Back to blog
Why Switch to Stytch?
Product
Apr 11, 2024
Author: MB Crosier
So, switch to Stytch? You might be thinking, “Well, what even is Stytch, how is it different, and THEN why should I switch?” This post is intended to answer all of those questions, plus a few more!
Stytch in a nutshell
Stytch is infrastructure for developers to build auth into applications. Stytch provides a suite of dev tools, including APIs, SDKs, UI components, tailored to support user & org management for a wide range of architectures & use cases.
There are a few things that make Stytch’s approach unique:
Auth and security in one — so your team spends less time integrating different solutions
- Authentication: Login and user management with user linking and SMS/email sending built in (no provider setup required). Plus robust multi-tenancy for B2B apps.
- Authorization: Role-based access control for B2B apps. AuthZ with Stytch starts simple, but comes equipped with out-of-the-box enterprise SCIM integrations.
- Fraud Prevention: Low-friction bot & spam protections (with as few CAPTCHAs as possible). Standalone or combined with Stytch’s authentication products.
- Machine-to-Machine Auth: Because sometimes humans aren’t necessary
Purpose-built products for B2B and B2C – so your team isn’t writing logic adapting a universal solution
- Consumer and B2B apps have different needs!
- Adding B2B features to a B2C data model leads to rough edges for users and internal glue code. And consumer companies don’t want the bloat that comes with a more complex B2B auth model.
- Stytch offers two different auth products, with different data models and features that are custom to each business model.
Implementation flexibility– so your code is streamlined and you can make your auth flow UX your own.
- Rather than a ‘Universal’ or one-size-fits-all model, Stytch offers a range of ways to integrate for both consumer and B2B apps:
- SDKs with pre-built components
- Headless SDKs
- Calling the API directly (for those who want total control)
There’s a trend here: Stytch means less work and less code for your engineering team.
Ok, but why does this matter enough for me to switch?
Well, only you can answer that question. Here’s what we’ll say:
There are really two main reasons that we see engineering teams switch. Either auth is starting to drain engineering resources or it’s limiting your growth.
Losing engineering time
Something we see particularly from in-house auth builds or open-source auth solution users is that authentication maintenance starts to take up a lot of time! Or writing a lot of middleware to make “universal” 3rd party tooling fit use cases that it isn’t designed for.
Engineers find themselves constantly battling bugs, handling downtime & support issues, or writing glue code and if-statements to meet the requirements for one Enterprise customer after another. If auth has started to get in the way of your roadmap, the dev time that switching to Stytch could free up is probably worth it.
Limiting your growth
This takes a lot of forms:
- For a consumer (B2C) app, it might look like losing purchases because the Auth0 hosted redirect makes login slow and decreases conversion. Or spending valuable support time troubleshooting with users who can’t log in.
- For a multi-tenant (B2B) app, you might miss out on growth because you don’t offer SSO as a Sales lever, or can’t support a company that uses two different Identity Providers (e.g. Okta & Microsoft Entra), or aren’t able to enforce MFA for only one customer like the IT team is demanding.
