Overview
This guide shows you how to set up Device Fingerprinting using the API. By the end, you’ll have:- Added Device Fingerprinting to your application.
- Wired up a JS event to call
GetTelemetryID(). - Called the
fingerprint.lookup()endpoint. - Collected fingerprint data to store.
- Analyzed Stytch’s verdict and recommended action.
Prerequisites
- An existing Stytch B2B or Consumer project in the Dashboard.
- The
project_id,public_token, andsecretfor your project’s Test environment. These can be found under your project’s Project ID & API keys section in the Dashboard. - Device Fingerprinting enabled for your project.
- If you don’t have Device Fingerprinting enabled, you can request access here.
Estimated time required: 1 hour
Get started
Add the Device Fingerprinting script to your app
-
To start, add the following script tag into the
HEADorBODYof your app’s HTML file: - Once the HTML page is live in your app, every client that loads the page will fetch a copy of the Device Fingerprinting bundle.
Create a JavaScript event handler to call GetTelemetryID()
- Call
GetTelemetryID()with your project’spublic_tokenwhen the client triggers a particular event or accesses a protected resource. - The function will return a promise that resolves to a Telemetry ID once the fingerprinting step is complete.
- Once you’ve extracted the Telemetry ID, send it to your backend or middleware as an X-header or URL paramater.
onClick() event handler to a login endpoint:Call Fingerprint Lookup for recommended actions
-
Extract the
telemetry_idfrom your backend, middleware, or wherever you sent the request from Step 2. -
Call the
fingerprint.lookup()endpoint and pass in thetelemetry_idto pull the data and analyze the fingerprints:This API call requires a basic auth header ofPROJECT_IDandSECRET, which can be found in the Dashboard. -
After a successful lookup call, the response should look like:
Response 200
- You can store and log this response to collect your fingerprint data.
Review recommended actions for decisioning
In the response, there is a
verdict object with a recommended action for you to take against the client. There are three possible recommended actions:ALLOW: A known valid device grouping or device profile that is part of the default set of known allowed devices by Stytch. This grouping is made up of mostly verified device profiles that match the fingerprint characteristics of known or authentic origins.BLOCK: A known bad or malicious device profile that is undesirable and should be blocked from completing the privileged action in question.CHALLENGE: An unknown or potentially malicious device that should be put through increased friction such as multi-factor authentication or other forms of extended user verification before allowing the privileged action to proceed.
Our recommended actions are based on proprietary fingerprinting and device classification processes.
Viewing lookup results and activity
You can see the results of your lookups in the Dashboard: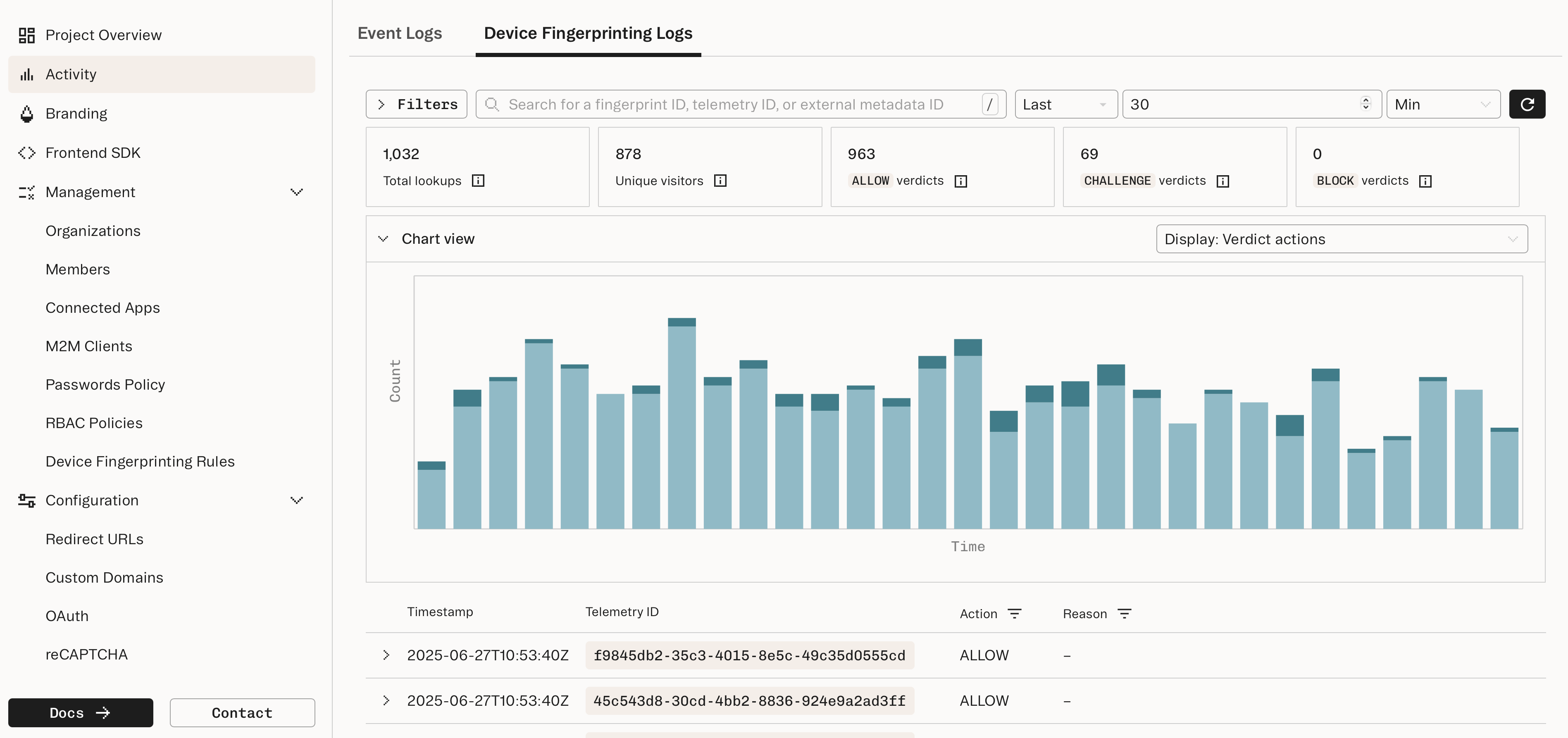

Next steps
Want to try Stytch Device Fingerprinting?
Find out why Stytch’s device intelligence is trusted by Calendly, Replit, and many more.

