StytchBlog
Latest
Auth & identity

Account Abuse Prevention in 2024
Latest
Auth & identity
April 9, 2024
Latest
Auth & identity
March 14, 2024
Session management best practices

Latest
Auth & identity
March 5, 2024
Managing user sessions: localStorage vs sessionStorage vs cookies
Latest
Auth & identity
March 5, 2024
Unpacking MACH architecture: The future of SaaS development
Company
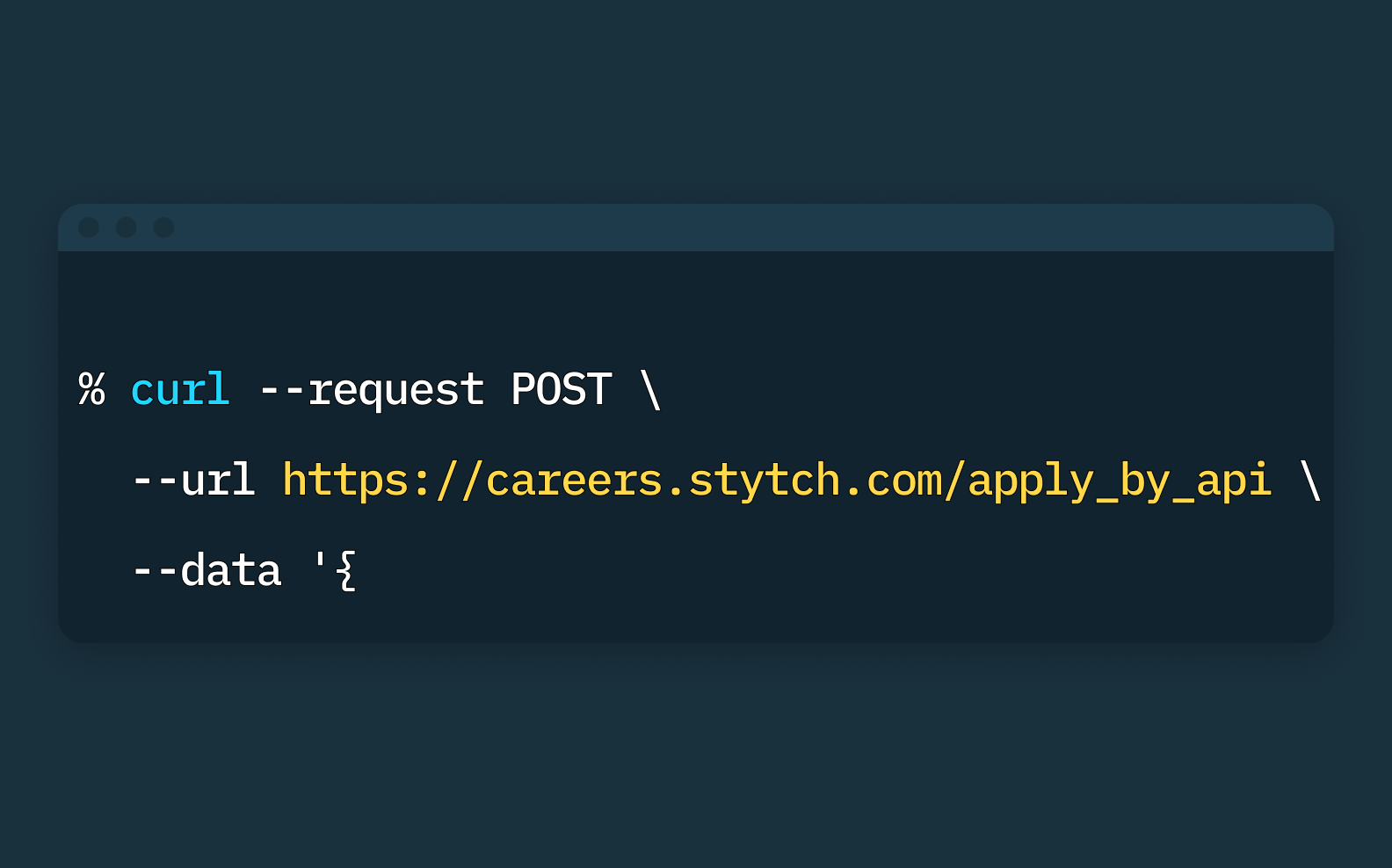
Apply by API: Making job applications developer-focused
Latest
Company
Engineering
December 29, 2023

Latest
Company
September 27, 2023
So you want to write an Engineering career ladder?
