Back to blog
Account Abuse Prevention
Auth & identity
Apr 9, 2024
Author: Alex Lawrence

Free pricing tiers and trials are a common part of the app onboarding experience for new users, whether it’s a B2B SaaS app or the latest consumer app. This move is designed to cater to the fleeting intent of potential customers, eliminating the friction of traditional sales conversations and thereby reducing the likelihood of early-stage evaluation drop-offs.
However, this open-door policy for account creation, while enhancing customer experiences and potentially boosting paid conversions, inadvertently opens up a Pandora’s box of abuse vectors. Among these associated risks, multi-account abuse stands out as a significant threat.
Multi-account abuse, the basics
Multi-account abuse is a form of account abuse where attackers create multiple new accounts for free to exploit resources that are available to logged in users. Companies may offer this as:
- Free self-service subscription tier
- Free time-based (eg. 30-day) trial
- Free credits for new accounts
- Promotional offers
While intended as a commercial incentive for real customers, these can open access to bad actors and fraudulent users, providing access to valuable and otherwise costly resources; including traditional and AI compute capabilities, particularly if these are client-side accessible.
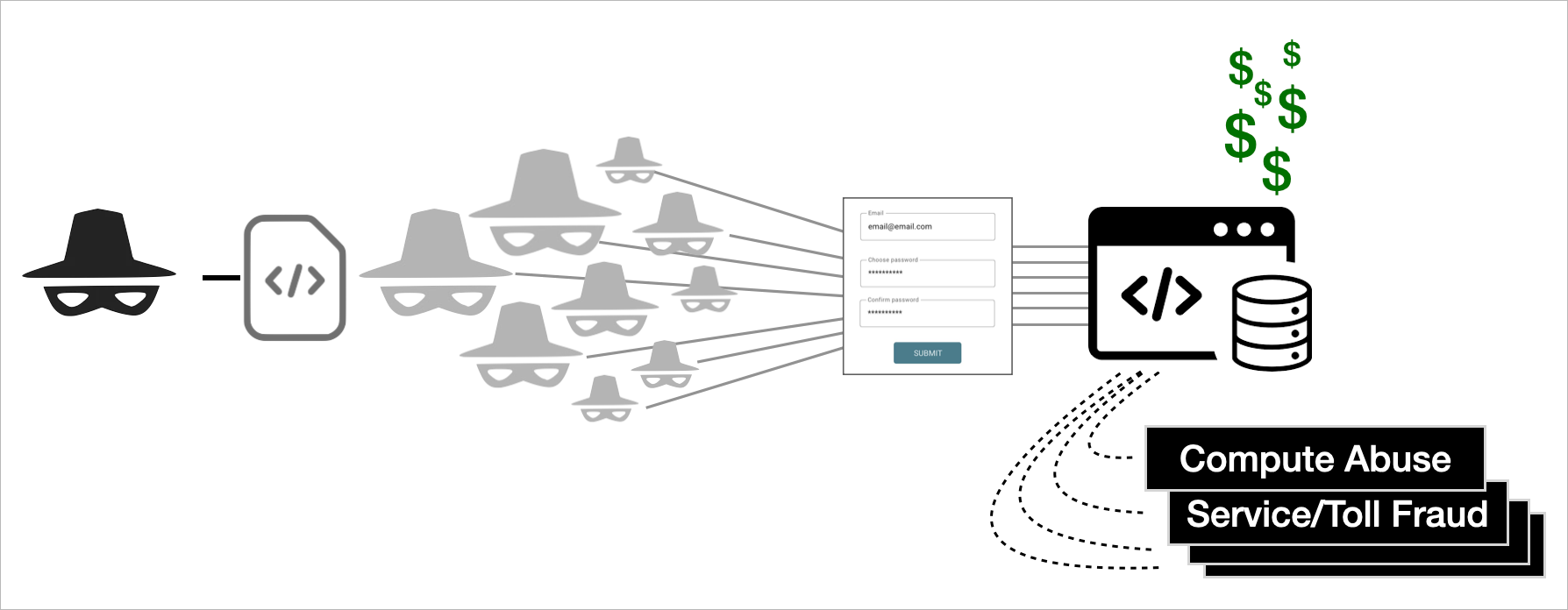
Multi-account abuse
While fake accounts are often associated with consumer-based threats such as credit card fraud and posting spam or malicious content, multi-account abuse can be far more costly for companies. Some examples include:
Cryptomining
In the realm of B2B products aimed at developers or data engineers that offer compute access, attackers often exploit these resources for unauthorized purposes by attempting to proxy cryptomining activities through freely available accounts in order to monetize the compute that the unsuspecting application is paying for.
