Back to blog
Stytch User Impersonation: Fast, secure troubleshooting
Product
Feb 22, 2025
Author: Stytch Team
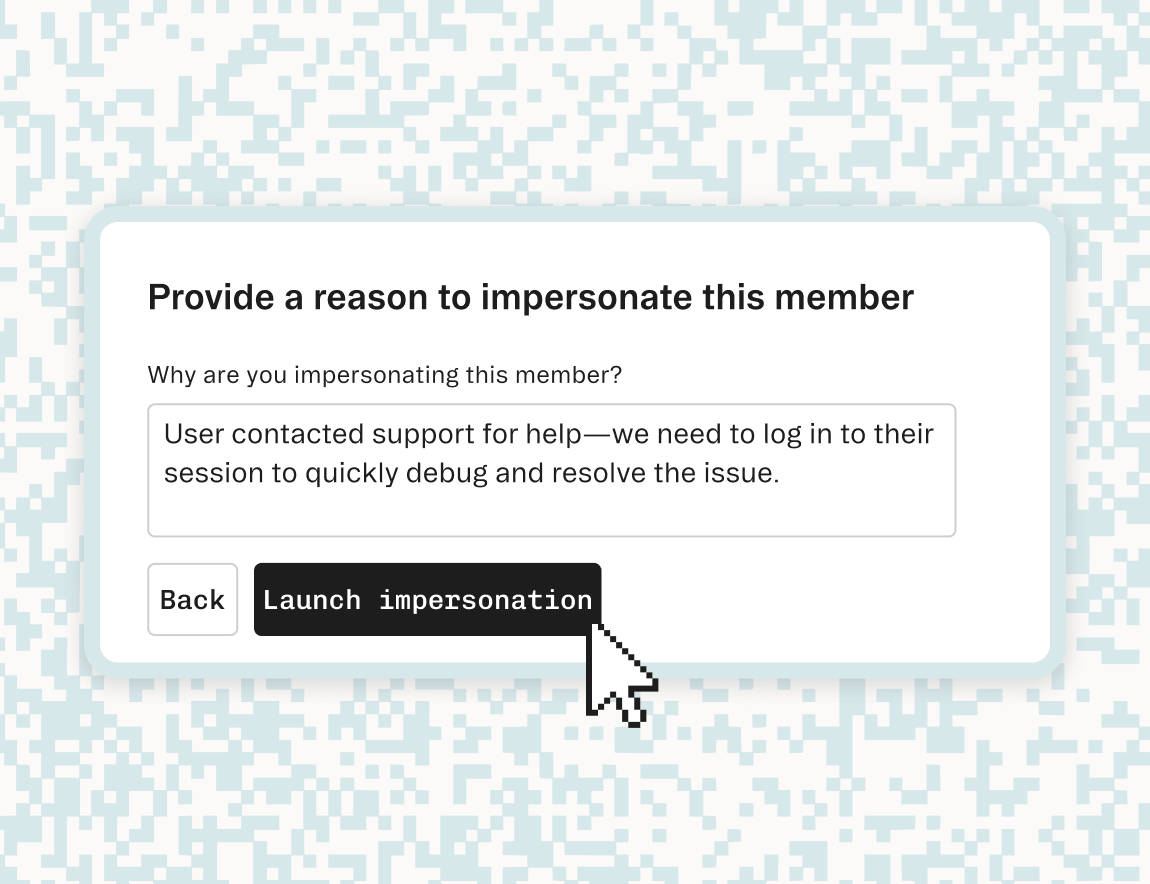
We’re excited to introduce User Impersonation, a feature that lets you log in to your application as a specific end user account to help you troubleshoot and debug securely.
It's often challenging to reproduce complex customer issues, and sharing screenshots only gets you so far — now, with a click, you can securely log in as any user and directly interact with your application as them, giving your support teams a powerful tool for troubleshooting. User Impersonation also comes with granular access controls, including audit logs and a limited session length to ensure you can conduct investigations into bugs with secure safeguards.