Latest
Company
September 1, 2023
Our approach to developer-focused conferences

Latest
Company
June 23, 2023
Stytch events with Orb: securing and pricing AI products
Engineering
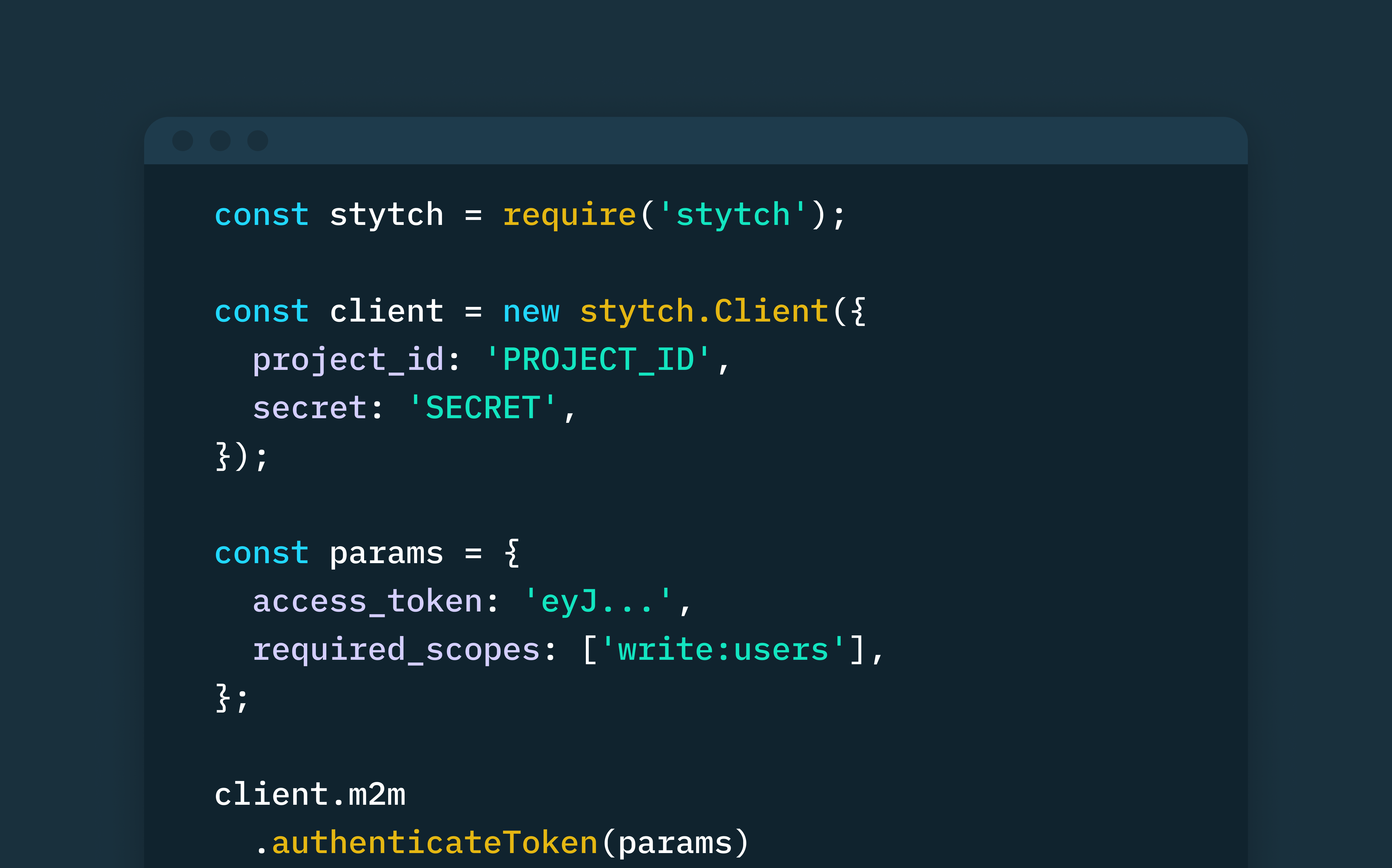
How to securely implement M2M authentication and authorization in Node.js using Stytch
Latest
Auth & identity
Engineering
January 12, 2024

Latest
Company
Engineering
December 29, 2023