- Or from a fraud/bot perspective, it may be because bots are abusing your compute resources or your AI endpoints and you can’t stop it. Instead of making it easier for users to get up and running, or building exciting new features, your engineers are playing whack-a-mole with fraudsters, with no end in sight.
If any of the above sounds familiar, switching to Stytch is probably worth it.
With Stytch, we cut the time spent on auth to about a tenth of what it would’ve been, and then got to use that time we saved actually building the product we needed. Stytch helped us ship much faster than we would have otherwise.
With Stytch, we cut the time spent on auth to about a tenth of what it would’ve been, and then got to use that time we saved actually building the product we needed. Stytch helped us ship much faster than we would have otherwise.
Table of Contents
A quick guide to the rest of the post, so you can jump around to the most relevant sections.
Why Stytch, by use case?
Why Stytch for multi-tenant (B2B) auth?
We have more detail at stytch.com/b2b, but there are really three key reasons why Stytch is the best choice for B2B authentication:
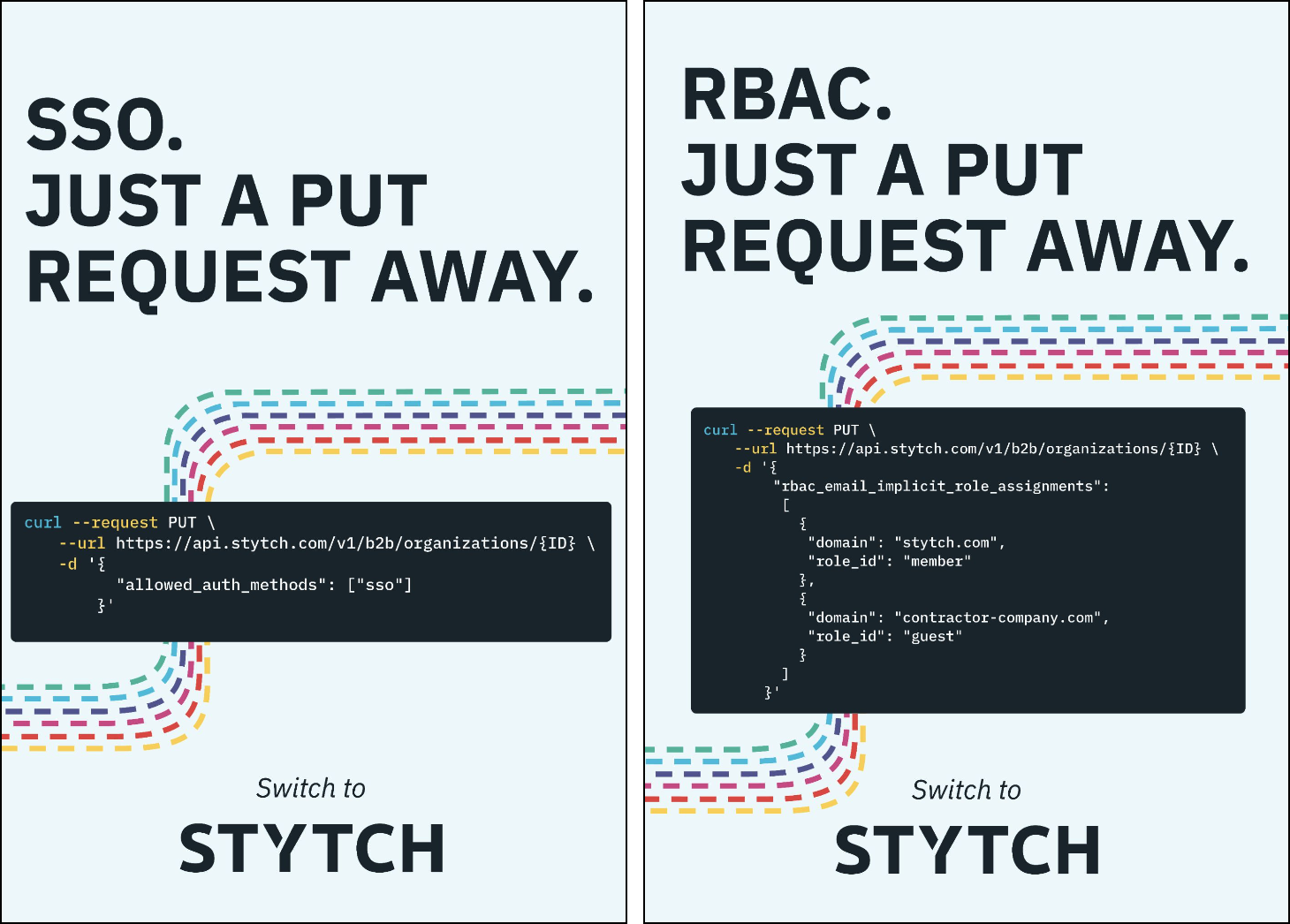
- Architected for multi-tenancy: Stytch’s B2B data model treats organizations as the top-level object, unlike other providers. Stytch supports setting custom authentication settings by organization, and adjusting them with just an API call. Better architecture = more flexibility and less time spent writing middleware, compared to other auth providers with a user-first data model.
- Full-featured authentication and authorization: In other words, Stytch supports all the acronyms: OIDC and SAML SSO, RBAC, SCIM, enforced MFA, JIT provisioning, and more.
- Device intelligence: Someone will always find a new way to abuse your app. This is a harsh reality – even for B2B. Stytch has built-in support for device intelligence, which helps you protect AI resources, compute, and customer data, and keep better track of threat exposure at login.
We’ll go deeper on each of these.
Architected for multi-tenancy
The key differentiator between Stytch and other B2B auth providers is that since B2B is a separate product from the Stytch B2C auth product, we designed it from the ground up for multi-tenant use cases (by comparison, Auth0 Organizations was launched in 2021 as an add-on that B2B teams need to use alongside and integrate with the Auth0 core product.
As part of building explicitly for B2B, Stytch intentionally chose to use a different data model for B2B, where organizations, not users, are the top-level tenant in the data model. We often refer to this as our ‘org-first’ data model, where organizations are the companies that buy and use your product.
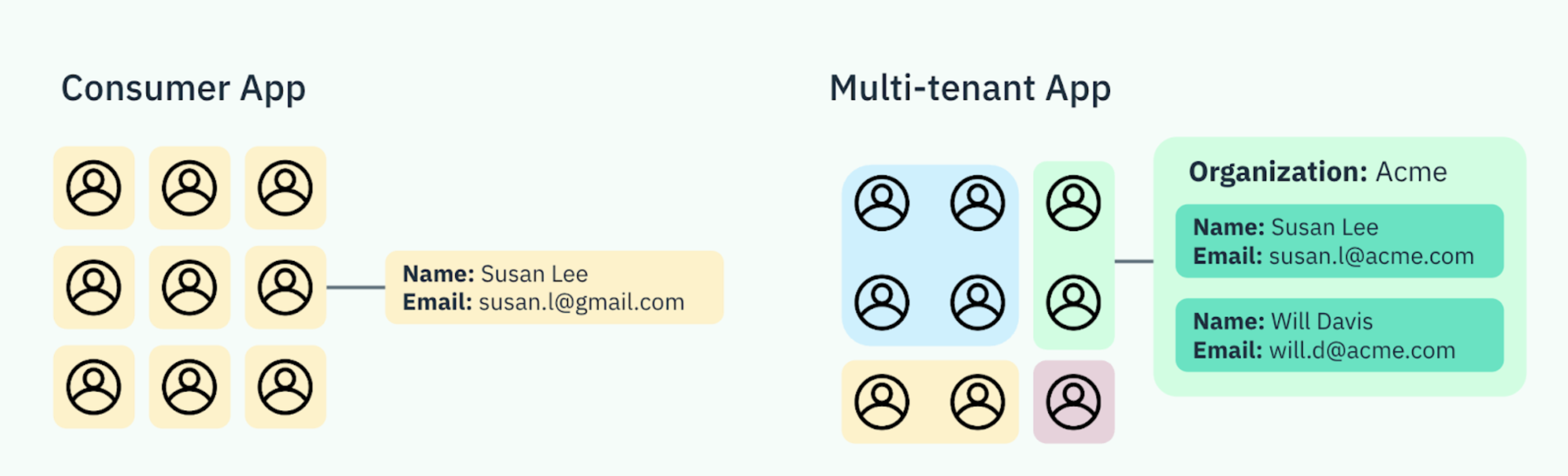
If you’re a B2B SaaS app, your customers are companies – and each of those companies wants full control of who can access their instance of your app, how those users must authenticate, and what they can do once they’re logged in. Without a data model that reflects this organization-driven ownership and control, you’ll quickly run into massive roadblocks preventing you from meeting the security and compliance requirements of your customers.
These roadblocks can start early. A common early pain point is around enforcing the appropriate authentication requirements for each Organization that the end user belongs to.
Example roadblock: Variable MFA settings by organization
We’ll go through a specific example to make it tangible. Imagine you have four customers, Organization A, B, and C, and some users (for example – agencies) need to switch between them regularly.
