Enterprise Single Sign-On
Enable SSO for your app.
Any identity provider. One integration.
SAML and OIDC-compliant authentication, fully configurable per customer—without the engineering hassle.
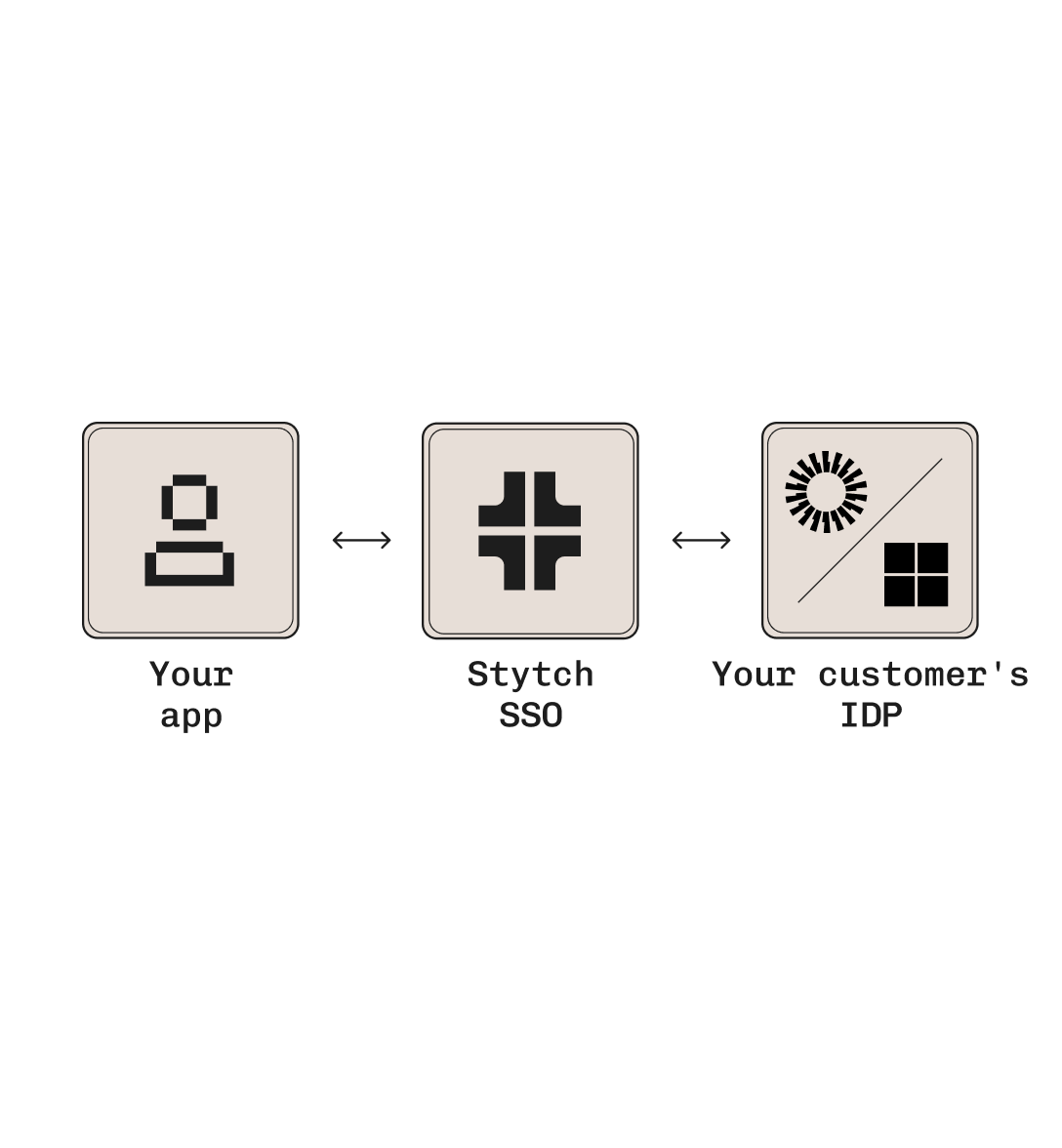
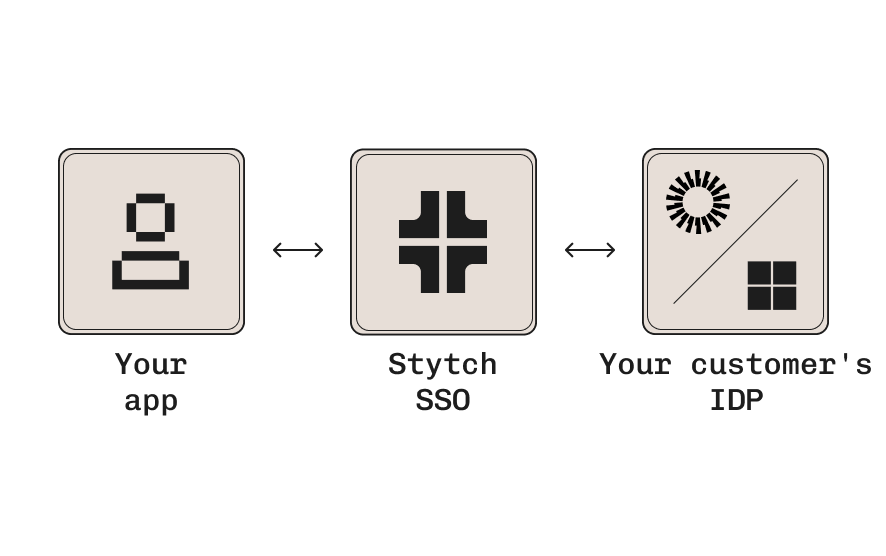
