The most powerful alternative to Auth0
Spend less time on auth
Less code to maintain, stronger bot and fraud protection, and no surprise fees—all with expert support every step of the way.
AuthN and AuthZ infrastructure with unparalleled flexibility
Auth how you want it, with pre-built UI, headless frontend SDKs, and backend APIs and SDKs
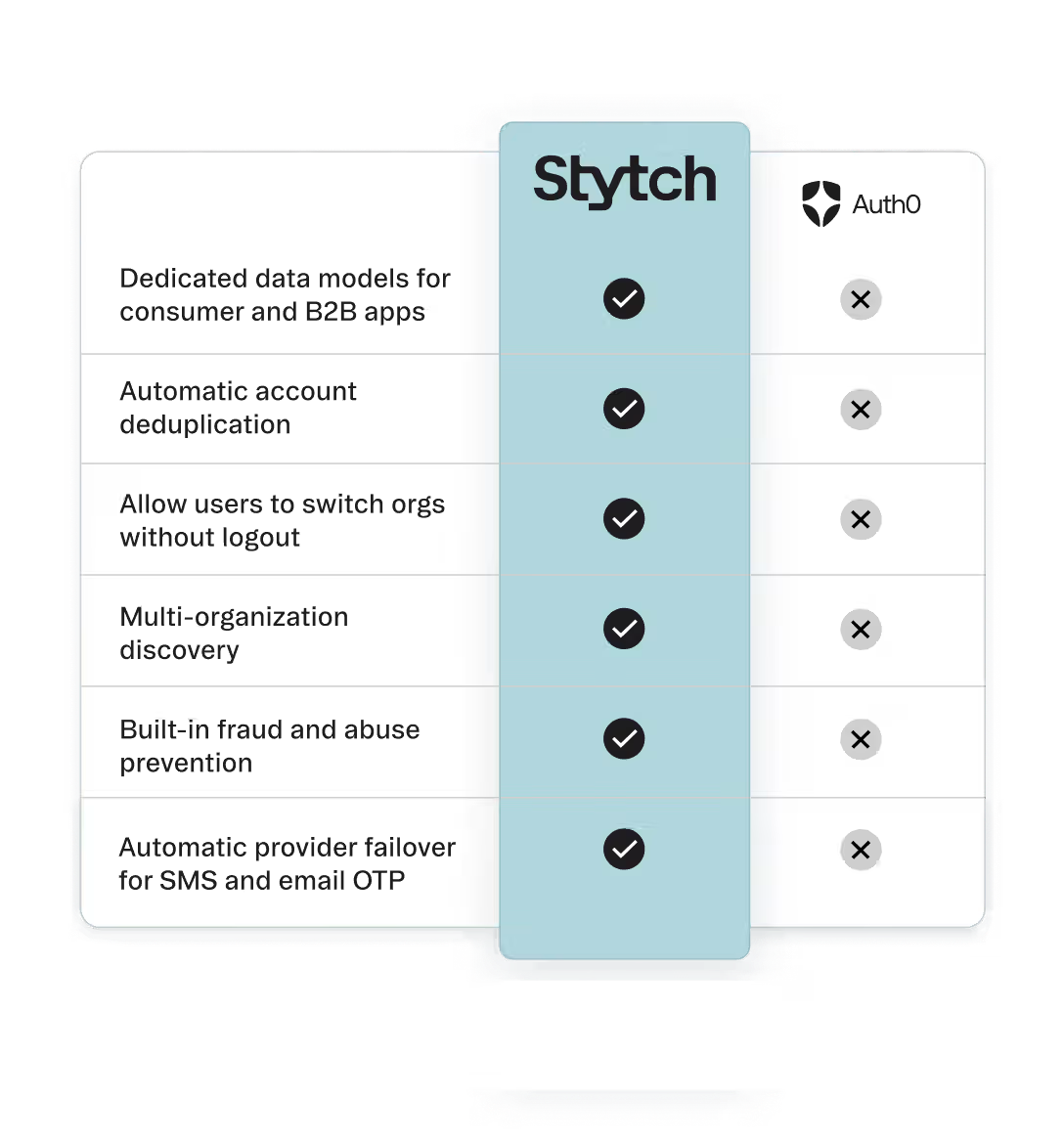
Simplify your codebase with tailored data models for consumer and B2B auth, freeing you from complex middleware
Scale with ease. MFA, SSO, RBAC, and SCIM—your entire auth roadmap, just an API call away
Manage users, organizations, and auth settings directly in your dashboard with an embeddable admin portal
Ship your auth roadmap in less time, with less code
Simple API calls handle the messy corner cases and best practices of auth and security, so you aren’t stuck building and maintaining hundreds of lines of middleware.