AI Compute Abuse
The issue of AI compute abuse has become increasingly prominent, driven by the surge in companies integrating interactive AI features into their platforms over the recent period. Similar to regular compute, AI compute is costly and, when exposed in a fungible manner, allows attackers to access the compute without having to foot the bill themselves.
Consider a tool like GPT4Free, which is an open-source project that makes it easy for fraudsters to steal AI compute from apps that expose this client-side.
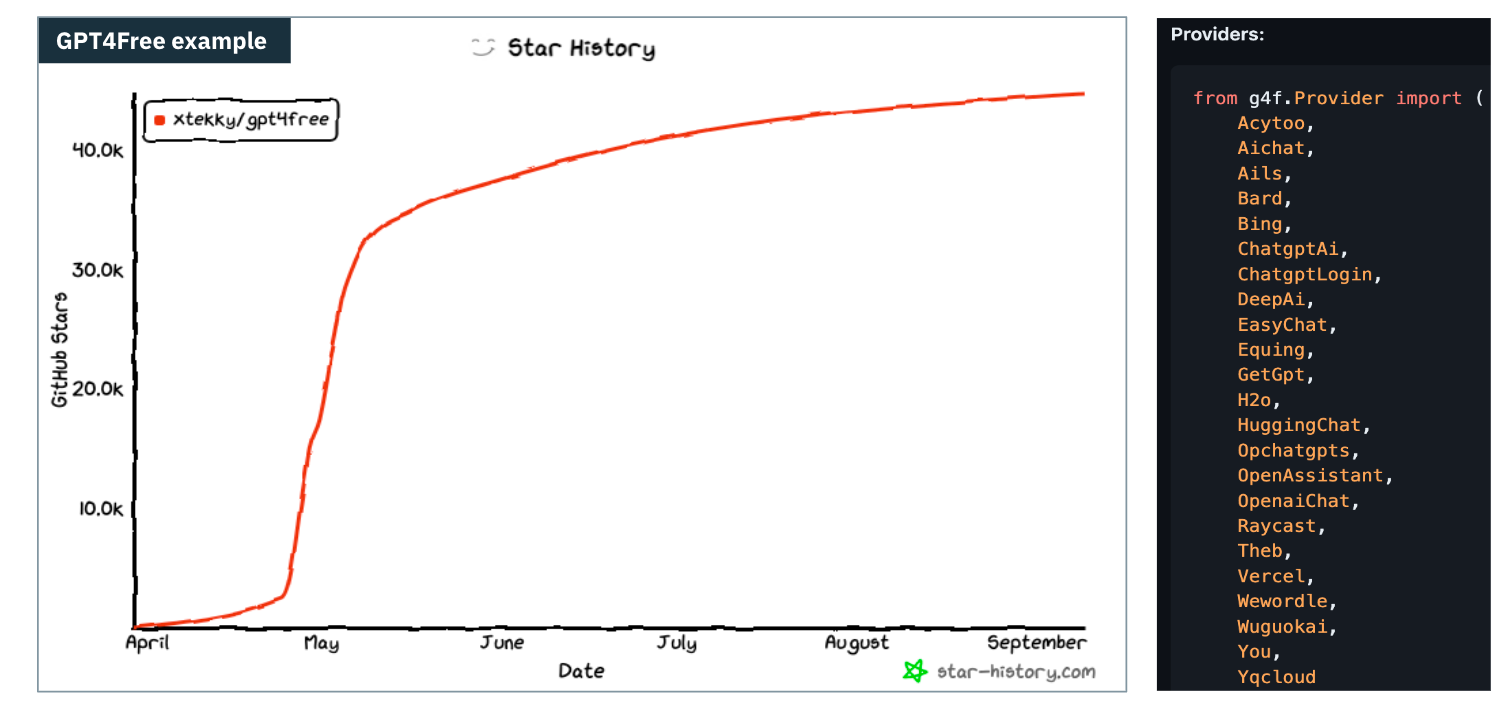
Impact of reverse engineering on AI API costs
Toll Fraud
Many applications offer access to infrastructure services like telephony that can be manipulated for profit and fraudulent transactions. In the case of toll fraud, bad actors abuse free accounts that expose SMS or voice dialing services to collude in profit sharing with a mobile network operator or carrier.
