Back to blog
An introduction to WebAuthn
Auth & identity
Dec 17, 2021
Author: Reed McGinley-Stempel
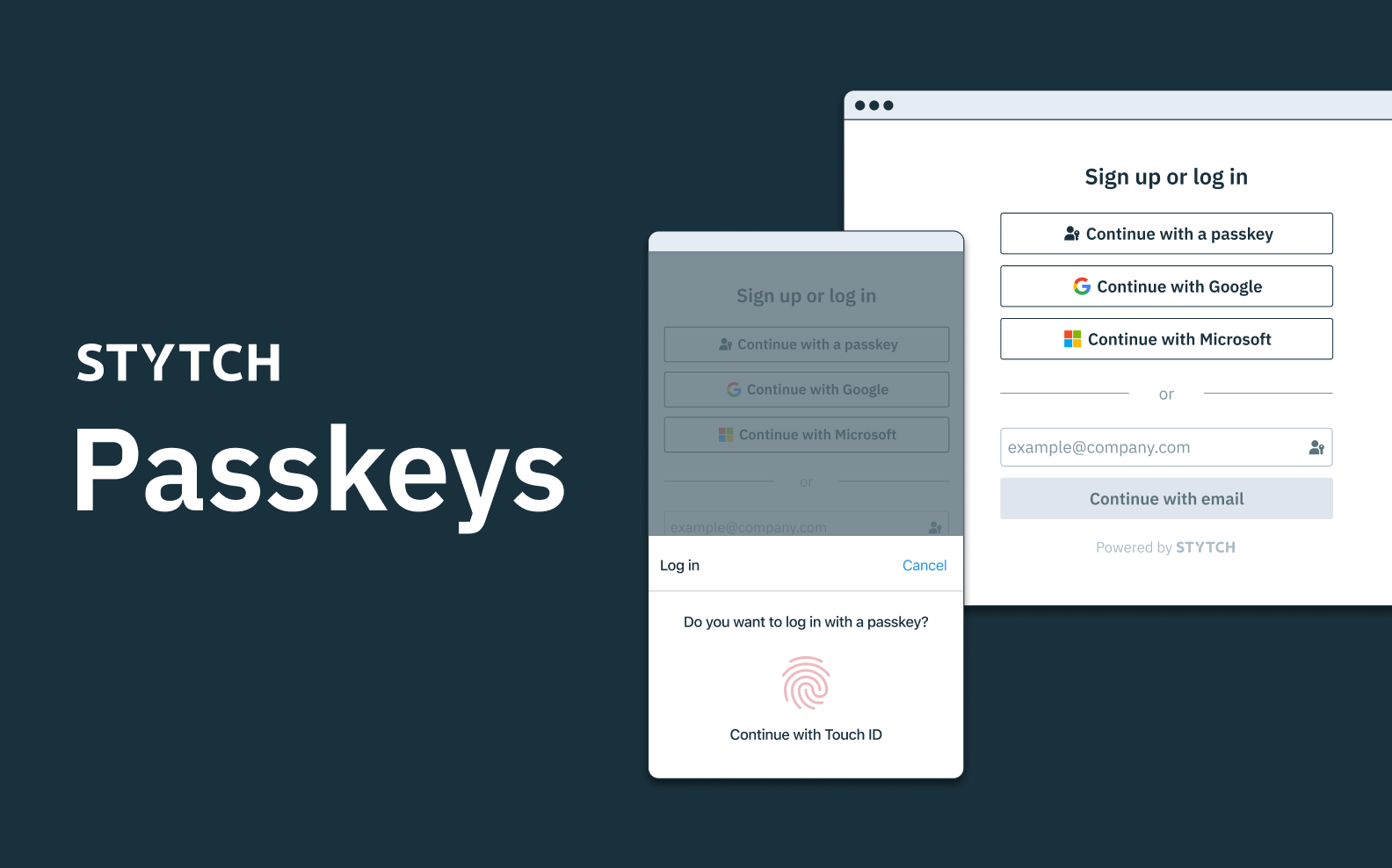
An example of the WebAuthn user flow on mobile or desktop. WebAuthn makes it easy for users to authenticate with device biometrics (e.g. FaceID/TouchID) or a hardware key like a YubiKey.
