Back to blog
Passkey authentication: The cure for password dependency?
Auth & identity
Dec 5, 2023
Author: Alex Lawrence
Our traditional reliance on passwords has proven to be one of the most glaring authentication vulnerabilities in modern times. Phishing attacks, password reuse, and credential stuffing are just a few of the risks still raining upon our fragile digital ecosystems with no end in sight.
Enter passkeys. Passkeys are a groundbreaking approach developed by the FIDO Alliance, offering a secure and potentially user-friendly (cross-platform!) alternative to passwords, and marking a significant step towards a ‘passwordless’ future.
Here we’ll cover what passkeys are and some examples of how they work their authentication magic.
What are Passkeys?
At their core, passkeys are biometric-based credentials, created by the WebAuthn standard, that are synced to the cloud, discoverable, require user verification, and work across devices. Passkey authentication has the potential to replace traditional passwords due to its innate security and portability.
The key aspect of passkey authentication is that it does not rely on passwords. Instead, the user’s identity is verified through a cryptographic exchange between the device and an authenticating server.
Authentication via passkeys and biometrics looks something like this:
- Upon selecting the passkey login option on a website or app, the user’s device immediately prompts for biometric authentication, such as a fingerprint scan, facial recognition, or similar alternative such as PIN.
- The user simply provides their biometric input for quick verification, and once authenticated, the passkey automatically logs them into their account, eliminating the need for manual password entry.
Authentication devices can be plug-in hardware like Yubikeys or embedded into a device like a smartphone’s or laptop’s biometric sensor.
Public key cryptography and the cloud
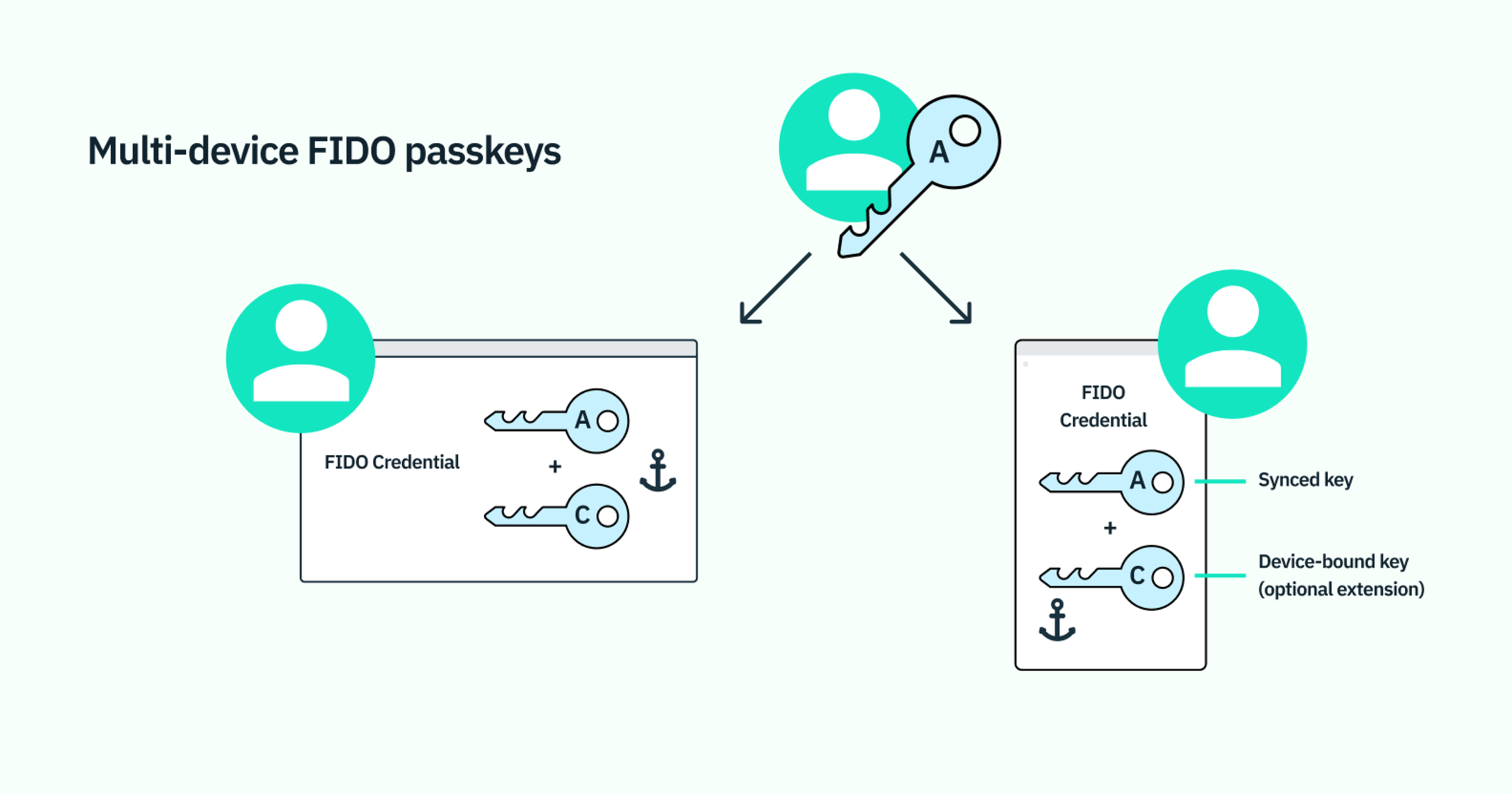
Passkeys use asymmetric public key cryptography to create a unique pair of public and private keys. The unique aspect of passkeys lies in their dual components: the private key, which is securely stored on the user’s device, and the public key, which is registered with the application (such as an online shop). Excitingly, the cloud enables passkeys to be stored and synced across devices and operating systems, unleashing a whole new level of user-friendly authentication with the cloud storing and syncing the user’s private keys.
