Back to blog
Choosing a B2B auth provider
Auth & identity
Engineering
Jan 20, 2023
Author: Gedney Barclay
Author: Edwin Lim

Welcome back to B2B Auth School. Our mission is to help B2B companies’ uplevel their understanding and implementation of user authentication technologies. Our first series of posts is dedicated to single sign on (SSO). This article is lesson seven, and the final lesson in this series.
Lesson one | Introducing B2B Auth School
Lesson two | Organization tenancy: the foundation of SSO and B2B data models
Lesson three | What is single sign on?
Lesson four | SSO protocols: SAML vs OIDC
Lesson five | What is OpenID Connect (OIDC)?
Lesson six | What is SAML and how does it work?
Lesson seven | How to choose your B2B auth provider
In the previous lesson, we took a close look at Security Assertion Markup Language – the current legacy protocol for handling single sign on (SSO). We looked at SAML’s origins, its benefits, and the anatomy and quirks of SAML messages – including their core components and common challenges and footguns.
To conclude this series of B2B Auth School, today we’re going to take a step back and walk through the decision of choosing a B2B auth provider – what you need to consider, what you need to ask, and how to choose a provider that will support your product in the long term.
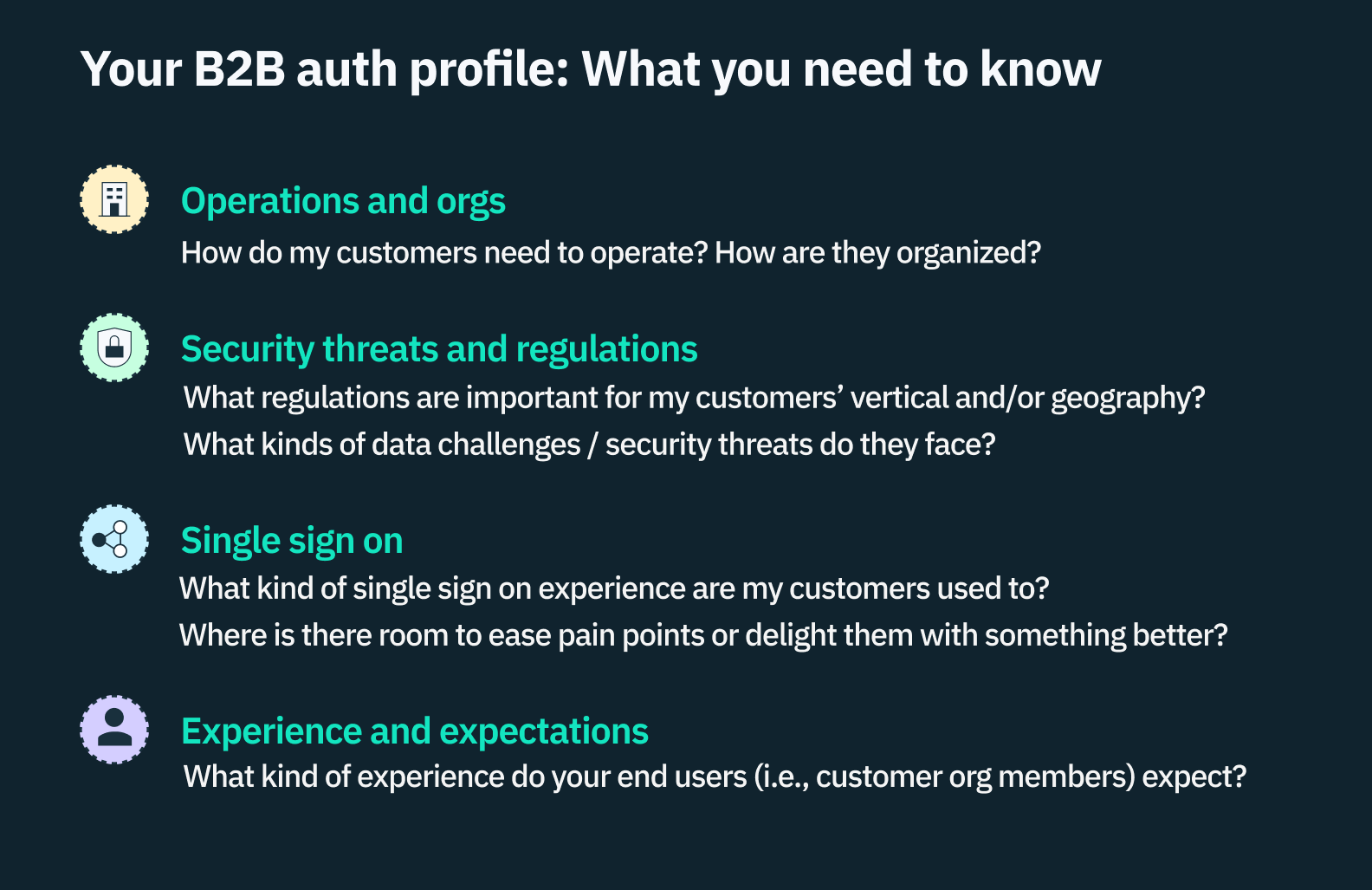
Building your B2B auth profile
Because B2B businesses are so diverse, there’s no one-size fits all checklist for a B2B auth provider. BUT, all B2B companies can arm themselves for conversations with potential auth providers by taking a thorough inventory of their customer’s needs and expectations.
Hint: it’s not just about SAML vs. OIDC!
To choose the right auth provider for your B2B company, you need to develop two key customer profiles: one for the customers you have today, and the other for the customers you intend to have in the next year to five years.
1. How do my customers need to operate? How are they organized?
- How do they currently handle identity management? Do they use an identity provider that’s on-prem or in the cloud?