Apply by API: Making job applications developer-focused
Latest
Auth & identity
Engineering
December 26, 2023
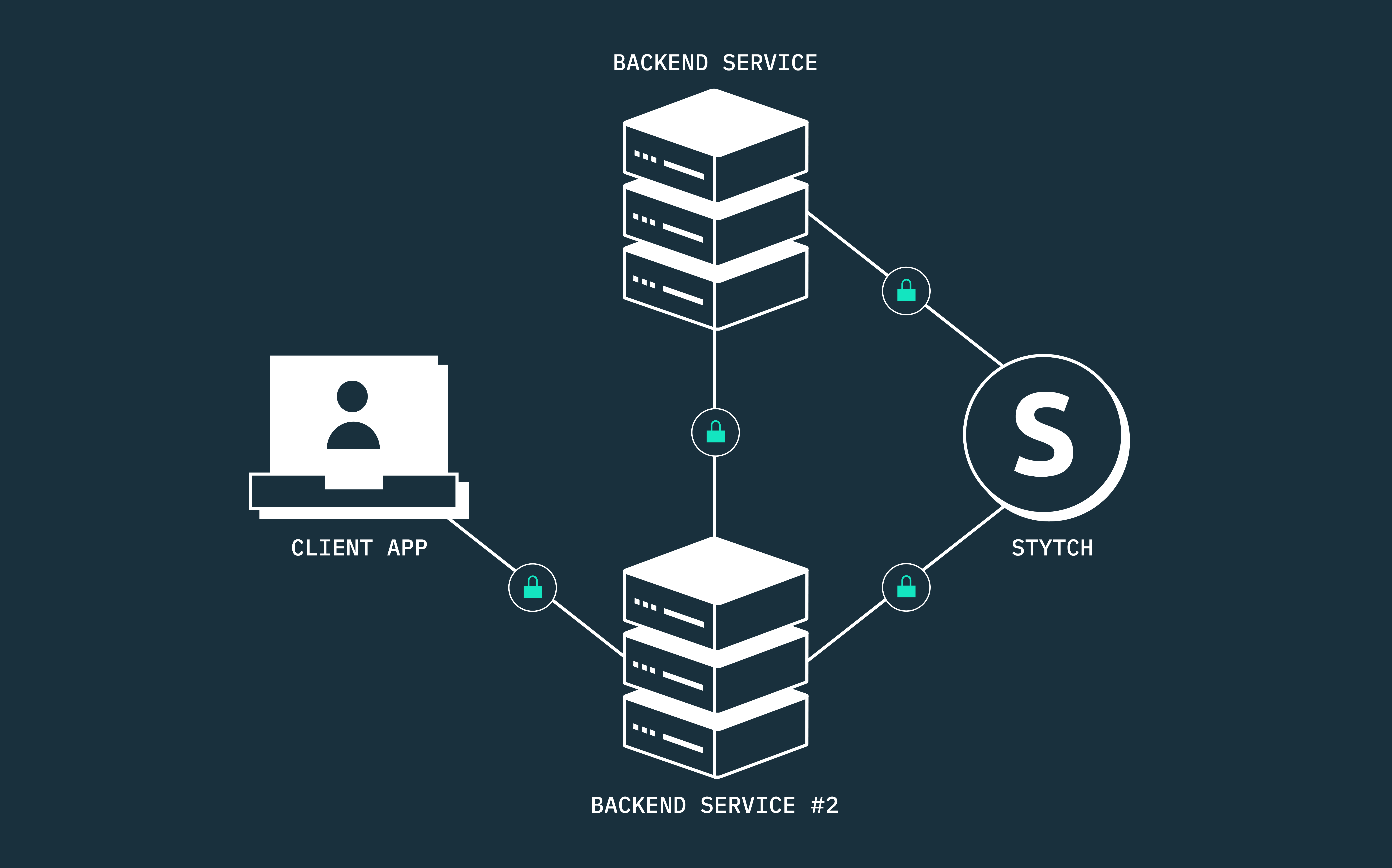
The complete guide to machine-to-machine (M2M) authentication and authorization
Latest
Engineering
December 21, 2023
Optimizing DBs at scale: how we reduced writes by 1000x for one of our most accessed tables
Product
Why Switch to Stytch?
