What is MFA (Multi-Factor Authentication) and how does it work?
Latest
Auth & identity
January 10, 2022
Author: Julianna Lamb
Today, there is scarcely an area of life that is not touched by or managed online. From our bank accounts to our health records, to our family photo albums, everything we do depends on an online account of some kind. This means the stakes for protecting those online accounts has never been higher.
One of the most important protections companies can leverage to protect their company and their customers is multi-factor authentication.
In this article, we’ll cover what multi-factor authentication is, how it works, and some of the most common ways it’s used today to protect online accounts.
Let’s dive in!
So, what is multi-factor authentication?
MFA stands for multi-factor authentication. It’s a layered approach to confirming a user’s identity to ensure they have permission to access a protected website, application, network, or other digital system or perform a protected task within a digital system.
As its name suggests, MFA requires users to successfully present relies on multiple authentication factors, instead of just one. This often (but not always) occurs at initial login; sometimes, the authentication factor prompts are dispersed throughout a digital experience.
Why is multi-factor authentication important?
As time passes, hackers only grow more sophisticated. They now have at their disposal advanced tools that allow them to generate and test username and password combinations until they arrive at the correct permutation and gain access to the system they are trying to breach.
Compounding the issue is the fact that users often select weak, obvious passwords and repeat them across multiple accounts, making it possible for hackers to breach multiple systems with one set of credentials.
As a result, passwords alone have been rendered insufficient as a means of protecting sensitive online data. In fact, 81% of all data breaches can be traced to weak or stolen passwords, and the Open Web Application Security Standard (OWASP) now encourages all authentication flows to treat passwords as “pre-breached.”
MFA makes online systems more secure in light of this threat. By requiring users to verify their identity through multiple factors—not just a single password or password alternative—MFA makes unauthorized logins and fraudulent transactions less likely to occur. In turn, it has become a pillar of cybersecurity.
How does multi-factor authentication work?
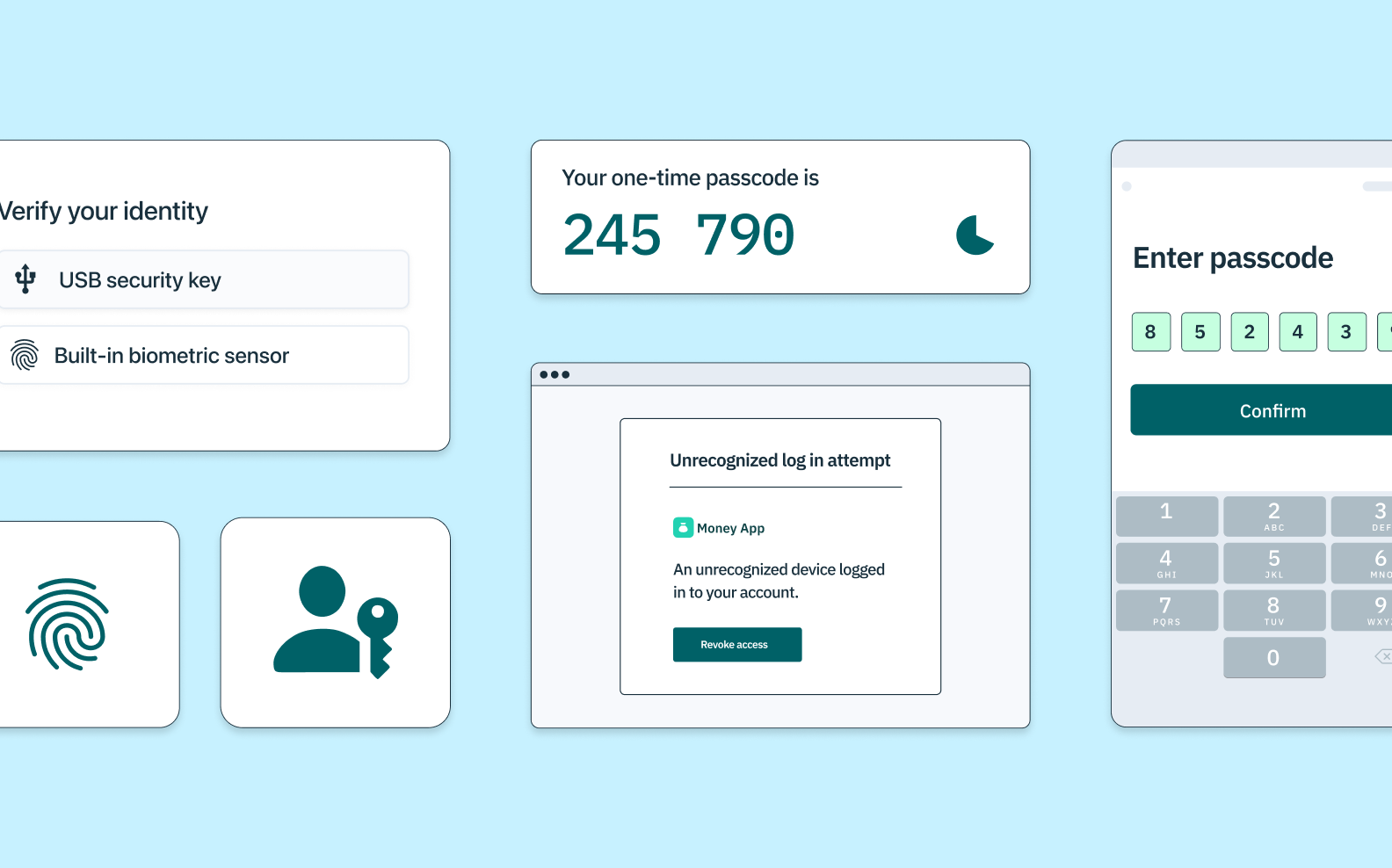
MFA works according to a principle of layered security. By asking users to provide additional forms of identification, it increases the likelihood that the user is who they claim to be, reducing overall risk.
