Back to blog
Identity security: The key to access, compliance and trust in the digital era
Auth & identity
Jun 28, 2024
Author: Alex Lawrence

Identity security in practice involves deploying the technologies, policies, and procedures designed to protect digital identities—essentially, the digital representation of individuals or machines within a system. It ensures that only authorized users or the right entities have the appropriate access to technology resources at the right times and for the right reasons. This security domain encompasses various elements, including authentication, authorization, identity verification, and compliance with regulatory requirements.
In this article, we'll cover the basics of identity security, its importance, and some best practices for implementing it in your organization.
What is identity security and why is it important?
Cybercriminals and fraudsters are constantly finding new ways to impersonate us. As our digital identity increasingly becomes our primary point of access to our most valuable assets and services, it’s essential for the applications we rely on to have strong identity threat detection security controls in place. At a base level, an effective identity security protocol must:
- Support the integrity of our digital identities. Without protective measures to ensure someone is who they say they are online, collective chaos and rampant fraud would render our online ecosystems useless (and dangerous).
- Protect organization and user data. Concurrently, for applications and organizations to thrive, business-critical information must only be available to the authorized individuals equipped and permitted to handle it safely. This helps prevent data breaches, insider threats, and other malicious activities.
- Ensure regulatory compliance. Many industries, such as healthcare and finance, are subject to strict regulatory requirements for protecting sensitive data. Implementing effective identity security measures helps organizations comply with regulations within industries where it’s particularly needed.
- Build trust with users. With the rise of online services and transactions, users need to have confidence that their personal information is safe and secure. Identity security helps maintain this trust by protecting user identities from cyber threats.
