Overview
Device Fingerprinting (DFP) collects and interprets various attributes of a user’s device to help you prevent fraud, reduce risk, and improve UX for your real users. Here are some examples of device attributes:- Browser type
- Screen size
- Operating system
- Time zone
- IP address and related geographical data (city, region or state, country)
Stytch fraud prevention framework
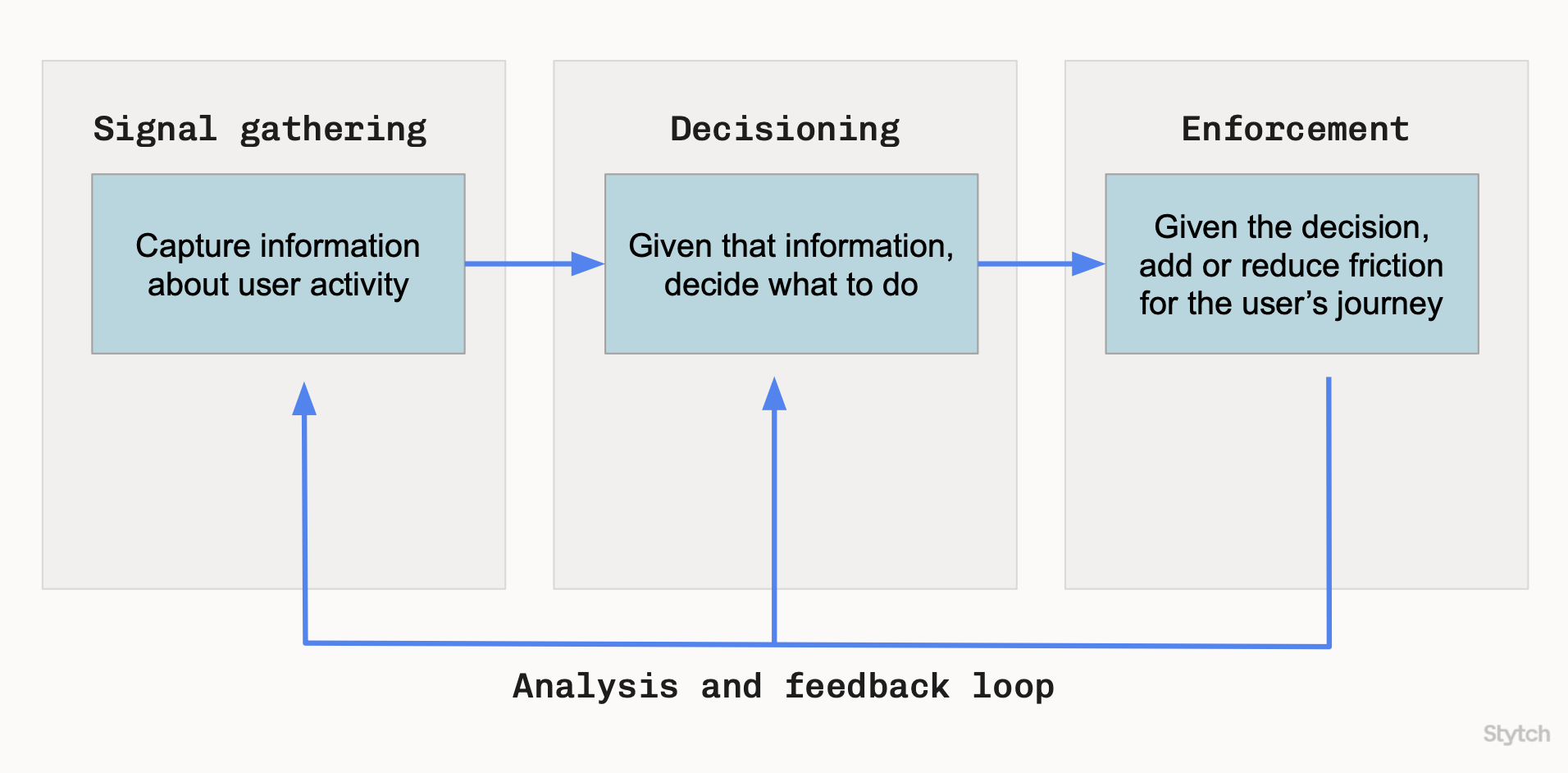
At a high level, Stytch thinks about fraud prevention in four main areas:- Signal gathering: Capture information about user activity.
- Decisioning: Given that information, decide what to do.
- Enforcement: Given the decision, add or reduce friction in the user’s journey.
- Analysis and feedback loop: Observe, iterate, and improve detection and controls based on real-world outcomes.