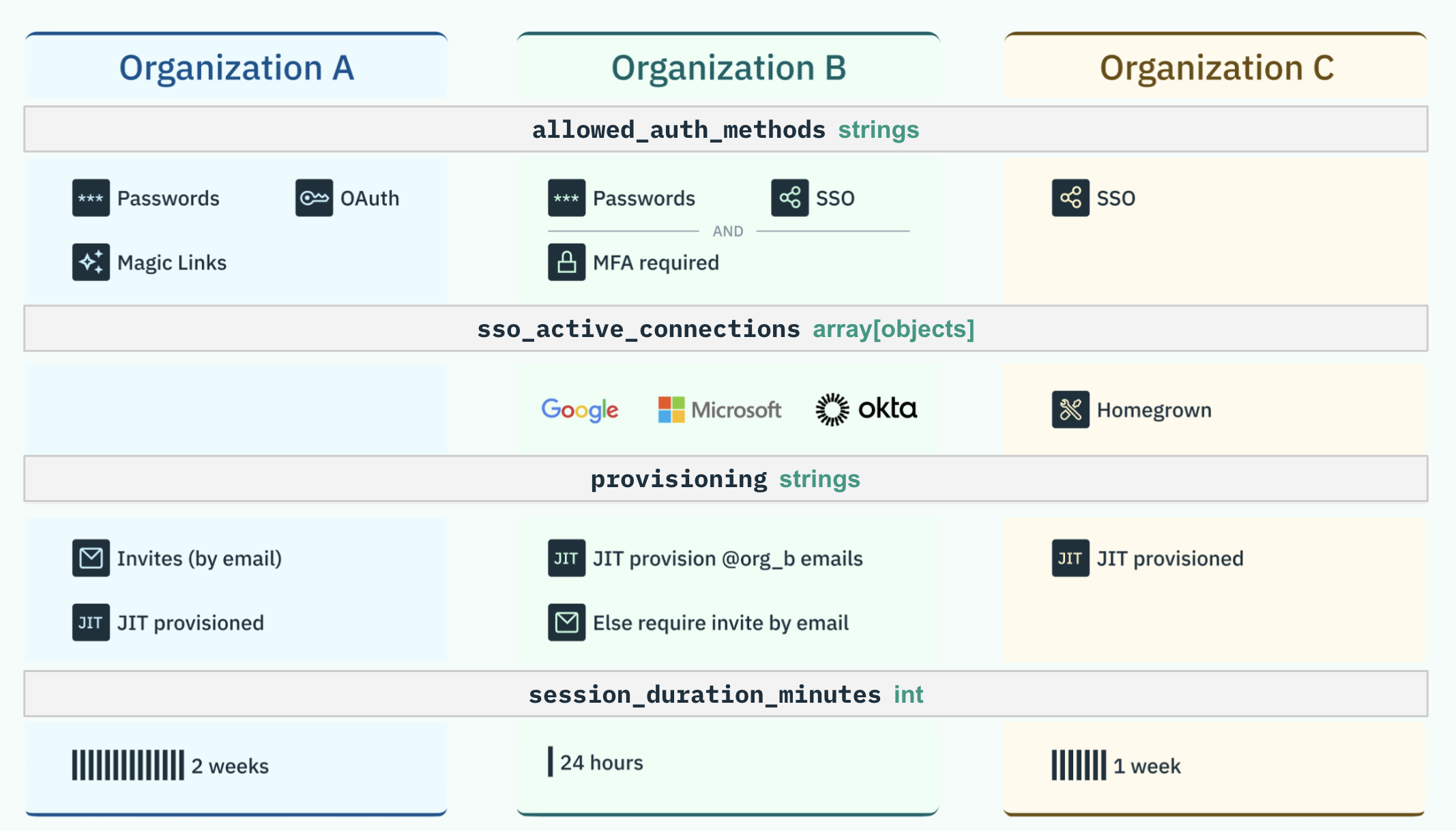
If one Organization, like Organization B, wants to start enforcing MFA – do you require the user to complete MFA before logging into any of their Organizations? What happens if different Organizations require different MFA methods? If the user loses access to their MFA method, who is allowed to reset it for them? Will they be blocked from logging into their other Organizations, too?
In practice, configuring authentication settings by organization
So how would you solve this? Well, it depends on what auth provider you use.