Latest
Product
April 11, 2024
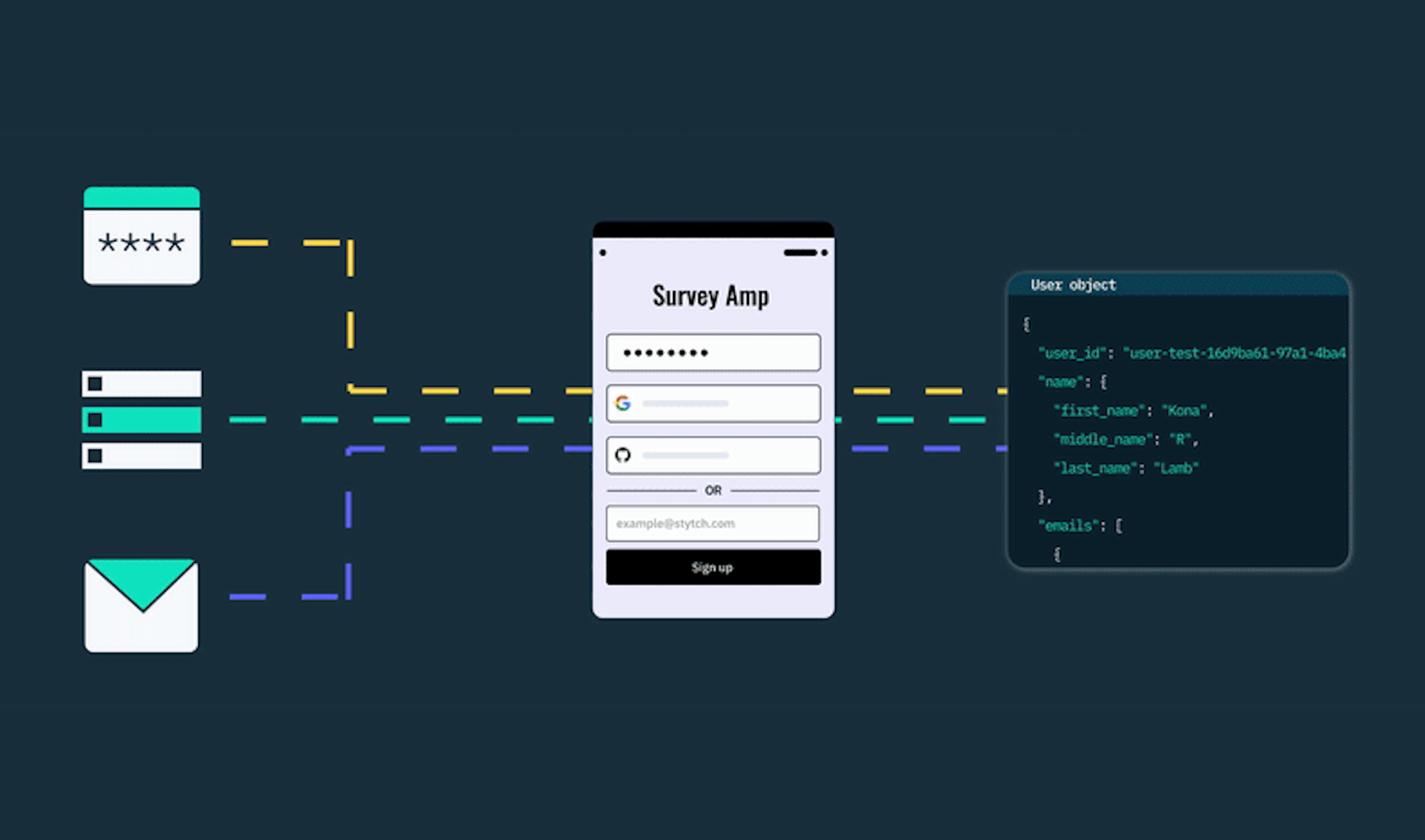
Latest
Product
April 11, 2024
Out-of-the-box: User