Back to blog
What is an enumeration attack?
Auth & identity
Aug 30, 2023
Author: Gedney Barclay
An account enumeration attack occurs when a bad actor tries to identify valid users, emails, or accounts with an app’s authentication flow. Account enumeration is primarily used to gain information about a system that can be used in further attacks, and does not directly result in compromised accounts. Because it’s most successful when executed at scale, it’s typically performed and classified as a brute force attack.
What are user enumeration attacks?
User enumeration attacks specifically target a user database, and are typically trying to verify whether a specific account exists with a given email, username or other basic user information. At Stytch, this is the type of enumeration attack we’re most concerned with and the ones we work with customers most on preventing.
A note on “user” vs. “account”: You may also find “user enumeration attacks” referred to as “account enumeration attacks,” as the main goal of verifying usernames in databases is in fact to gain access to users’ accounts. Typically, enumeration attacks are working with a list of usernames / credentials from previous breaches, as this makes their work a lot easier. Once an enumeration attack is successful for a particular login, bad actors will then attempt to use those same credentials on the victim’s other accounts.
How do user enumeration attacks work?
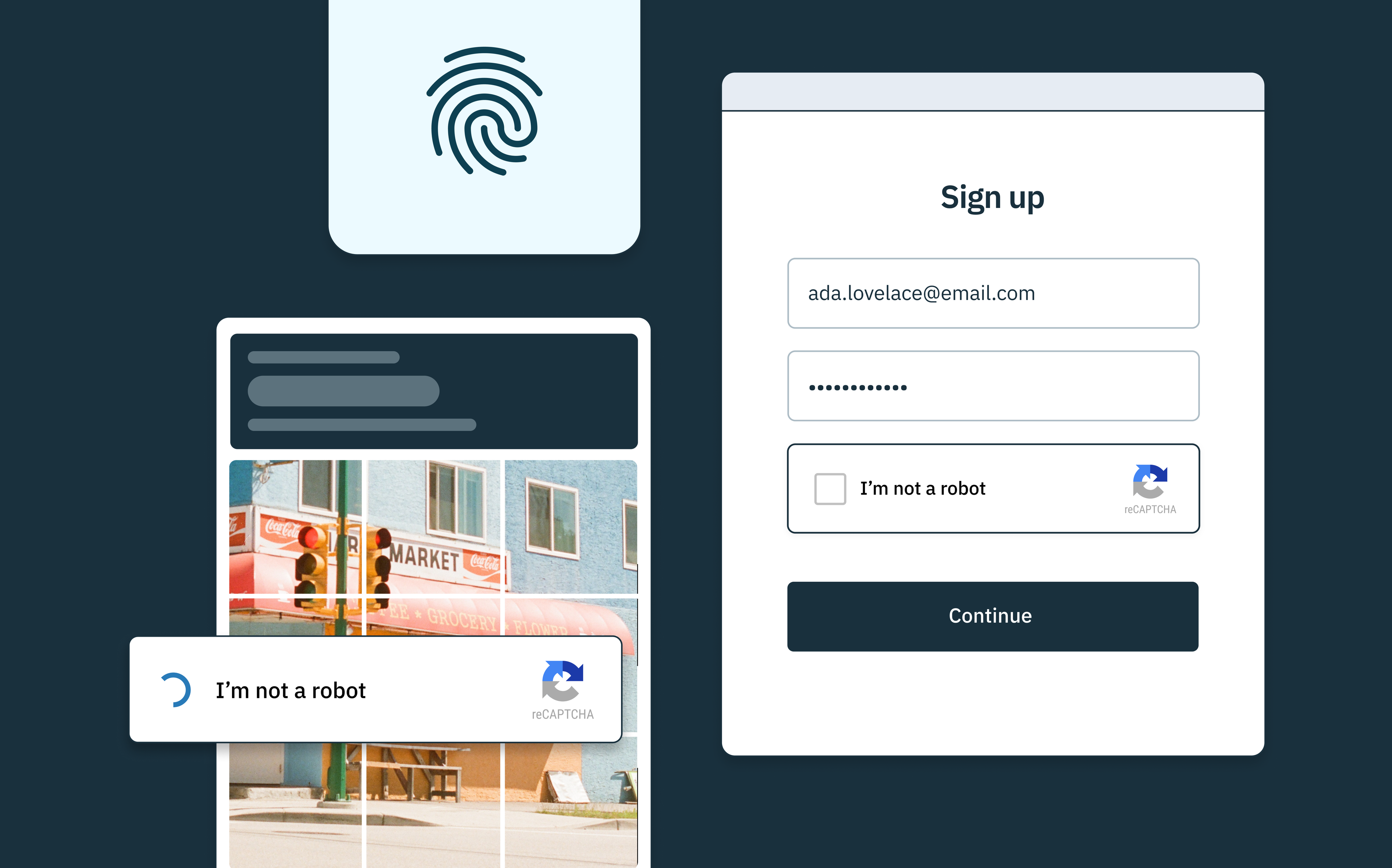
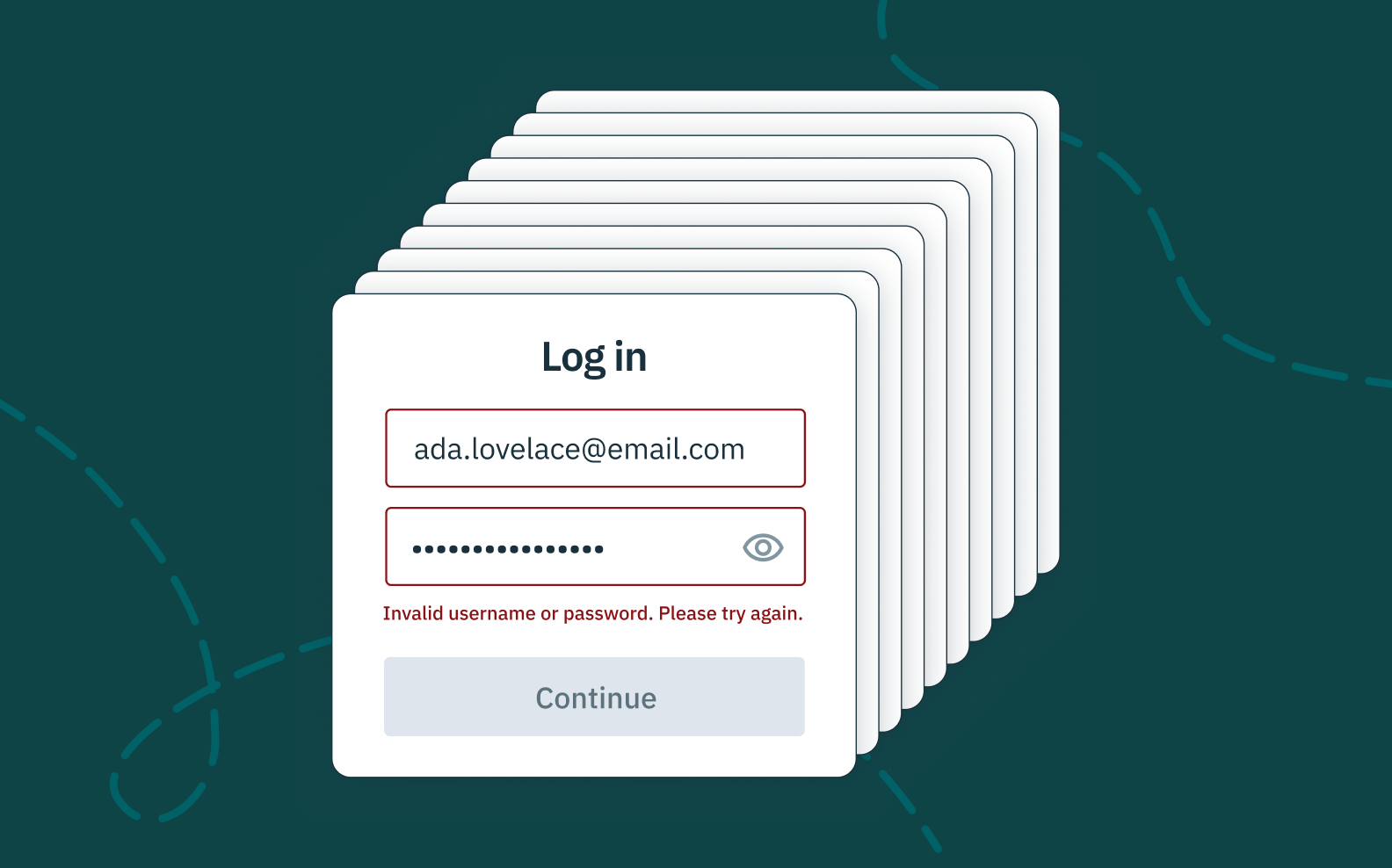
In order for account enumeration to occur, your app must expose some information about a user’s state. This most commonly happens on a login window, login form, or password reset page (hence why we at Stytch have thought about it so much!).
