Back to blog
Auth0's Security Incidents: How JWT Vulnerabilities Have Repeatedly Impacted the Platform
Auth & identity
Oct 31, 2024
Author: Stytch Team
Background
In the realm of cybersecurity, even the most sophisticated, high-profile companies can find themselves vulnerable to security incidents. Auth0, a well-known authentication and authorization platform, has experienced its fair share of such incidents, one of the most significant being the alg:nonE re-bug.
The repeated vulnerabilities reveal troubling element’s in Auth0’s security culture and have also come with additional product trade-offs for customers. In addition to the security headache this has posed to customers, this has also pushed Auth0 to limit the flexibility & customization of their platform to try to mitigate the recurring issues they’ve exposed themselves to historically.
For developers who are evaluating Auth0 as an authentication provider, continue reading to learn how these issues could compromise your authentication systems and overall security posture.
The Infamous alg:nonE Recurring Bug
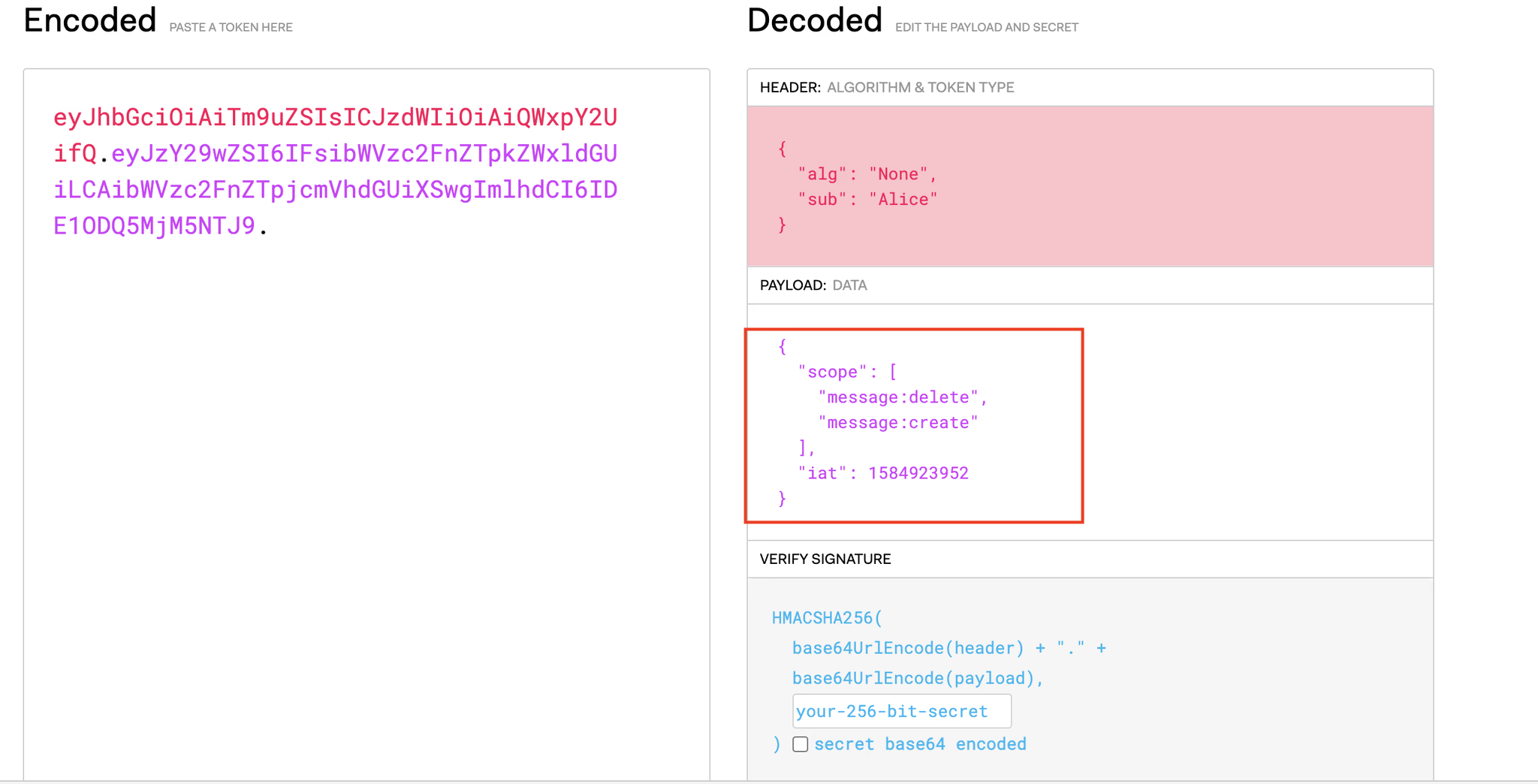
To understand the impact of the alg:nonE recurring bug, it's important to understand what it was and how it exploited Auth0's security systems. Essentially, this vulnerability lay in Auth0's Authentication API and how it handled JSON Web Tokens (JWTs), which are a popular method for securely transmitting information between parties as a JSON object.
