Back to blog
Trusted Auth Tokens: handle any custom auth flow in minutes
Product
Jul 18, 2025
Author: Stytch Team
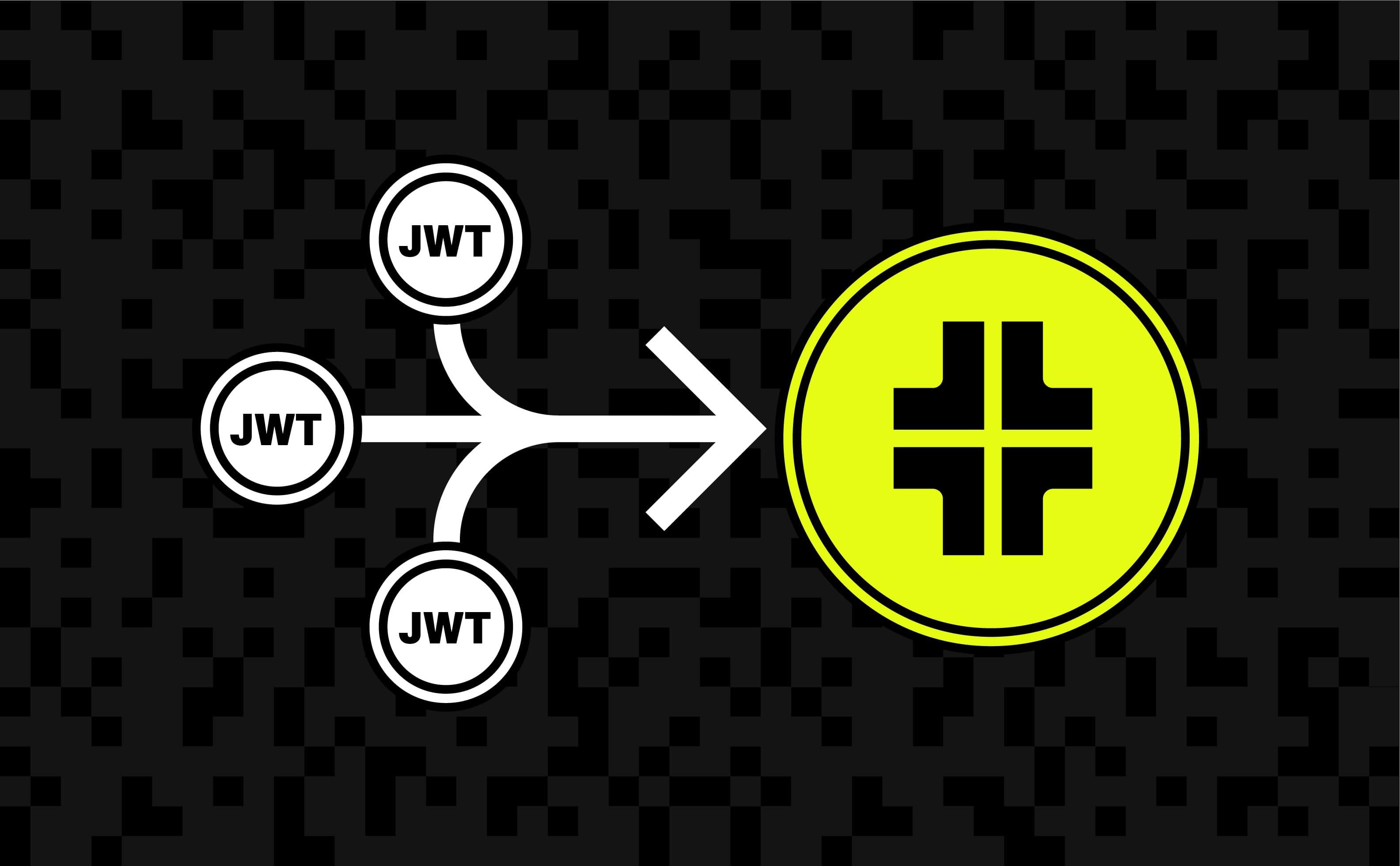
Stytch now has easier support for custom authentication methods with the introduction of Trusted Auth Tokens, a flexible way to bring any auth standard into your Stytch environment. When building integrations with third-party applications, developers often encounter providers that issue JWTs in nonstandard, proprietary formats. Handling these irregularities typically means writing custom middleware to validate sessions.
