Back to blog
Stytch Admin Portal: Self-serve management for organizations and enterprise auth
Product
Feb 21, 2025
Author: Stytch Team
Author: Edwin Lim
Today, we’re officially launching the Stytch Admin Portal, giving your customers the ability to manage auth and security settings directly within your application, with just a few lines of code.
The Admin Portal is an embeddable and fully customizable suite of UI components within our frontend SDKs, providing out-of-the-box support for everything your customers would need to self-serve manage their account—from configuring a mandatory MFA policy, to setting up their SSO Connection, to automating role assignments for their SCIM Groups.
Stytch’s Admin Portal components are powered by the Stytch API and protected via our RBAC product, allowing you to securely offer the full breadth of Stytch’s B2B product suite to your customers.
Managing Enterprise Auth, Without the Engineering Lift
Onboarding customers and setting up enterprise auth features like SSO and SCIM are never-ending and thankless tasks. Each new customer potentially demands valuable engineering and technical support resources, with back-and-forth troubleshooting between your team and theirs. It’s a time-consuming process that’s prone to errors and a drain on your resources.
That’s why we built the Stytch Admin Portal: to eliminate these pain points by offering a fully featured, drop-in dashboard experience that lets your customers take control of their auth setup directly within your app. Use only the components you need and style them to fit your brand.
What is the Admin Portal?
The Stytch Admin Portal itself consists of a library of components within our frontend JavaScript SDKs, available in Next.js, React, and Vanilla JS.
import { AdminPortalSSO, AdminPortalOrgSettings, AdminPortalMemberManagement, AdminPortalSCIM } from '@stytch/react/b2b/adminPortal';These SDK components interact directly with the Stytch API empowering your team to:
- Enable self-serve workflows: Your customers can independently manage authentication and authorization settings, eliminating the burden on your support or engineering teams.
- Add enterprise authN and authZ features on demand: Each Admin Portal component functions independently, so you can pick and choose what to integrate. Add new features like SSO, SCIM, and JIT provisioning as your business scales.
- Customize for a native experience: All components support custom styling, ensuring the Admin Portal seamlessly matches your application’s unique UX and branding. If you're already using Stytch’s prebuilt login UI, you can reuse the same style object.
- Strengthen security posture: All components enforce built-in RBAC policies, verifying that only authorized users have access to certain settings and perform sensitive actions.
- Build headlessly: You can also leverage our headless SDK methods to customize and extend any Admin Portal functionality if you need more control.
Modular Components, Native Look and Feel
At the heart of our Admin Portal’s design are modular, embeddable UI components. These independent components give developers the freedom to build a native admin experience that seamlessly integrates into their applications. Whether you need to manage members, configure authentication policies, or set up SSO, each component is designed to function autonomously or as part of a cohesive frontend management system.
This modular approach ensures that regardless of your application’s frontend architecture the Admin Portal UI fits right in. No iframes, no externally hosted screens, no links or redirects—just your app, built the way you want it.
const AdminPortal = () => {
return (
<Routes>
<Route path="/org-settings">
<AdminPortalOrgSettings styles={customStyles} config={config} />
</Route>
<Route path="/member-management">
<AdminPortalMemberManagement styles={customStyles} config={config} />
</Route>
<Route path="/sso">
<AdminPortalSSO styles={customStyles} config={config} />
</Route>
<Route path="/scim">
<AdminPortalSCIM styles={customStyles} config={config} />
</Route>
</Routes>
);
};Essential Auth Features for Enterprise Applications
RBAC Awareness and Enforcement
Every component is fully RBAC-aware, enforcing authorization at the UI and API levels. This ensures that critical functions such as SSO configuration, deletions, or role assignments are accessible only to the users that should have access to them.
