Prerequisites
In order to complete this guide, you’ll need:- A Stytch project. If you don’t have one already, or would like to create a new one, in the Dashboard, click on your existing project name in the top left corner of the Dashboard, click Create Project, and then select B2B Authentication or Consumer Authentication.
- A React or Next.js app authorized to use Stytch frontend SDKs.
- A Relying Party app (the Connected App) that wishes to receive user information from your application.
Integration steps
Implement the React component
To use the Stytch frontend SDK, we have created a component for use in your app:For this flow to succeed, the user must already be logged in to your Stytch-powered app and have an active session, so you’ll want to check for a valid session prior to rendering the component and if the user is not logged in, redirect to the login page with a
<IdentityProvider />for Consumer applications<B2BIdentityProvider />for B2B applications
redirect_uri with a code for the Connected App to complete the flow on its backend.return_to parameter. Learn more about the Authorization Code Flow here.Configure Stytch for the component
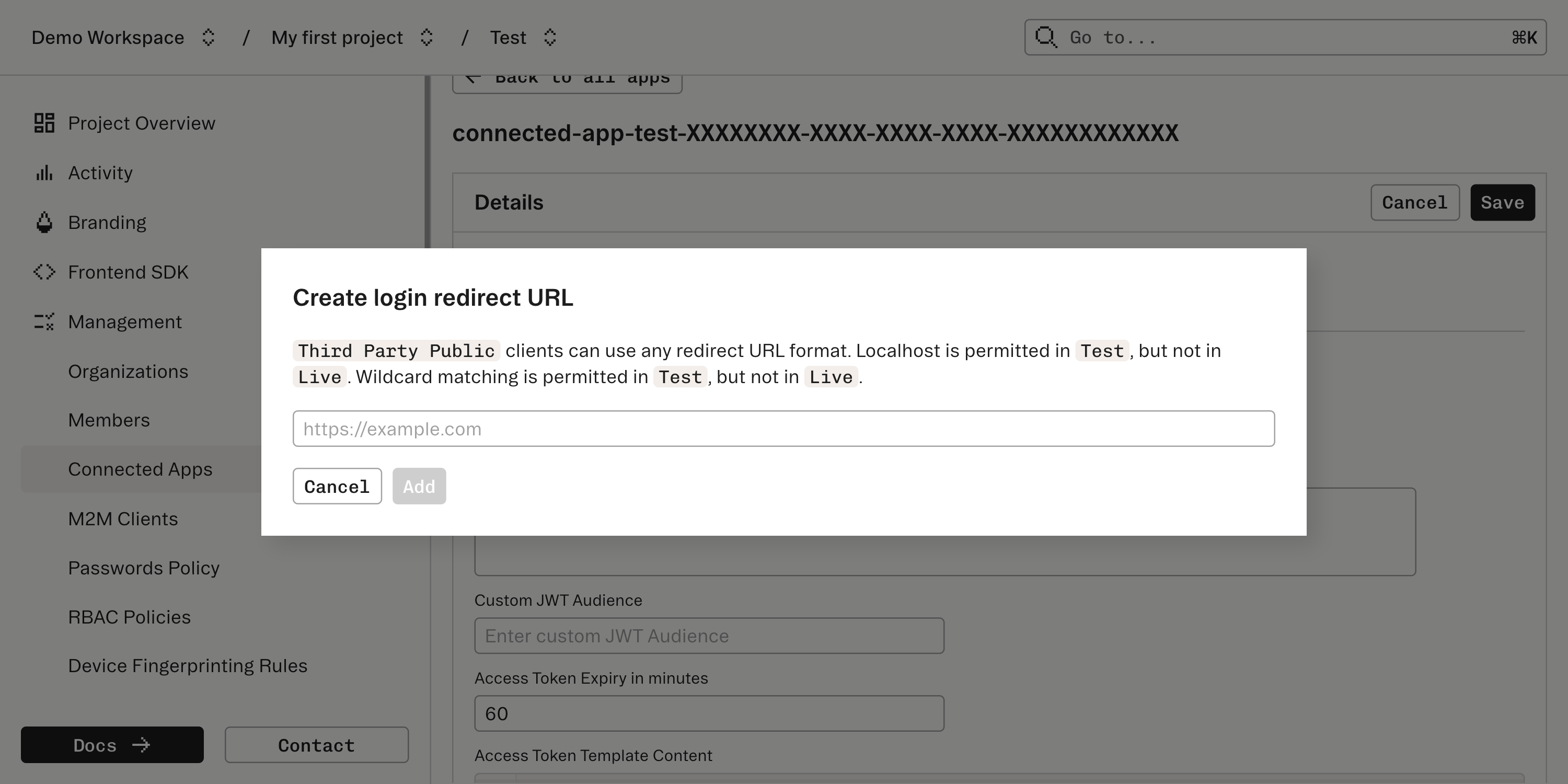
Enter the URL where the component is mounted into the Authorization URL field in the Connected Apps section of the Stytch Dashboard.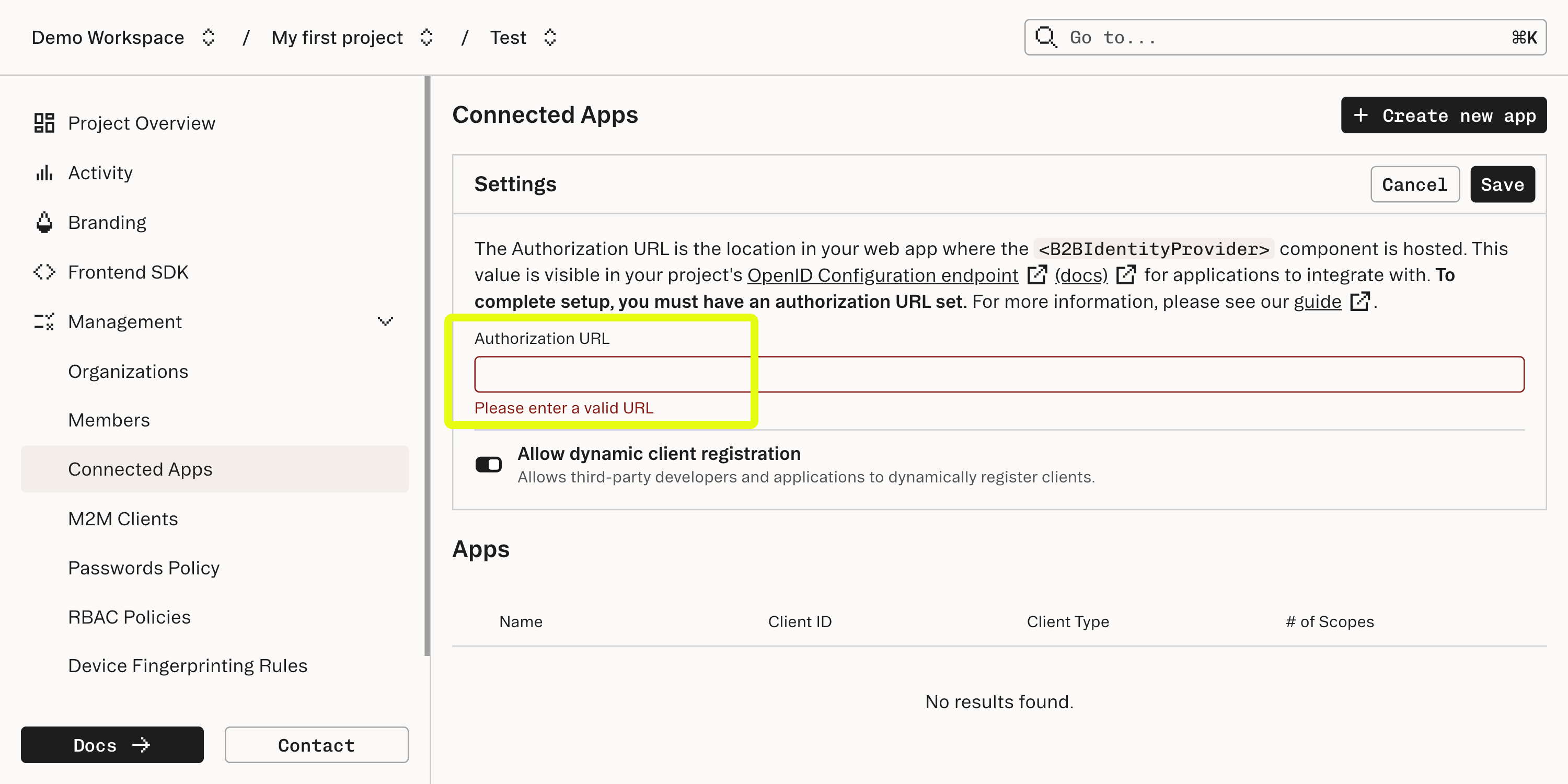

Create a new Connected App in the dashboard
After Stytch handles verification of the user and the application’s ability to access the user’s information, Stytch will issue a redirect. To set this up, each Connected App is also configured in the Connected Apps section of the Dashboard.
