- You are already using other tools or vendors for observability and monitoring purposes.
- You have different retention requirements than the default 30-day retention window Stytch provides.
- You want to set up monitoring and alerting side-by-side to your existing monitoring tooling.
- Streaming to a single destination per project
- Supported destinations are Datadog and Grafana Loki
Configuring streaming
You can configure event log streaming through the Dashboard or our management API. Furthermore, you can enable and disable streaming without having to delete your destination configuration. Note that re-enabling after disabling streaming will not backfill for the length of time it was disabled. Only new event logs will be streamed.Dashboard
Under the Activity tab in the Stytch dashboard, navigate to Stream Settings: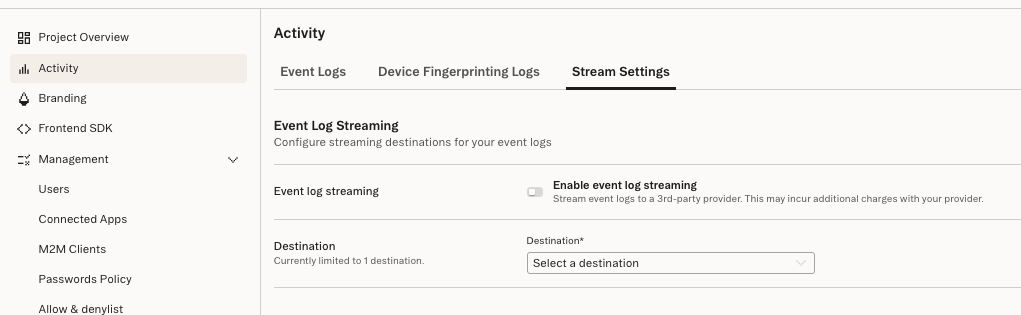
- Select which supported destination type you want to stream logs to
- Fill in the required information. See below for specifics for each destination type.
- Save the changes
Management API (Programmatic Workspace Actions)
This is available via a direct HTTP API, our Go SDK, or our Terraform provider. See the docs on PWA for more information.Destinations
Datadog
For Datadog, you will need the following information:- Datadog Site (Region): This determines the Datadog endpoint Stytch will send logs to. You can find the available options in this list, as well as information to see which one you are using.
- A Datadog API Key: This key allows Stytch to authenticate with Datadog and send event data to your account. The key is typically a 32-character string using the characters 0-9 and a-f only.
Getting a Datadog API Key
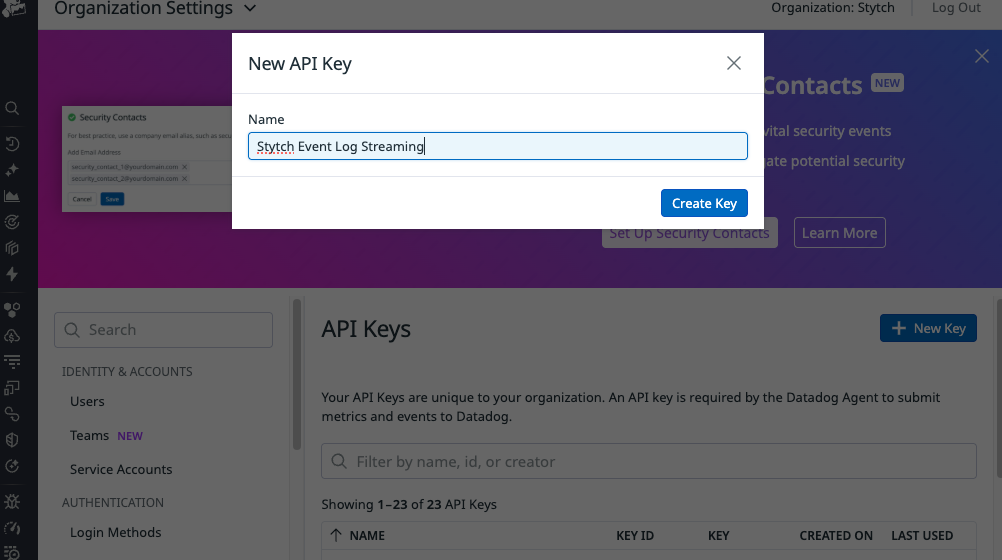
You can create a Datadog API Key so that Stytch can send event logs to your Datadog instance. You can use an existing one if you’d like to, but we recommend creating a new one.- Sign in to your Datadog account
- Navigate to the API Keys page within your Organization Settings
- Click on “New Key”. Give it a name and create the key. Store the key in a safe place
Logs in Datadog
The logs will have the following Datadog-specific metadata:source: stytchservice: stytch.auth
Grafana Loki
Streaming to a Grafana Loki backend is supported. Keep in mind that this must be a Loki backend. We do not support forwarding to Prometheus metrics or any other Grafana-owned service.- Loki HTTP API hostname: This should be the hostname of a Loki log ingestion API endpoint that is accessible to the public internet. Specifically, we’ll be hitting the Loki HTTP API documented on the Grafana Labs Loki HTTP API.