Transparent pricing
If you’re using Auth0, you’ve likely experienced steep price hikes when you exceed some obscure usage tier. With Stytch, our pricing is transparent, scales predictably as you grow, and eliminates hidden cost surprises.
No building admin portals from scratch
Unlike Auth0, which forces you to build your own admin portal manually with a collection of API endpoints, Stytch provides a SDK and components to embed an admin portal directly into your application. This interface empowers admins to configure and manage enterprise auth features like SSO within your platform without needing to build it yourself.

Lower friction UX. Higher-converting signups
Faster OAuth integration
Stytch normalizes data models and nomenclature across providers, making OAuth easy and intuitive to integrate.
Account de-duplication
If a user signs up with their email address and later signs in via social login, Stytch automatically links and safely de-duplicates the accounts.
Simplified org discovery and login flow
With opt-in just-in-time provisioning by validated email domain, self serve organization creation and surfacing of pending invites.
Leading fraud and abuse protection, built-in
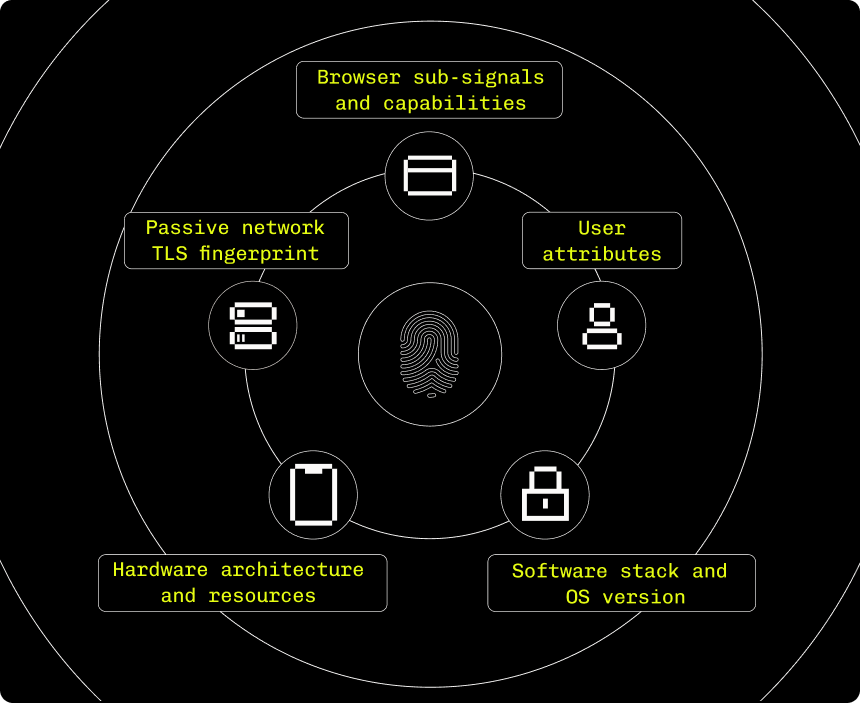
The world's most powerful fingerprint
Device intelligence built on a powerful combination of deterministic signals and supervised machine learning.

