Authentication for consumer apps
Auth exactly the way you want it
Build your auth once, and keep up with all the latest features. Deliver a smooth and secure login experience to your users without any headaches.
Leave your auth roadmap to us
As much control as you want
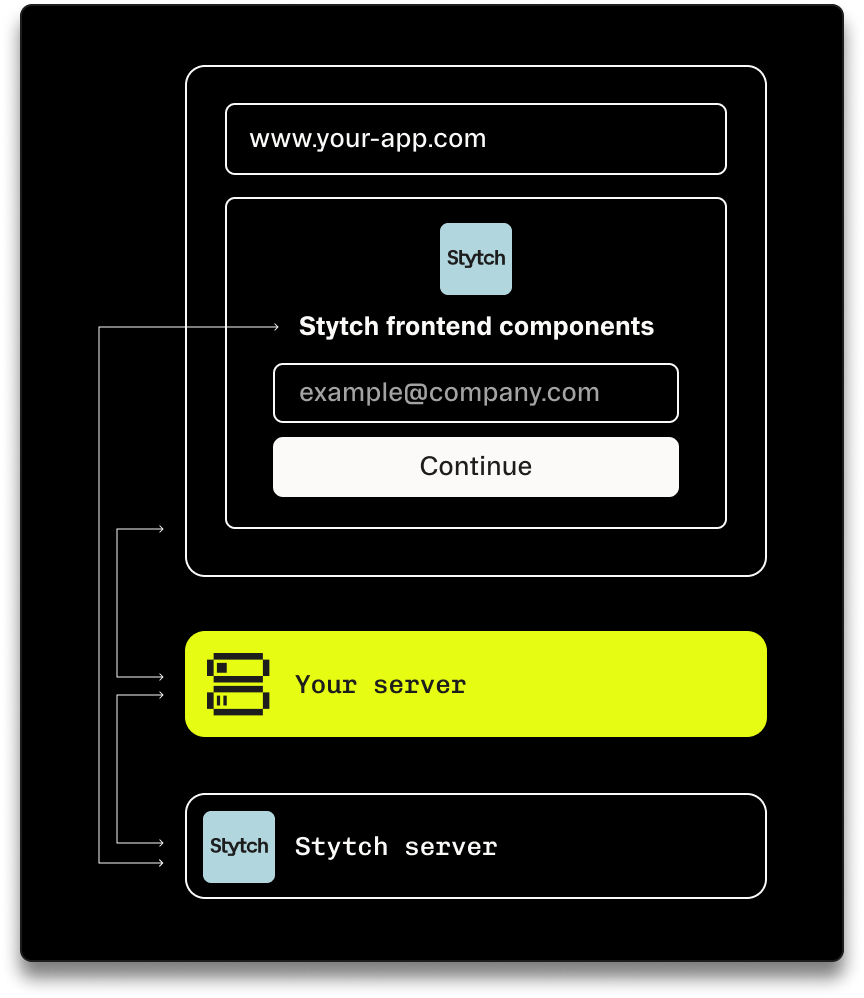
Easily embed ready-to-use login and signup components into your app. Keep users on your own domain, and match your own CSS to align to your brand.
Learn about Stytch pre-built UI

What engineering teams are saying
Partnering with Stytch has really eliminated the pain of having to manage and maintain an immense authentication system. Using a drop-in solution is so much simpler, as is having a team of experts by our side every step of the way.
Partnering with Stytch has really eliminated the pain of having to manage and maintain an immense authentication system. Using a drop-in solution is so much simpler, as is having a team of experts by our side every step of the way.
A more secure and flexible way to add Social SSO
Faster OAuth integration
Stytch normalizes data models and nomenclature across providers, making OAuth easy and intuitive to integrate.
Automatic account deduplication
If a user signs up with their email address and later signs in via social login, Stytch automatically links and safely de-duplicates the accounts.
Google One Tap
Stytch automatically detects a user’s logged-in Chrome or Gmail session for a frictionless login experience.
The Stytch difference
Option for headless SDK and UI whitelabeling | ||
Option for headless SDK and UI whitelabeling | Supported | Not supported |
OTP, built-in email & SMS with provider failover | ||
OTP, built-in email & SMS with provider failover | Supported | Not supported |
Native mobile biometrics | ||
Native mobile biometrics | Supported | Not supported |
Google One Tap support | ||
Google One Tap support | Supported | Not supported |
Automatic account deduplication | ||
Automatic account deduplication | Supported | Not supported |
Web3 login | ||
Web3 login | Supported | Not supported |
Authentication and authorization supercharged with device intelligence
The most advanced fraud and abuse prevention built-in. Protecting your users and application by unlocking powerful authentication features.
Fingerprint protected auth
SDK that protects your application from account takeover (ATO) and related attacks by implementing a Device Fingerprinting check on every authentication request.


Better OTP & 2FA checks
Remove login friction for your users by only requiring multi-factor authentication when your they log in from unrecognized devices.

Better than CAPTCHA
Don't make your users click on stop signs. Invisible bot detection improves UX and conversion by only adding friction to suspicious traffic.

Smart magic links
Reliable delivery of email magic links that work with and pass enterprise-level security link checkers.