- Your URL for ingestion should look something like:
https://{hostname}/loki/api/v1/push - Note: The https protocol and the endpoint path are static and added by Stytch. These cannot be modified.
- Authentication credentials: We require Basic Auth for authentication. Therefore we need the following information:
usernamepassword
Getting Grafana Loki Credentials (Grafana Cloud)
You’ll need to set up a new access policy and token for your account. Getting a hostname and username- Go to your Grafana Administration Cloud Portal
-
Click on your stack. This will show you the “Manage your stack” page
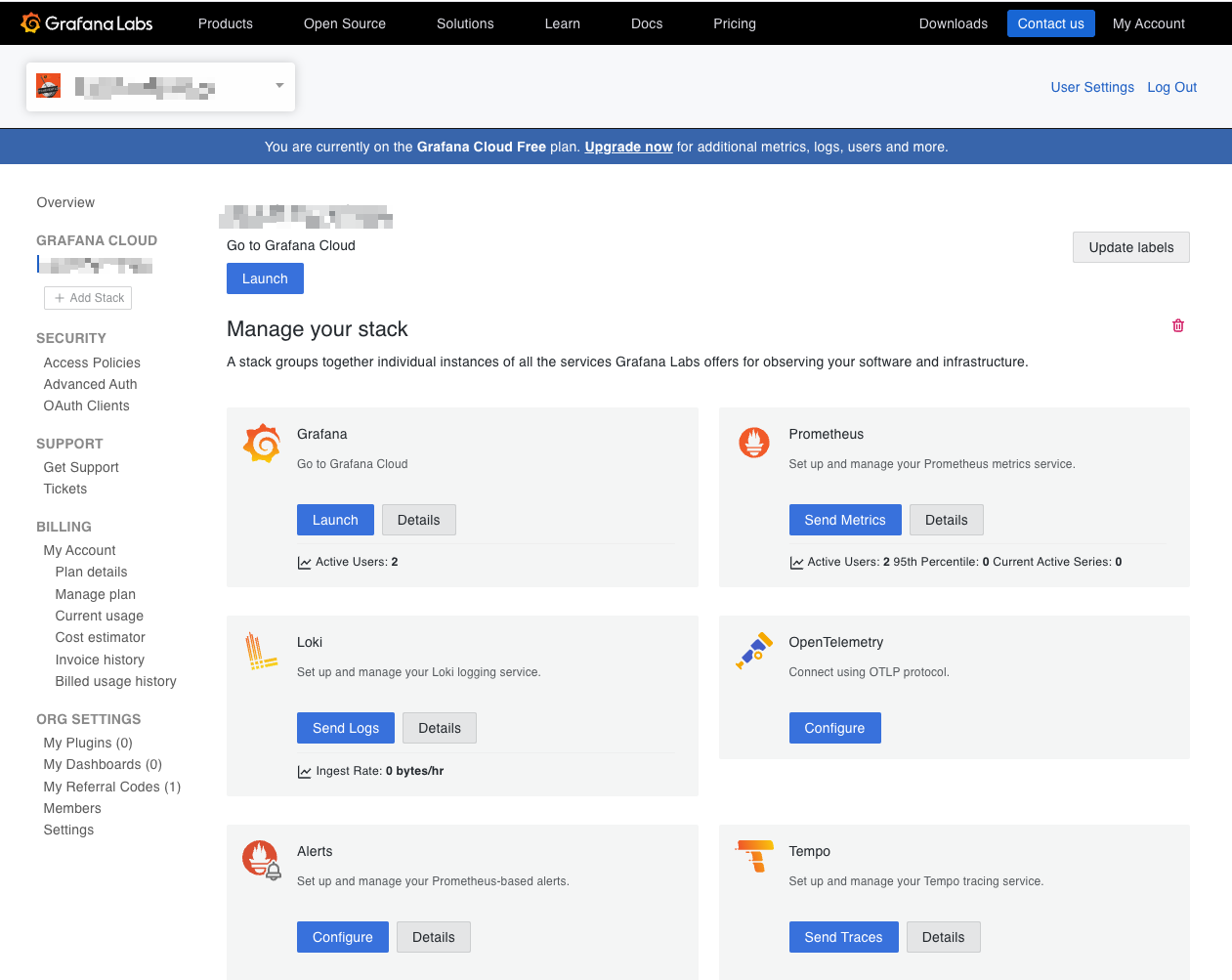
- Click on Loki -> Send Logs
- You will see a box with your auth settings. This will have Name, URL, Basic Auth (checked), User, and Password
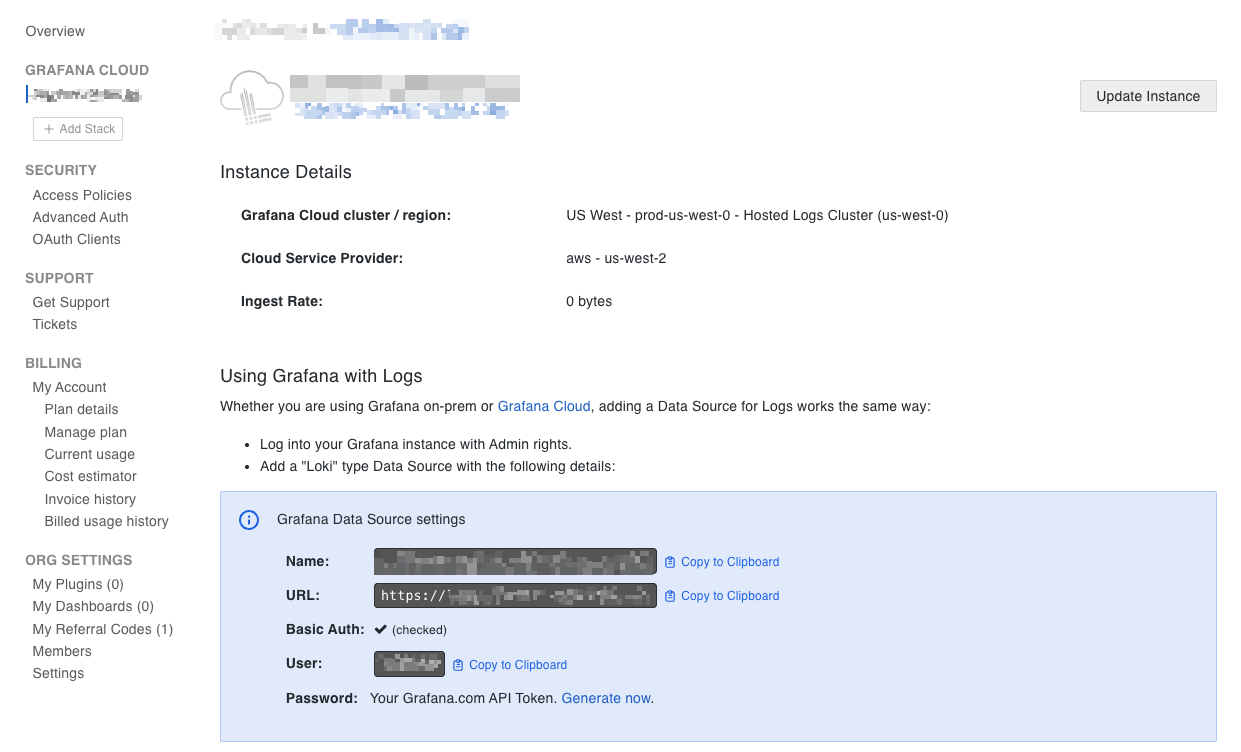
- Your hostname is the URL without the protocol. For example, logs-prod-021.grafana.net
