Back to blog
Step-up versus multi-factor authentication (MFA)
Auth & identity
Aug 23, 2022
Author: Stytch Team
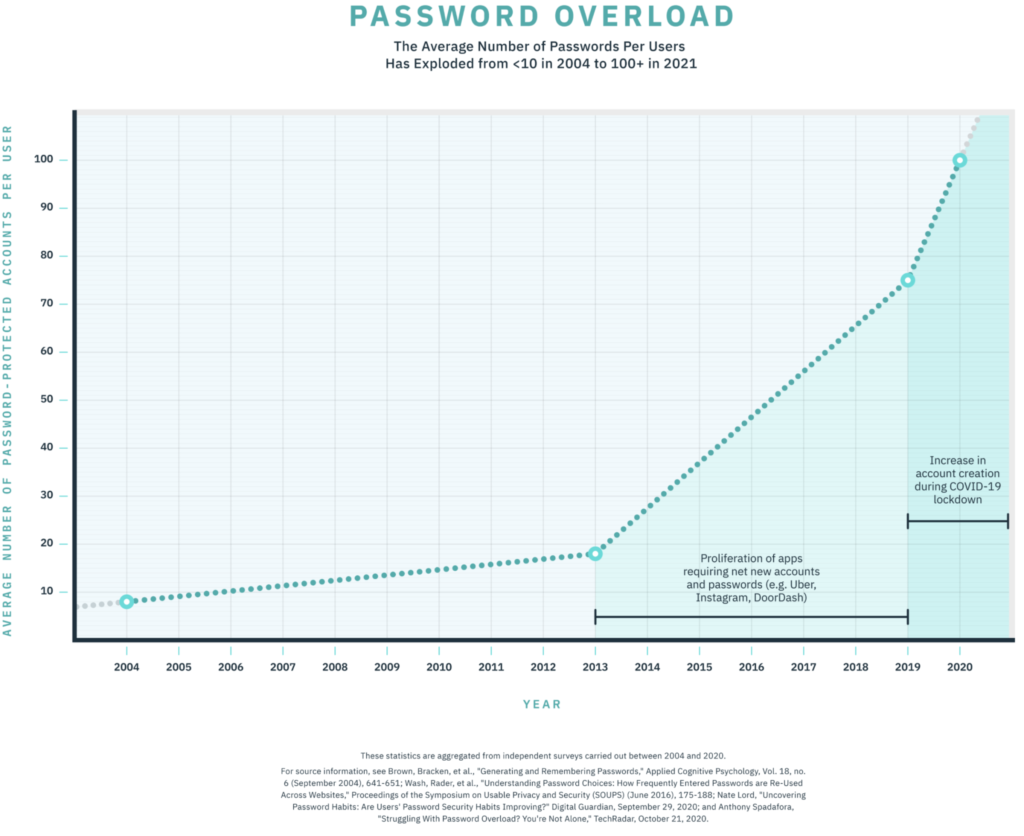
Over the past decade, digital transformation has touched every part of our lives. Even companies that have historically provided analog services to users (e.g. shipping) have had to adjust to this digital transformation – that’s because consumers expect to be able to access and act upon information with the digital devices in their pockets and on their desks. On average, users now hold over one hundred online accounts for every type of service that you can imagine. This shift has required virtually all companies to create digital solutions to support their core business functions and store sensitive data such as customer and vendor information. Keeping confidential data secure needs to be a top priority for all organizations, and this is exactly what digital authentication tries to achieve.
Digital authentication verifies identity when accessing sensitive data, applications, or other services. An entity could be a user (a human), an Internet of things device, a process, application, or service. Authentication is the backbone of IT security. Without it, no one could safely use digital technology as we do today.
Various authentication methods protect digital assets and govern access to them. Some are more secure than others, and some require more than one authentication method to achieve their desired security level. This article compares two popular authentication strategies, step-up authentication and multi-factor authentication (MFA), and discusses where each fits best according to an organization’s security needs.
Defining multi-factor authentication (MFA)
As data breaches become common, the need to strengthen current authentication systems that still only use usernames and passwords to protect sensitive resources becomes paramount. According to the Verizon Data Breach Investigations Report, 82% of all breaches involve weak or stolen credentials. Most of these breaches would not have happened if an MFA mechanism had been in place.
MFA (also often called two-factor authentication or 2FA) is a mechanism that requires users to provide two or more authentication factors to verify their identity. There are three major types of authentication factors, and each one requires different authentication methods to satisfy its conditions.