While challenges remain in broadly scaling the benefits of passkey authentication to diverse end users and hardware, increasing adoption of passkey authentication options by cloud services giants like Microsoft, Google, and Apple are certainly pointing things in a promising direction.
Passwordless authentication with passkeys, step-by-step
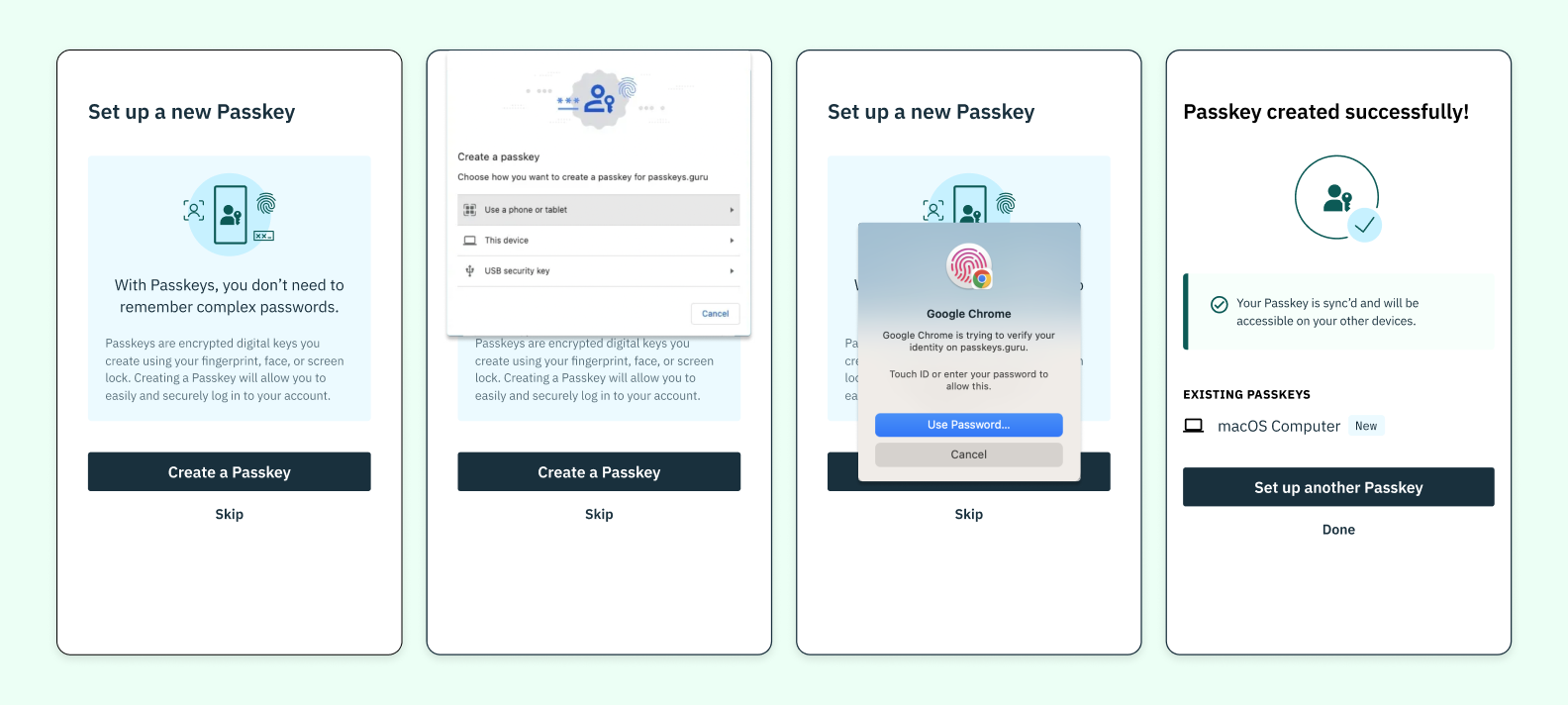
Let’s take a closer look at what passkey authentication looks like across the user journey.
- Account Registration: Passkey authentication begins when a user visits a site and sets up a new account on a platform that supports passkey authentication. The user’s device, be it an Apple device, an Android phone, or any other smart device, generates a new passkey for this account.
- Key Storage: The private key is securely stored on the user’s device, protected by the device’s security measures like Touch ID, facial recognition, or device PIN. Meanwhile, the public key is sent to the service provider’s server .
- Cloud sync: The private key on the device can be synced with cloud platforms like iCloud, Google Cloud, and Microsoft and even credential managers 1Password, enabling its use across multiple devices owned by the user.
- Sign-In Request: When the user attempts to access the service later, the server sends a challenge to the user’s device, initiating the authentication process.
- User Approval: The user approves the sign-in request. This could be through a biometric sensor or a simple approval on the device.
- Responding to the Challenge: The device responds to the server’s challenge using the private key. This process is securely conducted and is invisible to the user.
- Access Granted: The server verifies the response using the public key it has on file and grants the user access to their account.
With so little friction to the user, it’s easy to see why and how passkeys offer a better experience than traditional password-based authentication and even WebAuthn alone, which is bound to a single device.