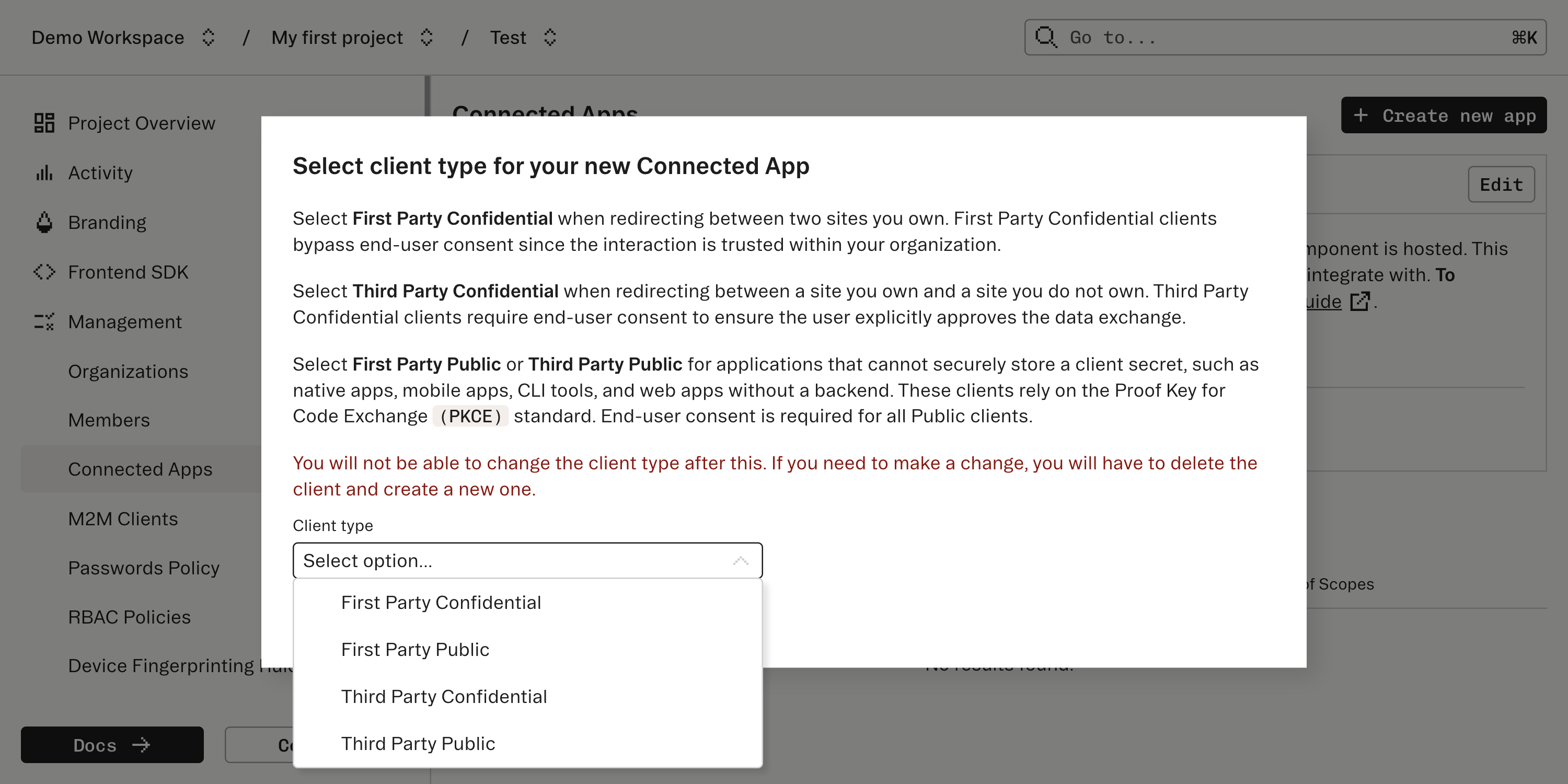
Create a new Connected App and specify what type of user consent and OIDC flow the Connected App should expect. Stytch supports connecting a few types of client apps which vary based on how much user consent is appropriate and specifics of the OIDC flow.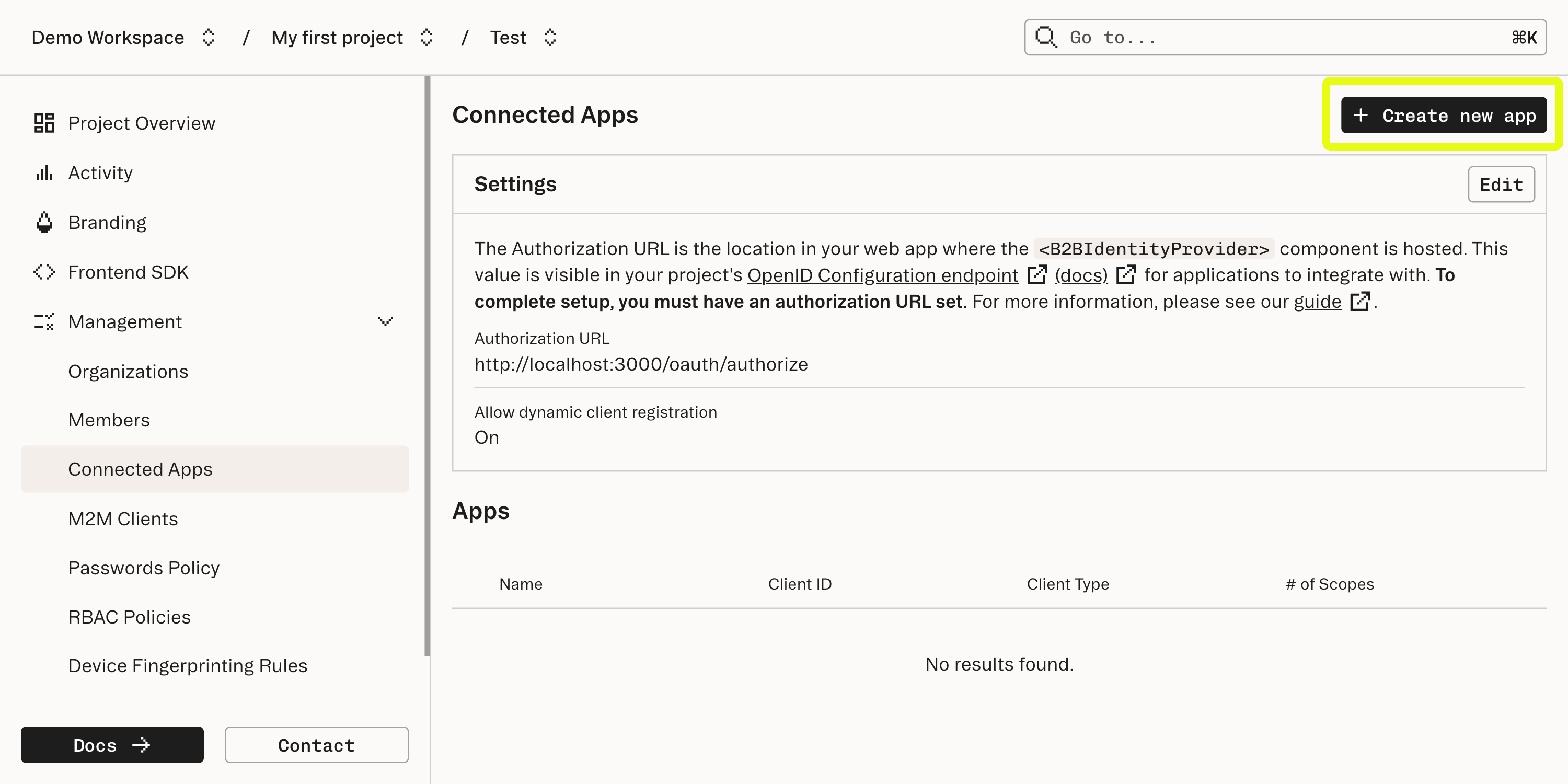
How does the redirect work
How does the redirect work
This redirect is intended to go to a callback URL which should be supplied by the Connected App. The redirect will pass an authorization
code - a short-lived credential that the Connected App will use to complete the authorization flow.

