The most powerful fingerprint solution
Use a better fingerprint
Stytch fingerprinting is tamper-resistant, lower latency, and encrypted device fingerprinting compared to Fingerprint. Get more stable fingerprints to more accurately identify your traffic.
Intelligent Rate Limiting
Stytch Device Fingerprinting uses granular device and network identifiers beyond just IP address detection to ensure that only suspicious traffic is restricted.
This is unlike Fingerprint, who provides no specific defense against high rate bot attacks beyond traditional open-source tools like Puppeteer and Selenium.
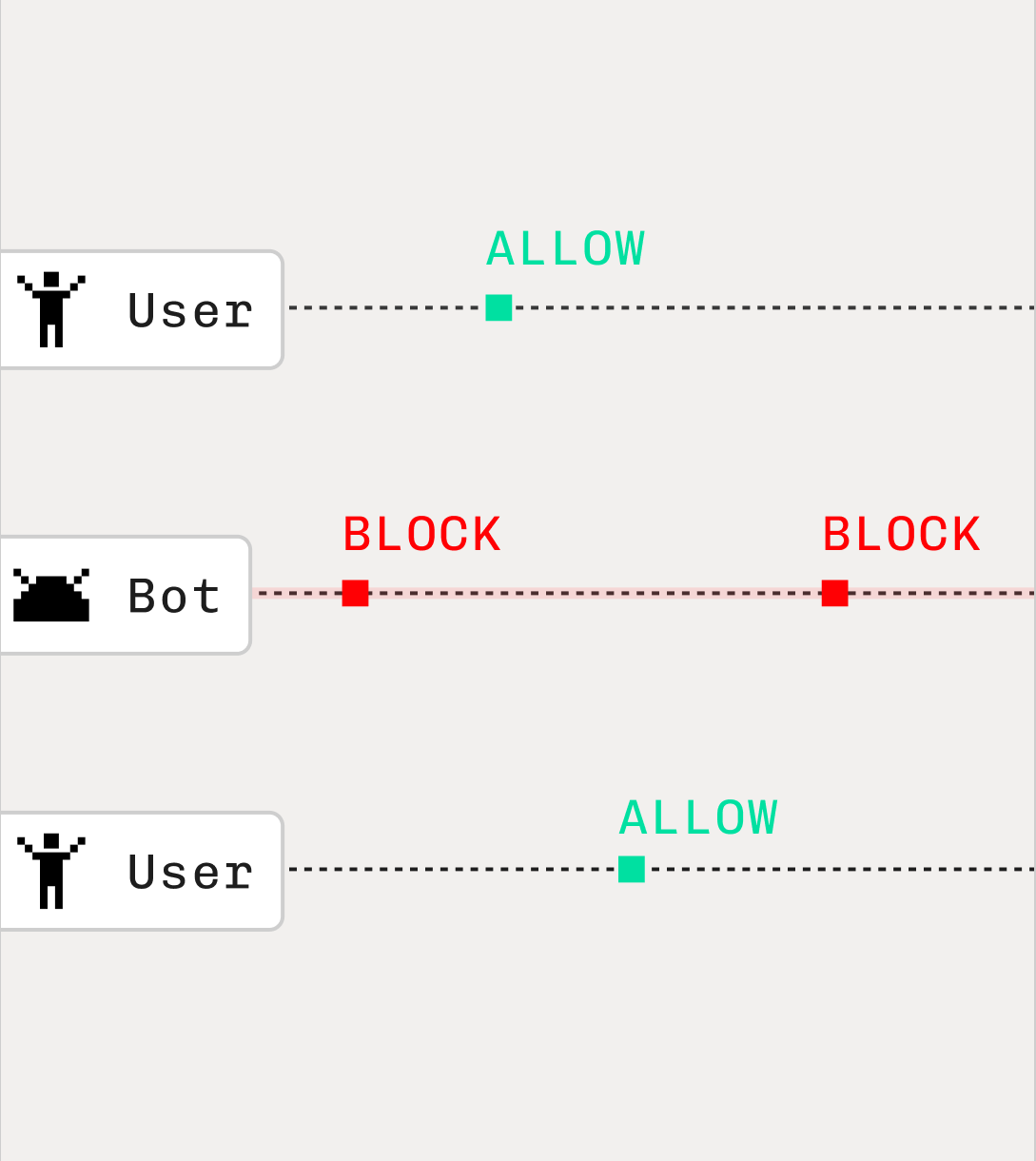
Clear decisions to remove the guesswork
Unlike Fingerprint, who will only provide an aggregate value based on their scoring system of individual attributes detected, Stytch uses a deterministic pattern matching approach to give you a direct clear ALLOW, BLOCK, or CHALLENGE verdict for your app to easily take action on.