Enterprise SSO in one sprint
Integrate across any SAML or OIDC based identity providers like Okta, Google, Microsoft
Compliance you can trust: SOC 2, ISO 27001, HIPAA, GDPR, and more
Integrates with your existing app with intuitive API calls
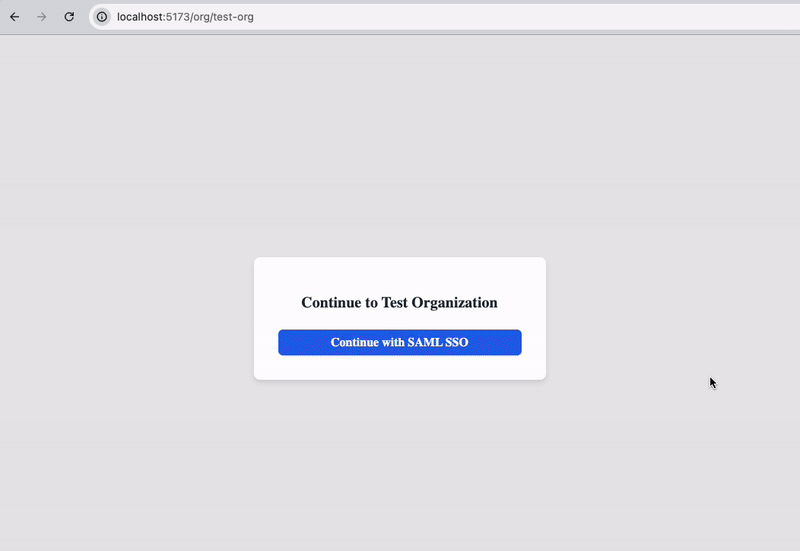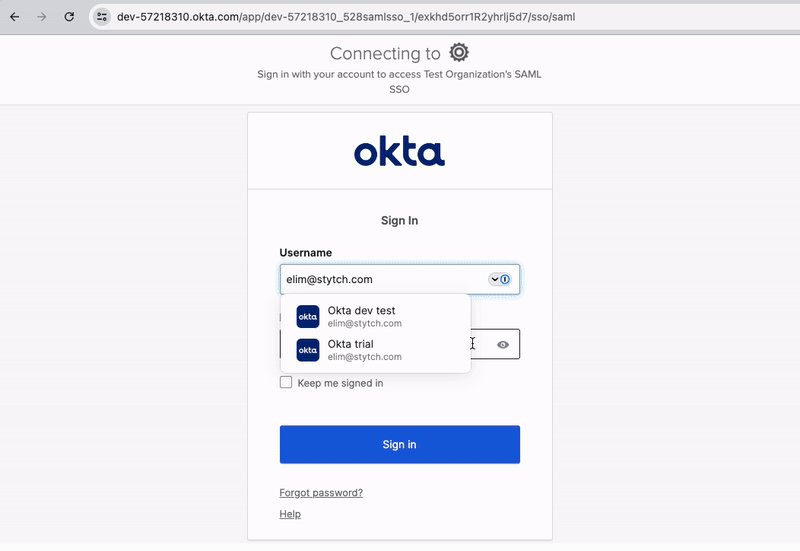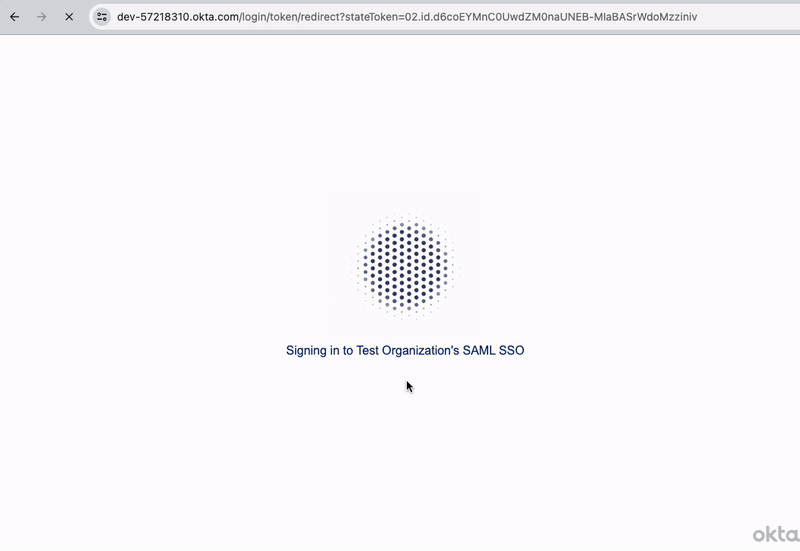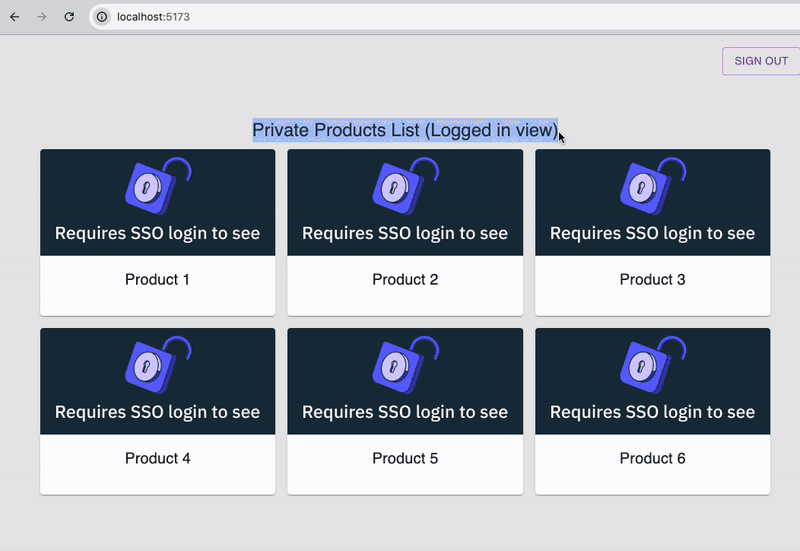
SSO simplified
Stytch handles the backend auth exchange with each identity provider, wrapping complex OIDC and SAML protocol flows into two simple API calls.