- Are their organizational and management structures complex? Do they have multiple personas, roles, teams, and departments using your application with different permissions and authorizations?
- How do they manage, provision, and deprovision their corporate accounts for their employees? Do they also have accounts for consultants, contractors, and other third-party members?
2. What regulations are important for my customers’ vertical and/or geography? What kinds of data challenges / threats do they face?
- Related to the above, are your customers in any uniquely regulated industries like healthcare or finance?
- Are they dealing with healthcare or financial data? Bank accounts and/or major financial transactions?
- Are they operating in specific geographies like Europe /GDPR, etc.?
- Do they have any specific SOC2 compliance expectations (i.e, security, availability, processing integrity, confidentiality, privacy, or some combination thereof)?
- Are they or have they been a target for account takeovers or ransomware?
- Have they ever suffered a breach before?
- What kinds of fraud protections do they currently have in place, and where might they still be vulnerable?
- What are the biggest risks that keep their CISOs up at night?
3. What kind of single sign on experience are my customers used to? Where is there room to ease pain points or delight them with something better?
- What kind of dashboard / management setup does their IT team use now?
- What other auth providers/experiences have they worked with in the past? Who do their other B2B vendors use and what has their experience been?
- Where have they encountered the most friction/greatest cost of engineering time with B2B vendors?
- Do they have any unique needs or expectations around approved domains or just-in-time provisioning?
- What kinds of metadata do they expect to be able to communicate during authentication transactions?
4. What kind of experience do your end users (i.e., customer org members) expect?
- What kinds of devices are they on?
- Are they dispersed across different time zones, geographies, native languages?
- Are they typically accessing applications through their identity provider? Or do they prefer to go directly through their service provider?
- What kind of authentication flow are they accustomed to? Which multi-factor methods are they already familiar with (if any)?
Once you’ve answered all these questions for your current customers and prospects, you should do it again – this time for the customers you want to go after in the next few years. Too many B2B companies we’ve talked to think of auth as a “set-it-and-forget-it” feature, but the reality for many startups and smaller companies is that their auth needs will change, and the sooner they take stock of that, the better positioned they’ll be to scale efficiently and avoid headaches down the road.
For this, they need more than an authentication provider – they need an authentication partner.
B2B auth checklist – what you need to build
Once you have a clear profile of your customer’s B2B auth needs, it’s time to take stock of your own resources. Whether you decide to build B2B auth in-house or go with an outside provider, to be an informed collaborator in the process you should make sure you have a solid understanding of the full-breadth of the B2B auth tech stack. Looking back at our series, that includes the following:
Are you prepared to support organization tenancy?
- How will you define organizations and organization membership? Your data model can change drastically depending on what use cases the application supports. You need to consider how you’re going to guarantee data isolation, what structure you need to store the metadata in, if there can be sub-organizations, etc.
- How will you handle org discovery? – email domain, manual entry, etc.?
- How will you manage membership and roles? Will your product allow members to belong to multiple organizations?
- How will you handle various authentication/authorization settings, like account deduplication, just-in-time provisioning, etc.?
Do you understand SSO auth flows?
- Do you have a solid understanding of the different roles and components of SSO? Ie., the roles and responsibilities of an identity provider, service provider, etc.?
- Do you understand the differences between IdP- and SP-initiated SSO? And the risks involved with each?
- Do you have a detailed grasp of the various transactions managed by the auth provider? This includes identity authentication, session management, and informational exchanges with both the identity provider and the service provider.
- Do you understand the value SSO provides to your B2B customers, and where you can enhance and differentiate that value?
Want single sign-on without the headaches? Switch to Stytch.
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Do you know the protocols that facilitate SSO and the differences between them?
- What are the origins of OIDC and SAML? And what needs did each arise to fulfill?
- What is OIDC? And why are its roots in OAuth and use of JSON important?
- What is SAML? Why is it the legacy protocol, and what are the implications of being XML-based?
- What are the common customer profiles for OIDC vs. SAML? And is it worth it providing both? (Hint: almost certainly!)
Do you understand each protocol (SAML, OIDC) in enough depth to implement?
With OIDC…
- How does OIDC build off of OAuth to offer authentication and authorization? Where do these two protocols diverge and complement each other?
- How do the roles and functions differ between resource owners, relying parties, resource servers? How do those mirror terms from SAML?
- What’s the role and anatomy of bearer tokens? What are best practices for using them?
With SAML…
- What are the different data elements in SAML? How do they relate to each other?
- What is the anatomy of a SAML message? What are the key differences and components of requests and responses?
- What are XML/SAML’s common footguns, and how can you best avoid them? Which are specific to SAML, and which are vulnerabilities of XML more broadly?

Auth partner vs. auth provider – a future-forward approach
At the beginning of this series, we talked about B2B auth as a crucial growth lever: the easier you make it for your customers to manage their employees’ accounts and onboarding to your application, the more likely you are to land upmarket sales and see widespread adoption.
Authentication is often framed as a pure security consideration. But authentication touches many different parts of your product and involves several customer touchpoints – especially with B2B companies. These touchpoints and product features also look very different as companies scale: the needs of startup B2B customers are very different from the enterprise.
That’s why when working with an authentication or SSO provider, B2B companies should find someone that’s not just looking at what their customers today need: they want an auth provider that’s able to predict upmarket needs so that authentication becomes an enterprise catalyst that accelerates a B2B company’s growth.
The decisions you make today about your authentication solution could have long-lasting effects that either hold your product up, or launch it into a bigger, brighter future.
If you want to talk to an auth expert about the right data model and auth solution for your B2B product, chat with one of Stytch’s auth experts today.
Congrats on finishing your first “course” in B2B auth school!
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.