Drivers for free account abuse
This type of free account abuse, also known as multi-accounting, where multiple accounts are created on a platform or application with the intention of exploiting resources or services, is done for a variety of nefarious purposes.
- Financial gain: Users may create many new accounts to take advantage of promotional offers, free trials, or credits, which can lead to significant financial losses for businesses.
- Market manipulation: In e-commerce environments, multi-accounting can be used to manipulate product ratings, reviews, or prices, resulting in an unfair advantage for the abuser and damaging the integrity of the platform.
- Manipulation of online contests, polls, or voting: Multi-accounting can be employed to skew the outcomes of online events, undermining the democratic process and eroding trust in the platform.
- Fraudulent activities: In some cases, multi-accounting can be used for more serious criminal activities, such as money laundering, identity theft, or other forms of financial fraud.
Types of free account abuse
There are two primary categories of free account abuse that you need to be aware of:
- Manual free account abuse: this does not involve bots and instead involves a human-in-the-loop to actually create the multiple free accounts
- Automated free account abuse: this is where an attacker uses a script (e.g. python, node, or headless browser) to automate mass account creation to take advantage of your application’s resources. With generative AI, almost anyone can now build a script and get step-by-step instructions to automate this workflow.
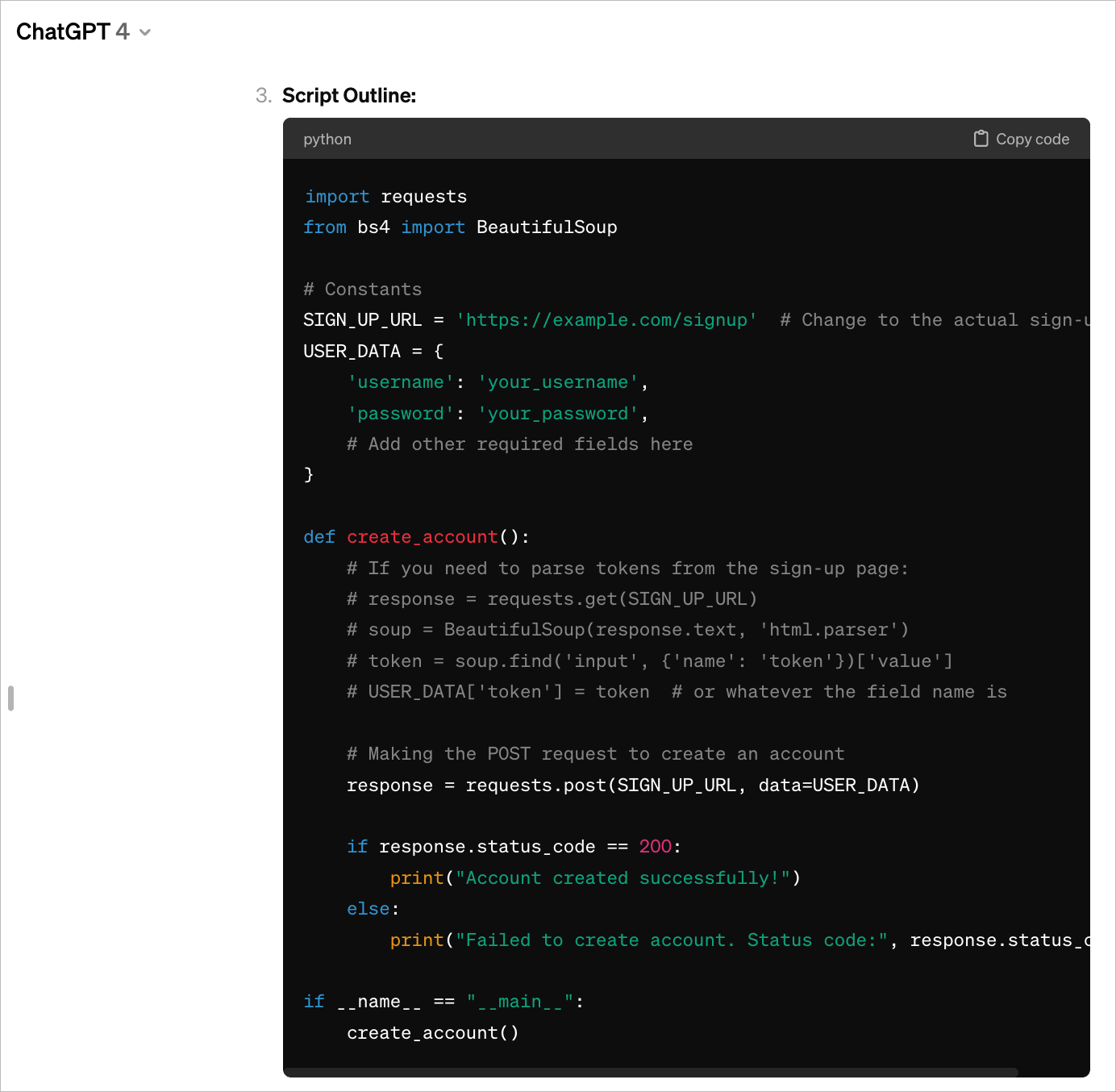
Automated account creation script from ChatGPT