“WebAuthn” is one of the most exciting passwordless technologies available to developers and users. With WebAuthn, experiences like the below are now possible, allowing applications to authenticate users with the biometric capabilities built into the devices they use every day:
Historically, integrating WebAuthn has been a complex and time-consuming activity for developers. Stytch now supports the WebAuthn protocol, so that developers can embed this feature in minutes rather than months.
So, what is WebAuthn?
Technically speaking, WebAuthn is a web standard that allows web-based applications to leverage public-key cryptography to authenticate users online.
That’s a mouthful, so let’s break that down. In layman's terms, WebAuthn provides users with two highly secure yet low-friction options for authenticating themselves with mobile and desktop web applications -- when applications integrate WebAuthn, they can give users the option of using either of the following authentication methods for accessing their account:
- Built-in device biometrics such as TouchID or FaceID
- When using this authentication method, you’re both verifying possession of the user’s original device and biometric proof in the user’s facial ID or fingerprint. This is also referred to as a “platform authenticator” because it’s tied to the device.
- Hardware keys such as YubiKey
- This is referred to as a “cross-platform authenticator” because, unlike platform authenticators that are tied to a particular device, the hardware key can be moved from one device to another and retain your authentication method.
What are WebAuthn’s advantages over existing authentication methods?
Historically, when signing up for or logging into online accounts, users are asked to set up a username and password as their primary authentication method for accessing their account (of course, we’d contend there are much better primary authentication factors than passwords).
Due to the prevalence of password re-use and how it contributes to stolen accounts, most applications will now also ask users to go through a two-factor authentication flow. Often, users get one or multiple of the following options for two-factor authentication:
- Security questions (e.g. what is your mom’s maiden name?)
- This is considered to be a low security form of 2FA because the information used to authenticate the user is often public information.
- SMS verification (e.g. receive a 6-digit one-time passcode over SMS)
- This is a medium security form of 2FA. A motivated attacker may try to steal a user’s phone number or trick the user into passing along their passcode to the attacker. While it’s much better than password-based authentication or security questions, it’s by no means invincible.
- Time-based one-time passcodes aka TOTP (e.g. enrolling with an app like Google Authenticator or Authy)
- This is a higher security form of 2FA. TOTP eliminates the risk of someone stealing your phone number because the authentication method is tied to a user’s device. However, a user could still be tricked into accidentally sharing their passcode with a bad actor.
While TOTP is the safest 2FA method on the above list, many applications do not offer it as an option because of the friction it can create for users. Every user with a phone number can receive a SMS one-time passcode, but TOTP requires the user to download a dedicated app like Google Authenticator to enroll and use this 2FA method. As a result, many applications don’t support TOTP, and when they do support it, a large portion of users will still opt to use SMS passcodes for two-factor authentication.
WebAuthn is an extremely compelling authentication method because it is both more secure and lower friction than the 2FA options listed above, encouraging users to adopt it over less secure methods. And unlike TOTP, users do not need to download anything or potentially use multiple devices to complete one login to use WebAuthn. They can simply use the TouchID on their computer or the FaceID on their mobile phone like they already do multiple times per day to log into their device. An additional benefit of WebAuthn is that it prevents the “phishing” of users because there are no passcodes for the user to expose to an attacker. This is why some refer to WebAuthn as “unphishable multi-factor authentication (MFA)”.
Why aren’t we all using WebAuthn?
So, if WebAuthn is so groundbreaking, why isn’t every website already using it? We expect a large number of apps will begin to integrate WebAuthn in 2022, but there are a couple contributing factors that explain why adoption has lagged so far:
- First, WebAuthn device support has only recently reached a critical mass, with ~90% of global users’ devices now supporting this authentication technology.
