Account creation abuse
Stop account creation abuse—without blocking real users
Detect and block bots, free trial abuse, and multi-account attacks with unmatched device intelligence.
Don’t let fake accounts wreak havoc on your app
Free tier resale
Stop attackers from reselling your AI and LLM free trial credits, while protecting your growth strategy for real users.

Compute abuse
Prevent developer-infrastructure or cloud tooling from being hijacked for cryptomining or GPU workloads that you pay for.

Toll-fraud loops
Stop paying thousands of dollars in fraudulent SMS pumping or SIP toll fraud every month.

Account farming
Keep bots from creating millions of dormant fake accounts stockpiled for future spam, phishing, and propaganda.

The cost of fake accounts
Ecosystem: Chargebacks, fines, regulatory scrutiny, and damaged partner reputation.
Growth: Skewed metrics, inaccurate forecasts, and low real-user conversion.
Brand: Eroded customer trust and increased attacks from bad actors who realize you're an easy target to exploit.
The strain on your engineering team
Alerts and capacity spikes that consume engineering cycles and mask real growth.
Hours lost tuning IP blocks, writing ad-hoc rate-limit scripts, and parsing risk scores.
Fragile integrations across WAF, CAPTCHA, and in-house scripts that still miss sophisticated bots.
Stop bots and bad actors automatically— before they sign up
Identify even the most sophisticated attackers. Stytch fingerprints are stable, resistant to evasion and reverse engineering, and designed to preserve user privacy.

The Stytch difference
99.99% accurate and reverse engineering resistant
Unique fingerprint from browser, hardware, and network signals—even behind VPNs and headless browsers.
Tamper-proof using obfuscated JS/WebAssembly plus client-side encryption to block anti-detect tools and fingerprint switchers.
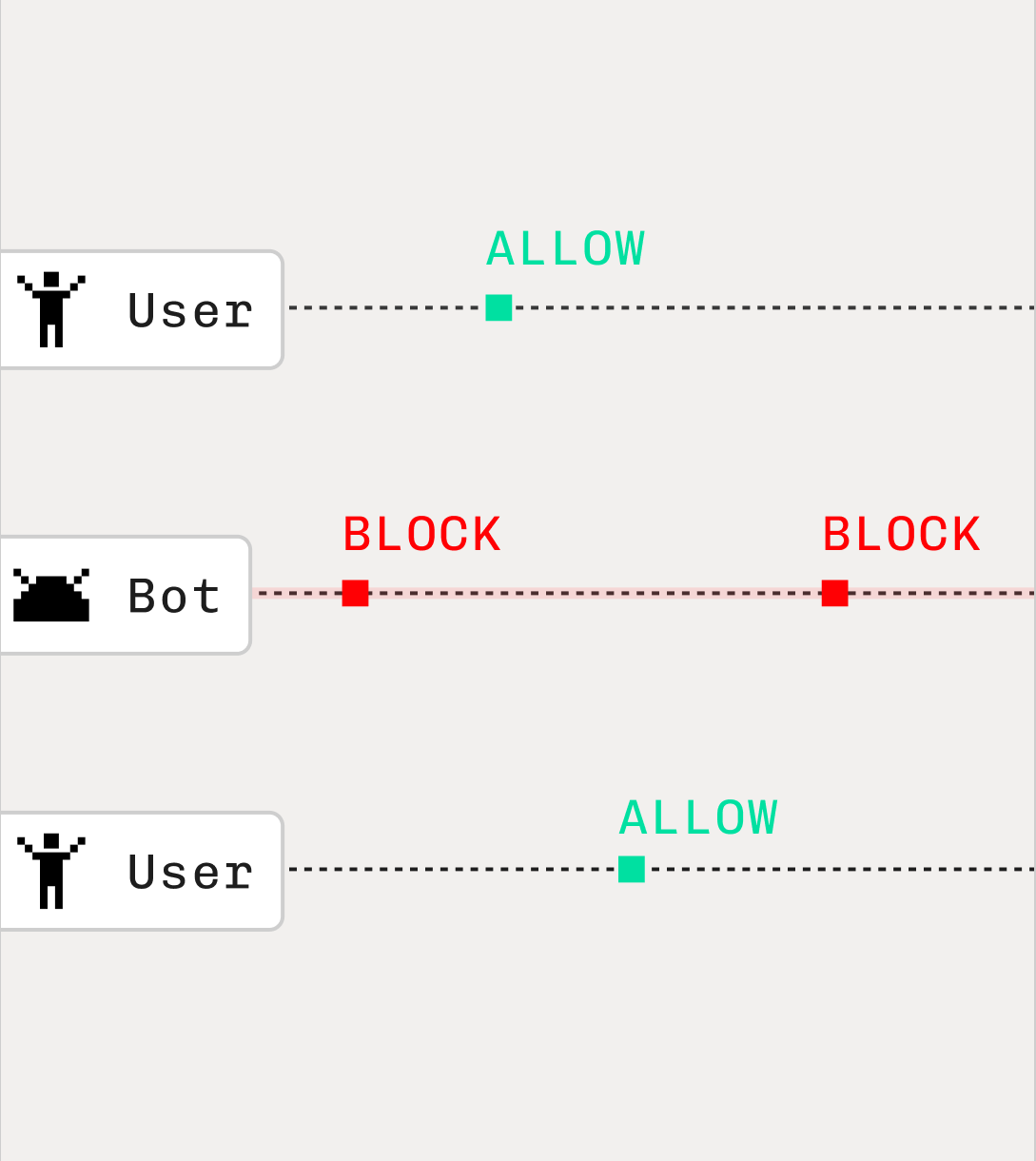
Deterministic verdicts (ALLOW/BLOCK/CHALLENGE) in <100 ms, giving clear actions, not fuzzy risk scores.
Intelligent Rate Limiting stops attackers, not users
Device-aware anomaly detection throttles abusive devices only, without punishing everyone on the same network.
Escalating friction moves from challenge to timed ban as abuse persists—no rule-tuning marathons.
Traffic-adaptive thresholds learn your normal peaks, so promos or launches aren’t mistaken for attacks.
Robust auth, no CAPTCHAs needed
Stop bots at sign-up and login, whether attackers use proxy solvers, LLM-powered automation, or traditional scripting.
Roll out the red carpet for your customers; add extra friction for suspicious traffic only, while remaining invisible to 99% of real users.
Flexible integration protects any sign-up, login, or critical action via API/SDK.
Custom rules & API-first control
Granular overrides: whitelist QA scripts, ban a fingerprint, or force MFA with a single call.
Live dashboards & webhooks stream verdicts so you can tweak rules and watch impact instantly.
Rich JSON payloads let you feed fingerprint data into risk engines, ML models, billing, analytics, or SIEM tools for deeper insights.
In my first month, we were hit with daily waves of spam signups. I realized that if I could block those at the source, I wouldn’t have to deal with the downstream abuse they caused after getting into the system.
In my first month, we were hit with daily waves of spam signups. I realized that if I could block those at the source, I wouldn’t have to deal with the downstream abuse they caused after getting into the system.