Conventional ways to defend against multiple account abuse
To effectively mitigate the risks associated with multi-account abuse and deter both automated and manual fraudulent account creation, it is imperative for application developers to implement robust security measures for fraud prevention.
Conventional account protection methods to combat free account abuse have been employed by developers for years, with varying degrees of success.
These methods include:
- Rate limits: Implementing a limit on the number of account creations or actions per unit of time to prevent excessive sign-ups or activity. This is often used in conjunction with other traits (e.g. IP address, user agent, email domain, etc.).
- IP tracking: Monitoring and tracking IP addresses to identify suspicious activity or multiple customer accounts originating from the same source.
- User verification: Verifying identity through various methods, such as email, phone number, or social media account linking.
- CAPTCHA: Implementing a challenge-response test to determine whether a user is human or a bot.
While the combination of these methods can be effective for new account abuse, in some cases, they are not foolproof and can be circumvented by sophisticated attackers. For example, anti-captcha.com and similar services exist that can solve CAPTCHA challenges automatically, rendering them ineffective. Additionally, attackers can rotate IP addresses to avoid detection, and they can create infinite permutations of email addresses or fake phone numbers for verification.
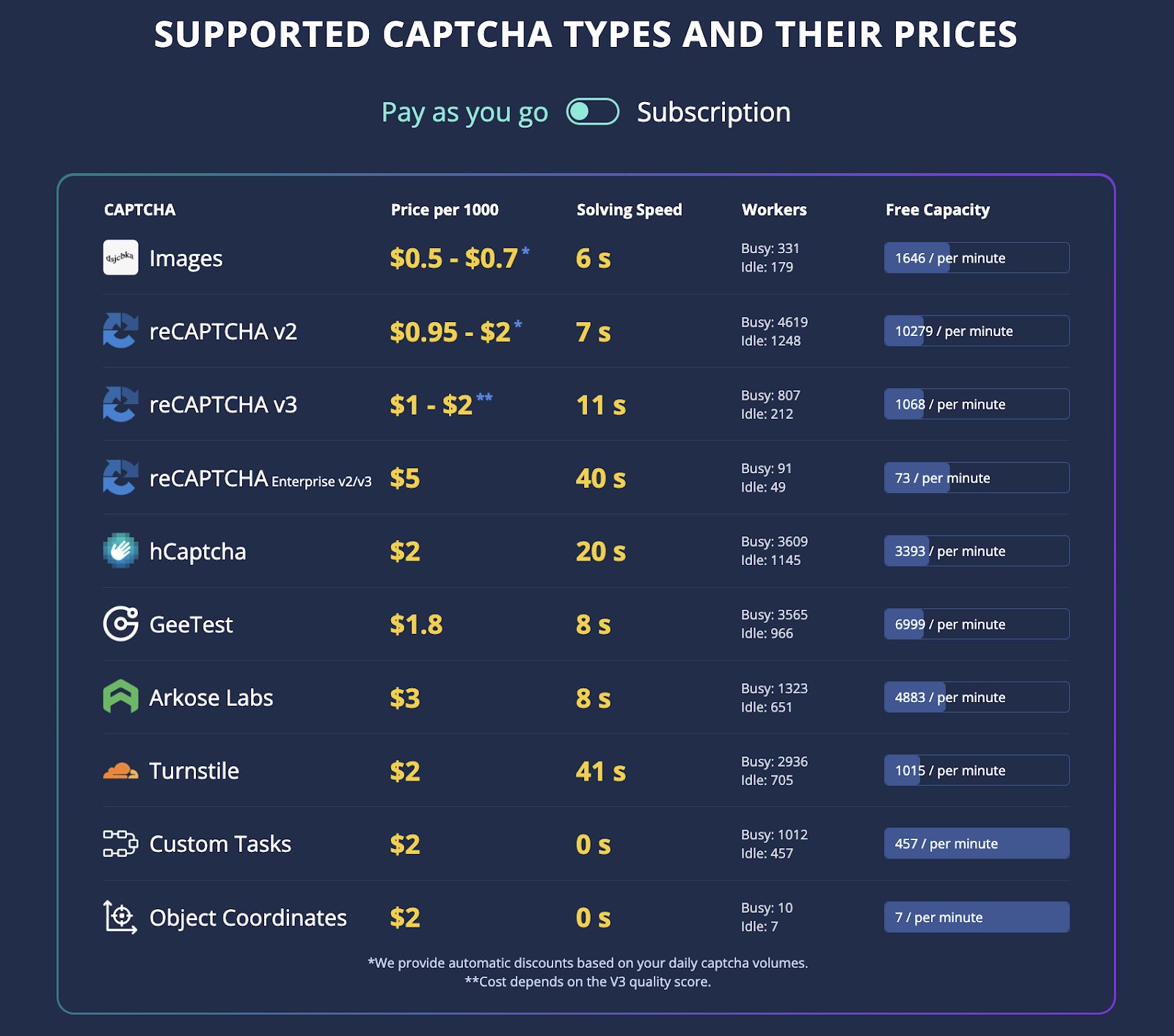
CAPTCHA types and prices
More powerful modern methods for account abuse prevention