Auth0’s official docs for enforcing org-specific MFA control require writing additional if-else glue code. Vs. with Stytch, you make a single auth method change.
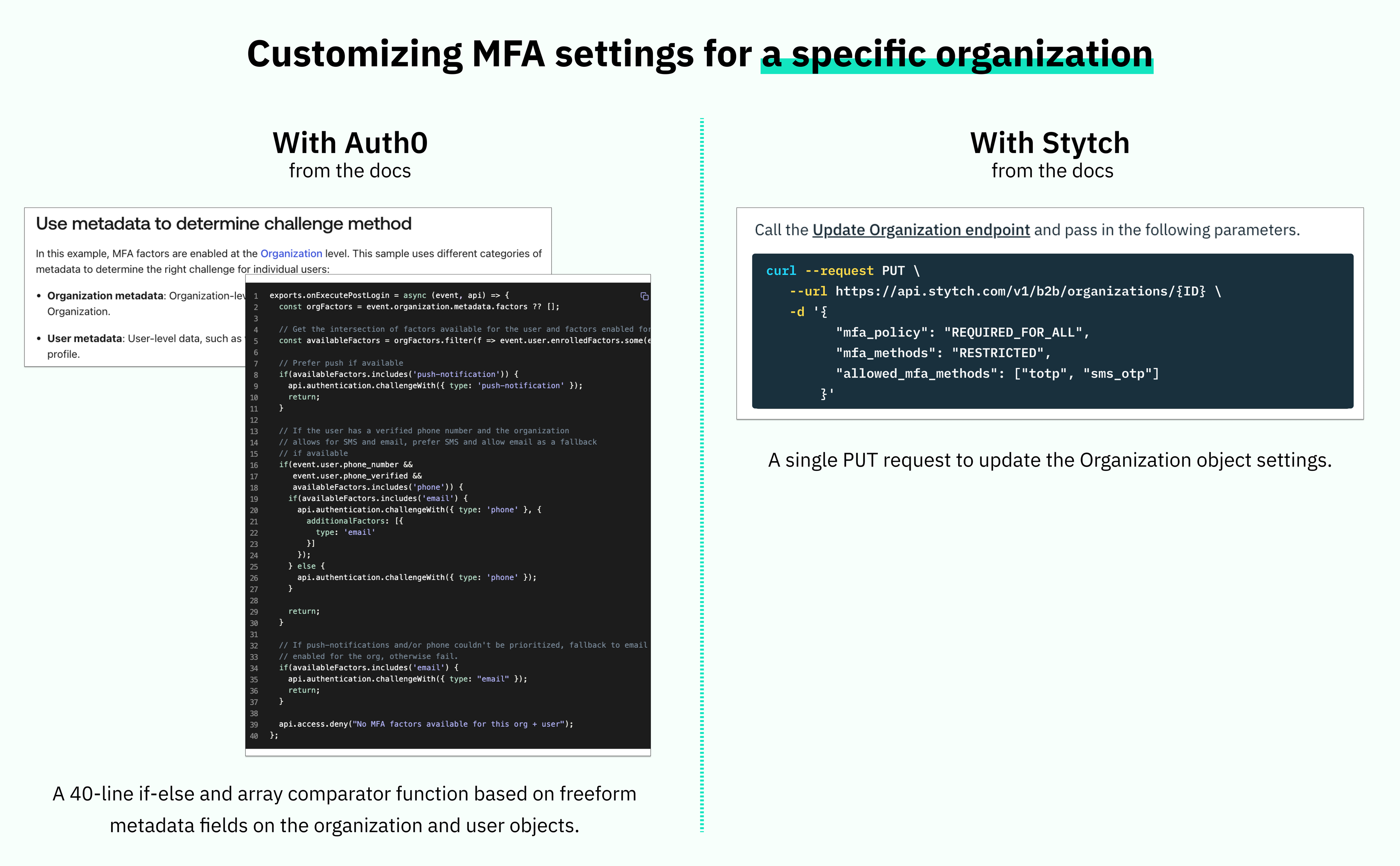
Because of Stytch’s unique data model, this functionality – and the ability to support fully custom authentication settings by organization – is available out of the box.
While this example looked at MFA, the same is also true of setting up just-in-time (JIT) provisioning, or adding SSO – including with more than one Identity Provider (IdP) and both SAML & OIDC.
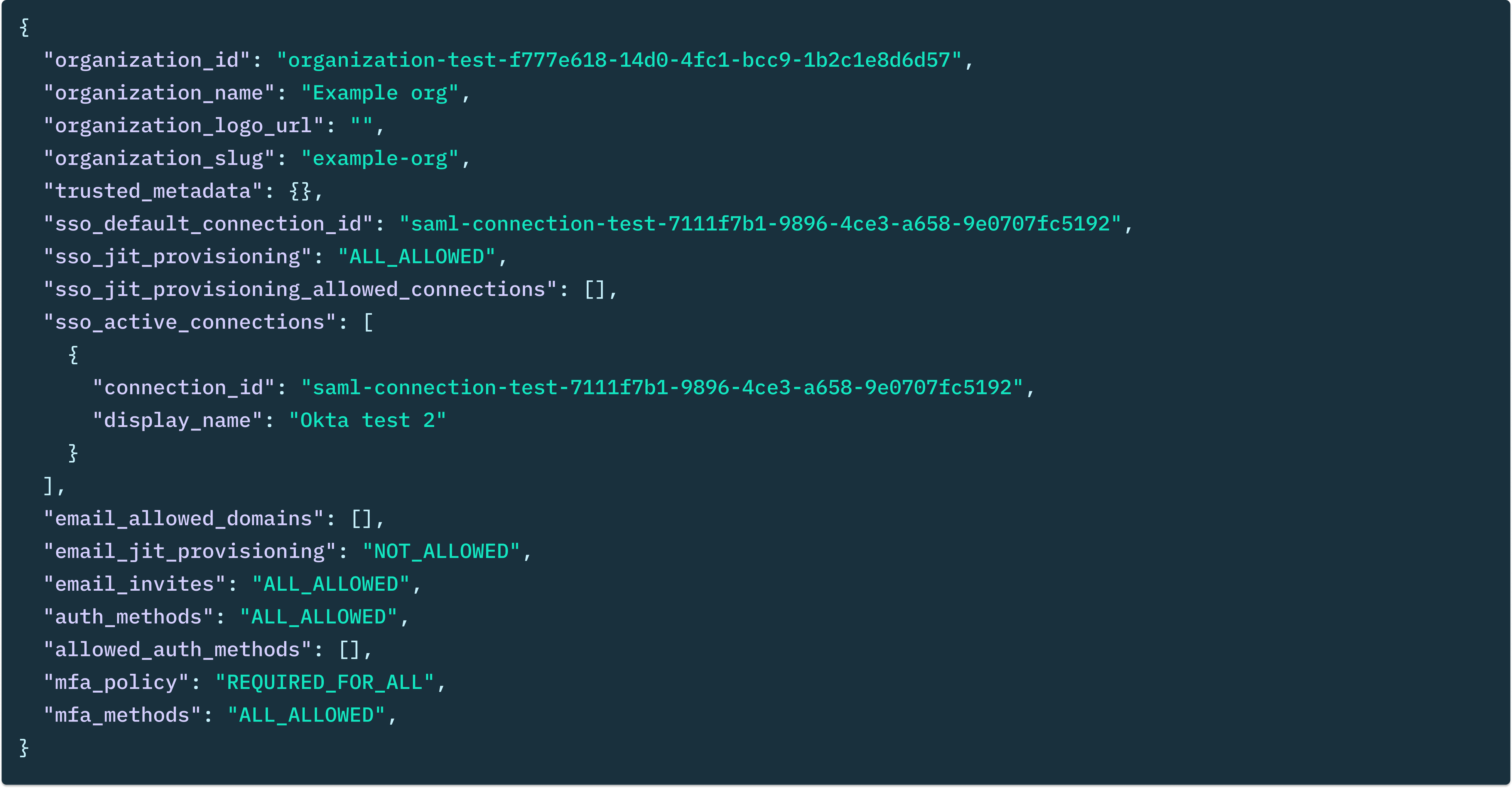
It’s that easy, because the data model allows for it.
