Back to blog
How just-in-time authentication boosts security and conversion
Auth & identity
Jul 30, 2021
Author: Reed McGinley-Stempel

Securing your app shouldn’t come at the cost of usability.
Front-loaded, application-based authentication methods have long dominated the security landscape. But these high-friction flows are tedious for users and can negatively impact their experience and your conversion rates.
Now, route-based models are making it easier for apps to verify users without compromising engagement.
Let’s take a closer look at the user access journeys across each of these authentication methods, identify their key differences, and compare their respective levels of friction and convenience.
Upfront friction: application-based authentication
Traditionally, apps have front loaded their authentication requirements. Once users pass a number of steps—typically involving a username and password, security question, and two-factor verification process through SMS or Google Authenticator—they are granted full access to the app and can carry out any action they like, regardless of its sensitivity.
For example, if a stock trading app uses this model, it doesn’t matter whether a user is pursuing a relatively minor, “read-access” task (like checking a stock price or their account balance) or a riskier, “write-access” task (like withdrawing funds). Once they’re in, they’re good to go.
This front-loaded approach is called application-based authentication, because it treats the entire app as a monolith.
The problem with application-based authentication is that it requires users to complete the same high-friction, burdensome flow each time they engage, regardless of the risk level of the actions they wish to take.
Application-based authentication is a relic of the early days of online security, when there was really only one form of verification: the password.
In a password-based world, this front-loaded approach made sense because the password was the only authentication factor. Either you’d successfully enter it and access your account, or you’d be shut out. But with the advent of new methods like SMS, email, and biometrics—which are added to existing password flows—sticking to an app-based approach overcomplicates the sign-in process without offering additional security when it’s needed most.
Security when it matters: route-based (aka just-in-time) authentication
Today, application-based authentication is no longer sensible. In recent years, new methods have emerged, enabling us to verify users more intelligently through a process known as route-based authentication.
In route-based flows, applications only introduce friction when it’s needed, using incremental security for higher-risk actions within an app.
Tasks like moving money, changing credit card information, and accessing personal data all justify this increased security and added friction. At the same time, users pursuing low-risk tasks aren’t burdened with undue verification measures.
Because the process is triggered by a specific, sensitive task and the resulting access is temporary, this approach is also referred to as just-in-time authentication.
So, what does it look like in practice?
Consider an app like DoorDash. Users enter a username and password to access the platform. From there, they can browse local restaurants and even place an order whenever they want without signing back in. But if they try to do something riskier—like change their delivery address—they trigger a two-step, SMS verification process.
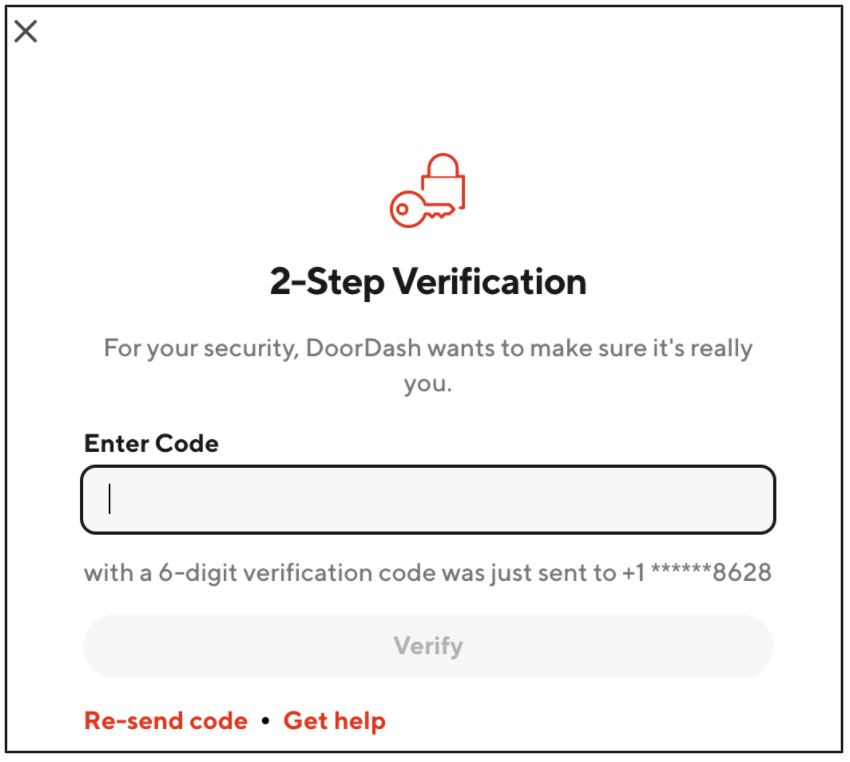
By introducing friction only when it’s necessary for extra security, an app greatly improves user experience—and, in turn, boosts customer conversion and satisfaction.
Breaking it down
Think of these two different authentication methods like security on a house.
With app-based authentication, you’re essentially putting a deadbolt or two (or five) on your front door. To be safe, you have to lock and unlock all of those bolts every time you go in and out. And once someone gets in, they can help themselves to anything in your home.
With route-based authentication, you may have a lock on your front door, but you reserve the extra bolt (or alarm, guard dog, or Home Alone-type setup) for the safe inside holding your valuables. Even if you leave the front door unlocked every now and then to let your friends in, an intruder will still have a hard time getting to what matters most. It’s more secure (and less demanding) because the components are more strategically and conveniently arranged. It’s also friendlier and more welcoming for those who mean your home no harm.
Key takeaways
The days of heavy, up-front app security are behind us, and the future promises more seamless and organic access flows. Integrating route-based authentication methods into your app will help you safeguard what’s most important—while delighting, engaging, and converting your users.
A path forward with Stytch
Stytch is on a mission to eliminate friction on the internet, and our platform supports and facilitates route-based authentication flows across use cases.
Want to learn more about how we do it? Read up on our easy-to-integrate user infrastructure solutions in our API docs.
Interested in trying our platform?
Sign up for free to test out our API.
Helpful terms
Let’s clear up some of the jargon:
- Application-based authentication is a front-loaded security method, where users must pass through a single, heavy-handed verification flow every time they access an app and are then permitted to all its internal tools and services.
- Route-based authentication is an incremental security method, where a user must only undergo extra checks—like two-step, SMS verification—to carry out more sensitive tasks within an app.
- Just-in-time (JIT) authentication is another, less technical term for route-based authentication.
- Step-up challenges are additional steps users are asked to take in order to verify their identity.
Build auth with Stytch
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.