Instead, product teams need to consider newer approaches to safeguard their platforms against the myriad of abuse vectors that threaten the integrity and reputation of their applications.
Stytch’s device fingerprinting product offers a more foolproof way to curb free account abuse by providing three powerful primitives to developers
1. A verdict object
A verdict object will frictionlessly detect and assess every piece of traffic on your site as a true human (an ALLOW verdict) or a bot/headless browser (a BLOCK verdict which comes with the detailed reasons for the block such as `HEADLESS_BROWSER_AUTOMATION`) .
Unlike products that provide a confusing risk score that requires endless trial and error, this makes it simple to detect and eliminate unwanted programmatic activity in your app.
2. Multi-vector fingerprinting and threat analysis
Stytch offers a unique and stable set of device, browser, hardware, and network fingerprints for identifying each user.
Particularly useful for preventing ban circumvention from malicious, manual abusers, these identifiers are derived from various attributes of the user’s physical device, browser software, and user characteristics. By aggregating these attributes into a single identifier, Stytch ensures that the identifier is unique to each device, offering enough entropy to prevent fraudulent actors from creating multiple accounts or exploiting resources.
3. Custom fingerprint rules
An ability to set custom rules on individual fingerprints, so that you can allow any wanted programmatic traffic (e.g. end-to-end tests) while setting explicit ban rules for any human abuse you’re seeing (e.g. permanently ban a specific browser_fingerprint or visitor_fingerprint).