As you move upmarket, there are more and more of these situations where this fundamental mismatch between your data model and who actually owns the account can derail enterprise deals or require complicated refactors and migrations. Organization-first sets you up with the necessary foundation to easily satisfy the requirements of both the smallest self-serve startups, all the way to enterprise Fortune 100 companies – with just a single API call.
You can read more about this and see sample code in the Stytch docs.
Full featured authentication and authorization
Enterprise customers request a lot of authentication and authorization features. Stytch has broad coverage – broader than many other players who offer point solutions for SAML SSO, for example – to meet a wide array of Enterprise needs.
IN A NUTSHELL | MORE INFO | |
|---|---|---|
SAML SSO | ||
SAML SSO | Enterprise-grade auth protocol demanded by most large companies so they can manage their users. | |
OIDC SSO | ||
OIDC SSO | Another auth protocol that’s important to support to facilitate Enterprise single sign-on. | |
Enforced MFA | ||
Enforced MFA | Not just multi-factor authentication, but enforced MFA. This allows you to require MFA for users of specific organizations, but not for others, providing. | |
RBAC | ||
RBAC | Role-based access control - ensuring the right people have access to the right things, and nothing more. | |
SCIM | ||
SCIM | A tool that allows IT admins to manage and populate identity changes across systems. | |
M2M | ||
M2M | Machine-to-machine auth; used to authenticate between services. | |
JIT provisioning | ||
JIT provisioning | A process for creating new users and organizations at the time of login. This allows you to dynamically create new accounts & tenants, rather than manually creating them as an admin. | |

Device intelligence
Authentication security hinges on both ensuring that users are who they say they are, and that actors with malicious intent can be blocked swiftly and reliably. By building device intelligence directly into our frontend SDKs, Stytch provides reliable fingerprinting at the point of login. Alternatively, you can deploy Stytch device fingerprinting independently, to protect specific customer data, compute resources, or a free offer. You can learn more by reading ‘Why Stytch for fraud prevention?’
Stytch also applies device intelligence in other unique ways that benefit B2B customers, beyond explicitly reducing fraud. For example, Stytch magic links use device fingerprinting to ensure that when magic links are scanned for security, such as Microsoft Outlook’s Safe Links, they aren’t then followed – and invalidated – by the bot traffic. By applying device intelligence, Stytch ensures the magic link token remains valid and ready to be clicked by a user when the time is right.
This allows you to decrease friction for real, good users, and increase friction for everyone (and everything) else.
Why Stytch for consumer (B2C) auth?
A non-exhaustive list of reasons to pick Stytch for B2C auth:
- Stytch’s separation of consumer and B2B auth avoids overcomplicating B2C; no bloat and no workarounds to support organization multi-tenancy that you don’t need!
- Stytch’s B2C product includes a wide-range of consumer-focused auth factors – such as WhatsApp OTPs, or login with Facebook, Yahoo, and TikTok. All of these are consumer friendly, high converting, and not broadly supported by other auth providers.
- One of the most powerful is support for Google One-Tap, which can increase signup conversion by 10X for consumer-facing companies (and which providers like Auth0 don’t offer)
- Stytch’s solution is not hosted (so no redirect), and offers granular control – including the option to use the API directly. As a result, you have the option to use Stytch’s built-in UIs, but you can also create whatever customization or flow you dream of. Plus, removing the hosted redirect is a boon to conversions.
- Stytch has provider failover for email and SMS OTPs built-in, which means higher deliverability rates and fewer customers who can’t log in and contact support
- Stytch offers secure account deduplication by default so fewer users get locked out, or confused, and you write less (dangerous) spaghetti code to try to link accounts yourself
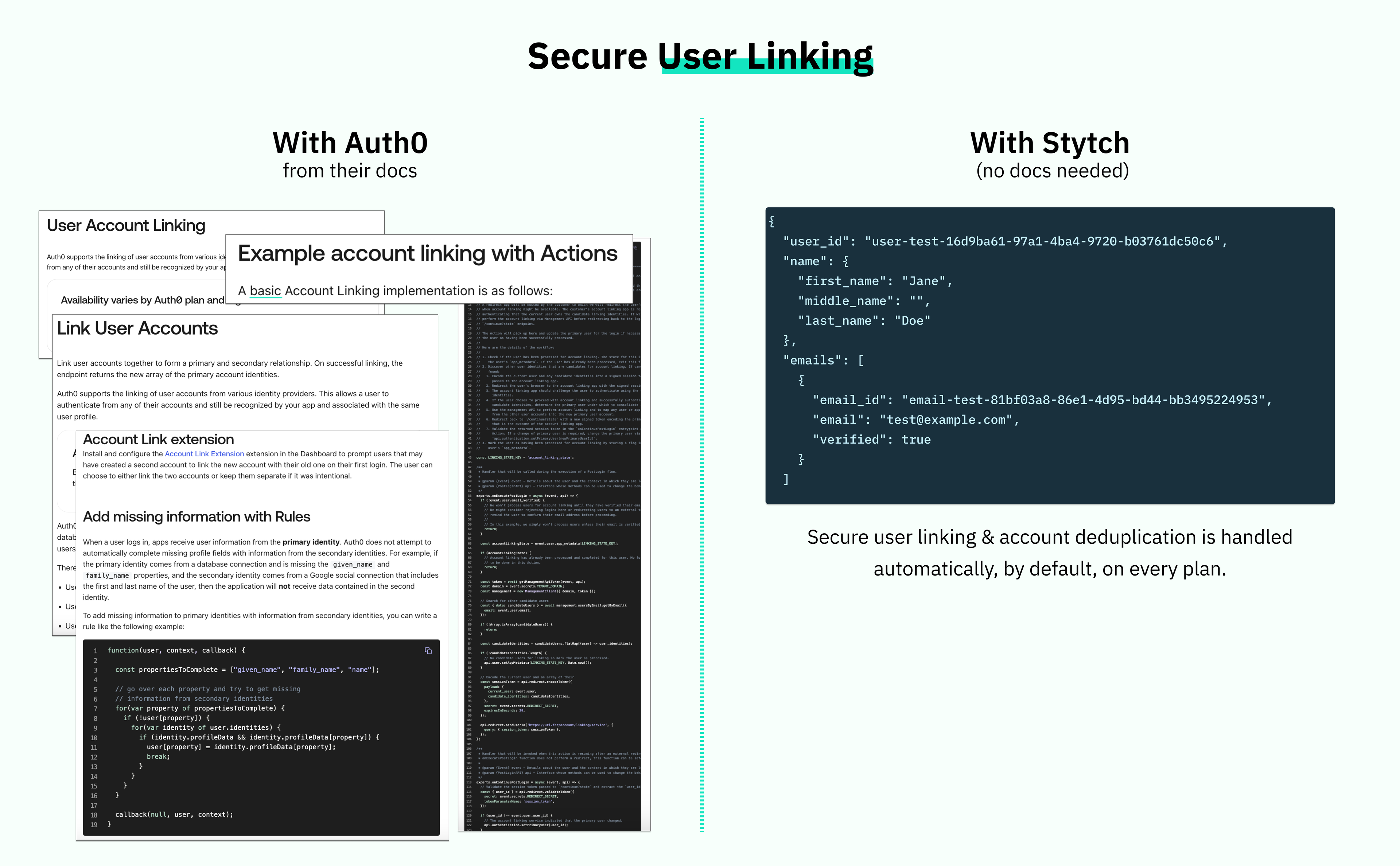
The issue with a Universal Login, is that login isn’t really universal – every app has different needs. Stytch understands that, and is built for it.

