Passwordless authentication
It’s also possible to pass app store reviews while offering exclusively passwordless authentication methods.Email-based authentication
For email-based authentication methods, this can generally be accomplished by leaving a note for the app store reviewer describing how they can use their own email address to log in. The exact wording will depend on the specific authentication products that you offer in your application.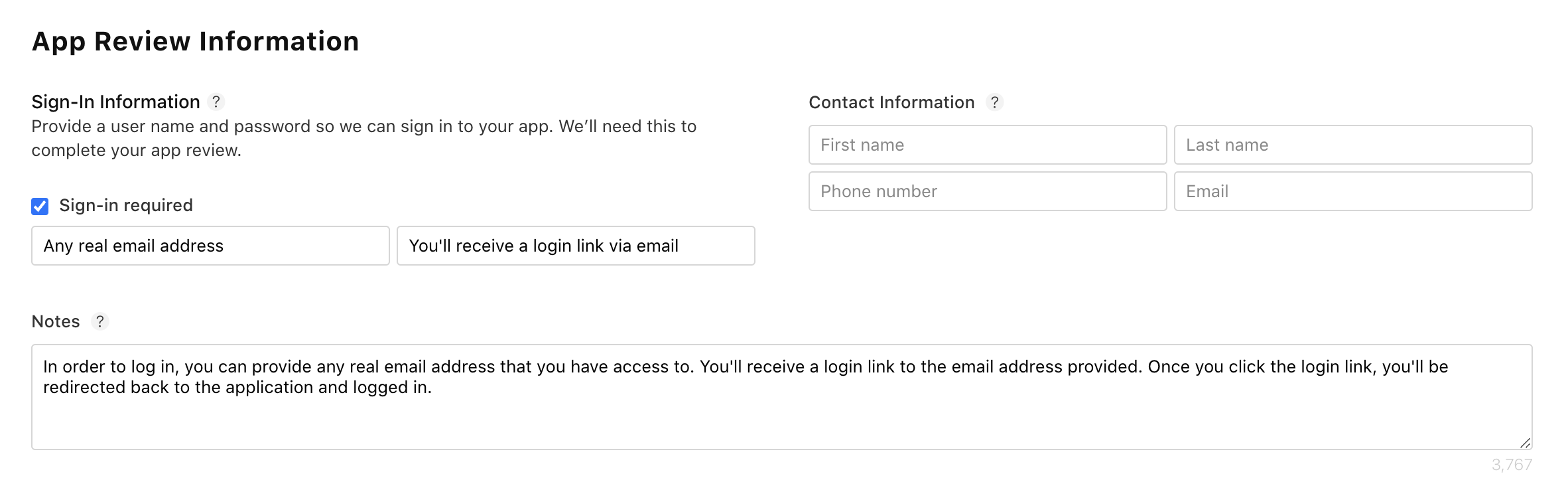
Phone number-based authentication
For phone number-based authentication methods, reviewers are sometimes willing to use their own phone numbers in order to authenticate as well. However, if your application is rejected because the reviewer was not willing to use their own phone number, we generally recommend the following strategy as a backup:- Set up a programmable SMS inbox via a service like Twilio or Mailosaur.
- Forward OTP codes sent to the programmable inbox to a Google Sheet (or other similar shareable resource). Twilio provides a helpful resource demonstrating how to set this up.
- Include a link to the Google Sheet in your app store review notes, along with the phone number that corresponds to the programmable inbox. That way, app store reviewers can enter the phone number in your app and retrieve the OTP code through the Google Sheet.