Features & benefits
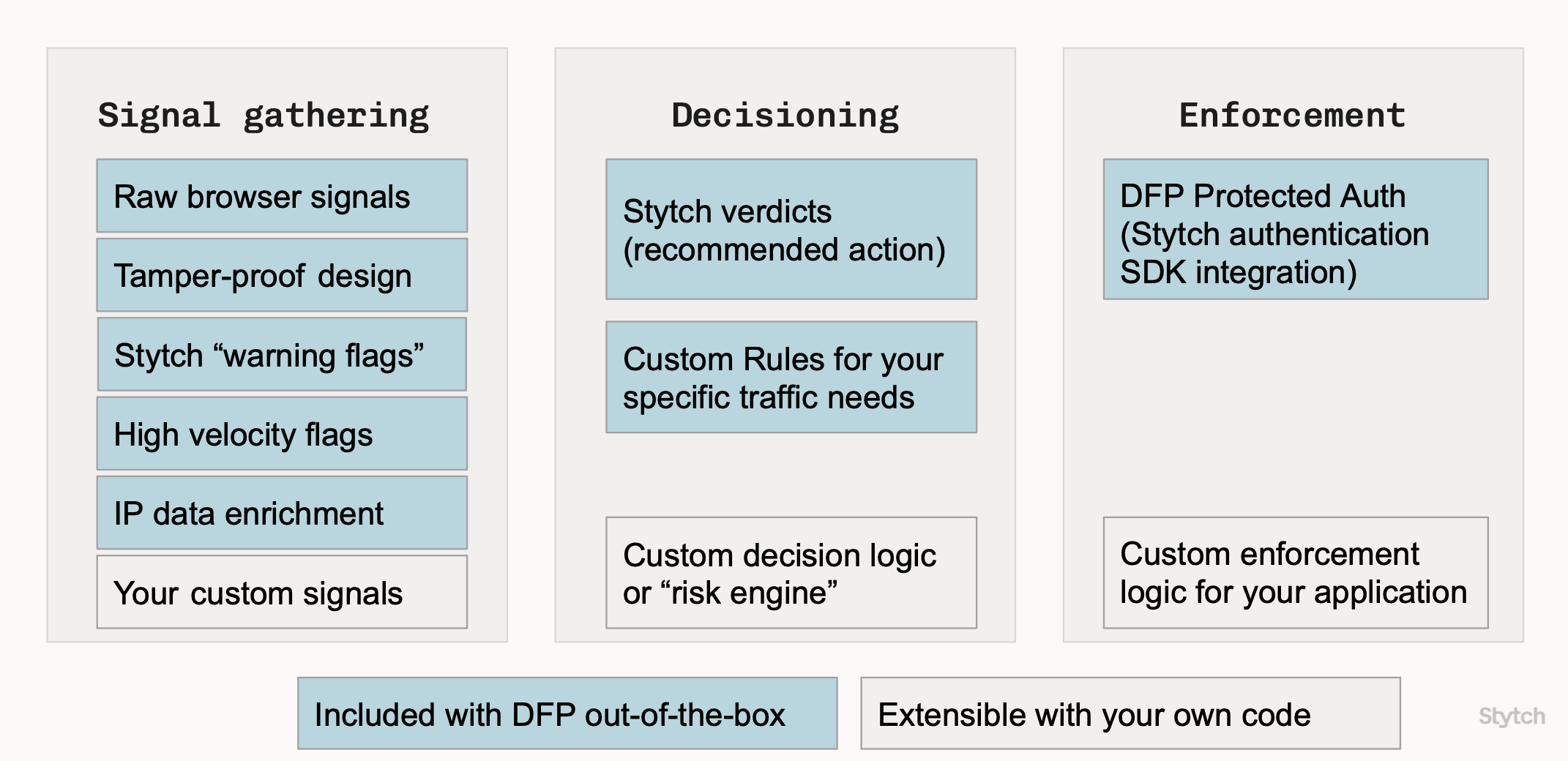
Verdicts
Clear action recommendations (ALLOW, BLOCK, CHALLENGE) rather than opaque floating-point risk scores along with:
- Warning flags about automated or deceptive behavior, like headless browser automation or user agent spoofing.
- High velocity flags with Intelligent Rate Limiting.
Deterministically-generated fingerprints
Aggregations of device signals that remain stable across incognito browsing, webviews, VPNs, changes to user agent or IP addresses, and more.Customizable rules
Tailored decisioning rules for your own application needs.Tamper-resistant design
Including encryption, obfuscation, and proprietary tamper detection.Flexible integration
You can use Stytch Device Fingerprinting as a standalone fraud and risk solution, or integrate with your existing signal gathering, decisioning engine, and enforcement logic.Integrating Device Fingerprinting
If you’re using Stytch for authentication already, you can turn on Protected Auth to start protecting your sign-ups and logins immediately. Otherwise, you can integrate with the Device Fingerprinting API directly.How it works
At its core, Stytch Device Fingerprinting requires two integration points: a client-side Javascript library that gathers signals, and a backend API that interprets them. The Javascript library calls a WebAssembly binary that gathers and sends signals to the Stytch backend for processing. The Stytch backend will return a Telemetry ID. When you want to make a decision about that user, call the Lookup API with the Telemetry ID. The API will return Stytch’s view of the user, including signals, fingerprints, warning flags, and verdict. Now, you can decide how to respond to the user’s request and enforce your decision.Next steps
Get started with Protected Auth
Enable Protected Auth with no code changes.
Get started with the API
Integrate with the Device Fingerprinting API.
Want to try Stytch Device Fingerprinting?
Find out why Stytch’s device intelligence is trusted by Calendly, Replit, and many more.