As virtual threats evolve, investing in an identity security solution that can adapt and scale is more crucial than ever. In the next section, we’ll cover the foundations of building and growing an identity security practice that can stand the test of time.
The foundations of identity security
To build effective identity security, SaaS companies should consider the following pillars as essential components of an enterprise identity solution.
Identity verification
Identity verification is a crucial component of the "know your customer" concept, focusing on confirming the authenticity of identity documents, histories, or attributes linked to the owner of an account, such as date of birth, address, passport, driver's license, social security number, or employee number. This process aims to strengthen security measures by verifying that individuals accessing a system are indeed who they claim to be, thereby minimizing the risk of unauthorized access to sensitive data and improving the dependability of the security protocol.
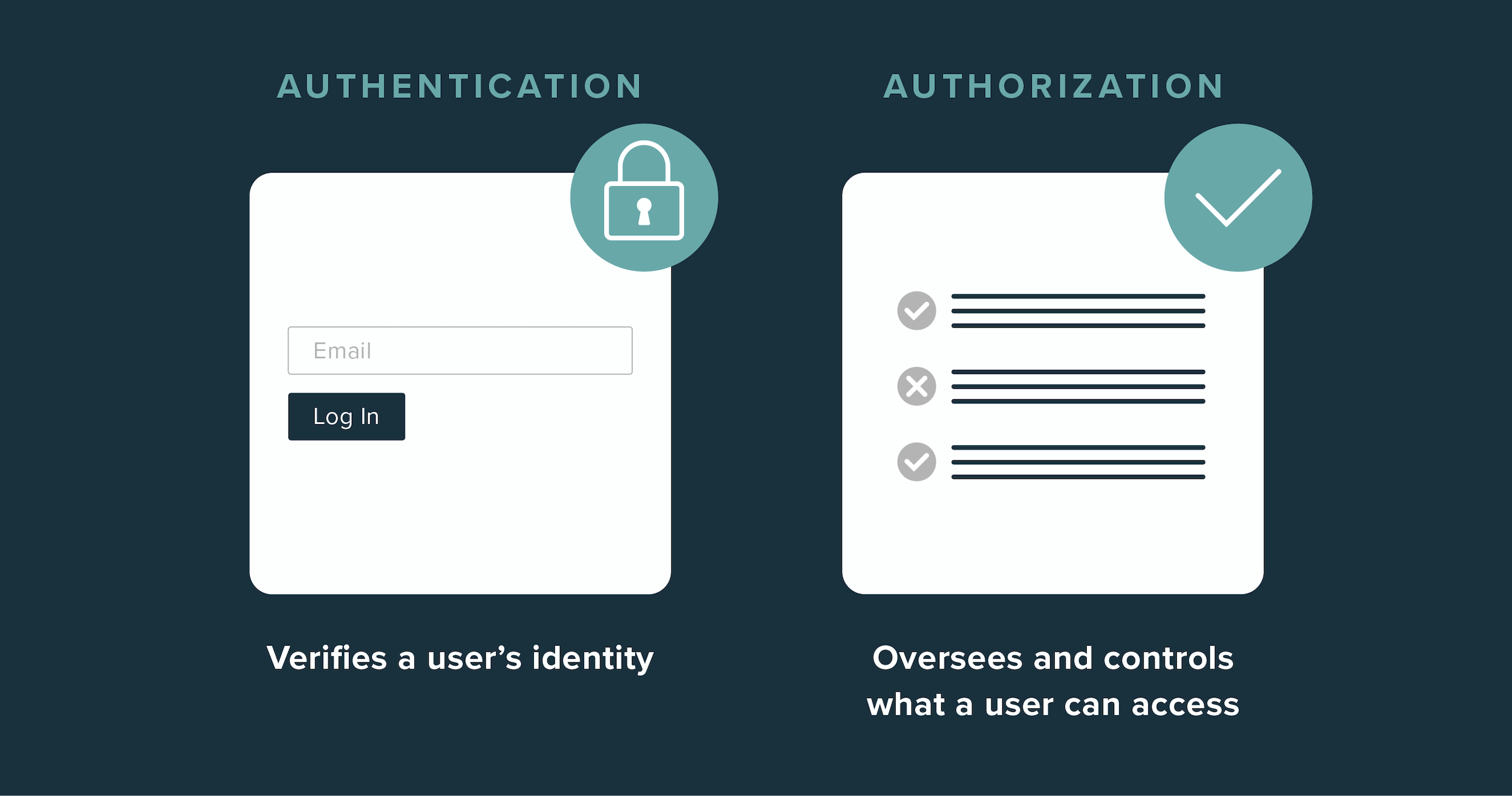
Authentication and access management
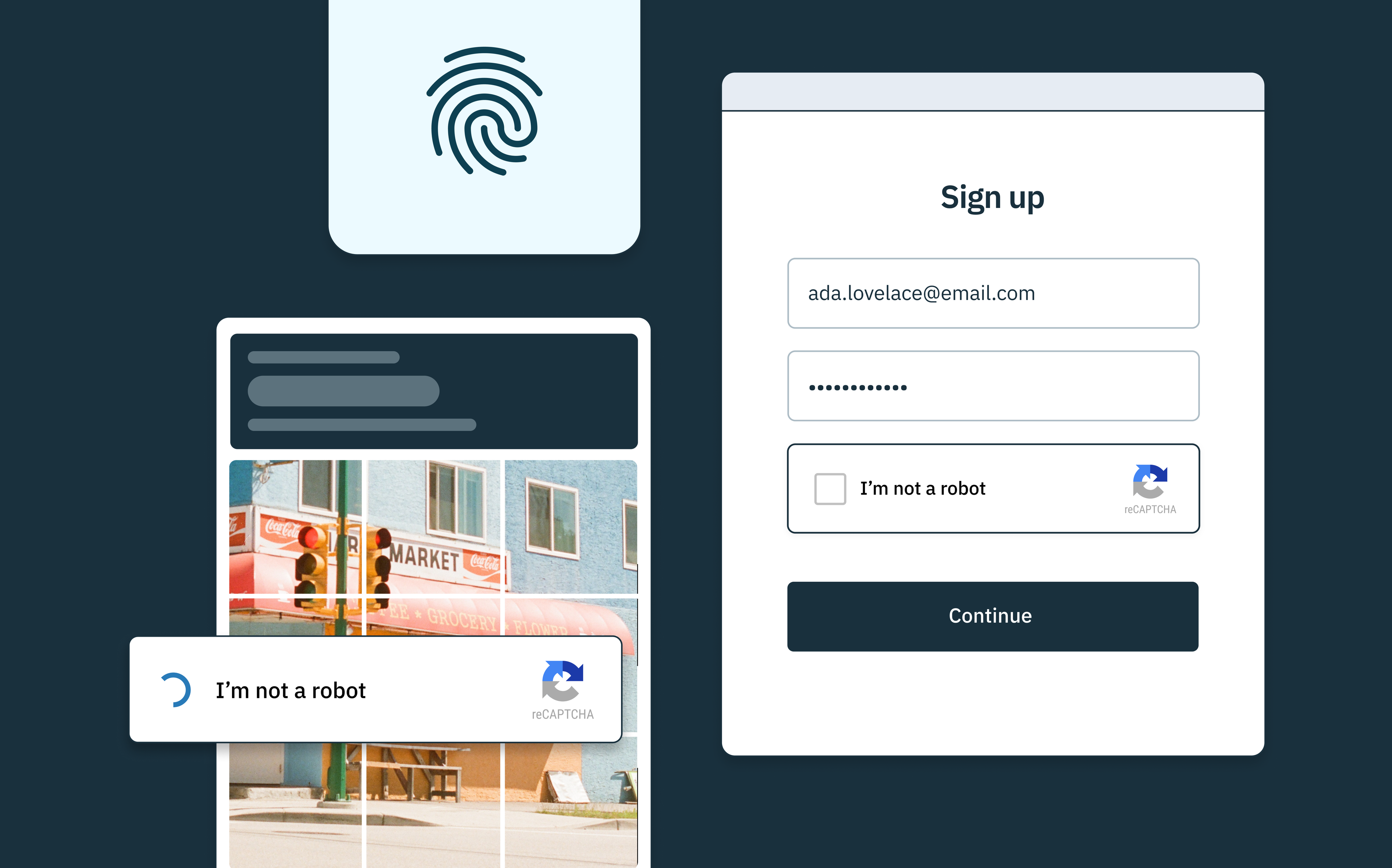
Authentication is the process of verifying a user's identity when they attempt to gain unauthorized access to a system. This is typically the first line of defense in identity security and can include methods like passwords, one-time passcodes, passkeys, and biometric scans. Multi-factor authentication (MFA), which requires two or more verification methods, is becoming a standard practice due to its enhanced security benefits, and is increasingly a requirement for regulatory compliance across modern agile organizations.
Authorization
Once authenticated, authorization plays a crucial role in determining what resources a user can access and what they can do with those resources. This process involves setting and enforcing policies that define user permissions based on their role within the organization. Techniques such as role based access control re-based access control (RBAC) and attribute-based access control (ABAC) are commonly used to manage these permissions efficiently.