Why Stytch for fraud prevention?
Authentication and authorization are the mechanisms by which you get into an app and get access, but they’re also the tools that keep people out and prevent access.
So your authentication flow needs to strike a delicate balance: it needs to let legitimate users in with as little friction as possible, while also defending your app from bad actors who want to access your precious resources – user data, credit card info, API endpoints, AI credits, compute, or something else entirely.
Conventional tools that companies use to address this, like CAPTCHAs, are outdated and ineffective at stopping bots. And there are thriving services that exist to solve and bypass CAPTCHAs at scale.

Most auth providers don’t recognize this, and expect you to rely on 3rd party providers to protect your auth flow, or offer limited tooling that treats fraud prevention as a secondary consideration. If you switch to Stytch, the opposite is true: account security and fraud prevention are baked into our auth model. And the tools we’ve built are so effective that we also sell them separately.
Stytch’s approach to fraud prevention is threefold:
- Protect end users from account takeover (ATO) by offering customizable password strength detection and built-in breach detection
- Use device fingerprinting to better distinguish real people and bots, to show CAPTCHAs to fewer users
- Make CAPTCHAs more effective by ensuring they’re solved where they’re shown – not by a bot, or by an outsourced service
Protect end users from account takeover (ATO)
Stytch passwords come with (customizable) security protections built in: support for password strength strategies like LUDS or zxcvbn, as well as breach detection powered by Troy Hunt’s HaveIBeenPwnd.
This allows you to require users to create secure passwords, and to alert them and require a reset if their passwords have been exposed on the web to limit account takeovers and reduce fraud risk. More info in our consumer docs, B2B Saas docs & on the Stytch blog.
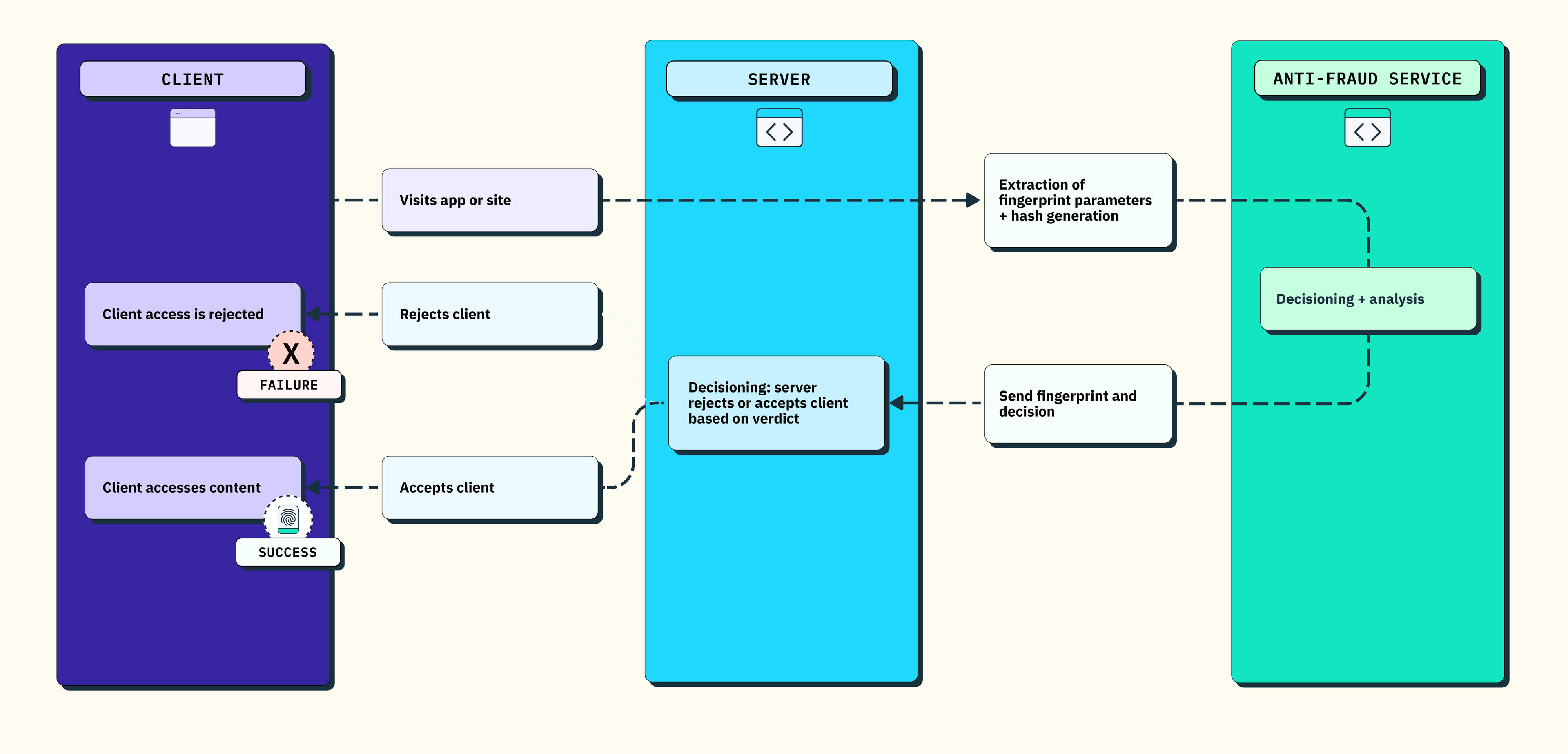
Use device fingerprinting to distinguish humans from bots
Device fingerprinting (sometimes called browser fingerprinting) uses a large number of signals from a visitor’s device and browser (think: IP address, device type, operating system, and more) to distinguish real users from bots or web scrapers. Stytch’s device fingerprinting solution returns a set of unique identifiers for the visitor, device, and network, as well as a recommended action (Allow, Block, or Challenge), to reduce the need to add friction for real users, while preventing abuse by bots or bad actors.