Responsiveness that keeps things snappy
When compared head to head with identical environments, Stytch Device Fingerprinting repeatably is at least 4 to 5 times faster than Fingerprint even in worse case scenarios, going up to 14 times faster in select scenarios.
For a brand new fingerprint, a payload that took Fingerprint 366ms to finish took Stytch 56ms, a difference that is felt in the responsiveness of your application.
Built for resilience to all attack vectors
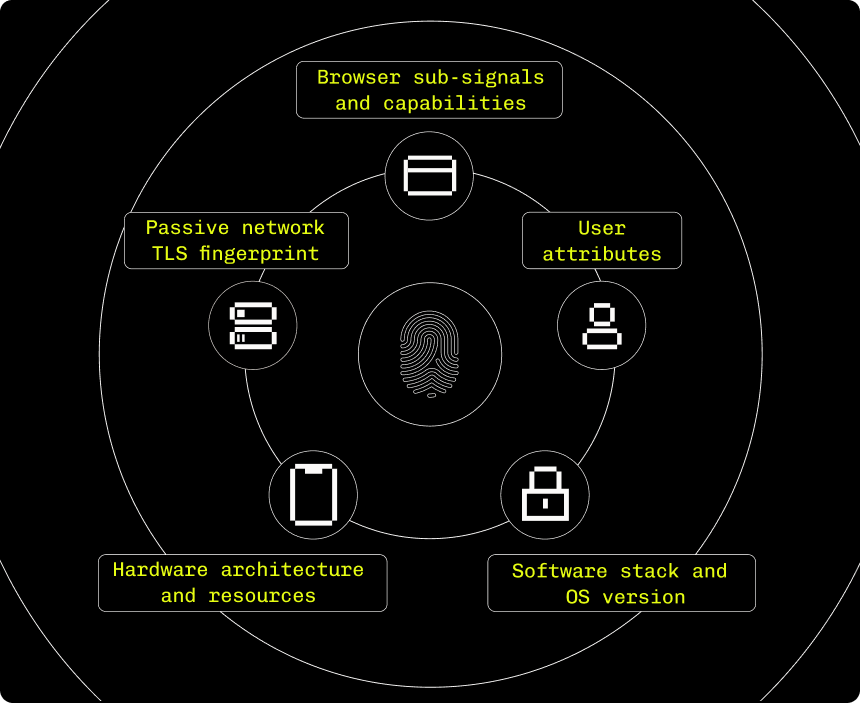
The world's most powerful fingerprint
Device intelligence built on a powerful combination of deterministic signals and supervised machine learning providing a more accurate solution than Fingerprint.

Hardened against the most sophisticated attackers
In a recent head-to-head analysis between Stytch's device fingerprinting solution and Fingerprint Pro, Stytch offered superior tamper resistance.
What engineering teams are saying
Stytch’s Fraud & Risk tools give us granular visibility into attempted attacks and effortlessly prevent a range of bot and fraud attempts.
Stytch’s Fraud & Risk tools give us granular visibility into attempted attacks and effortlessly prevent a range of bot and fraud attempts.