Configure the Connected App
Continue to configure the Connected App. Make sure to take a note of the “Client ID” and the “Client secret” (for confidential apps); these will be needed by the Connecting App to complete the Authorization Code Flow.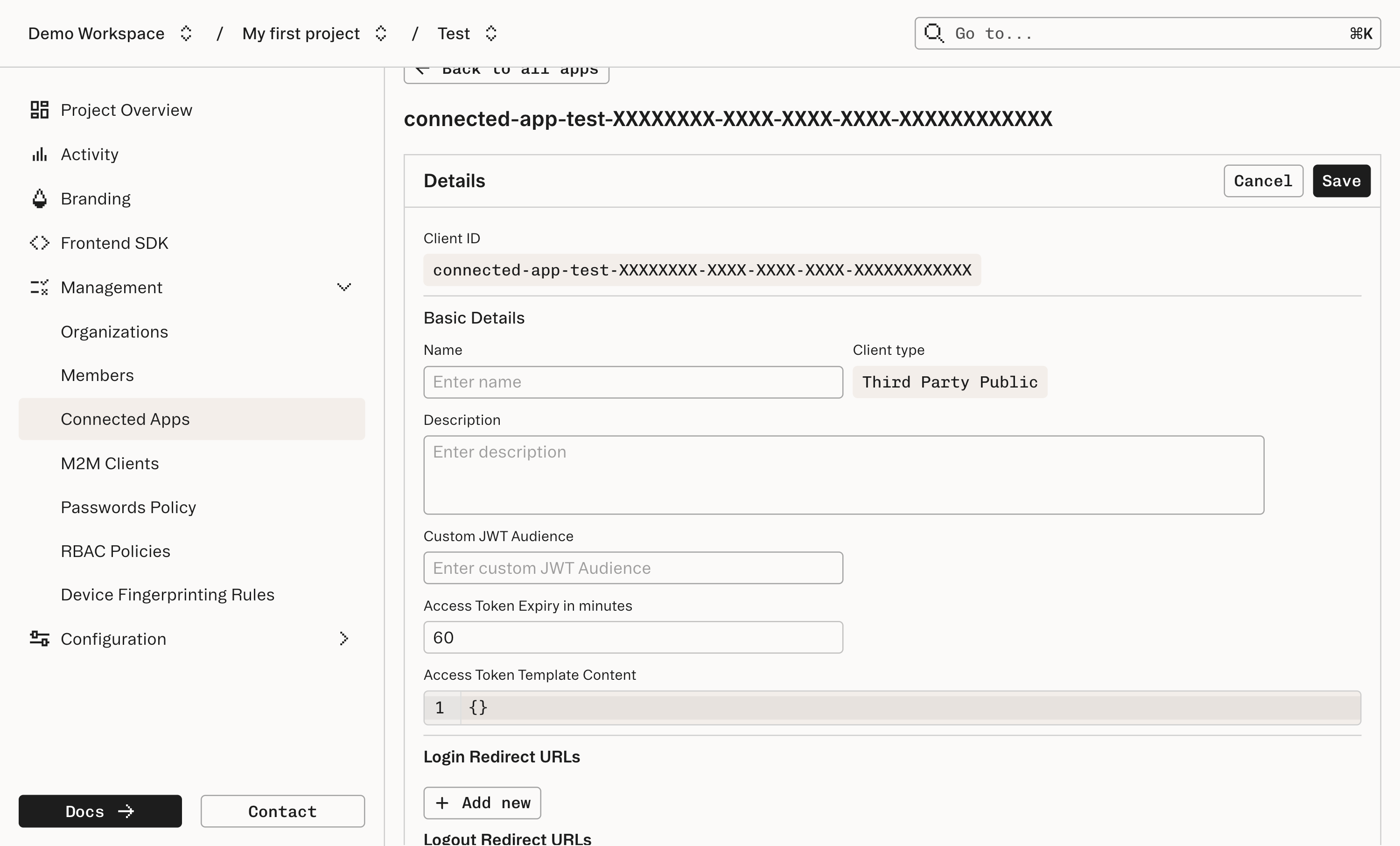


What’s next
Read more about our other offerings:- Implementing your own Connected App
- Public Apps: Authorization Code Flow with PKCE
- Log users in with other commonly used IdPs such as Google and Microsoft ActiveDirectory with OAuth multi-tenant and consumer applications
- Learn more about Machine-to-Machine authentication with M2M for multi-tenant and consumer applications
- Add custom claims to your Connected Apps access tokens using a Custom Claim Template for multi-tenant and consumer applications

