Goals and overview
The business purpose of a free trial is to enable real new users to try your product. This means our goal is to reduce “wasted” free trial resources that are given to abusers, without impacting real users. Using Stytch Device Fingerprinting, you will be able to make better decisions by:- Identifying automated requests, including scripts, bots, and browser automation
- Identifying confirmed repeat users using the Visitor ID
- Identifying suspected repeat users based on fingerprint and traffic patterns
This guide uses the terminology of the Stytch fraud prevention framework. Follow the link to learn more about the framework.
Signal gathering
You should collect and look up a fingerprint at account creation time. See Use the Device Fingerprinting API to add Device Fingerprinting to your application and start collecting data. You should also send external metadata related to the account creation, which will help you correlate the fingerprints with additional application context.Decisioning
Using the fingerprint data and the Stytch verdict, you will be able to classify different kinds of new accounts.1. Identify automated and malicious requests
Device Fingerprinting detects automation tools, including browser automation and programmatic access. By default, any request which is detected as automation receives a verdict with recommended actionBLOCK. Other warning signs like the use of Tor or high-velocity traffic will also receive a BLOCK verdict.
You should block any request that receives a BLOCK verdict from Stytch.
2. Identify confirmed repeat users
In Device Fingerprinting, the Visitor ID is guaranteed to be unique for each user. If you see multiple attempts to create an account that share the same Visitor ID, these accounts are being created from the same device. You should block any request that shares a Visitor ID with earlier requests.3. Identify suspected repeat users
In Device Fingerprinting, the Visitor Fingerprint is a collection of various device characteristics. The Visitor Fingerprint does not change when using incognito, clearing cookies, or using a VPN. However, the Visitor Fingerprint is not guaranteed to be unique. It will be identical between two devices with the same hardware and software configuration. High traffic that shares the same Visitor Fingerprint may be manual abuse: a bad actor repeatedly creating accounts by clicking around on your website. You can still use the Visitor Fingerprint to identify traffic with suspicious characteristics. As a general rule, if 1% of your traffic shares the same Visitor Fingerprint, this is suspicious and worth further investigation. By combining Visitor Fingerprint with other attributes like IP address, you can also get more granular views. These can also be rate-limited or restricted based on your expected traffic. Stytch support can help you determine reasonable rate limits for your traffic level and use case.Enforcement
Now that you have identified different categories of users, you can take action. As described in Enforcement with Device Fingerprinting, you have multiple options. For each of the three categories above, you could:- Immediately block sign-ups and do not create an account.
- Or, restrict the accounts until they pass stricter uniqueness checks, like SMS 2FA phone number or credit card number.
- Or, shadow-ban the account and provide a limited or worse experience.
- Or, allow the creation of accounts, but log the information and use it to periodically perform “ban waves”.
- For sign-ups with a
BLOCKverdict, immediately block the sign-up with a generic error message. - For confirmed repeat users, allow account creation but provide a shadow-banning experience.
- For suspected repeat users, log the information and review regularly. Once you have established baseline activity metrics, you can block more proactively using appropriate rate limits.
Analysis and feedback loop
You can monitor your results through the Device Fingerprinting Dashboard, as well as your own logging and analytics systems.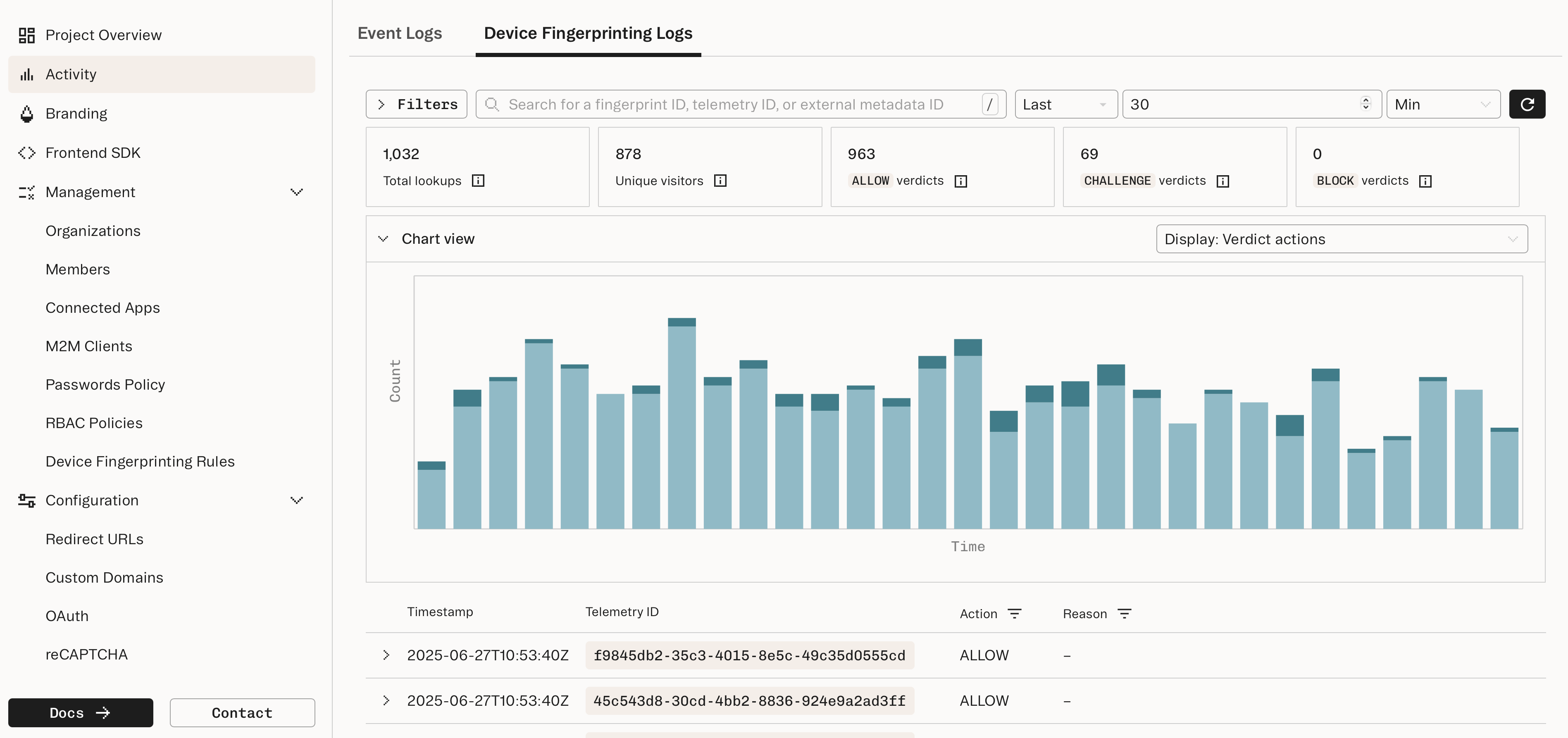
- Track the costs associated with free trial abuse
- Exclude fake users from growth metrics and marketing data
- Observe traffic patterns over time
What’s next?
Learn how to get started with Device Fingerprinting in just a few minutes. If you are interested in stopping free trial abuse, please reach out to Stytch.Want to try Stytch Device Fingerprinting?
Find out why Stytch’s device intelligence is trusted by Calendly, Replit, and many more.