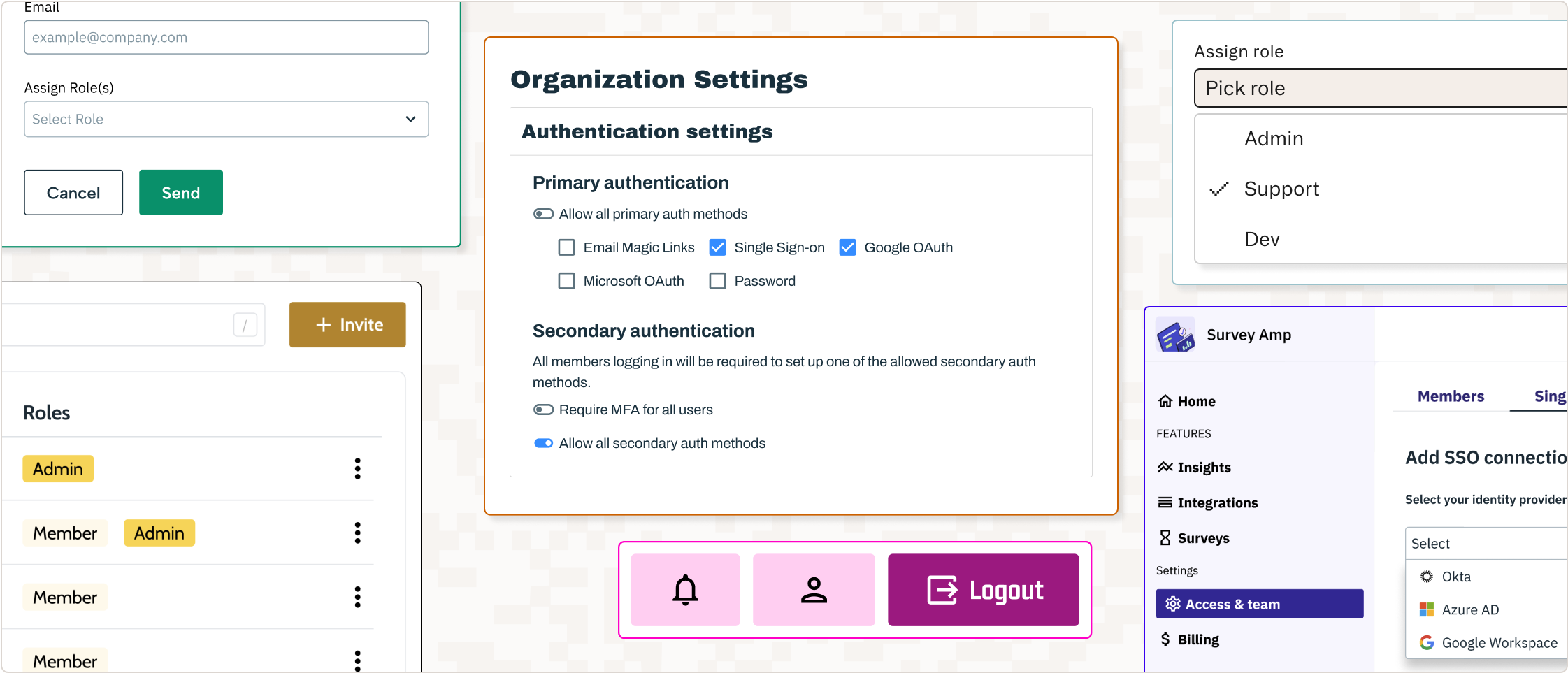
Organization Settings
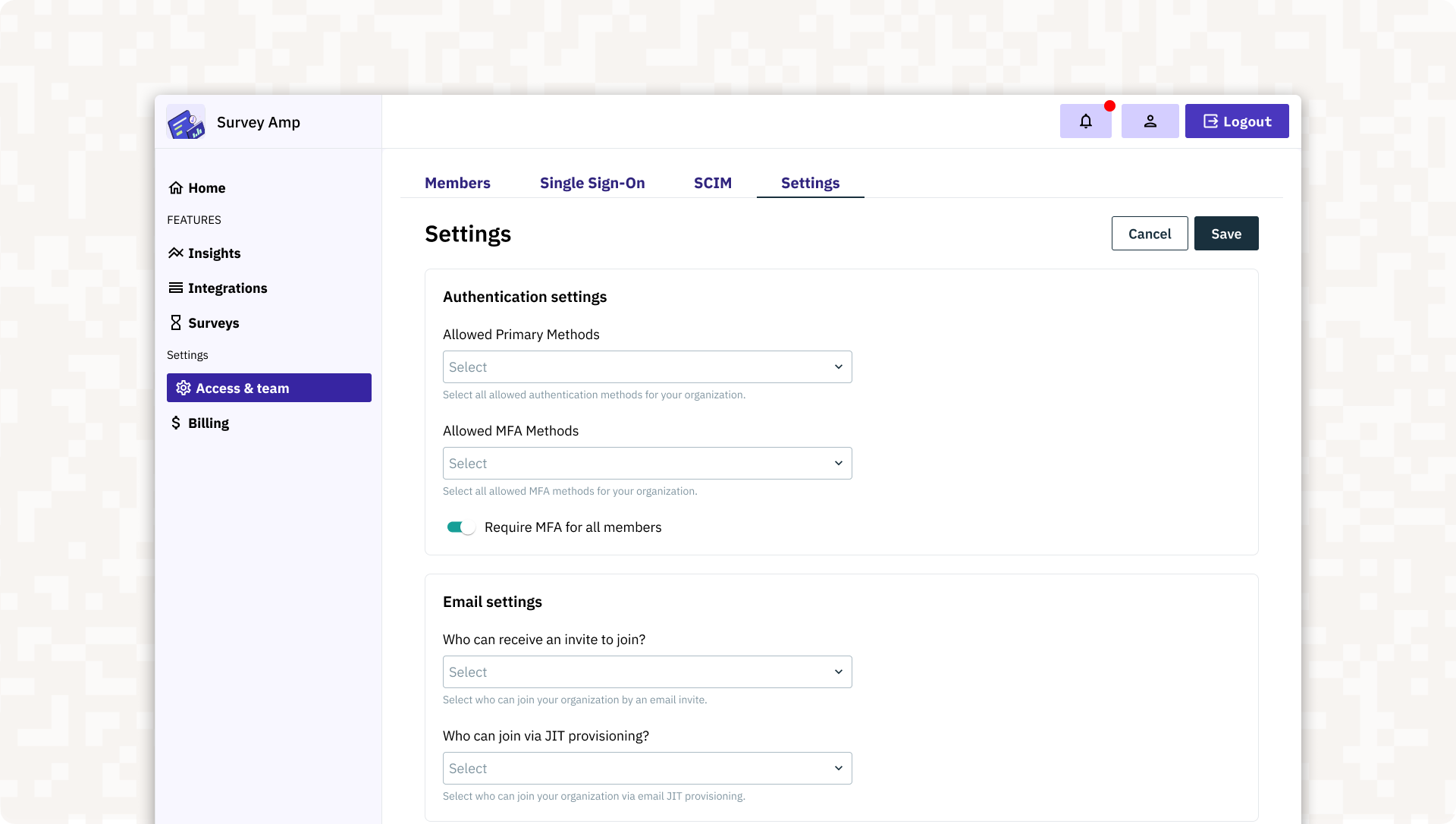
The <AdminPortalOrgSettings> component gives your admin users control over their tenant-specific auth settings. This includes the ability to safely configure, update, and manage essential policies and features such as:
- Authentication settings: Admin users can define and update allowed authentication methods (e.g., single-sign on, passwords, email magic links, OAuth, etc.)
- Multi-Factor Authentication: Admins can configure MFA settings to enforce compliance and security standards.
- JIT provisioning and invites: Admin users can manage invites and configure automatic JIT provisioning flows based on SSO credentials, email domains, and specified OAuth tenants like a specific Slack workspace or GitHub organization.
- RBAC assignments: Admin users can manage role assignments manually or automate them based on email domains or SSO connections.