Often, a user is prompted to present all of their credentials at initial login. A typical security protocol might have them submit their username and password (factor 1) and answer a security question (factor 2) before asking them to enter a one-time passcode sent to them by text or email (factor 3). Once the user completes all steps, they have access to the entire application.
The advantage of MFA isn’t just that it asks for more than one piece of identification; it’s that it also asks for identification of different types. The most common types of authentication factors employed by MFA are:
- Knowledge-based (things a user knows)
- Possession-based (things a user has)
- Inherence-based (things a user is)
Knowledge-based factors
Knowledge-based factors include information that ideally only the user will know. These include factors like:
- Passwords are the de-facto authentication factor most people think of. Unfortunately, while passwords are designed to be information that only the user knows, hackers have a lot of ways of learning this information.
- Usernames are also knowledge-based factors. While we sometimes think of passwords as the main authentication factor, it’s really the combination of the username with the password that identifies them exclusively as a factor.
- Pins are very similar to passwords, except they typically draw from a smaller character-base (like numbers only) and are typically a shorter string.
- Security question answers like “What street did you grow up on?” or “What was the name of your first pet?” are also knowledge-based authentication factors. Unlike pins, usernames and passwords, though, these are usually a second factor and not a primary.
Of the categories of authentication factors, knowledge-based authentication factors are generally the least secure, particularly when not paired with second or tertiary factors.
Possession-based factors
Possession-based factors refer to something the user has or has access to instead of knows. These include factors like:
Magic links
Also called email magic links, this type of authentication method lets users instantly log in via a URL sent to a pre-registered email address.
One-time passcodes
SMS one-time passcodes (OTPs), which ask users to enter a unique numeric or alphanumeric sequence sent by text to a recognized mobile phone number
Time-based one-time passcodes
Time-based one-time passcodes (TOTPs), which ask users to confirm control of their device within a certain time frame via a passcode generated by a smartphone app like Google Authenticator.
Push authentication
Push authentication, which sends notifications to an app on users’ devices, asking them to approve or reject a login attempt
WebAuthn
WebAuthn can take a few different forms, but generally combines public key cryptography with on-device biometrics or external security-key hardware – often referred to as a physical key, a hard token or physical token. Most people are familiar with these keys as a USB key called a YubiKey.
Inherence-based factors
Inherence-based factors rely on biological traits unique to the user. You may also hear these referred to as biometrics or factors based on what you are. Examples of biometric factors include fingerprints, hand geometry, iris or retina recognition, voice recognition, and facial recognition.
Biometrics
Biometric authentication is typically built into a device and is designed to scan, analyze, and recognize distinctive, measurable features — like a user’s fingerprint, facial contours, iris/retina patterns, and voice qualities. Many biometric solutions are also equipped with liveness detection tools, so they can distinguish between a legitimate user and a reproduction (like a photograph or voice recording) in order to prevent fraud.
WebAuthn
Wait WebAuthn is both an inherence and possession-based factor? Yes! Because WebAuthn often combines biometrics with public-key cryptography, the biometrics portion of the WebAuthn flow both confirms the user’s identity (inherence) along with ownership of their device (possession).
Passkeys
Passkeys are a new evolution built on WebAuthn, with some key improvements. While WebAuthn pioneered the concept of a single-device passkey (i.e. a single hardware key or a biometric validation tied to your mobile device or laptop), “passkeys” as we’re discussing here refer to multi-device passkeys that can be synced to the cloud and used across devices – even across operating systems! This makes them a drop-in replacement for passwords as well as an excellent additional authentication factor for MFA flows.