Keep in mind, however, that a perfect implementation of passkey auth across platforms is not always possible. You may not be able to ensure the same level of cloud syncing or secure user verification across all platforms or devices chosen by your end users. For example, not all devices can handle biometric authentication, leading to a less-than-ideal, more hackable MFA procedure using PINs or patterns rather than the virtually inimitable fingerprint or facial scan.
But that’s OK! For now. Progress is the prize we’ve been waiting for, technology advances rapidly, and even passkey auth in its early stages delivers significant advantages.
Unlike passwords, passkeys are super secure
Passkeys have the power to mitigate common security issues and vulnerabilities to brute force attacks. Now that we’ve spent some time focusing on the UX benefits of passkeys for users, let’s zero in on their security advantages.
The password buster
By design, passkey authentication eliminates the need for users to remember complex passwords, which often leads to password reuse and increases vulnerability. This “password fatigue” phenomenon is a common cause of security breaches. With passkeys, there are no passwords to remember, no sticky notes to be lost, and no password docs accidentally flushed down the digital trash can. This also means there are no passwords to steal — hackers and thieves will find little to feast upon once passkeys go mainstream.
WebAuthn
Passkeys are a form of WebAuthn, which provides an open authentication standard using public key cryptography, eliminating the need for passwords. With WebAuthn, website users can use devices they already own, such as their mobile phones or security keys, for secure and easy authentication. This promotes better security practices while enhancing the user experience (though it does not solve for the multiple device login issue that can hinder UX — that’s where passkeys come in).
WebAuthn was designed with privacy in mind and does not rely on personally identifiable information (PII) for authentication. This means that even if a company’s database is breached, user accounts are still secure as the passkey itself is not linked to any personal information.