A complete, API-first solution
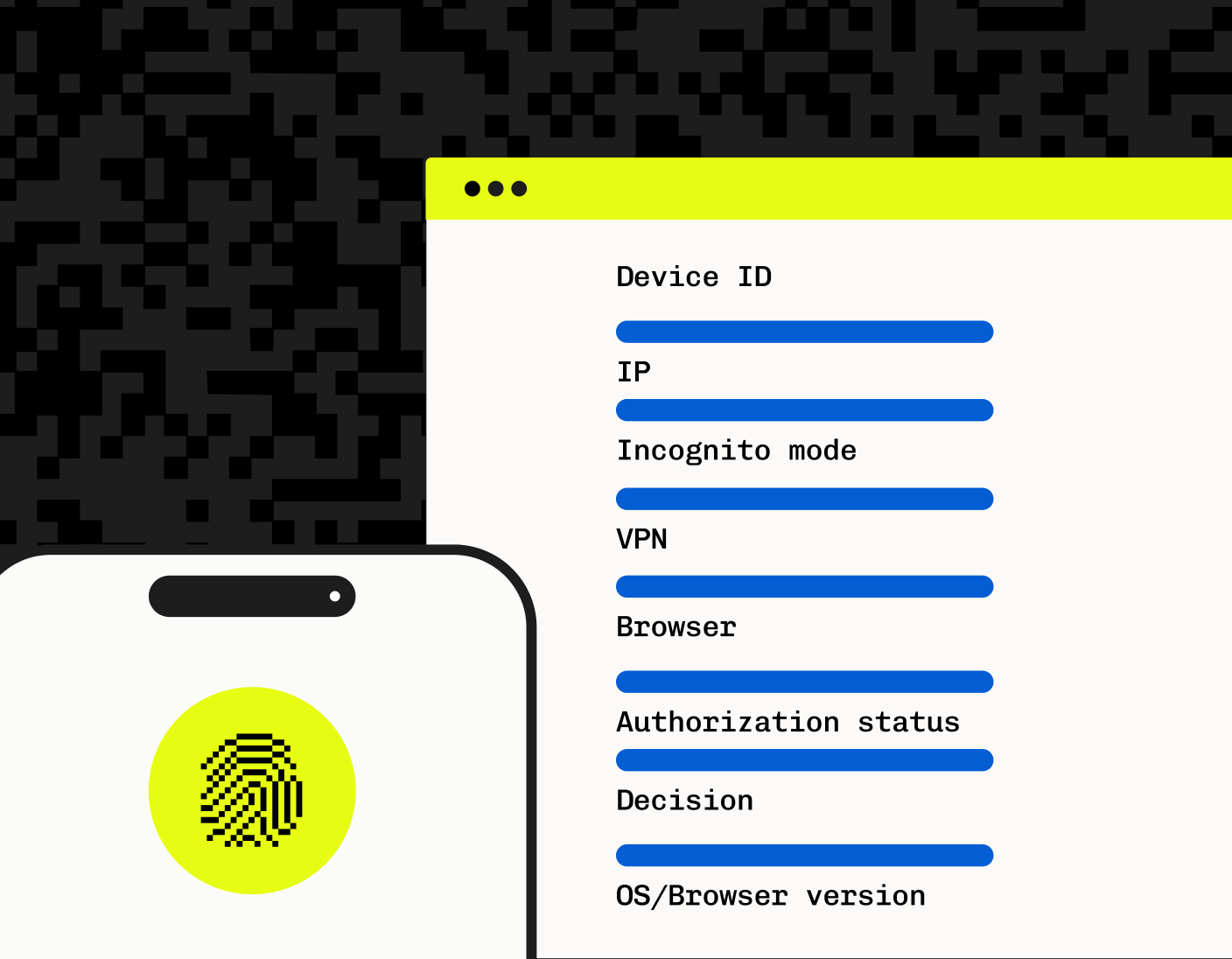
Stytch Device Fingerprinting provides full API-based programmatic access for easily integrating fraud prevention into your application. Here’s an example JSON response from the API:
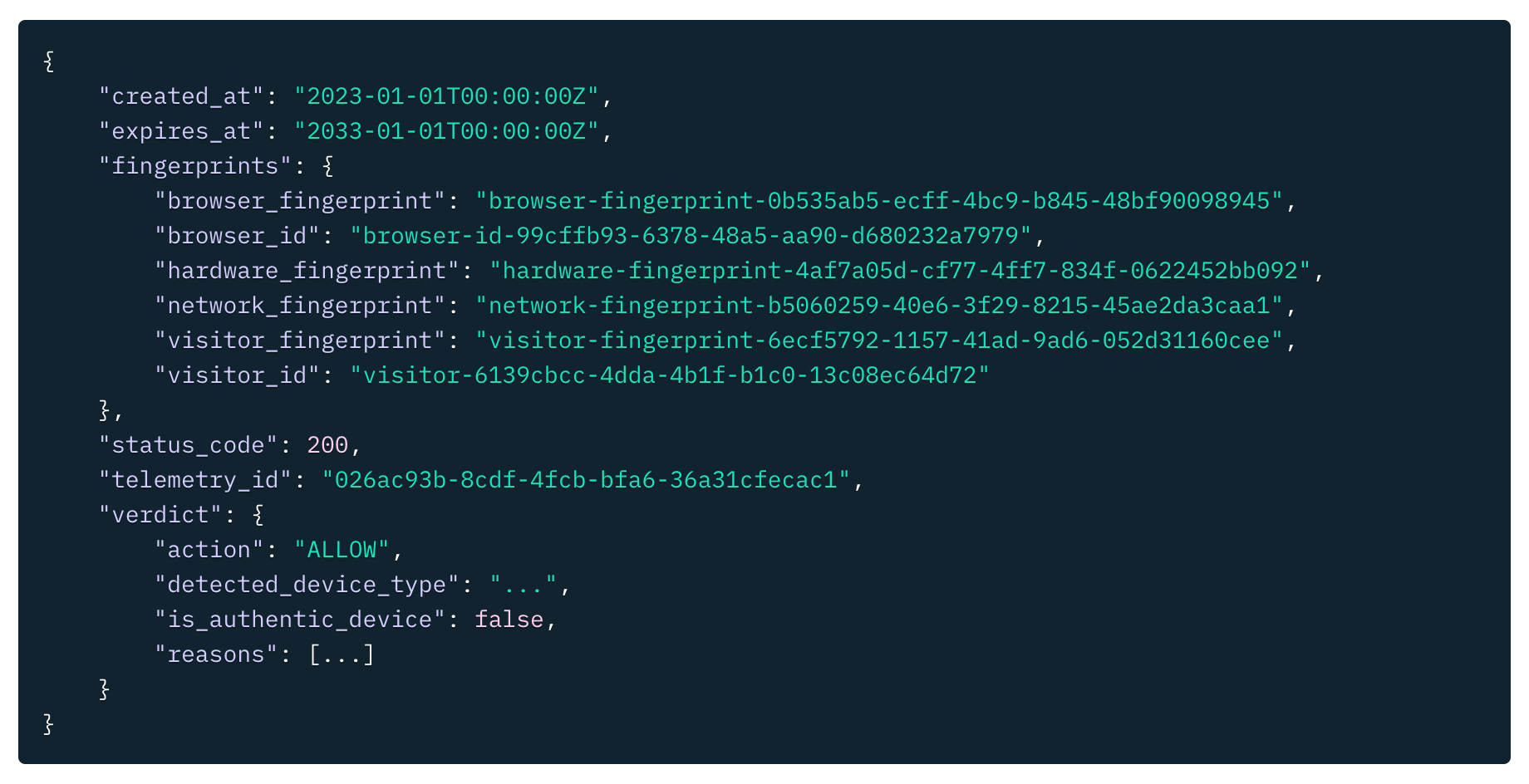
In addition to actively mitigating fraudulent activity, and full API access to customize and monitor activity, Stytch offers a Device Fingerprinting Dashboard with real-time and historical data of the fingerprints, verdicts, and verdict reasons your application experiences.