Hardened against the most sophisticated attackers
Immutable and resistant to evasion or reverse engineering, all while preserving user privacy.
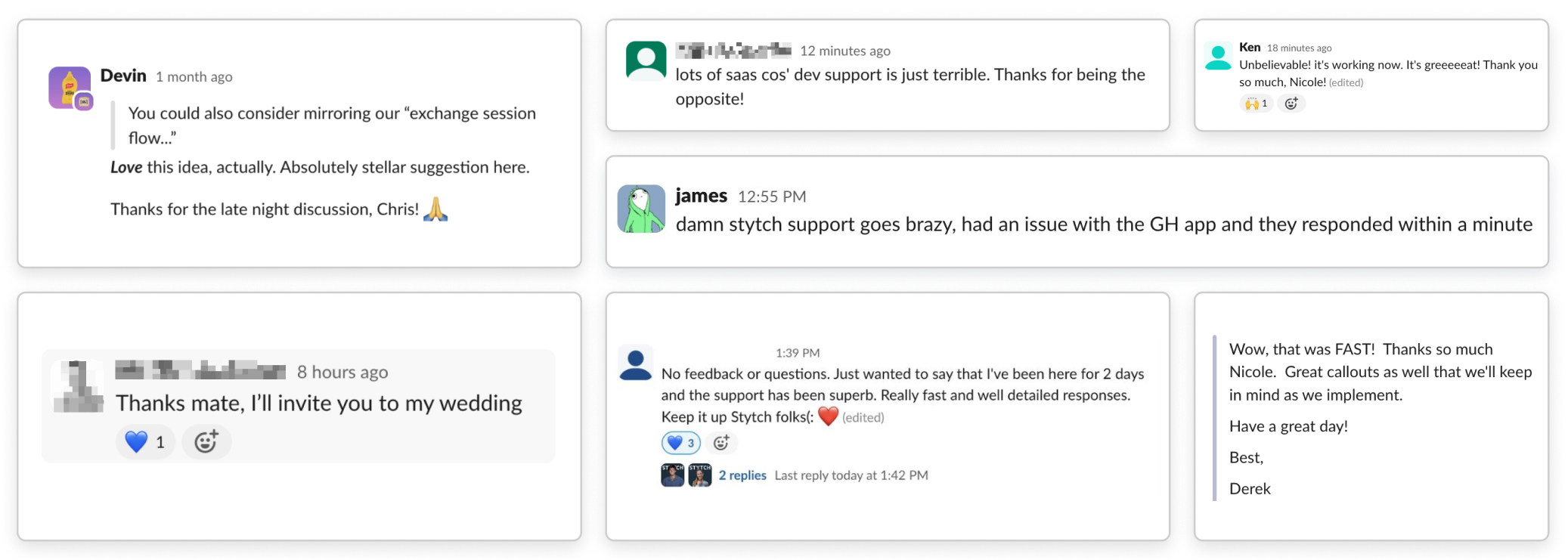
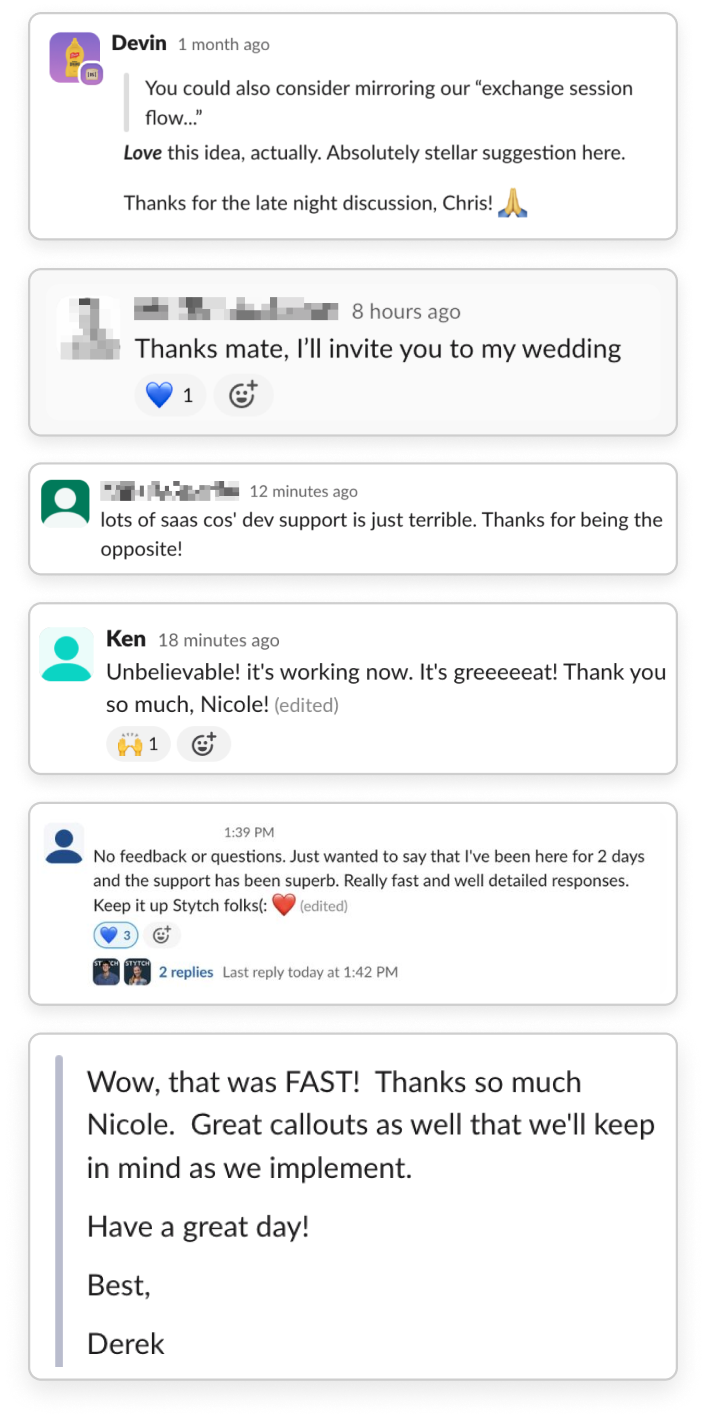
What engineering teams are saying
We migrated tens of millions of users from Auth0 to Stytch in less than a month. It was far and away the easiest migration I’ve ever worked on.
We migrated tens of millions of users from Auth0 to Stytch in less than a month. It was far and away the easiest migration I’ve ever worked on.
