Fraud and risk prevention
The most reliable way to stop attacks and abuse
Beyond WAF and CAPTCHA: 99.99% bot detection, intelligent rate limiting, and reverse engineering protection.
Know every user and every device on your app
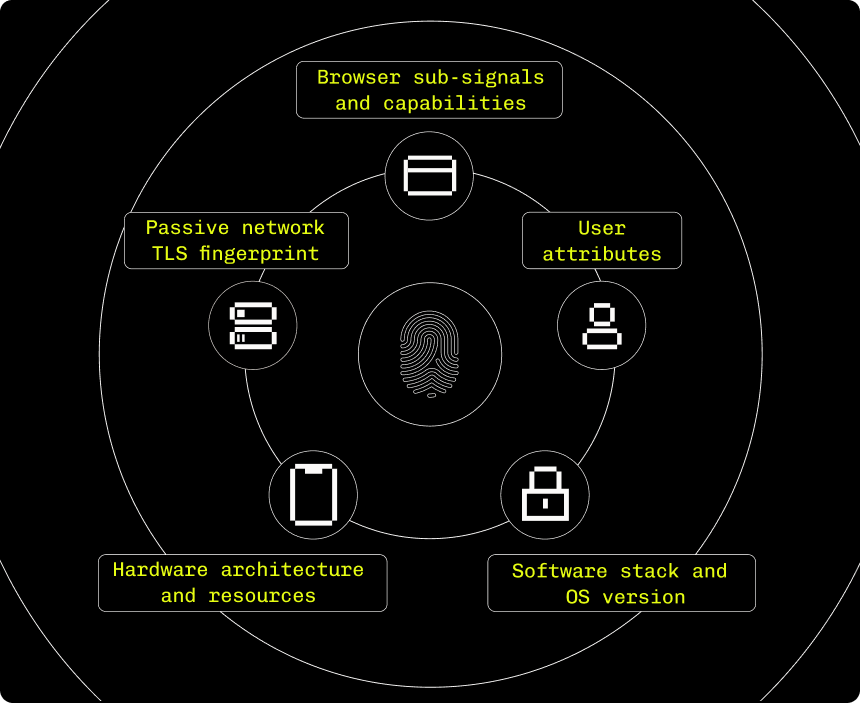
The world's most powerful fingerprint
Device intelligence built on a powerful combination of deterministic signals and supervised machine learning

Hardened against the most sophisticated attackers