- The “something-you-know” authentication factor
This factor is something a user knows, such as a username and a password or the answer to a secret security question. This is the most common form of authentication online today where a user must re-supply some shared secret with the application (e.g. their password) in order to prove themselves. - The “something-you-have” factor
This factor is something the user has possession of, such as a smartphone to receive an SMS message containing a secret code or a hardware security device to generate a one-time passcode (OTP). - The “something-you-are” factor
This factor is something strictly unique about the user, such as a biometrics characteristic. Biometric authentication involves verifying users’ biological or behavioral characteristics, such as voice and facial recognition, fingerprints, or DNA matching.
The benefits and challenges of MFA
MFA provides numerous benefits for organizations:
- It increases security by providing additional layers of authentication. If cybercriminals steal a user’s password, they must still give a second authentication factor.
- It has become mandatory for many organizations working in high-value industries to comply with the relevant data protection requirements.
- An MFA system that uses biometric and passwordless authentication streamlines the authentication process and makes employees and users happier by removing the need to remember traditional passwords.
Despite its benefits, MFA also comes with challenges:
- Deploying an MFA system is costly compared with traditional password-only systems, especially in the initiation phase.
- Implementing MFA to secure applications, data, and systems in hybrid environments is technically challenging. For example, some applications could be local while others are cloud-based. Implementing the same authentication system across hybrid environments requires continual monitoring and maintenance to remain operational.
- Some users find it daunting to use MFA authentication, which makes them abandon the service in favor of the traditional username and password combination.
Add MFA to your auth flow today
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Defining step-up authentication
As mentioned above, organizations use various digital authentication methods to protect their sensitive assets. Multi-factor authentication describes the process of combining multiple authentication factors to increase the security of users’ accounts. Step-up authentication is a specific type of multi-factor authentication where the application implements an authentication strategy that requires an additional authentication level specifically when trying to perform high-risk operations on an IT system.
For example, customers can use the banking applications installed on their smartphones to view their profiles and check their latest account transactions. Of course, they must log in to their account using, for example, a username and password. However, suppose the customer tries to perform a risky operation, such as transferring a large sum of money to another account. In that case, the banking app requires an additional authentication method. Another method might be providing a one-time passcode (OTP) sent through email or text messaging, an authentication app, or biometrics.
As the previous example shows, step-up authentication requests additional identification information to verify a user’s identity when trying to accomplish sensitive actions. Requesting further information enables IT administrators to use different authentication levels based on the sensitivity of the resources.
You can contrast step-up authentication with another type of MFA called adaptive MFA – step-up authentication is a MFA strategy where particularly sensitive routes in an application require MFA while adaptive MFA is a strategy where only certain types of user characteristics (e.g. a suspicious IP address) require MFA. Both are individually helpful, but they become even more powerful when combined together into a comprehensive authentication strategy.
You can use step-up authentication to secure access to critical resources, such as updating payment information, transferring funds, and changing payment settings in an account to enable withdrawing funds to other accounts. You can also use the adaptive MFA scheme to verify users’ identities when:
- They fail to log into their account several times — for example, by providing an incorrect username and password.
- They access an online service from an unusual location, such as a foreign country, for the first time.
Step-up versus multi-factor authentication
In general, most authentication systems to date still use usernames and passwords as the first authentication factor. However, many organizations have strengthened their authentication systems by adding additional authentication factors like possession or biometrics. For instance, if the traditional password is the first authentication factor, the second one could be the following:
- Hardware tokens that mimic USB dongles and generate a temporary code.
- Software tokens generated by programs on computers or smartphones.