Member Management
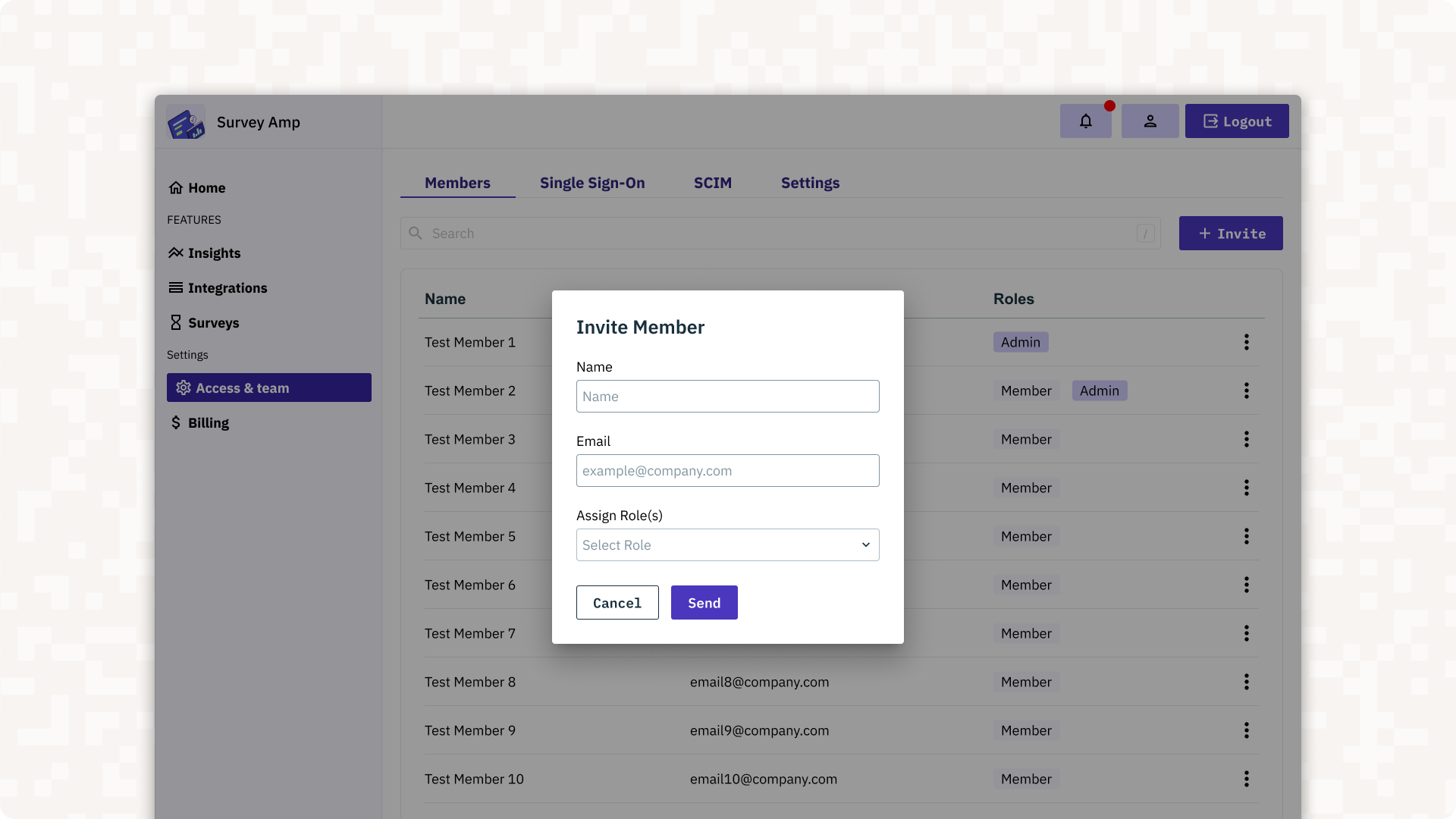
The <AdminPortalMemberManagement> component grants admin users the ability to directly manage individual users and their memberships, including features such as:
- Updating, inviting, or deactivating members.
- Resetting passwords, MFA, or session tokens.
- Assigning RBAC roles and permissions.