User Impersonation is configurable from within the Stytch dashboard, making it straightforward to implement. This feature is now available to all Stytch B2B and B2C customers on their existing plans.
The Fast, Secure Path to Pinpointing User Issues
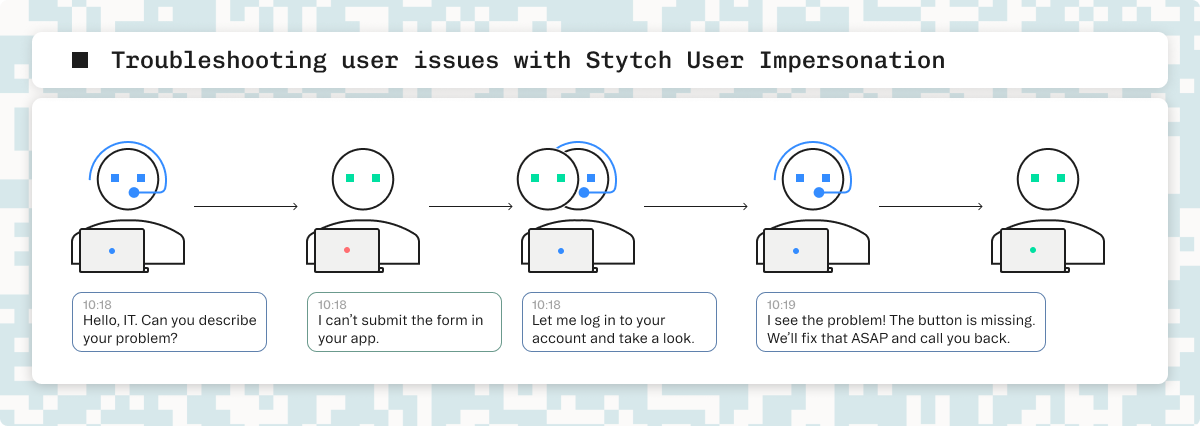
When a user reaches out for help, they've most likely already exhausted the self-service resources available to them and hit the limits of their technical understanding. Support staff, in turn, have to attempt to try and communicate with these frustrated users and talk them through potentially complicated steps for diagnosing and resolving issues (“How do I take a screenshot?!”), hampered by miscommunication and slow, asynchronous responses.
While remote access tools go some way to help, this too requires the user to follow confusing instructions. Asking the user to share their credentials is out of the question in any context, meaning that users and support staff both have to be online and available.
Stytch’s User Impersonation eliminates these support bottlenecks and security concerns, by allowing you to log into your app directly as a user and troubleshoot issues in real-time with strong security and compliance controls.
Key benefits:
- Faster support resolution: Log in as an end user with a single click to diagnose and resolve issues in real-time.
- No credential sharing: Securely access user accounts without sharing or exposing login credentials.
- Seamless experience: Perform actions exactly as the user would, ensuring an accurate troubleshooting and debugging process.
Security safeguards:
- Audit logging: Every impersonated session is logged for compliance and security monitoring.
- Enforced RBAC: Only authorized support managers can initiate impersonation based on auto-enforced RBAC policies.
- Limited session duration: Impersonated sessions can be revoked and automatically expire after 60 minutes to reduce security risks.
- Mandatory reason: Every impersonated session requires the support manager to write and submit a reason, ensuring transparency and accountability.
How Do You Implement User Impersonation with Stytch?
User Impersonation is available now to our Stytch B2B and B2C customers on their existing plans, and it can be enabled on a per-project basis by users with the admin role.