We also very intentionally don’t make our Device Fingerprinting product self-serve, because self-serve fraud prevention products very easily become testing playgrounds for bad actors.
Stytch device fingerprinting can be used as an integrated solution with our frontend SDKs, or deployed standalone. More in our fraud prevention docs, in our Stytch vs. Fingerprint page, and on the Stytch blog.
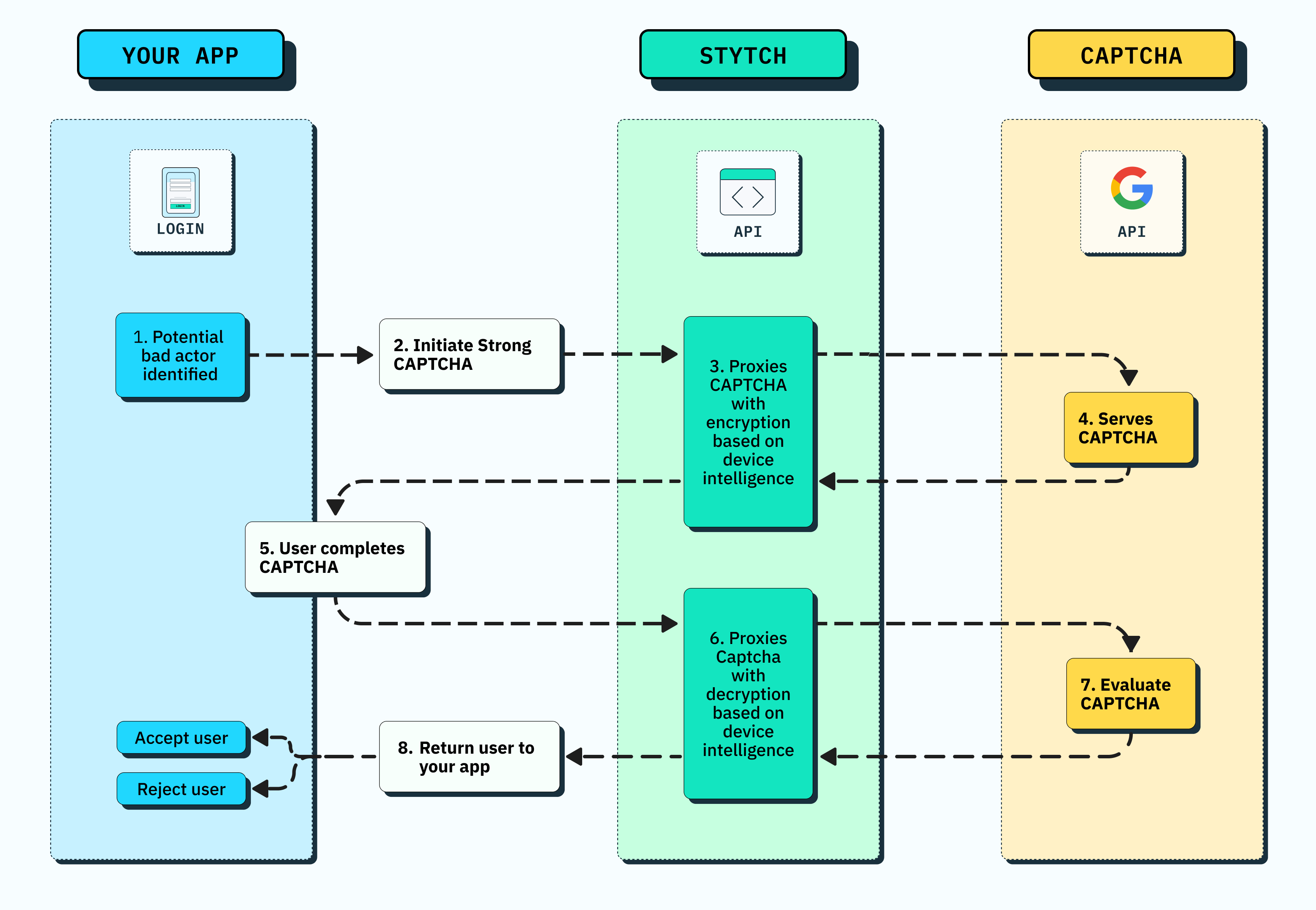
Make CAPTCHAs more effective
When you do choose to challenge a user, traditional CAPTCHAs are not particularly effective solutions. Not only do users find them frustrating, it’s been well established that bots are better at solving CAPTCHAs than humans, that modern AI agents can easily be tricked into solving CAPTCHAs, and – absent that – that a wide array of CAPTCHA solving services take advantage of the public keys that CAPTCHAs expose to outsource CAPTCHA solving at low cost.
Stytch’s Strong CAPTCHA solution works with Google reCAPTCHA to encrypt the payload with proprietary signals specific to the device, network, and user to whom the CAPTCHA was shown. This prevents CAPTCHA solving services or bots from easily manipulating CAPTCHAs at scale, as any CAPTCHA-solver except the original user will have different identifiers from the ones used for encryption.