linking and provider failover with Stytch
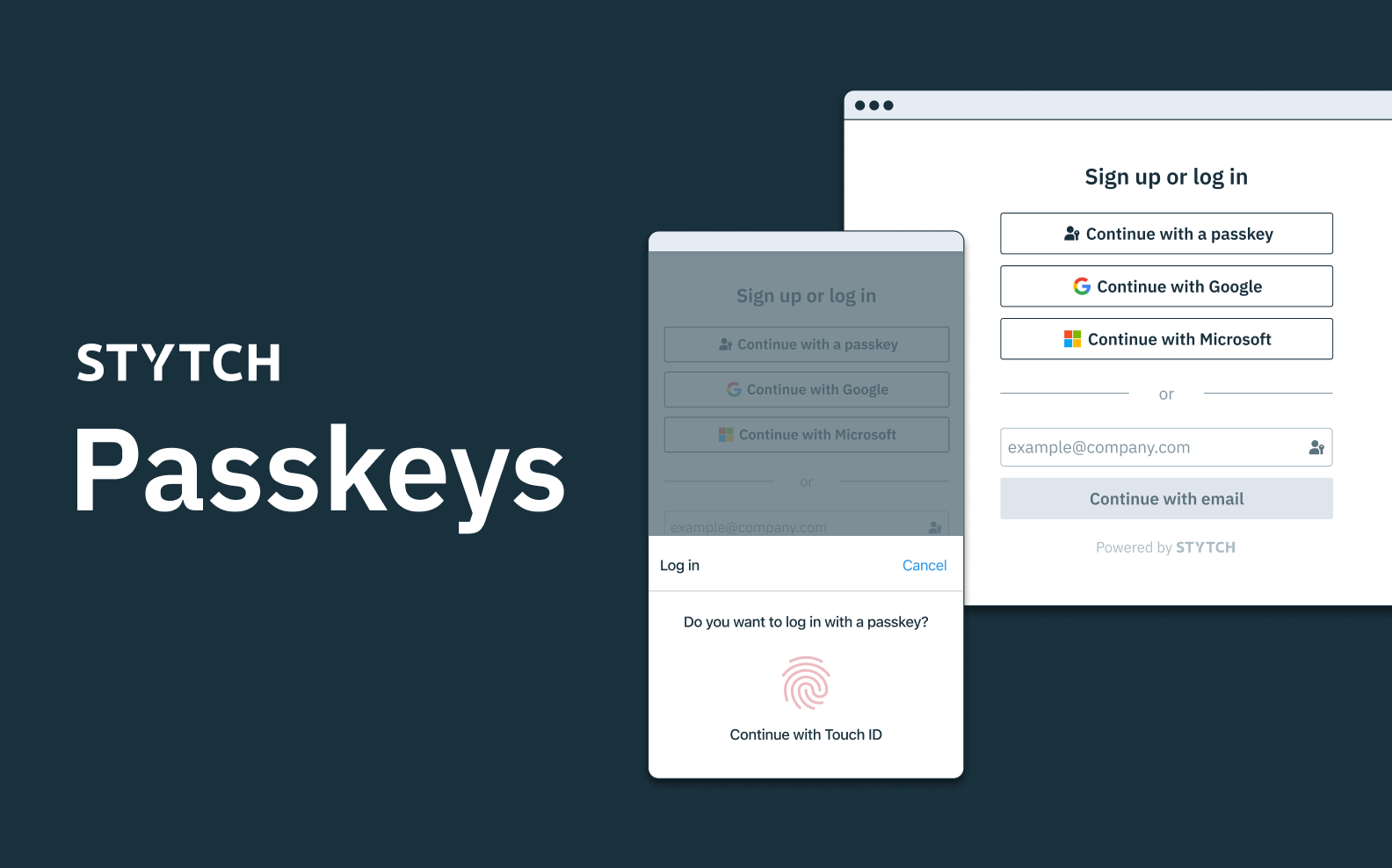
Latest
Auth & identity
Product
December 5, 2023