Trusted Auth Tokens makes it easy to support these special cases. Just register an issuer profile and exchange any trusted JWT for a full Stytch session in a single API call. Now you can build support for any third party auth factor in minutes, even if not explicitly supported.
Custom auth without the custom infrastructure
Even with popular standards like OIDC and SAML, there are an endless number of authentication protocols on the internet. There are many edge cases, where popular services don’t follow standards. To support these, we believe developers shouldn’t have to maintain additional infrastructure and middleware. Instead, we wanted to make it as easy as accepting trusted tokens these services already return, and turning them into Stytch sessions.

Trusted Auth Tokens make this happen by letting developers bring any JWT-based scheme into Stytch for validation and session creation. We can assert trust from third party platforms without forcing users to log in multiple times or create new accounts, among other use cases. This way, instead of waiting for a native solution to be built, the power is in your hands to support more custom authentication methods.
How Trusted Auth Tokens work
Here’s how to get started with Trusted Auth Tokens:
1. Register a Trusted Auth Token profile
In your Stytch dashboard, open the Trusted Auth Tokens tab where you can create a new profile with:
- An expected JWT Audience
- An expected JWT Issuer
- A set of public keys – either a dynamic JWKS URL or a static list of PEM files
- (Optional) Attribute mappings that link JWT fields to Stytch-platform-specific attributes, such as email addresses
2. Exchange the token
Once you have made a profile, your backend can swap a JWT for a Stytch session by calling the “Attest Session” API endpoint:
curl -X POST api.stytch.com/b2b/v1/sessions/attest \
-H 'content-type: application/json' \
-d '{
"token_profile_id": "vercel_jwt",
"token": "eyJ....",
"organization_id": ...,
"session_duration_minutes": 60,
"session_custom_claims": {},
"session_token": "token..."
}'Stytch will then verify the signature, validate claims, and return a Stytch session object.
3. Start or extend a session
You can use the resulting object to start a session as the primary auth factor, or add it alongside other factors for MFA.
When to use Trusted Auth Tokens
Partner integrations and marketplaces
Many platforms have unique tokens for things like partner add-ons and integrations. For example, Vercel’s marketplace issues ID tokens to every partner app. Instead of building your own OIDC server or hosting a userinfo endpoint, you can now directly exchange these tokens for Stytch sessions. This makes it easy to build for third party marketplaces regardless of whether authentication methods are compatible with your infrastructure.
Auth infrastructure migration
Trusted Auth Tokens can also help during a migration to Stytch, allowing you to continue supporting users on legacy authentication flows without added friction. You can use the JWTs generated by that flow to create Stytch sessions, making the transition smoother for end users. This can even be used if you want to move from a Consumer Stytch organization to a multi-tenant B2B one, or vice versa, using the resulting JWT returned from a Stytch authentication call.
Plug-and-play for any JWT-based provider
Any specialized vendor that issues JWTs for authentication can be used with Trusted Auth Tokens, without any special handling. Using a specific biometric authentication device that issues JWTs on successful scans? Trusted Auth Tokens supports it. We even support linking authentication tokens from other providers if you have strict requirements on providers.
Start building with Trusted Auth Tokens
Trusted Auth Tokens gives you a simple, powerful way to handle the growing complexity of authentication, without slowing down your team. Whether you’re integrating with a partner, adding a new auth factor, or future-proofing your infrastructure, Trusted Auth Tokens provides a bridge to make it work with Stytch.
Trusted Auth Tokens is available now! Head to your dashboard, create a profile, and start exchanging tokens in minutes.
To learn more, check out our API docs or contact us to discuss your use case.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.