, as a way to protect any credentials or keys stored locally.
- Just like they did with the signup flow, once you’ve unlocked your key data with your biometrics, the auth provider will use the public key that they have to create a challenge that can only be solved with the private key on your phone. The auth provider here does not have access to the private key, but they do know what the answer should be based on the public key.
- The challenge is solved using the private key on your phone, and that answer/signature is returned to the auth provider for verification.
- If the response matches what Stytch believes it should be, you are authenticated and officially logged in!
The main takeaway here is that biometric authentication is especially powerful in cybersecurity when paired with public key cryptography. This combination helps reduce friction and increase security all at once, without giving your biometric information to a single application.
What are the advantages and challenges of working with biometric authentication?
Advantages
The two main advantages of biometric authentication are security and ease of use.
Enhanced security
Because biometric authentication is based on a user’s unique characteristics, it cannot be lost, forgotten, or guessed. This makes it a more safe and secure authentication option vs password-based authentication, which is an increasingly insufficient means of protecting sensitive information. A
dditionally, biometric authentication offers best-in-class security by ensuring that a user demonstrates both possession of an original device and a unique biometric trait such as a Face ID or fingerprint.
Ease of use
Convenience and ease of use is the major advantage of biometric authentication. It’s much easier for users to glance at their phone or tap a sensor to unlock a device or log in to an app than it is for them to enter (and remember) a password or request a SMS passcode every time they want access. Biometric authentication reduces friction, which, in turn, can increase user conversion and retention.
Challenges
The biggest challenges with biometric authentication relate to spoofing,usability, and trust.
Spoofing
While much more secure than other forms of authentication, hackers are quickly developing ways to get past biometric authentication processes. They may use an authorized user’s photo, voice recording, fingerprint replica or other form of mimicry to trick a biometric reader into giving them access.
Fortunately, spoofing isn't possible with the device-tied nature of on-device biometrics. So for any developer building for FaceID, TouchID or other mobile applications, spoofing is not a concern.
And for that small cadre of developers who have non-on-device biometric authentication in mind, mapping users’ faces in 3D or requiring them to say a unique phrase at every login, for example, can help mitigate the risk of spoofing.
Usability
While the technology is improving every day, there are still some false rejections with biometric authentication that users may find frustrating. These can result from changes to users’ faces and voices as they age or due to circumstances such as mask-wearing, glasses, or lighting.
Biometric methods like facial recognition systems have also come under scrutiny in their confluence with artificial intelligence (AI) and law enforcement use cases, particularly for the ways their inaccuracies affect treatment of those who are underrepresented in AI's databases, particularly women and people of color.
Privacy & trust
Biometric data is highly sensitive, and people are understandably wary about it being stored in centralized databases or transmitted between systems susceptible to a breach. As of 2019, 25% of people surveyed said they did not trust biometrics, while 35% felt they didn’t have enough information. There are a few things companies can do to help build trust and protect privacy:
- Triple-check your security measures: This should go without saying, but biometric authentication is no different from other types: it’s very easy to do poorly, and hard to do well. If you’re going to be using biometric authentication information in your app, do due diligence and our partner with a third party (like Stytch!) to help manage your security risks.
- Transparency and education: Develop a highly secure and transparent plan for using and protecting biometric data. Explain how your technology works to your users, so they understand who has access to what, and all the ways in which they’re protected.
- Device biometrics: Because of some of the risks that can come with storing biometric information, it often makes more sense for app developers to use device-based biometrics (described above) for their purposes. Using Apple and Android biometric technologies allows them to avoid many liabilities, and device-based methods are becoming increasingly easy to implement.
Get started with biometric authentication
Stytch is leading the way in easy-to-implement authentication solutions that boost security and increase conversions. If you’re interested in integrating biometric authentication, check out our WebAuthn and Passkeys products, or check out our docs. Sign up for a free account to get started, or contact support@stytch.com to discuss all things auth.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.