Paired with device fingerprinting, this means Stytch allows you to show CAPTCHAs only when absolutely necessary, and to ensure those CAPTCHAs can’t be easily solved by bad actors, effectively deterring a wide range of attack mechanisms like credential stuffing. More in our Strong CAPTCHA docs and on the Stytch blog.
To summarize, Stytch offers low-friction fraud prevention tools – both built into our authentication suite and separately – to offer secure login flows without sacrificing on user experience.
Why Stytch, vs. alternatives?
We know you have options! But Stytch offers a level of flexibility and control that many 3rd party providers lack, without the hassle – and security risk – of building and maintaining auth yourself. And we’ll support you every step of the way. Read on for how we compare to specific options – in-house, open-source, cloud/database platforms, and other 3rd party solutions.
Why Stytch vs. building auth in-house?
Please don’t roll your own auth.
If you don’t believe us, pick any web-dev-adjacent Reddit or a CTO Slack Group and make a post declaring that you’re going to build auth yourself. See what you get back 🙂.
Why Stytch vs. open-source auth solutions? (think Keycloak, Nextauth/Auth.js)
At Stytch, we’re big advocates of open source. And the good news about open source auth options is that they’re free and you have full control over the code and the hosting.
The bad news is that you have full responsibility over the code and the hosting, which ends up being a lot of work. Part of the motivation to start Stytch for our CTO, Julianna Lamb, was actually based on her experience working with Keycloak and how challenging it was to manage and scale.
Stytch also handles a lot of the best practices and secondary requirements that these solutions don’t (for example – Stytch will send email and SMS for you (no additional config necessary), complete with backup providers as failover in the case of an outage from Twilio, MessageBird, or similar), and offers broader product coverage – including a wide range of auth methods and fraud prevention tools – so your login flow can evolve more easily over time.
Further, Stytch is built to scale and we invest heavily in our infrastructure, which is why we’re the only auth platform that offers a 99.999% uptime SLA to our Enterprise customers.
As with everything in engineering, though, it depends on your needs! Lucia is a great example of a dead-simple and highly functional auth provider that works really nicely for a Typescript project; but it’s probably not the best choice for Enterprise-grade multi-tenant auth. (hint: the best choice for that is Stytch).
Why Stytch vs. ‘platforms that also include auth’? (think: Cognito, Firebase, Supabase)
The good news about these options is that they’re very cheap, and can be easy to choose if you’re already using other products from that provider.
The bad news is that the reason they’re cheaper is that you’re saving on (1) Caliber of support; and (2) R&D / development focus.
- Support: If you have an issue with AWS Cognito, you will have a very, very hard time talking to a human. If you have an issue with Stytch, ask in our Slack, on our Forum, or via email, and a real human from our team will get back to you promptly (unless a helpful Stytch customer beats us to it). We pride ourselves on high-quality, responsive support; and believe this is an invaluable resource, since every auth implementation is different.
- R&D / development focus: To put it simply, auth is not the primary product for these platforms. It’s an auxiliary offering and a ‘check the box’ rather than how they’re making money. And so the investment in pushing the product forward – fixing bugs, adding new features like Passkeys, ensuring customers can add multi-tenancy without having the ‘development and operation effort… [be] high’ just isn’t there like it is with a dedicated provider.
That said, if you have straightforward auth needs & are using one of these stacks already, the products might be a good choice for your specific use case. And if your needs get more complex, you can always switch to Stytch later (consumer; B2B) 🙂
We offer comparison pages on our website for AWS Cognito & Firebase (aka Google Identity Platform) if you want to go deeper here.
Why Stytch vs. other 3rd party auth providers? (think: Auth0 and a growing list of smaller lookalikes)
This one is more complex to summarize, since every third party auth provider has a different flavor or approach. We have a dedicated page to compare Stytch vs. Auth0 specifically.
That said, a few differentiators about Stytch apply when comparing against almost any other dedicated 3rd party auth provider:
- Stytch splits out B2B and consumer auth to make products tailored to each use case. And Stytch’s unique B2B SaaS data model makes it much easier to build low-friction multi-tenant auth with organization-level customizations.
- Stytch has robust fraud prevention tools, including device intelligence, built into our auth products. This helps to secure your app and mitigate bot attacks, account takeovers, and more, while also reducing friction and 2FA checks for real users. It’s like having a better version of FingerprintJS fully integrated across your auth platform.
- Stytch’s range of implementation options (API, headless SDK, SDK with UI) and broad range of SDKs (Go, Java, Node, Ruby / Vanilla JS, React, Next.js / Android, iOS, React Native) support wide ranges of stacks and implementations, without the restrictions (or redirect!) of a hosted or component-based auth library.
- Stytch includes advanced API primitives to simplify processes like account deduplication and SMS- and email-sending (with provider failover) out of the box. This means easier setup, less glue code, and fewer vendors to maintain.
- With Stytch, you get the pace of development and innovation of a startup, but with funding for the long haul, and Enterprise-grade customer credentials.
We’re also happy to share specific thoughts on a particular Stytch vs. x comparison if you have one in mind. Feel free to join our Slack if you have quick technical questions, or talk to a Solutions Engineer if you’re interested in learning more about Stytch’s Enterprise offerings.

How can I switch to Stytch?
Switching to Stytch doesn’t have to seem intimidating. We’ve done this before, and can guide you through it.
Here’s one of our favorite customer quotes from Tome, because it just about sums it up:
We migrated tens of millions of users from Auth0 to Stytch in less than a month. It was far and away the easiest migration I’ve ever worked on.
We migrated tens of millions of users from Auth0 to Stytch in less than a month. It was far and away the easiest migration I’ve ever worked on.
A few resources that are worth checking out from the Stytch docs:
But most importantly, consider reaching out to our team, either by requesting a demo or dropping us a note in our developer Slack.
We have a lot of migration experience – from Auth0, Firebase, Cognito, in-house, you name it – and are happy to help think through how to make switching to Stytch as easy as possible.
Build auth with Stytch
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.