In customer-facing authentication, biometrics are typically paired with additional cryptographic technology. Good examples of these include WebAuthn, passkeys, and other technological standards that have come out of the FIDO alliance.
What are the benefits and drawbacks of multi-factor authentication?
Benefits of MFA
The main benefit of MFA is security – multi-factor authentication process makes it considerably more difficult for hackers to breach a system than single-factor authentication. That’s a huge advantage, especially when you consider the exorbitant costs incurred by organizations and individuals affected by security violations.
Drawbacks of MFA
One of the biggest drawbacks to MFA is in its effects on the user experience: in the process of making systems more secure, MFA can add some amount of friction to the system’s user experience. The good news is that can be mitigated by smart authentication design.
Improving MFA user experience
One way to avoid undue hassle and frustration is to employ a route-based approach, in which MFA is only introduced for certain actions or transactions online. Another is to eliminate passwords as a verification factor entirely, since remembering and entering passwords are their own source of friction.
Passwordless authentication methods are simpler and faster than passwords, making user retention more likely. And because they can easily be layered in a multi-factor approach and avoid the security risks posed by weak and compromised passwords, they are inherently more secure.
Multi-factor authentication FAQs
What’s the difference between multi-factor authentication and two-factor authentication (2FA)
MFA and 2FA are not fundamentally different. Two-factor authentication is just a subset of multi-factor authentication, which is an umbrella term for any authentication process that uses more than one verification factor.
In other words, all 2FA is MFA, but not all MFA is 2FA, because some applications of MFA use three or more factors.
What is adaptive multi-factor authentication?
This is a great question. But to understand adaptive MFA, it can be helpful to understand a few different types of auth that often get mixed up:
- Route-based authentication refers to any incremental security method, where a user must only undergo extra checks—like a second or multi-factor authentication—to carry out more sensitive tasks within an app.
- Just-in-time (JIT) authentication or risk-based authentication is another, less technical term for route-based authentication, deriving its name from the fact that users are only asked to authenticate with additional factors at the moment the more sensitive tasks are being attempted. This is also sometimes referred to risk-based authentication, because users are only prompted with additional authentication factors when their behavior is flagged as suspicious or potentially fraudulent.
- Step-up or adaptive authentication refer to a specific type of just-in-time authentication that requires an additional authentication level specifically when trying to perform high-risk operations on an IT system. Unlike JIT, adaptive authentication is invoked based on the type of transaction, not based on user behavior or flags.
All three of these terms are important because they offer ways for companies to remove friction from MFA flows without compromising security – a key to driving conversion, adoption, and user engagement for any business model.
Does MFA make accounts un-hackable or unphishable?
In short, no. There is virtually no authentication method or combination of methods that can guarantee 100% impenetrability from outside attacks. Just as authentication companies like Stytch are constantly innovating to improve our product, hackers are also constantly innovating to find new ways to compromise cybersecurity.
MFA is no exception: while more secure than single-factor authentication processes, secondary factors like one-time passcodes and email magic links can be phished or stolen by attackers who are willing to put in the time.
If phishing is a big concern for your product, it might be good to consider integrating “unphishable” authentication methods into your MFA flow – biometrics, Yubikeys, and passkeys are all much more difficult to phish or steal because they rely on inherence factors, rather than possession or knowledge.
To learn more, you can check our our article about unphishable MFA.
Is MFA the same thing as “zero trust”?
Not exactly, though they are often mentioned together:
- Zero trust refers to an approach to cybersecurity in which no user nor device is trusted until their identity and access is verified. Every single device or user must be authenticated to gain access to a given network application, or server.
- Multi-factor authentication has become a popular approach to zero trust because it adds a few additional layers of verification to the zero trust model.
Put another way, zero trust is a guideline or model for how often or in what cases you authenticate, while multi-factor authentication refers to how that authentication is performed.
Which MFA is right for my business?
At Stytch, we highly advocate for designing your authentication flows around what introduces the least amount of friction to your users, while still keeping them secure. Determining that usually varies from business to business.
While we provide a more in-depth rundown how to choose the right MFA flow in another article, any company can start by considering three main decisions:
- Will you make MFA optional or require it for all users?
- Will you offer multiple MFA options so that users can choose what best fits their needs? How many and which options will you provide?
- Will you layer on?
Remember, when answering these, think about what kind of information is most at-risk or valuable that hackers might want to access, how much friction your users will tolerate, and at which junctures in their signup or login flow they’re most likely to tolerate that friction.
Explore Stytch’s multi-factor authentication solutions
Looking for additional information on implementing secure, user-friendly, multi-factor authentication methods? Stytch has you covered. Sign up for a free account to get started, or talk to an auth expert today to discuss what MFA looks like for your product.