- The username is the string in the User field
-
In the same Grafana Administration Cloud Portal, click on “Access Policies” in the Security section
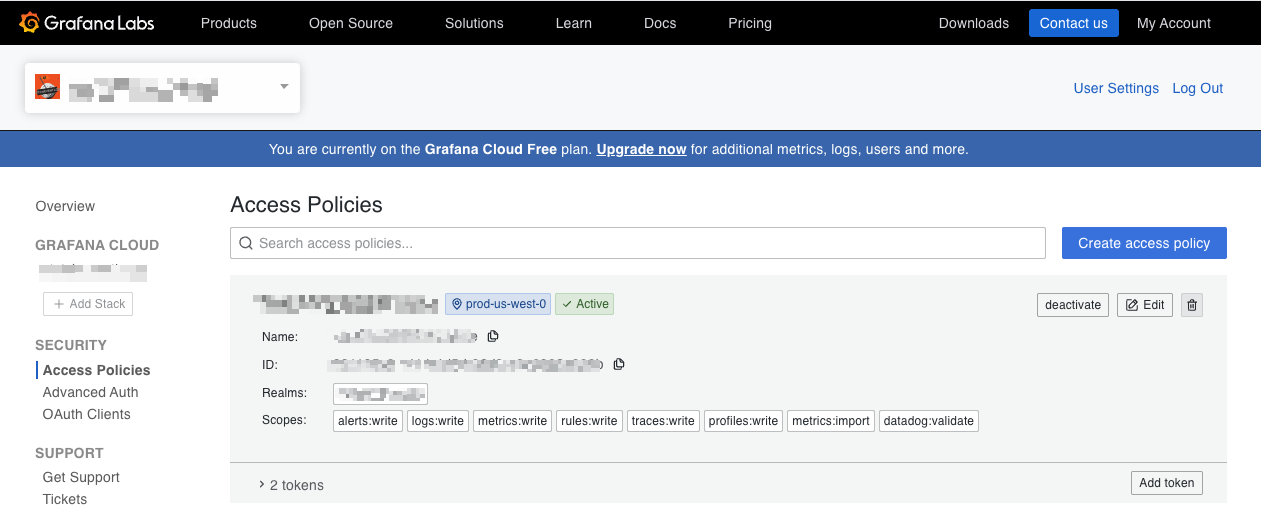
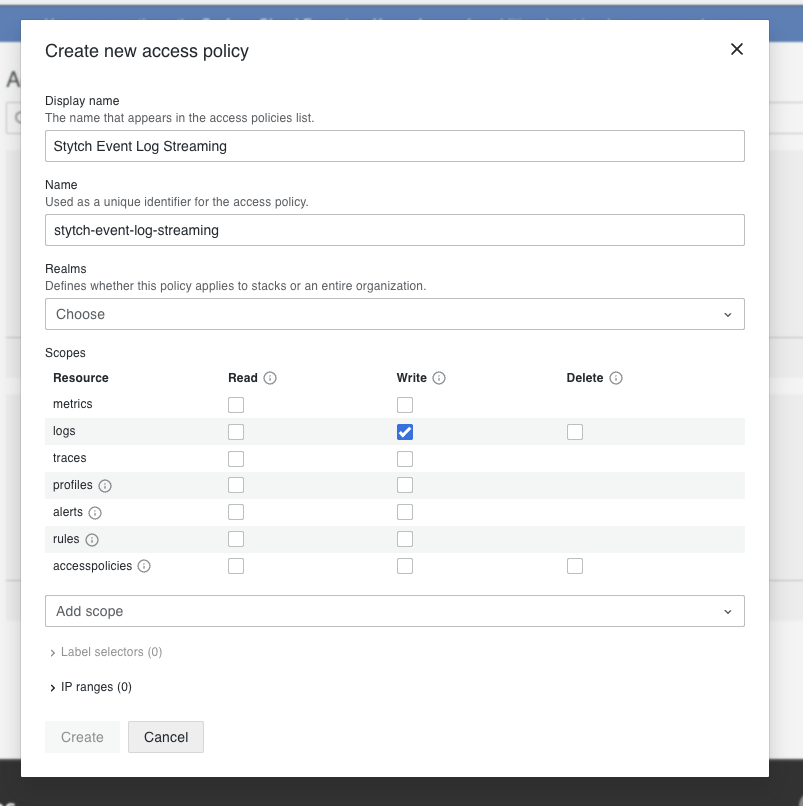
- Create a new access policy or reuse an existing one. Set up the realm and scope that you need for your setup. To forward logs, you need logs:write
- Once created, click on “Add token” and give it a name