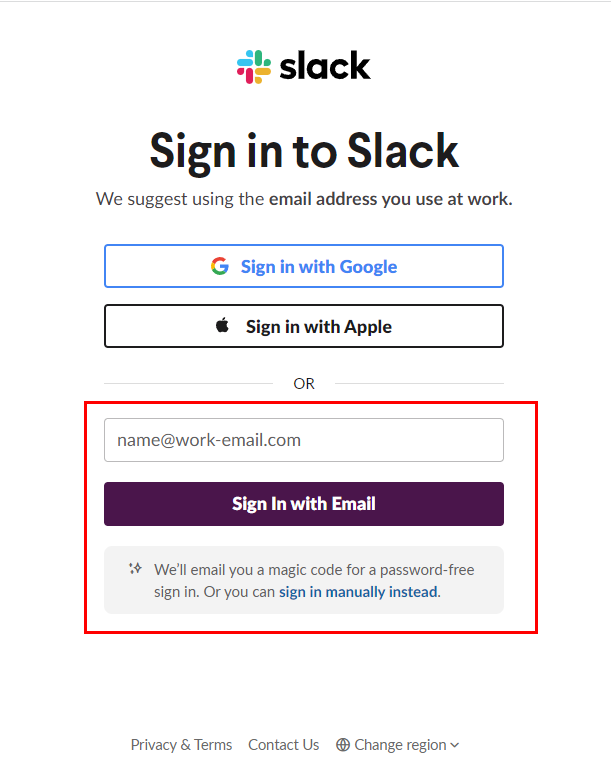
- Magic links sent by the system to email addresses enabling users to log in by clicking the link. See the screen capture below for a sample magic link sent using Slack:
- OTPs sent to a user’s registered mobile phone number by SMS that contain a temporary passcode.
- Push notifications sent using an authentication application installed on users’ smartphones. An example of such an application is Microsoft Authenticator.
- Biometric authentication using unique biological traits for verification, such as voice recognition, facial recognition, retina and iris recognition, fingerprint scanning, hand geometry, and vein recognition.
You can use step-up authentication with MFA to add additional layers of authentication when accessing critical resources. The system authenticates users with MFA. However, when they want to perform risky operations, the system requests additional authentication using a different factor to confirm their real identity. In this context, step-up authentication is a system that uses MFA techniques to provide a sequence of authentication chains when users want to access critical resources.
Organizations often use step-up authentication to follow their security policies and compliance requirements. This allows them to strengthen the security of their system while allowing the right amount of friction based on the different security needs of other parts of the application. It’s worth noting that route-based authentication and just-in-time authentication are other terms used synonymously with step-up authentication.
Managing the burden of MFA systems and incorporating the step-up approach within them requires investing in a solution that can handle this process. Stytch provides a rich authentication solution that uses a suite of authentication factors. We believe the best approach to MFA is to introduce friction when needed, using incremental security for higher-risk actions within an app. This approach allows you to restrict specific actions within an app that require higher security and allow lower security, read-only actions to occur easily.
In terms of the effort required to implement step-up versus MFA, any system that uses MFA can use step-up without much additional effort. As previously mentioned, you can consider step-up a subtype of MFA in terms of using different authentication factors when trying to access sensitive resources.
Authentication in practice
High-risk industries, such as finance, health care, e-commerce, and government, should use MFA to secure their digital assets. However, they should also deploy step-up authentication to protect access to the most critical areas within their IT systems. For example, in the health care sector, patients could use MFA authentication, such as a traditional password and an OTP sent by SMS, to access their medical profile held by a health institution. However, when a patient wants to access the area containing information about their diseases, medical treatment, or the type of medicine they take, they must submit an additional authentication factor, which is where step-up authentication can be used.
In finance, most people already use two-factor authentication (considered a type of MFA) when withdrawing funds from ATMs. For example, customers must provide their credit card and a memorized PIN code when withdrawing money from an ATM.
Developing MFA authentication that includes step-up authentication is a challenging task that most organizations can’t achieve alone. Stytch provides an authentication platform that handles the entire auth process for customers. It includes the following key features:
- Magic Links to send password-free links for registration and login.
- One-time passcode sent by SMS to registered mobile phone numbers.
- One-time passcode sent to registered email addresses.
- One-time passcode sent by WhatsApp, allowing users to sign in from any place worldwide.
- OAuth 2.0 and OpenID to provide a low-friction authentication option.
- Support for just-in-time authentication that allows for selecting the level of authentication based on the sensitivity of the accessed resources.
- Support for built-in biometrics authentication and hardware token authentication.
- Ability for crypto wallets to register and log in to any web2 or web3 app or service
- Various additional security measures, such as breach detection for password authentication.
- Bot prevention technologies.
Traditional password-only authentication systems are insufficient to stop the ever-growing number of data breaches. Deploying an MFA system has become necessary to protect the most sensitive digital assets. Step-up authentication adds extra security for logged-in users attempting to access sensitive information.
Despite numerous cyberattacks, organizations may still find it challenging to deploy modern authentication systems that use step-up authentication and MFA because of the technical complexity of developing and maintaining such solutions. Stytch provides a comprehensive authentication solution that includes today's most popular authentication factors to provide frictionless authentication solutions for both MFA and step-up approaches.
Talk to an auth expert to learn more about the authentication options that Stytch offers.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.