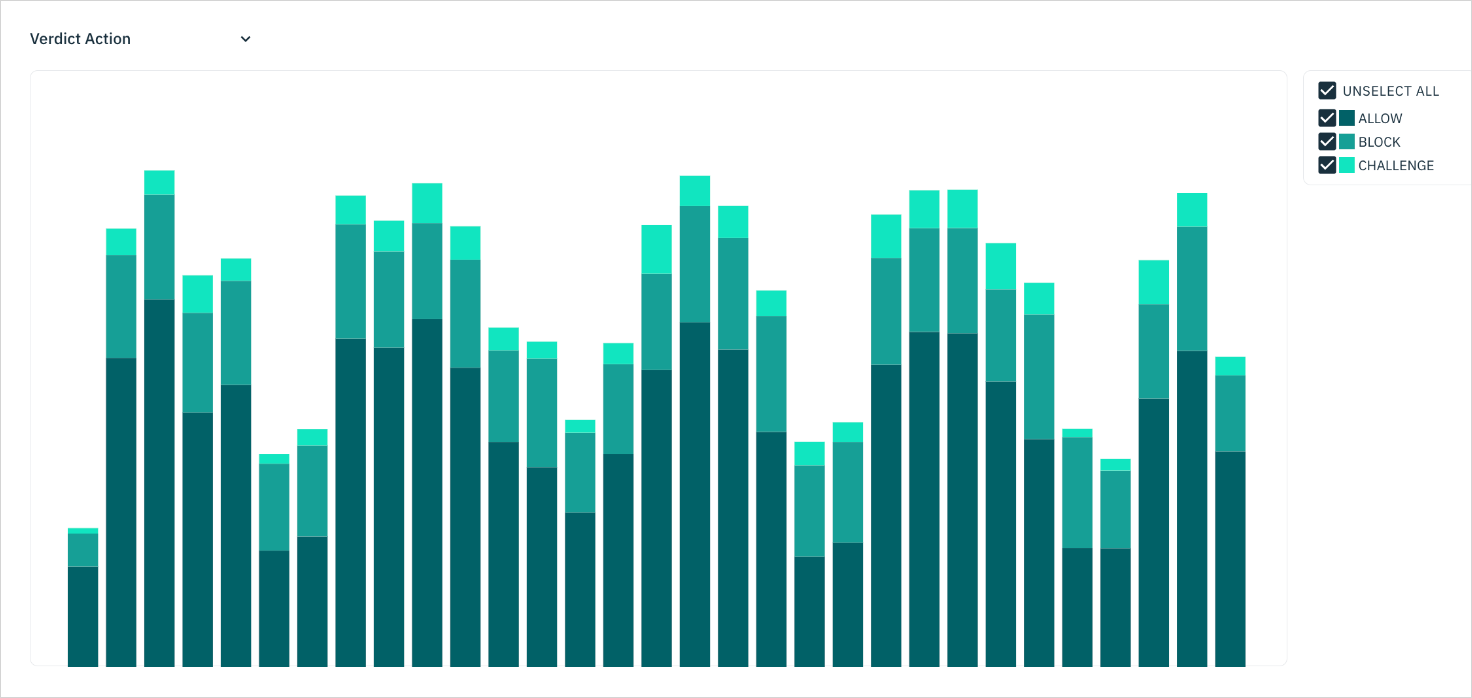
Device fingerprinting real-time monitoring
Innovations in device fingerprinting
Stytch’s approach to device fingerprinting is designed specifically to be tamper-resistant, making it difficult for attackers to reverse engineer or spoof the fingerprinting process. The product’s stability is maintained across incognito browsing, webviews, VPNs, changes to user agent or IP addresses, and other potential manipulations.
Compared to conventional methods, such as rate limits, IP tracking, user verification, and CAPTCHA, Stytch’s device fingerprinting product offers several advantages:
- Stability: Stytch’s device fingerprints remain stable across various conditions, ensuring that the same identifier is associated with the same device, even when the user switches browsers or IP addresses.
- Resilience: Stytch’s fingerprinting process is obfuscated, making it difficult for attackers to reverse engineer or spoof the fingerprint.
- Customizable tools: Stytch’s product provides a set of customizable tools for businesses to accurately identify users by device and take appropriate actions based on the fingerprint review.
By utilizing Stytch’s device fingerprinting product, app developers can effectively combat free account abuse, including both automated and manual recurring abuse. This solution addresses the shortcomings of conventional methods, such as the ability of attackers to circumvent rate limits, IP tracking, and user verification, as well as the emergence of anti-captcha services. By providing a more robust and reliable method of device identification, Stytch’s device fingerprinting product improves application security to prevent abuse and safeguard against a poor customer experience.
Prevent fraud with Stytch
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.