With the addition of private key storage in the cloud, passkeys are moving the WebAuthn needle further towards a far more seamless yet equally secure UX across devices and platforms that doesn’t rely on multiple-device authentication.
Want passkeys without the headaches? Switch to Stytch.
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
The benefits of physical devices
One of the primary reasons passkeys are a superior method of authentication is their requirement for physical device proximity. This adds an extra layer of security as it significantly reduces the risk of unauthorized remote access to user accounts. A potential attacker not only needs to know the passkey but also needs physical access to the device, making it exceptionally difficult to get in.
When combined with additional security measures like biometric checks, the likelihood of a security breach dims even further. Passkeys are inherently phishing-resistant, as the authentication process requires physical proximity and often a biometric check, rendering remote phishing attacks far less effective.
In essence, passkeys can provide a multi-factor authentication experience through a single authentication factor, combining two out of three types of user verification: the private key (what you have) and biometric information (what you are). These verification methods are widely recognized as more secure and difficult to hack or forge compared to traditional knowledge-based authentication (what you know).
Cross-platform in practice: progress & challenges
So how will passkeys find their way to the top? Major operating systems and platform/cloud vendors have already started to integrate passkey support, making it increasingly possible to use passkeys across various devices, including mobile phones, tablets, and laptops. But challenges remain.
Let’s cover some markers of progress and remaining hurdles towards achieving a passwordless future.
Synchronization in the cloud
As mentioned, the ability to synchronize passkeys across devices massively raises the bar for user convenience and accessibility. For instance, Apple devices allow passkeys to be synchronized via an iCloud account, ensuring that users can access their accounts from any trusted device. Similarly, Google accounts offer passkey synchronization for Android devices, providing a cohesive experience across the user’s devices.
These features are not yet available for all passkey providers due to the multitude of devices and OSs that users and employees enjoy, and thus may prove challenging for developers to implement universally.
Industry standards and collaboration
To ensure the smooth adoption and interoperability of passkeys, it is crucial that industry-wide standards are established. This includes standardizing the format of passkeys, as well as developing protocols for their storage and transmission. The FIDO (Fast Identity Online) Alliance (of which Stych is a proud member) is working towards these goals, and its efforts have already resulted in the WebAuthn standards. However, widespread adoption of these standards may still take time as different vendors may have varying interpretations or implementations of the standards that support passkeys.
Collaboration may also be challenging due to competitive pressures and differing business objectives. Ensuring the same level of security across various platforms can be resource-intensive and complex. Developers should account for potential vulnerabilities in each platform and create solutions that are effective without compromising the user experience.
Lastly, creating a seamless user experience across all devices and platforms requires extensive testing and may require updates or changes to existing software, which can be time-consuming and costly.
Passkey authentication in practice
When integrating passkeys into your system, two critical considerations should guide your approach:
- Industry-specific security needs: Consider the security demands of your sector and the nature of the data you’re handling. Are you working with sensitive financial data? This, for example, might lead you towards a passkey strategy with less reliance on the cloud for passkey storage, and more deliberate use of hardware or multi-device WebAuth.
- End-user requirements: It’s important to take stock of the common devices and browsers used by your audience. Understanding their preferences for login experiences and authentication methods will help reveal the right auth fit – not too snug, nor too loose.
Simplifying passkey authentication with Stytch
The intricacies of configuring passkeys can be overwhelming when considering specific authenticator types, resident keys, and compatibility across diverse device operating systems. These are technical details that, while important, might be too time-consuming for product developers who need to focus on their primary offerings — but it’s not the end of your passkey journey!
You truly don’t need to be an expert in passkeys to provide a top-notch experience to your users. Our passkeys solution is streamlined and efficient, requiring only two APIs: one for creating passkeys and another for authentication.
To further ease the integration process, we also offer frontend SDKs equipped with ready-to-use UIs. This setup allows for quick implementation without the hassle of dealing with various authenticator types or different device operating systems. We’ve established intelligent defaults so you can easily integrate our solutions and focus on what you do best — developing your core product.
Every company and developer journey in authentication is unique. Whether you’re looking to get started for free or wish to explore our solutions through a demo, we’re here to assist. We’ll handle the complexities of passkey authentication, so you can dedicate your resources to your product.
Get in touch with us today and take the first step towards a more secure, user-friendly authentication system.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.