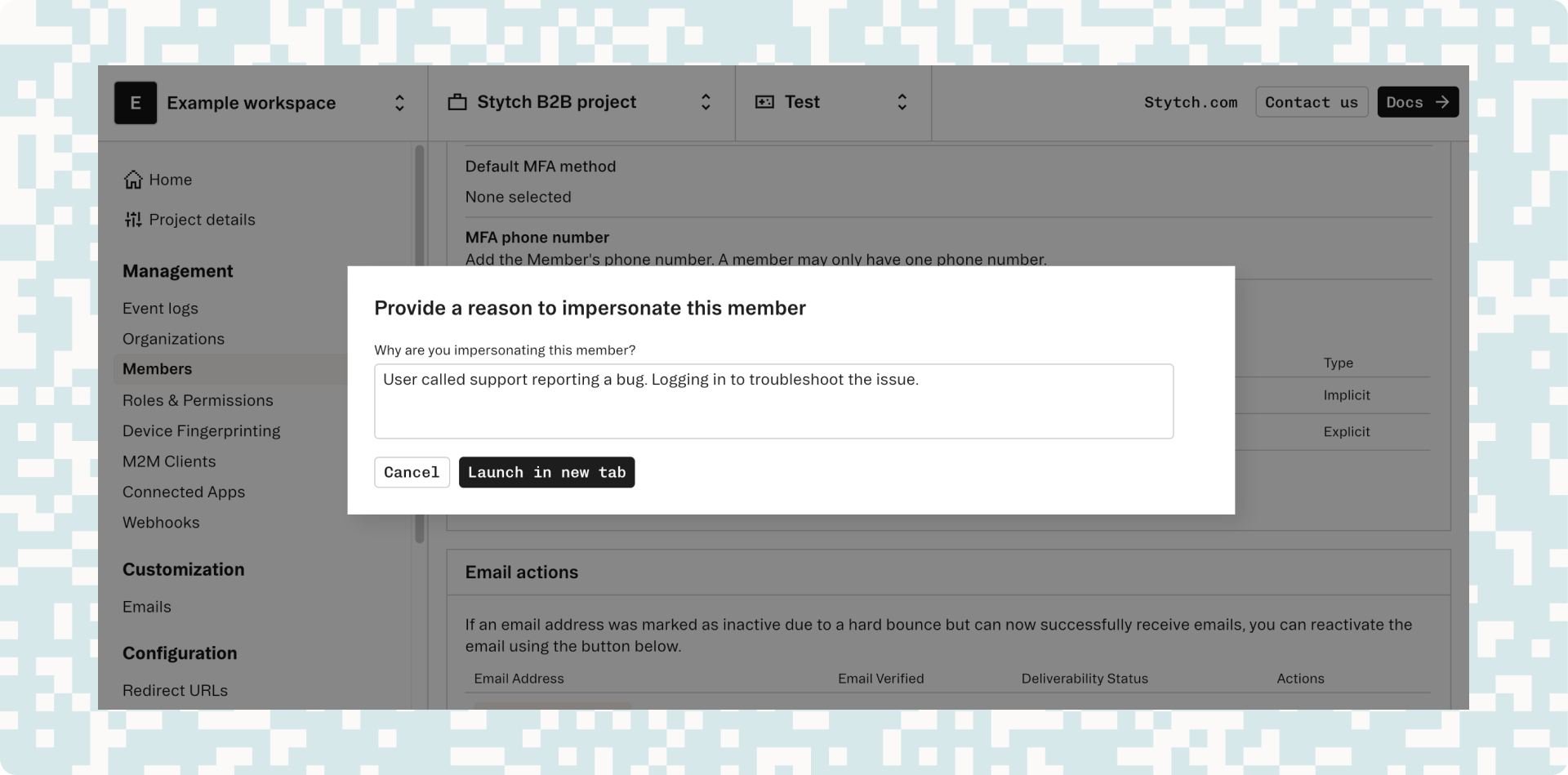
Navigate to Password and user policies in the Stytch dashboard and toggle on Allow user impersonation. Once you've explicitly opted into this functionality, anyone with the support manager role can then select a user to impersonate.