The problem surfaced when the Authentication API did not adequately validate a user’s JWT, which is provided in the response upon successful login. Attackers could forge a JWT for any user by creating a JWT with an algorithm of 'none' (i.e. alg: none) and no signature. Auth0’s API would mistakenly validate these forged tokens as legitimate, and return 200 response codes back to the malicious actors.
While Auth0’s Authentication API prevented the user of the lower-case alg:none, it was a case sensitive filter, which meant simply capitalizing any letter (e.g. alg: None or alg: nonE) allowed attackers to forge tokens – this was discovered by Insomnia Security [4].
Notably, this wasn't the first time that Auth0 had dealt with this vulnerability - it was a recurrence of an earlier issue that Auth0 had claimed to resolve less than a year prior. This repeat incident raised eyebrows in the cybersecurity community, as the recurrence of such a fundamental flaw pointed to a deeper issue within Auth0's security culture [3].
Many questioned how the same vulnerability could appear twice, suggesting a lack of rigorous security practices. Stytch works very closely with Latacora, a renowned security consultancy. Security researchers have pointed to the alg:nonE re-bug’s repeat occurrences as a key indicator of a broken security culture at Auth0.
The Impact
The implications of the alg:nonE recurring bug were far-reaching. It allowed attackers to do two things:
- They could bypass multi-factor authentication (MFA) when enabled on the user's account. With a forged JWT, an attacker could exploit Auth0’s API to register secondary factors to their own devices instead of the rightful account owner.
- They could fully bypass authentication in instances where the client application did not also independently validate the token itself. Relying on an auth provider’s token inspection API should be an acceptable method for verifying a token’s validity, but Auth0 was totally compromised in this regard.
Pivot in Product Strategy: Restricting Developer Control and Flexibility
In response to the vulnerabilities and the aftermath of the alg:nonE re-bug, Auth0 made a decisive pivot in their product strategy. To attempt to reduce the impact & time to remediation for future Auth0 vulnerabilities, they introduced an inflexible integration option known as Universal Login.
Universal Login is a mechanism that transfers authentication to Auth0's servers instead of in-app authentication, forcing all user logins to occur on Auth0’s domain. This approach effectively strips the developers of any native code control over the auth flow, placing complete reliance on the external provider to manage the entire process.
By significantly restricting the integration flexibility for developers, this strategy has some security benefits particularly for a company with a history of multiple core vulnerabilities [11] [12] [13], as it centralizes user authentication. By mandating the use of Universal Login, Auth0 could streamline updates to its service, ensuring that security patches and updates are immediately implemented across its customer base. However, this shift has not prevented the recurrence of authentication bypass vulnerabilities on the Auth0 platform.
In other words, Auth0’s inability to create a security culture that could consistently avoid these types of major vulnerabilities led the company to make far-reaching changes to how customers are allowed to build authentication into their applications.
Recent Vulnerability: Authentication Bypass
Additionally, a recent security flaw in Auth0, highlighted by Sentor Security, involved an authentication bypass vulnerability due to session [1]. This issue allowed unauthorized access to protected resources by exploiting weaknesses in Auth0's token validation process.
The vulnerability stemmed from improper validation of certain token parameters within Auth0's authentication flow. Attackers could manipulate these parameters to bypass authentication checks, gaining unauthorized access to sensitive data or services.
This flaw significantly compromised user account security and raised concerns about the overall effectiveness of Auth0’s authentication mechanisms.
Conclusion
The repeated occurrence of vulnerabilities like the alg:nonE re-bug and the recent authentication bypass indicates a persistent issue in Auth0’s security culture. These incidents underline the need for a more robust and proactive approach to security, as recurring vulnerabilities suggest underlying weaknesses in the company's security practices.
The shift towards Universal Login illustrates that a significant strategy pivot is sometimes necessary to manage security risks, but it also highlights the trade-off between security and flexibility.
Auth0’s universal login approach isn’t just a design choice; it reflects an inherent weakness in their ability to deliver secure embedded authentication for developers that require flexible and customized in-app control over their auth flows.
For companies seeking more adaptable solutions, this underscores the value of security vendors who prioritize both robust security measures and flexibility, avoiding the pitfalls of inflexible integration options.
Citations & Sources
[1] https://sentorsecurity.com/blog/vulnerability-disclosure-session-fixation-in-auth0/
[2] https://auth0.com/blog/improving-the-way-you-configure-security-settings-in-the-dashboard/
[3] https://www.bleepingcomputer.com/news/security/auth0-warns-that-some-source-code-repos-may-have-been-stolen/
[4] https://cybercx.co.nz/blog/json-web-token-validation-bypass-in-auth0-authentication-api/
[5] https://auth0.com/blog/auth0-response-to-security-report/
[6] https://news.ycombinator.com/item?id=22890604
[7] https://auth0.com/blog/common-threats-in-web-app-security/
[8] https://news.ycombinator.com/item?id=24346317
[9] https://auth0.com/blog/critical-vulnerabilities-in-json-web-token-libraries/
[10] https://www.akto.io/blog/jwt-none-algorithm-test
[11] https://www.cvedetails.com/cve/CVE-2019-7644/
[12] https://www.cvedetails.com/cve/CVE-2015-9235/
[13] https://www.cvedetails.com/cve/CVE-2015-9235/
[14] https://www.rfc-editor.org/rfc/rfc8725
Switch to Stytch
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.