Start the SSO process:
curl --url https://test.stytch.com/v1/public/sso/start?connection_id=saml-connection-test-51861cbc-d3b9-428b-9761-227f5fb12be9&public_token=PUBLIC_TOKENComplete SSO Authentication:
curl --request POST \
--url https://test.stytch.com/v1/b2b/sso/authenticate \
-u 'PROJECT_ID:SECRET' \
-H 'Content-Type: application/json' \
-d '{
"sso_token": "SeiGwdj5lKkrEVgcEY3QNJXt6srxS3IK2Nwkar6mXD4="
}'Easily customize SSO configurations based on individual customer requirements
Easily configure one, or many different providers per customer
Modular tooling to add in features like SCIM and Magic Links as you need them
Start with SSO, add enterprise features and AI agent security with ease down the line
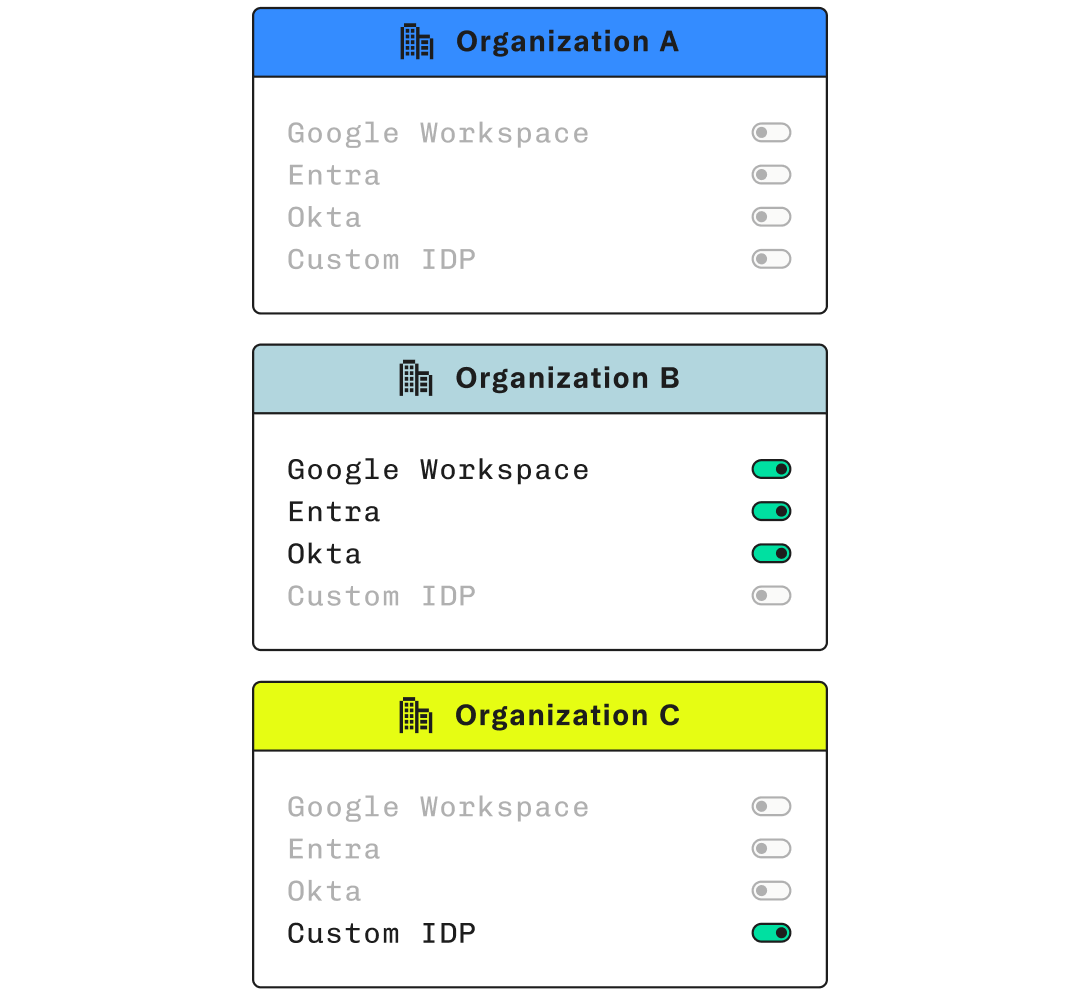
Build with flexibility
Integrate SSO via backend APIs, headless frontend SDKs and pre-built frontend UI
Easily embed ready-to-use login and signup components into your app. Keep users on your own domain, and match your own CSS to align to your brand.