Immutable and resistant to evasion or reverse engineering, all while preserving user privacy
See what happens when you attempt to mask your identity.
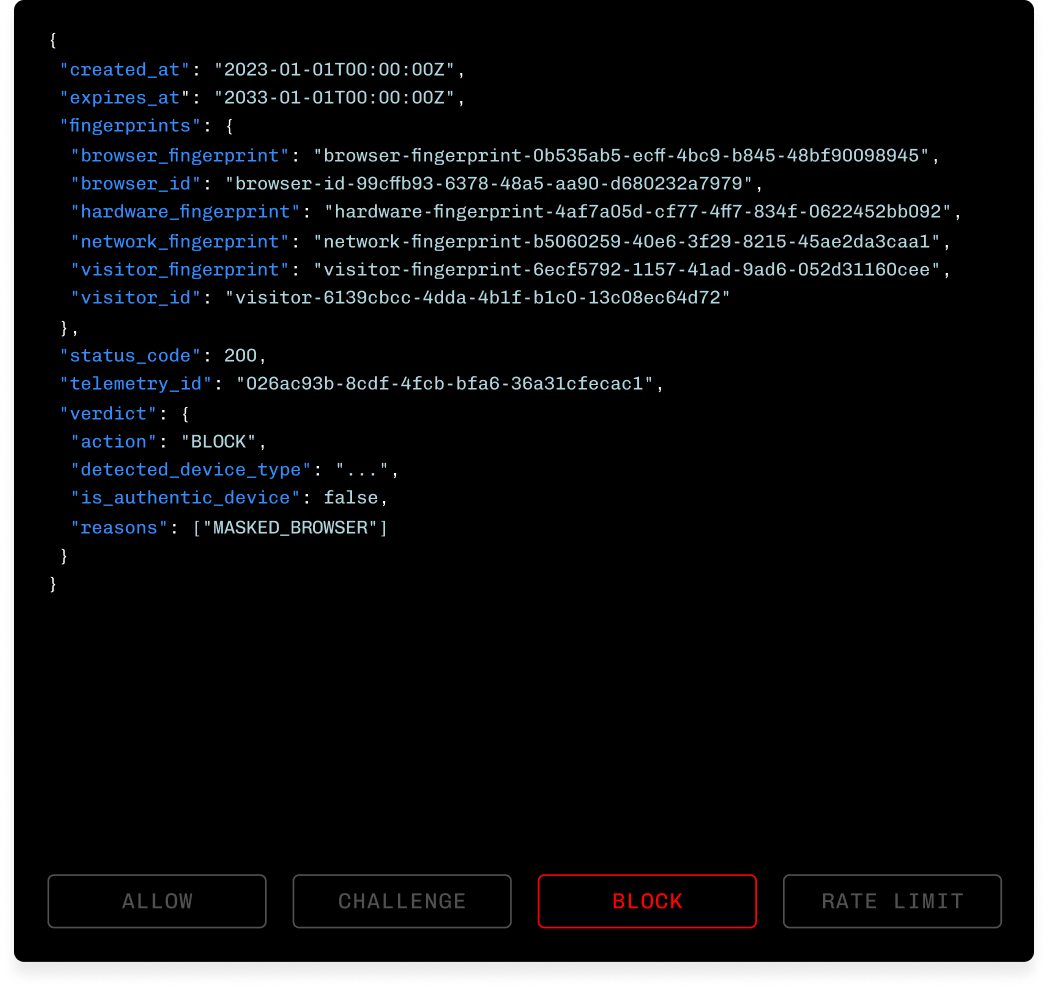

Any Device. One Verdict.
Keep bad actors and bots out
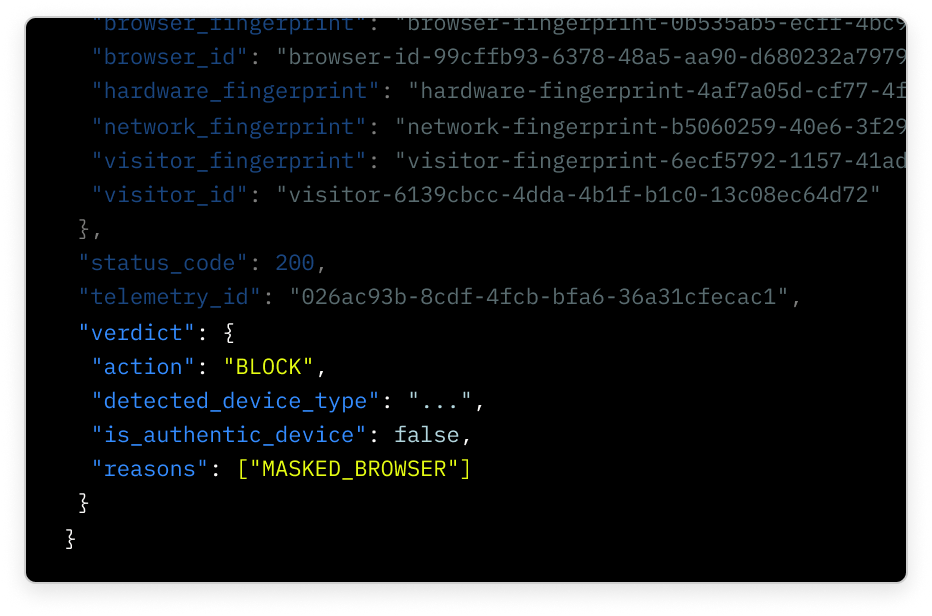
A recommended action for every visitor
ALLOW, BLOCK, or CHALLENGE verdicts with detailed context on the reasons for the decision, enabling you to act with confidence.