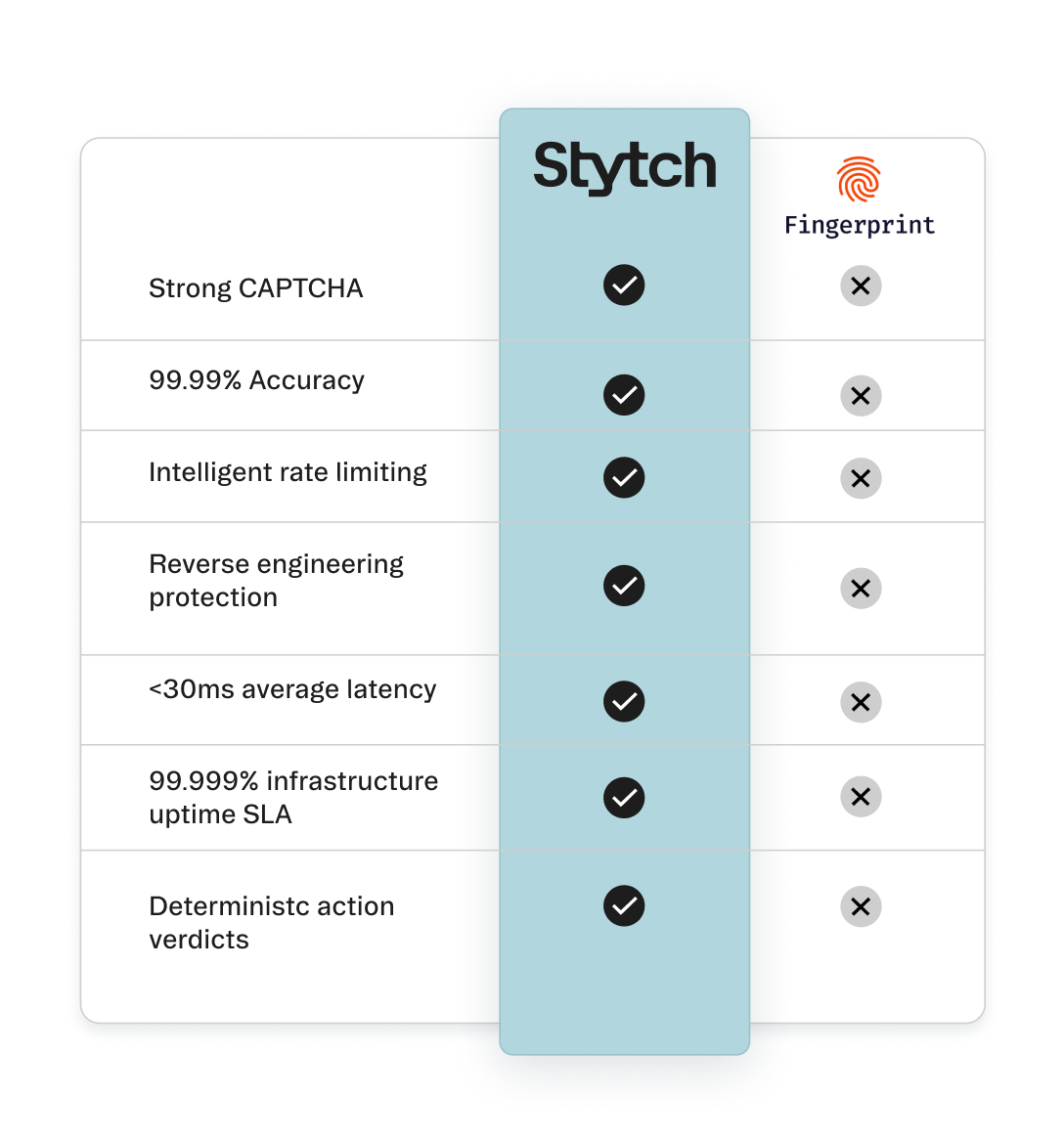
Detailed feature comparison
Fraud and Risk Prevention | ||
|---|---|---|
Bot detection & prevention via Device Fingerprinting | ||
Bot detection & prevention via Device Fingerprinting | Supported | Supported |
Strong CAPTCHA that enforces the identity of person solving | ||
Strong CAPTCHA that enforces the identity of person solving | Supported | Not supported |
99.99% Bot detection accuracy | ||
99.99% Bot detection accuracy | Supported | No guarantees on accuracy |
<100ms Latency user evaluation | ||
<100ms Latency user evaluation | Supported | No guarantee on latency, often exceeding 800ms |
Intelligent rate limiting | ||
Intelligent rate limiting | Supported | Not supported |
Reverse engineering protection and preserves user privacy | ||
Reverse engineering protection and preserves user privacy | Supported | Not supported |
ML-powered device detection | ||
ML-powered device detection | Supported | Supported |
Ready to switch to Stytch?
We have a lot of migration experience – from Cognito, Firebase, Auth0, in-house, you name it – and we’re here to help make your switch to Stytch as seamless as possible.