Compliance
Regulations such as the General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), and California Consumer Privacy Act (CCPA) mandate the protection of personal and sensitive data. Organizations must implement stringent identity security measures to ensure compliance with these laws, which often include guidelines on data encryption, user consent, and access privileges and timely breach notifications. Failure to comply can result in significant financial penalties and loss of trust from customers and stakeholders.
Want multi-tenant auth without the headaches? Switch to Stytch.
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Federated identity and access management
Federated identity management allows users to access multiple systems and applications across different organizational boundaries with a single set of credentials. This approach not only enhances user convenience but also simplifies the management of identities and reduces the risk of password reuse, which can lead to security breaches and identity theft.
Federated identity management relies on trust between parties and uses standard protocols such as Security Assertion Markup Language (SAML) and OpenID Connect to enable secure communication between different systems. By implementing federated and identity management systems, organizations can improve security and identity related access risks, reduce administrative overheads, and support a seamless user experience.
Identity providers (IdPs)
Identity Providers (IdPs) are services that create, maintain, and manage identity information while providing authentication services to multiple applications. By centralizing user access and authentication, IdPs help reduce the complexity of managing separate credentials for each service, thereby enhancing overall security posture. Examples of IdPs include companies like Okta, Azure, Ping, Auth0, OneLogin, etc., and in more recent years also includes social media platforms such as Google, Facebook, and LinkedIn.. Organizations can also choose to set up their own IdP using tools like Active Directory or open-source solutions such as Keycloak or Shibboleth (IBM).