Detailed feature comparison
Auth features | ||
|---|---|---|
Email/password login | ||
Email/password login | Supported | Supported |
Password reset flow | ||
Password reset flow | Supported | Supported |
Password breach detection | ||
Password breach detection | Supported | Pro plan required |
One-Time Passcode (OTP) via SMS and Email | ||
One-Time Passcode (OTP) via SMS and Email | Supported | Essential plan required |
One-Time Passcode (OTP), built-in email & SMS with provider failover | ||
One-Time Passcode (OTP), built-in email & SMS with provider failover | Supported | Must bring your own provider. No failover provided. |
Email magic link | ||
Email magic link | Supported | Essential plan required |
Embeddable magic links | ||
Embeddable magic links | Supported | Not supported |
Smart email magic links with passcode delivery protection | ||
Smart email magic links with passcode delivery protection | Supported | Not supported |
Social OAuth, support across major identity providers | ||
Social OAuth, support across major identity providers | Supported | Supported |
Social OAuth, Built-in support for Google One-Tap | ||
Social OAuth, Built-in support for Google One-Tap | Supported | Not supported |
Native mobile biometrics | ||
Native mobile biometrics | Supported across iOS, Android, and React Native SDKs | Not supported |
WebAuthn | ||
WebAuthn | Supported | Supported |
Time-Based OTP (authenticator apps) | ||
Time-Based OTP (authenticator apps) | Supported | Enterprise plan required |
OIDC & SAML SSO | ||
OIDC & SAML SSO | Supported | Supported |
Machine-to-Machine (M2M) | ||
Machine-to-Machine (M2M) | Supported | Supported |
Web3 Login | ||
Web3 Login | Ethereum & Solana login | Requires integrating 3rd party |
Organization Management | ||
Migrate users to either a new auth method (eg. SSO) or IdP | ||
Migrate users to either a new auth method (eg. SSO) or IdP | Supported | Must create duplicate user IDs for every change |
Allow users to change orgs without logging out: Honoring each org's distinct authentication requirements (Auth method + MFA policy) | ||
Allow users to change orgs without logging out: Honoring each org's distinct authentication requirements (Auth method + MFA policy) | Supported | Only allow 1 org per user ID |
Allow users to have different profiles per org | ||
Allow users to have different profiles per org | Supported | Not supported |
New users can self-serve, create new orgs | ||
New users can self-serve, create new orgs | Supported | Not supported |
Per-organization MFA controls | ||
Per-organization MFA controls | Supported | Not supported |
Multi-organization discovery | ||
Multi-organization discovery | Supported | Not supported |
Authorization | ||
SCIM | ||
SCIM | Supported | Supported |
RBAC basic functionality | ||
RBAC basic functionality | Supported | Supported |
RBAC default role assigment at 1st login | ||
RBAC default role assigment at 1st login | Supported | Workaround required |
RBAC implicit many-to-many role assignments | ||
RBAC implicit many-to-many role assignments | Supported | Workaround required |
Operations and Scale | ||
Account deduplication | ||
Account deduplication | Supported | User ID can only be linked to one auth type/connection |
JIT provisioning of new users (e.g. by email domain or sso connection; with per organization controls) | ||
JIT provisioning of new users (e.g. by email domain or sso connection; with per organization controls) | Supported | Lacks even basic controls like restricting to email domain |
Enforce per-Organization auth requirements (e.g. OrgA requires Google OAuth while OrgB requires SSO via their 2 IdPs) | ||
Enforce per-Organization auth requirements (e.g. OrgA requires Google OAuth while OrgB requires SSO via their 2 IdPs) | Supported | Requires additional Organizations product. Can't use a common user ID |
Fraud and Risk Prevention | ||
Device Fingerprinting | ||
Device Fingerprinting | Supported | Not supported |
Device Fingerprinting protected authentication | ||
Device Fingerprinting protected authentication | Supported | Not supported |
Risk-based actions: Allow, Block, Challenge | ||
Risk-based actions: Allow, Block, Challenge | Supported | Not supported |
Captcha | ||
Captcha | Supported | Supported |
Strong CAPTCHA. Bot farm resistant: Prevents CAPTCHA bypass from tools like 2captcha.com & anti-captcha.com | ||
Strong CAPTCHA. Bot farm resistant: Prevents CAPTCHA bypass from tools like 2captcha.com & anti-captcha.com | Supported | Not supported |
Frontend UI | ||
Headless implementation | ||
Headless implementation | Via web & mobile SDKs | Hosted-domain only |
UI whitelabeling | ||
UI whitelabeling | Supported | Not supported |
Full UI control and customization | ||
Full UI control and customization | API access for full customization | Limited without using Auth0 "Rules" |
Prebuilt Admin Portal UI | ||
Prebuilt Admin Portal UI | Supported | Requires in house middleware with APIs |
Ready to try Stytch?
We’re here to help make your onboarding to Stytch as seamless as possible, where our team will provide step-by-step assistance throughout your entire process.