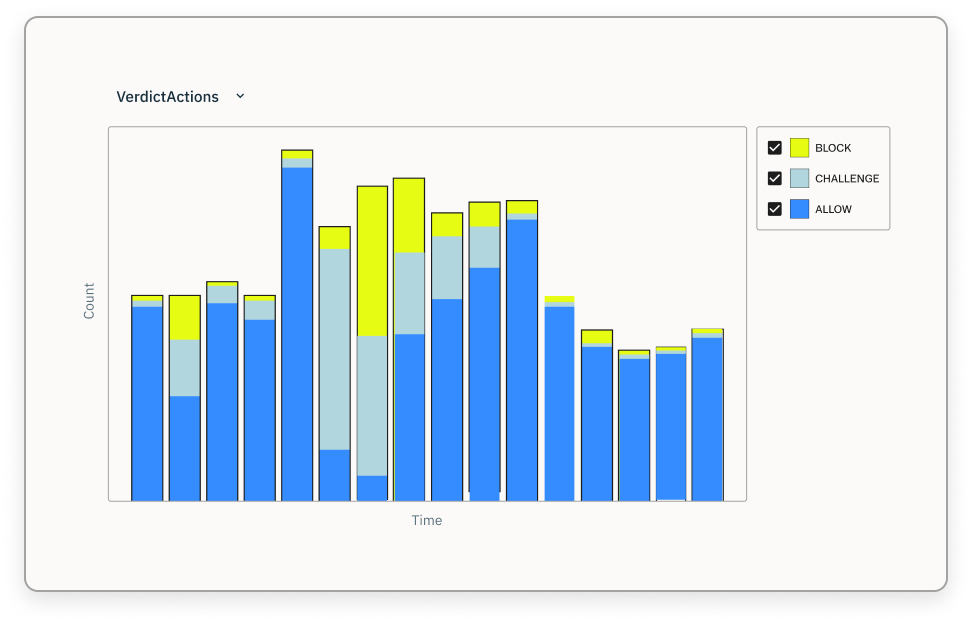
Monitor your app’s fraud and risk profile
Detailed dashboard and live logs to better understand the risk to your users and application in real-time
Next-Level Protection
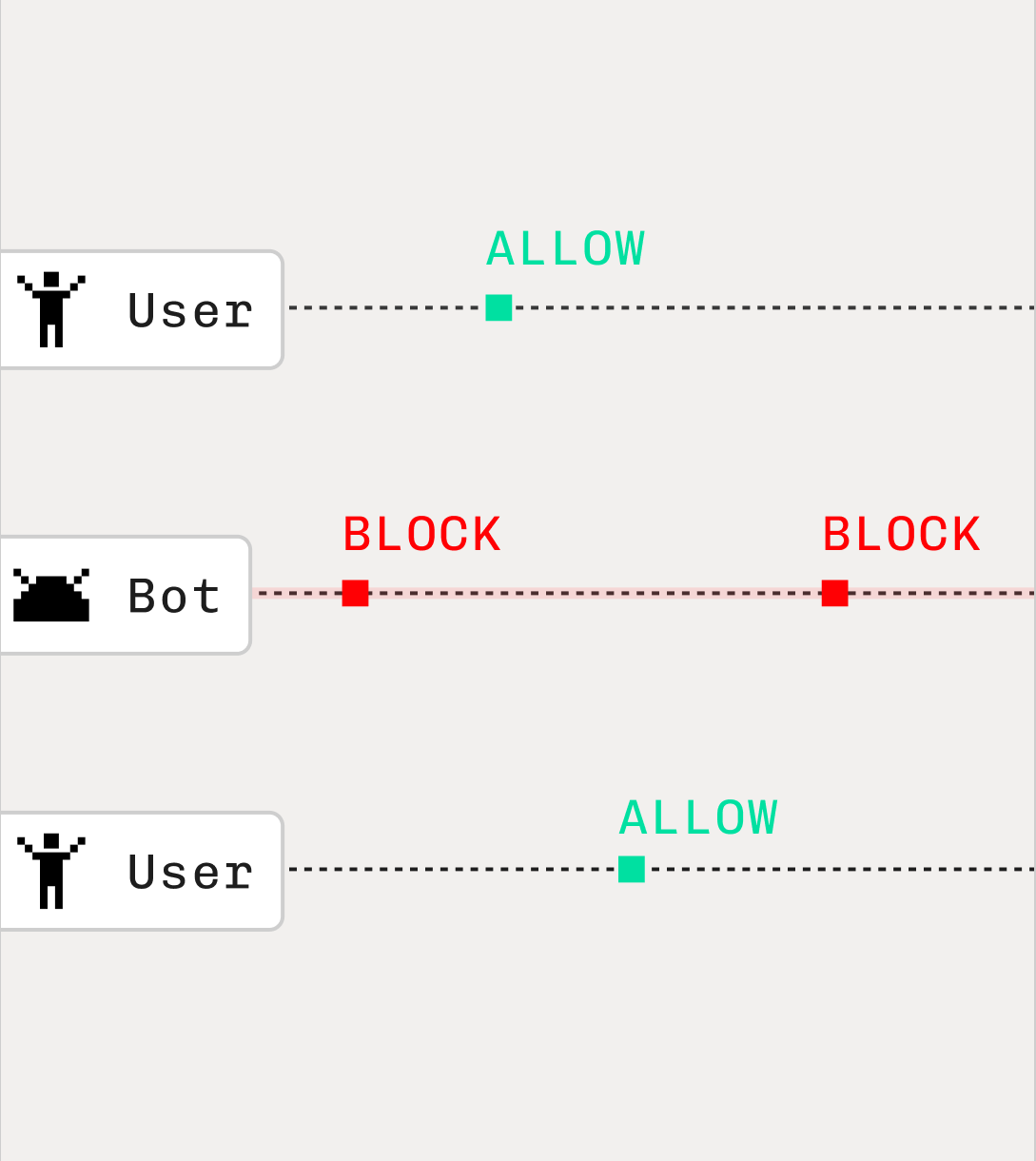
Intelligent Rate Limiting
Granular device, browser, and network fingerprints go much deeper than basic IP address or user agent detection to ensure that only suspicious traffic is rate limited.
Invisible and better than CAPTCHA
Stronger bot detection with device fingerprinting lets you focus on real users, not the bot swarms.
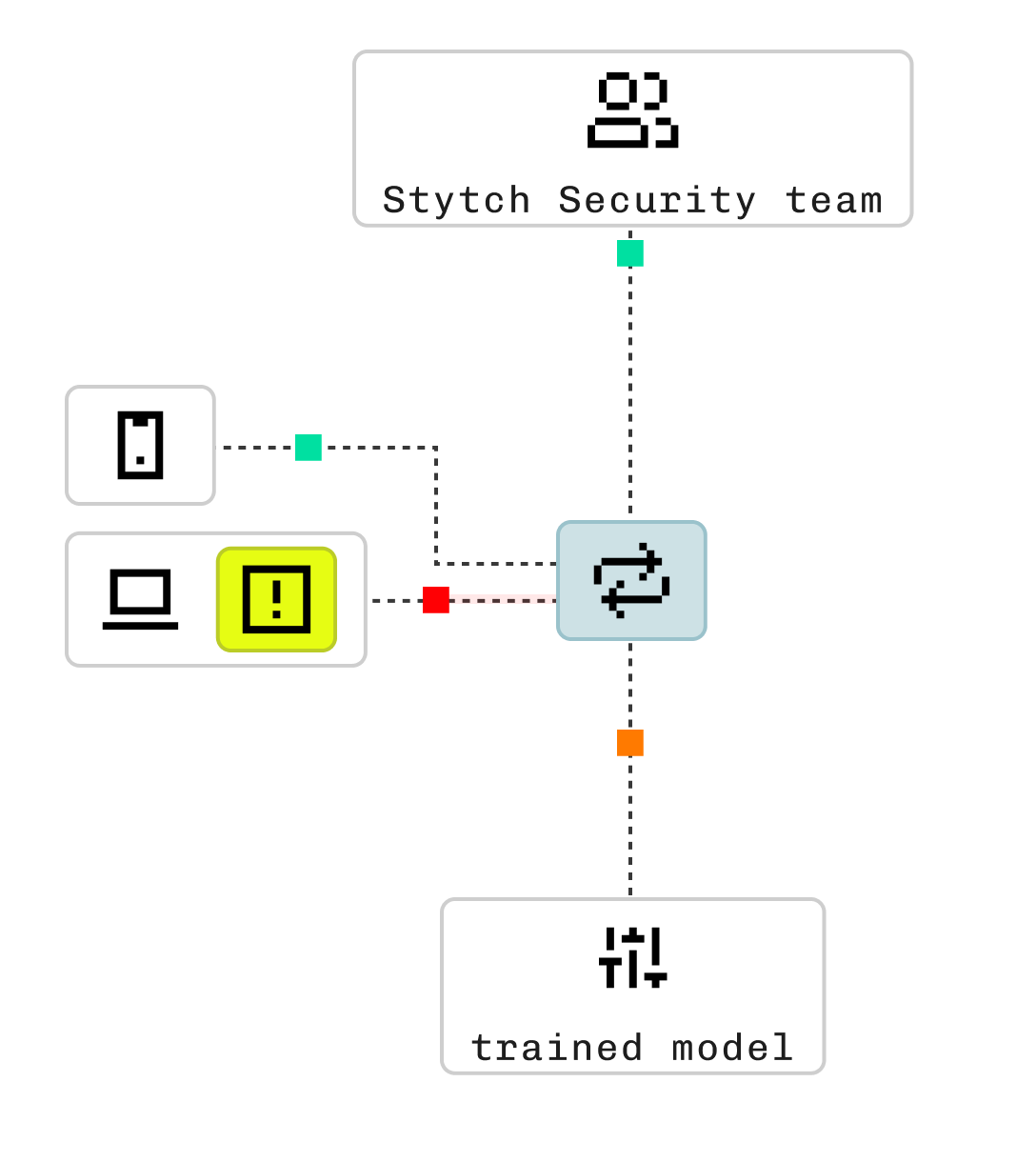
ML-Powered Device Detection