The support manager is then prompted to provide a reason (and they must provide a reason for the audit log) and then clicks Launch in new tab to create the impersonated session.
This initiates the User Impersonation flow in a new browser tab at your project’s default login redirect URL with an impersonation token appended to the query parameters. Here’s an example:
http://localhost:3000/authenticate?stytch_token_type=multi_tenant_impersonation&token=yXxYg2g2h4Ythaue-PwvKpxgTDw5ObE_MFsC1JLwefiaYour application then takes the impersonation token from the redirect URL’s query params and authenticates it with Stytch using either the frontend SDK or backend API and SDKs. Here's what the authenticate request looks like:
curl --request POST \
--url https://test.stytch.com/v1/b2b/impersonation/authenticate \
-u 'PROJECT_ID:SECRET' \
-H 'Content-Type: application/json' \
-d '{
"impersonation_token": "yXxYg2g2h4Ythaue-PwvKpxgTDw5ObE_MFsC1JLwefia"
}'Once your application has successfully authenticated the token, we return a full, impersonated Stytch session for the target user. Here's an example of a successful response from the User Impersonation API endpoint:
{
"status_code": 200,
"request_id": "request-id-test-b05c992f-ebdc-489d-a754-c7e70ba13141",
"member_id": "member-test-32fc5024-9c09-4da3-bd2e-c9ce4da9375f",
"organization_id": "organization-test-07971b06-ac8b-4cdb-9c15-63b17e653931",
"session_jwt": "eyJhbGciOiJSUzI1NiIsImtpZCI6...",
"session_token": "mZAYn5aLEqKUlZ_Ad9U_fWr384...",
"member_authenticated": true,
"member_session": {...},
"member": {...},
"organization": {...},
...
}Every impersonated session is flagged by an impersonated authentication factor that includes the impersonator's email address and workspace ID, so you can display a banner to ensure the impersonator is aware of who they are logged in as, keep their purpose clear, and remind them to log out when they're done. This can also be used to redact information in impersonated sessions to protect users and comply with privacy regulations.
As impersonated sessions are easily identifiable, the client application can revoke access as it would a typical session. To assist with the implementation of secure user impersonation in your apps, impersonated sessions are limited to a duration of 60 minutes and cannot be exchanged between organizations.
We also provide audit logging so you can track who initiated any impersonated session: these event logs are kept by default for 30 days. Additionally, a webhook is emitted at the start of each session that can be used to notify users, or for your own internal notification and auditing purposes.
{
"action": "IMPERSONATE",
"event_id": "webhook-event-test-00000000-0000-0000-0000-000000000000",
"id": "member-test-00000000-0000-0000-0000-000000000000",
"member": {
"email_address": "adalovelace@stytch.example.com",
"member_id": "member-test-00000000-0000-0000-0000-000000000000",
"name": "Ada Lovelace",
"organization_id": "organization-test-00000000-0000-0000-0000-000000000000",
"roles": [
{
"role_id": "stytch_member",
...
}
]
...
},
"object_type": "member",
"project_id": "project-test-00000000-0000-0000-0000-000000000000",
"timestamp": "2024-01-02T03:04:05.678901Z"
...
}Getting Started
User Impersonation is available in your Stytch dashboard right now. Navigate to your Stytch settings under Project details and toggle on Allow user impersonation. Then it's just a single click from the user management or members page to start an impersonated session in your app.
Visit our API docs for more details.
This feature is a part of Stytch Launch Week—see what else is new!
Build with Stytch
APIs and SDKs for authentication, authorization, security and fraud prevention, designed to remove complexity from your codebase.
Related Articles
Product
Feb 20, 2025
Stytch Connected Apps: Make any app an OAuth provider for integrations and AI agents
Product
Feb 19, 2025
Stytch Fraud & Risk Prevention: Intelligent Rate Limiting, real-time monitoring, and more
Product
Feb 21, 2025
Stytch Admin Portal: Self-serve management for organizations and enterprise auth
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.