Learn about Stytch pre-built UI
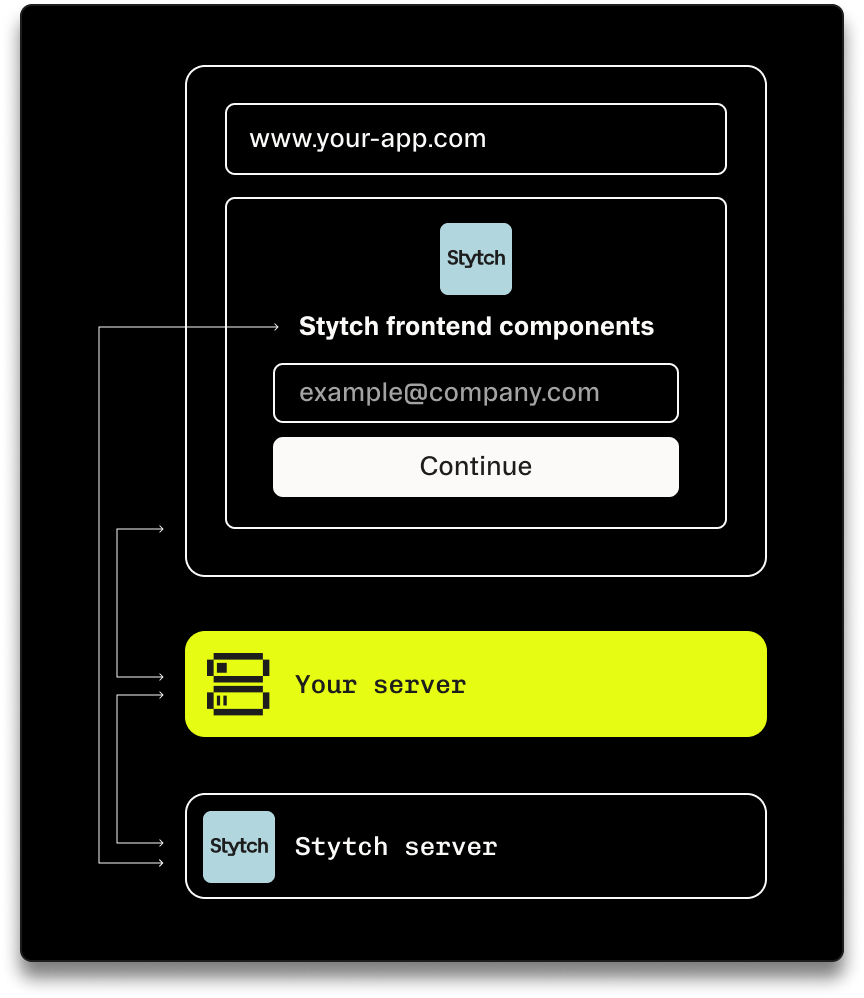

With self-serve SSO settings and onboarding
Let your customers handle configuration for members, organizations, and SSO via an admin UI embedded right inside your app
It’s remarkable how much work well-thought-out abstractions can do for you. Since Stytch handles the initial request to determine available login methods, requiring SAML or Google login is as simple as flipping a bit via Stytch’s API.
It’s remarkable how much work well-thought-out abstractions can do for you. Since Stytch handles the initial request to determine available login methods, requiring SAML or Google login is as simple as flipping a bit via Stytch’s API.
Transparent pricing
No price hikes, feature gating, or hidden fees. Pricing scales predictably with each additional SSO connection added.
SSO connections
5 connections: free
6-10 connections: $125 per connection / month
FAQ
While libraries simplify basic protocol handling, they don't handle all of the complex challenges of SSO. You still need to manage provider-specific integrations, handle edge cases (race conditions, clock skew, expired assertions, etc), implement secure multi-tenant session management, and develop onboarding and administration tools.
Stytch abstracts all of this away by providing:
1. Comprehensive IdP integration: Fully managed, out-of-the-box compatibility with Okta, Azure AD, Google Workspace, OneLogin, and more via both SAML and OIDC, eliminating custom code for provider-specific quirks.
2. Just-in-time (JIT) provisioning and automatic role assignment: Configurable settings to automatically provision new users and assign roles based on SSO connections, IdP group membership, or email domains.
3. Org-level auth policies: Allow customers to define domain enforcement, permitted login methods, and multi-factor authentication (MFA) settings via Admin Portal or API.
4. Multi-tenant session management: Built-in support for scoped sessions, isolated identities, and seamless switching between multiple organizations—all while enforcing each Organization's unique authentication requirements and protecting against account takeover attack (ATO) vulnerabilities.
5. Prebuilt Admin Portal: Fully managed UI enabling customer self-service for configuring and managing their own SSO setups, significantly reducing your engineering and support burden.
6. Production-grade reliability: Proven handling of real-world SSO edge cases, including assertion validation, relay state mismatches, and time synchronization issues critical to enterprise environments.
7. Breakglass users: Designate trusted admins who can bypass organization auth policies to resolve critical issues quickly if an IdP integration breaks.
6. Trusted External SSO Connections: Enable secure Managed Service Provider (MSP) scenarios by explicitly allowing SSO from trusted external IdP instances without introducing account takeover risks.