Supervised machine learning programmatically detects and categorizes new threats, device types, and spoofed attributes in real time.
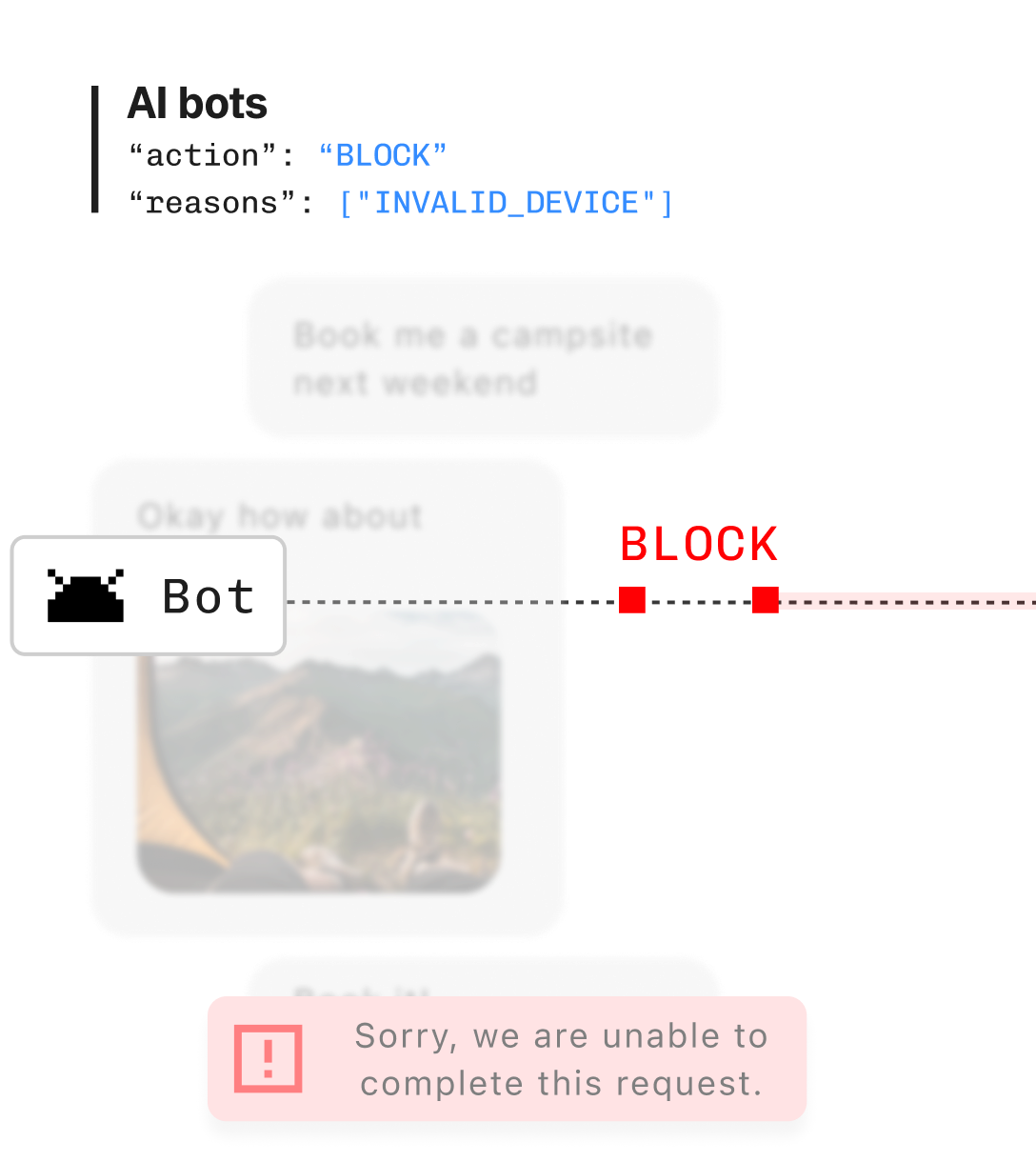
AI agent detection & monitoring
Detect AI agents like OpenAI’s Operator and Anthropic’s Computer Use API, giving you the power to monitor allow, or restrict AI-driven activity in your app.
Without compromise
99.99% accurate bot detection
The world’s most accurate fingerprint, leveraging standard and proprietary signals
<100 ms latency
A frictionless UX with more than 3× lower latency than competing solutions
Multiple fingerprint types
Unique fingerprint for visitor, browser, network and more to handle any use case
Device classification grouping
Automatic categorization based on trust level, authorization status, and more
Client-side encryption
Encryption at rest and in transit to prevent reverse engineering
Integrate in minutes
Add a javascript snippet to immediately start monitoring vulnerabilities
Authentication and authorization supercharged with device intelligence
The most advanced fraud and abuse prevention built-in. Not just protecting your users and application, but unlocking powerful new authentication features.
Fingerprint protected auth
SDK that protects your application from account takeover (ATO) and related attacks by implementing a Device Fingerprinting check on every authentication request.


Reduced OTP & 2FA checks
Recognize devices so that users only need to do multi-factor authentication when logging in from a new device.

Better than CAPTCHA
Don't make your users click on stop signs. Invisible bot detection improves UX and conversion by only adding friction to suspicious traffic.

Smart Email Magic Links
Ensure the delivery of email magic links even when enterprise security services are in place to check links.

What engineering teams are saying
Stytch’s Fraud & Risk tools give us granular visibility into attempted attacks and effortlessly prevent a range of bot and fraud attempts.
Stytch’s Fraud & Risk tools give us granular visibility into attempted attacks and effortlessly prevent a range of bot and fraud attempts.