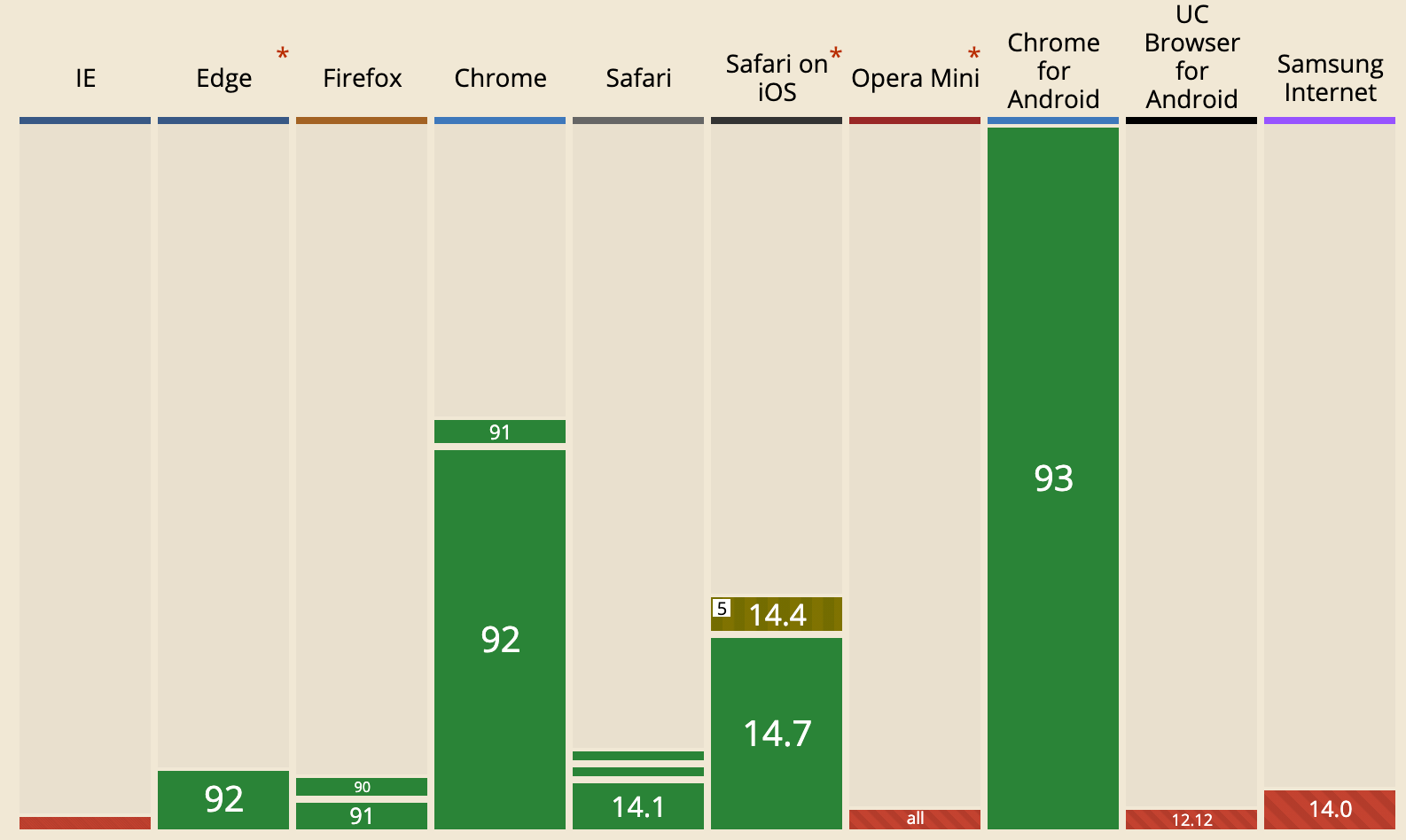
- Second, it’s historically been very difficult to integrate WebAuthn, so developers have reasonably chosen to focus on more product-related work rather than trying to integrate an opaque and complex web authentication standard. There are also certain poorly documented edge cases to consider when using WebAuthn, which can significantly complicate implementations if you’re not familiar with WebAuthn.
In 2022, Stytch is focused on helping bring WebAuthn mainstream.
Using WebAuthn with Stytch
Seeing the immense benefits of WebAuthn but also the frustrations that developers had with integrating with it, we’ve built our product to be the simplest way for developers to support WebAuthn. We’ve also made it simple to offer other authentication methods alongside WebAuthn to easily support cross-device access and account recovery such as email magic links, OAuth logins, and more.
If you’re interested in integrating our WebAuthn product, check out the API documentation here or sign up for a Stytch account here.
Build auth with Stytch
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.