Identity security in the context of CIAM
Customer Identity and Access Management (CIAM) solutions are designed to securely manage the identities of customers accessing various online services. CIAM systems provide features such as session management, user management, authentication, authorization, multi-tenant SSO, and in Stytch’s case, fraud prevention. These identity and access management services are essential for enhancing customer experiences and complying with data protection regulations, and are critical for keeping your company and customer data safe.
They’re also a pain to build on your own.
In the context of CIAM, what makes identity security important is that it plays a crucial role in an organizations ability to store and process sensitive information about their customers. Having a reliable and user-friendly CIAM provider has spillover benefits beyond just security, which is why so many companies choose to outsource these services to a third party.
1. CIAM builds customer trust
Effective CIAM solutions not only enhance security but also contribute to building trust with customers. By protecting against security threats and providing a seamless and secure user experience, organizations can demonstrate their commitment to protecting customer data. According to research from Gartner, this builds confidence among customers, resulting in increased trust and loyalty towards the brand.
Furthermore, through features such as consent management, CIAM solutions empower customers to have more control over managing digital identities and their personal data, strengthening the ties between organizations and their customers.
2. CIAM helps maintain regulatory compliance
CIAM systems play a crucial role in enabling compliance with regulations by providing features such as privacy management, access controls and consent management. These capabilities allow organizations to meet the requirements set by laws such as GDPR and CCPA, thereby avoiding potential legal consequences. CIAM solutions also help with auditing and reporting, making it easier for organizations to track and monitor compliance efforts.
3. CIAM providers can evolve to meet changing consumer behavior
Consumer behavior and expectations are constantly evolving, especially when it comes to their digital lives. As customers become more technologically savvy, they expect a seamless and personalized experience across all touchpoints, including the login process. CIAM solutions have evolved to cater to these changing behaviors and expectations by offering features such as social login, single sign-on, and personalization, improving UX and increasing customer satisfaction and loyalty.
Aside: Developing a CIAM solution in-house involves significant investments in time, budget, and expertise – particularly in staying abreast of evolving customer identity trends. Partnering with third-party providers like Stytch can offer a quicker, more cost-effective route to secure customer identity management, offering a ready-to-go suite of developer tools (such as OAuth social logins and Single Sign-On), backed by industry-leading compliance. Learn more about CIAM with Stych.
Technology and tools to consider
Implementing identity security successfully begins with strong authentication measures, adopting a zero trust security model, and leveraging artificial intelligence (AI) and machine learning (ML) for better threat detection and response. Using a third party vendor to enhance authentication processes can speed time to market and potentially avoid any risks incurred during the building and rolling out of an internal security solution itself – an option that appeals to many developers and businesses.
Stytch authentication for B2C and B2B applications
Stytch's authentication solutions are designed to bolster identity security and streamline the authentication process for an application's end users and the business-to-business (B2B) cloud environments in which they operate.
- Breach-resistant password-based and passwordless authentication such as Stytch Passkeys for passwordless login using cryptographically secure keys on the user's device for easier, secure access.
- OAuth that enables logins using a single credential set, such as an existing user social account, leveraging secure, token-based authentication.
- Single sign-on auth capabilities for any B2B company looking to support larger customers and sell upmarket as well as Role-Based Access Control (RBAC) tailored for complex B2B environments to assign roles by job function, boost security, streamline management, and mitigate access risks.
- System for Cross-Domain Identity Management (SCIM), a critical feature for large enterprises, who rely on this protocol as a way to centrally and securely manage employee identity and access the thousands of SaaS tools companies use at scale.
- Email Magic Links that enhance login ease by providing authentication via an emailed link, eliminating passwords and reducing a fraudster's ability to gain access.
- Multi-factor authentication (MFA) that improves security by requiring users to provide two or more verification factors prior to accessing their account, greatly reducing the likelihood of account compromise.
- Fraud and risk prevention like Device Fingerprinting that identifies unique characteristics of a user's device, such as the operating system, browser version, screen resolution, and even unique identifiers like IP address, helping distinguish between human and machine to safeguard against OTP bot attacks and other potential automated breaches.
To learn more about how Stytch end-user and B2B authentication solutions can support you in securing, scaling and growing your applications, check out our docs and start building for free today. Or, to learn more about how these or other solutions work, reach out to an auth expert to start a conversation.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.