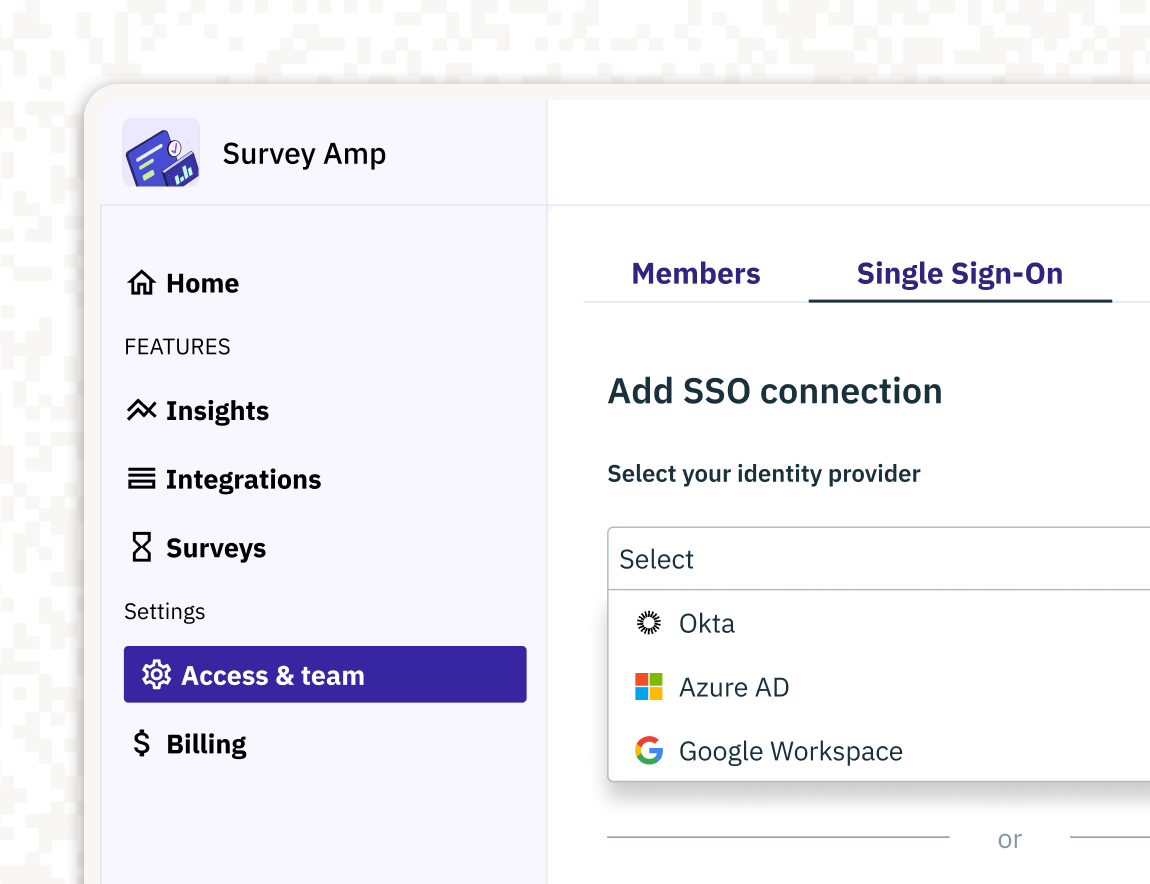
Single Sign-On (SSO)
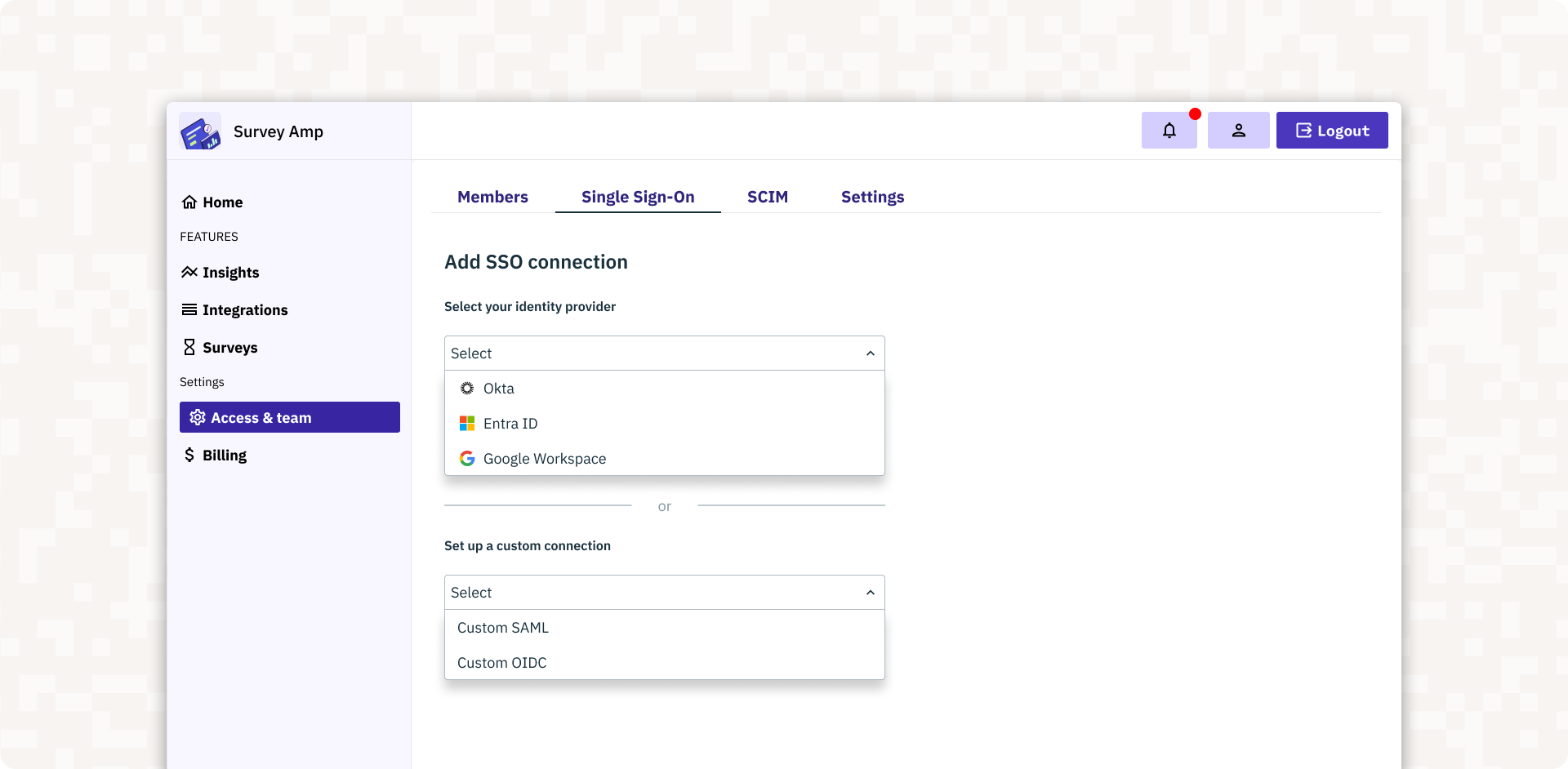
The <AdminPortalSSO> component simplifies SSO configuration by supporting both SAML and OIDC-compliant identity providers like Microsoft Entra, Google Workspace, Okta, and more. Key features include:
- SSO configuration: Admins can easily add, update, or remove SSO connections directly from the portal.
- Support for External SSO Connections: Admins can configure shared SSO connections that can be used across multiple organizations, streamlining setup across identity providers.
- Certificate rotation: Admins can ensure uninterrupted service and enhanced security by handling certificate updates through the portal.