Let’s say a bad actor navigates to your application’s login page. If they enter an arbitrary username and password combo, they will typically come away with one of three outcomes:
- They will get an invalid username message saying that the username does not exist,
- They will get an error message saying that the password is incorrect (confirming that the username exists), or
- They successfully log in.
In all three of these instances, the bad actor gets useful information. In the first scenario, they learn which username is not in your database. In the second, they can at least confirm a valid username that is in your database. The third, though unlikely, obviously gives them most of the information they need to take over someone’s account (assuming of course you don’t have other preventative measures in place like multi-factor authentication or device fingerprinting to flag potentially fraudulent activity!).
Because of the unlikelihood of the third scenario, most bad actors are primarily targeting username information with this attack.
Usually, these attacks follow a very general two-step sequence:
1. Guess existing usernames with brute force
While it would take many lifetimes to manually guess arbitrary usernames and passwords, most bad actors work around this constraint by using bots to automate login attempts, flooding login or password reset pages with potential usernames. If there are no security measures in place to prevent such attacks (often called brute force attacks), they can come away with a fairly robust list of usernames for your application.
Once an attacker has a list of usernames or accounts for your application, they can run more sophisticated and targeted attacks, including:
- Credential stuffing: As outlined in step two, credential stuffing is when bad actors flood your login page with potential username/password pairs. Unlike in this step however, for credential stuffing they’re not trying to mine or confirm valid usernames – they’re trying to validate username/password pairs.
- Social engineering: Social engineering attacks involve using deceit to convince a user to give over their account information willingly. These can take place over email, text, phone, or even in person, depending on the information the hacker has available.
- Phishing: Phishing is a specific type of social engineering typically involving an email or text message, usually from an authoritative institution and using a sense of urgency, danger, or high reward to lure the user into sharing sensitive information.
For more detailed information on these techniques, check out our blog on the top ten password hacking techniques, and how to protect yourself against them.
Want to stop fraud? Get Device Fingerprinting from Stytch.
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
2. Pair existing usernames with possible passwords
With a list of valid usernames in hand, hackers usually then proceed one of two ways:
- They will then “credential stuff” your login page with valid usernames and common passwords, or
- They will search databases of leaked username/password combinations and attempt to log in with any matches they find.
If they opt for the first route, they’ll leverage the same exposed information they did in credential stuffing to find valid usernames, only this time with potentially graver results – accessing one of your user’s accounts.
Thinking outside the password box
While a web server database with username/email combinations is the most common type of user database target for enumeration attacks (largely because they are unfortunately still the most common type of authentication), they are not the only potential targets.
One of Stytch’s most popular solutions is – Email Magic Links, and just like with a username/password login page an EML login page can still expose information about the user if a bad actor enters an arbitrary email, which in this case serves as the username. Worst case for them, they discover an email is not in your database. But in their best case scenario, they can discover an email that is in your database, and still leverage that information subsequent attack to phish or compromise the user.
Server response times – enumeration attacks with minimal info
While the most common way to collect valid usernames is by directly reading the messages returned by the application, some more sophisticated hackers will instead monitor the server response time. Usually, servers take more time responding to an invalid username than they do a valid one.
By monitoring server response times instead of the actual message, hackers can deduce whether or not the username is in the database even if a company is obfuscating their user data with a message like “Your username and/or password is incorrect.” Typically, they do this by coopting or misusing common penetration testing tools.