Introducing Passkeys authentication
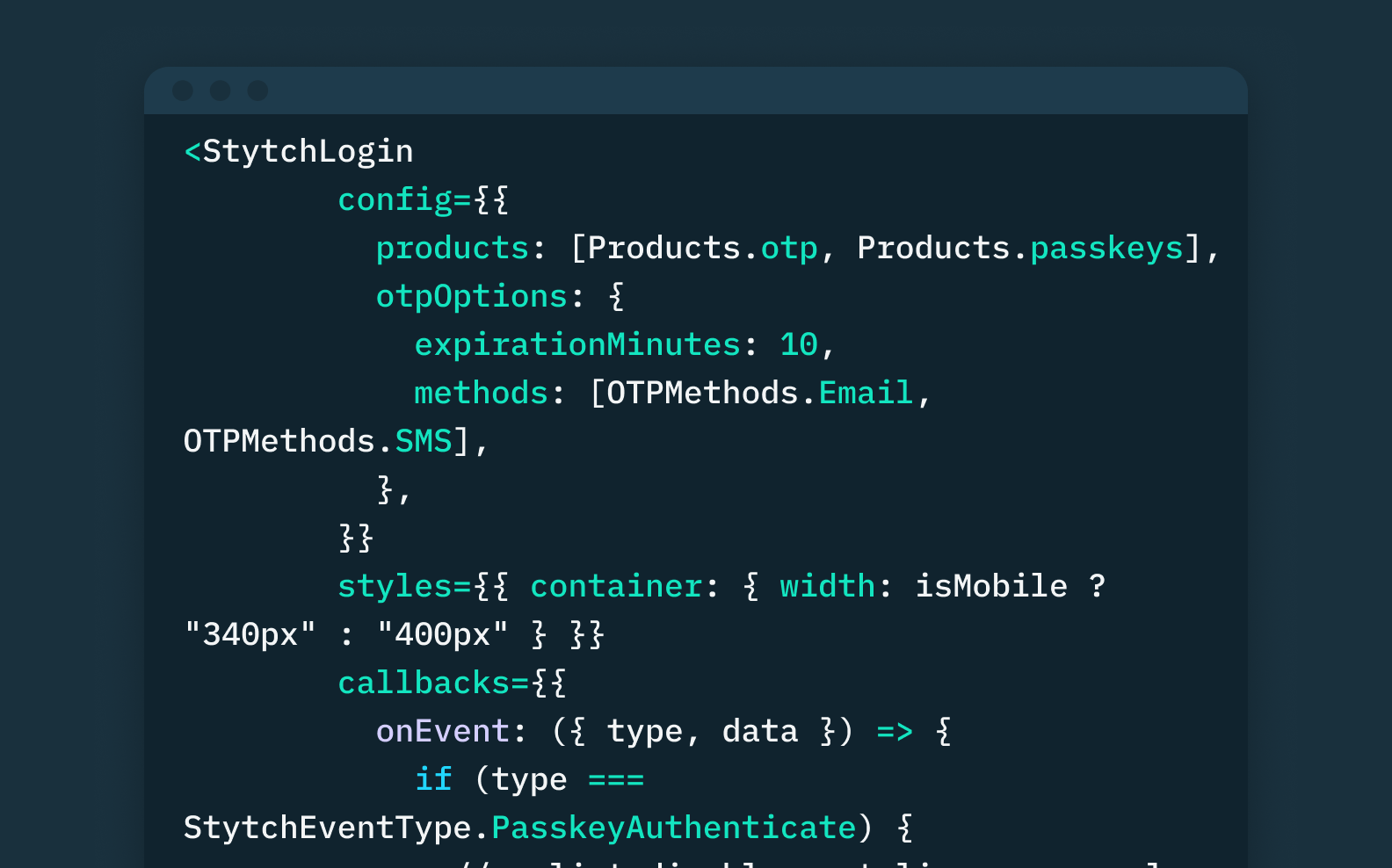
Latest
Engineering
Product
December 5, 2023