SCIM Integration
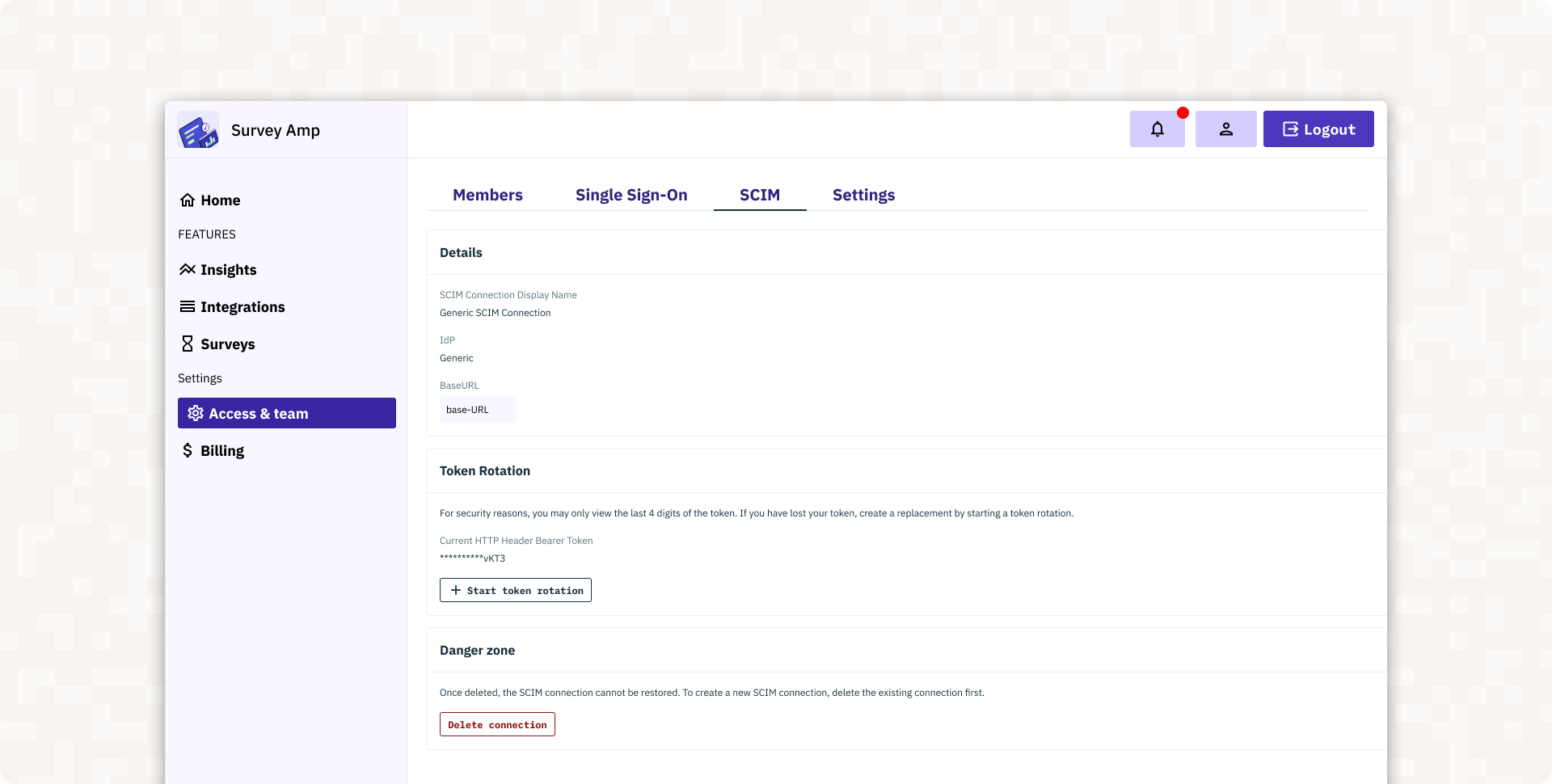
The <AdminPortalSCIM> component streamlines role assignments with SCIM group mapping, automating updates to role assignment based on the identity provider’s groups and your SCIM Connection.
Getting Started
Visit out our SDK docs to get started with the Admin PortaI.
And to see it in action, watch our video to see how the Admin Portal streamlines organization and enterprise management.
Check back tomorrow for more Launch Week! And follow us on X for daily product announcements.
Related Articles
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.