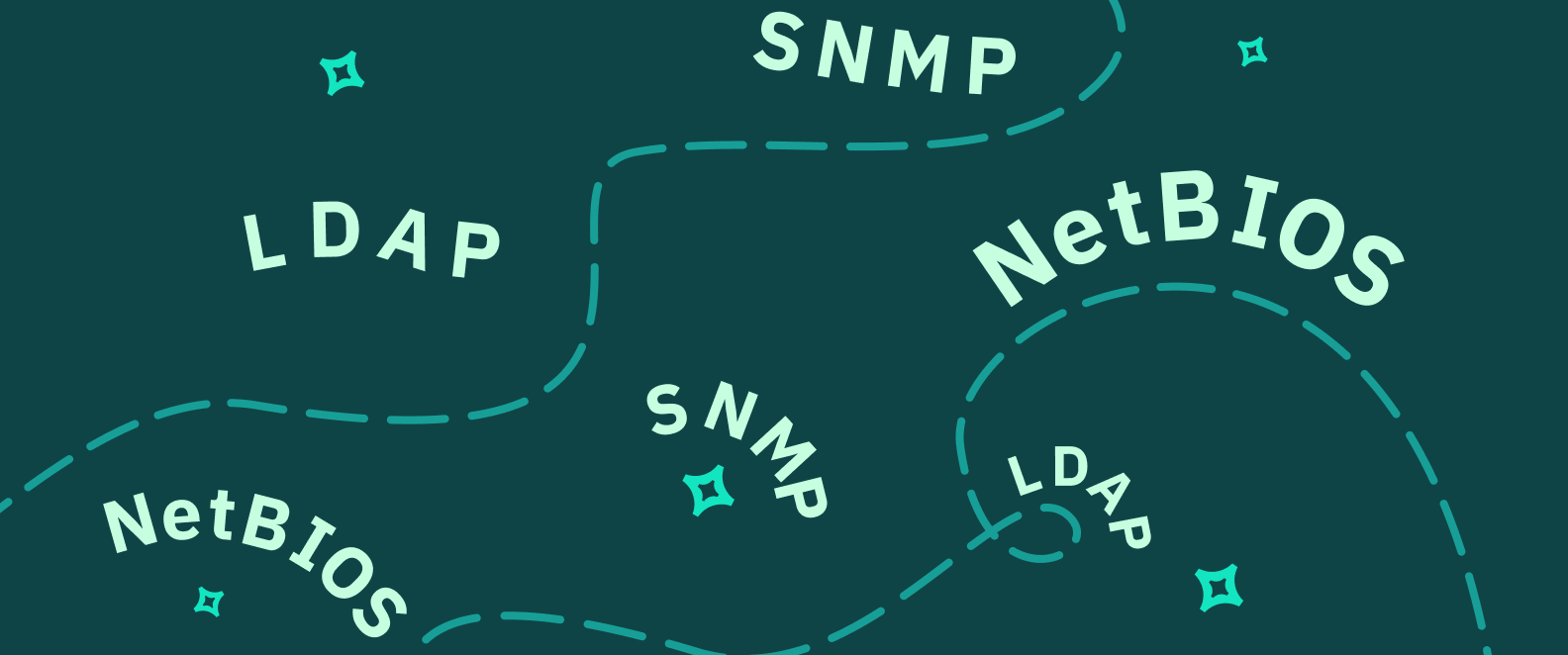
Examples of other complex enumeration attacks
While user enumeration attacks are the most common type of enumeration attack, there are a couple others that are worth being aware of. All three typically rely on specific tooling.
NetBIOS Enumeration
NetBIOS stands for Network Basic Input Output System, and is a protocol used to enable communication between devices over TCP/IP (Transmission Control Protocol/Internet Protocol). It is used only on Microsoft operating systems.
Devices on TCP/IP networks are identified with a 16-character NetBIOS string. When printer and file services are enabled, hackers can perform enumeration attacks to try to derive those strings using specific tools.
If a valid NetBIOS string is discovered, hackers can either then recruit that device to become part of a botnet, or can use it to obtain additional information like a list of the devices that belong to a given domain, policies, and passwords to the TCP/IP network.
LDAP Enumeration
Lightweight Directory Access Protocol (LDAP) is another internet protocol that works on TCP/IP, and is specifically used to store and authenticate specific user information across directory services.
Using specific tools, hackers perform enumeration attacks on LDAPs to obtain usernames, addresses, and other contact information.
SNMP Enumeration
Simple Network Management Protocol (SNMP) refers to an application layer protocol that manages IP network routers, hubs, and switches, specifically for User Datagram Protocols (UDPs). You might see this protocol in video playback transmissions or looking up a DNS. SNMP agents run, and are thus only vulnerable to attacks, on Windows and UNIX networks.
Critically, SNMP stores two passwords, one of which is always publicly available, and thus exploitable by bad actors.
Hackers engaging in SNMP enumeration are typically targeting user accounts, passwords, groups, system names, and devices.
The dangers of an enumeration attack
Clearly, user enumeration attacks can be grave, namely in the form of an account takeover. This can be especially consequential if the credentials a hacker obtains through a user enumeration attack belong to an admin or employee of a company with privileged access.
Successful user enumeration attacks could result in:
- Identity theft
- Intellectual property theft
- Fraud
- Corruption of database
- Breach of regulatory requirements or contractual obligations
While user enumeration attacks are not a particularly heavy target for most non-sensitive consumer applications, apps or services with access to PII (personal identifying information) should be mindful.
Very preventable
In spite of the many different kinds of enumeration attacks that exist, the good news is they’re generally preventable through a variety of methods. Which method is right for your application simply will depend on the sensitivity of the information you’re protecting (i.e., how likely you are to be a target), and where and how much you are willing to introduce friction into your user experience.
Read our next blog to learn about how to prevent enumeration attacks.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.