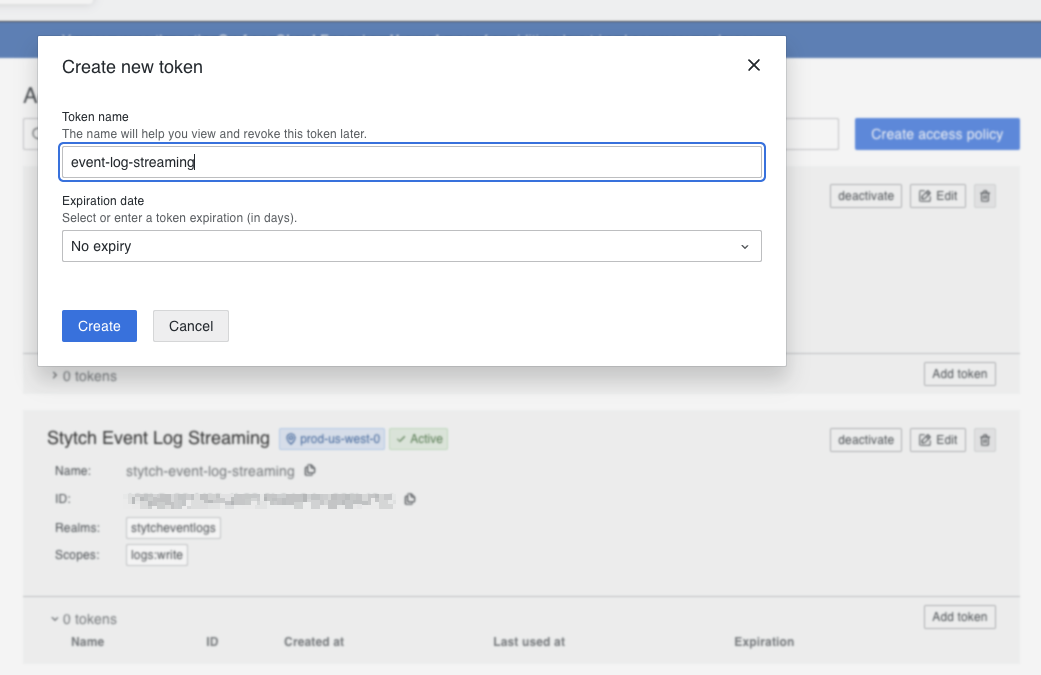
- You will get a token. This is the password used in authentication. Copy this and store it in a safe place.
Logs in Grafana Loki
Logs will be sent in gzipped compressed JSON format, which is supported by Grafana Loki’s HTTP push endpoint. The logs will have 2 additional labels. These can be used to filter for only these logs when querying Loki.- source: stytch
- service_name: stytch.auth

