Back to blog
What is identity and access management (IAM)?
Auth & identity
Sep 16, 2022
Author: Stytch Team

Identity and access management (IAM) is a broad term used to describe how organizations manage individuals and devices and control access to sensitive resources. With IAM, an organization can authenticate digital identities, define which assets they can access, and manage these relationships over time.
In an increasingly online world — with more users, more devices, and more threats — IAM plays a critical role in helping organizations protect their data, promote growth, comply with government regulations, and much more.
What are the benefits of IAM?
IAM is utilized throughout large and small organizations because it offers a wealth of proven benefits for enterprise.
Greater control over users
When unauthorized people have access to confidential and privileged information, an organization is at risk of costly data breaches and identity theft, among other issues. These concerns only grow as workforces remain highly distributed, and operate in fast-paced environments.
The primary purpose of IAM is to control who has access to information and assets, which is especially important if you are dealing with privilege creep (when access privileges expand unnecessarily) or large numbers of users being onboarded and offboarded.
With IAM, you can:
- Manage and track nearly every aspect of a user’s identity and permissions.
- Quickly and accurately see which users can access any specific asset.
- Grant granular permissions to ensure that users only have access to assets that are relevant to their work.
- Change privileges across the enterprise as groups and teams evolve and security policies are updated.
- Incorporate proven security-related platforms and features such as single sign-on (SSO), which promotes good password hygiene by reducing the need for users to track and manage multiple credentials.
- Collaborate more easily and cost-efficiently with third-party contractors, customers, and other outside groups by granting them controlled, secure access to your network.
Cloud-based IAM provides additional benefits, including controlling access with browser-based SSO.
Protect sensitive data, credentials, and other assets
Consider all of the digital threats to your organization, including hacking, phishing, and stolen passwords. These risks are directly related to unauthorized user access. By allowing you to control, manage, and limit user access through a centralized system, IAM helps keep your information safe and mitigates your risks.
An automated approach
Humans make mistakes. Automating the processes that are used for IAM helps minimize (or even eliminate) the human errors typical in manual account setup, permissions, and tracking processes. In addition to improving security, automation saves your IT department time and money by reducing the number of help desk requests for password resets and related tasks.
How does IAM work?
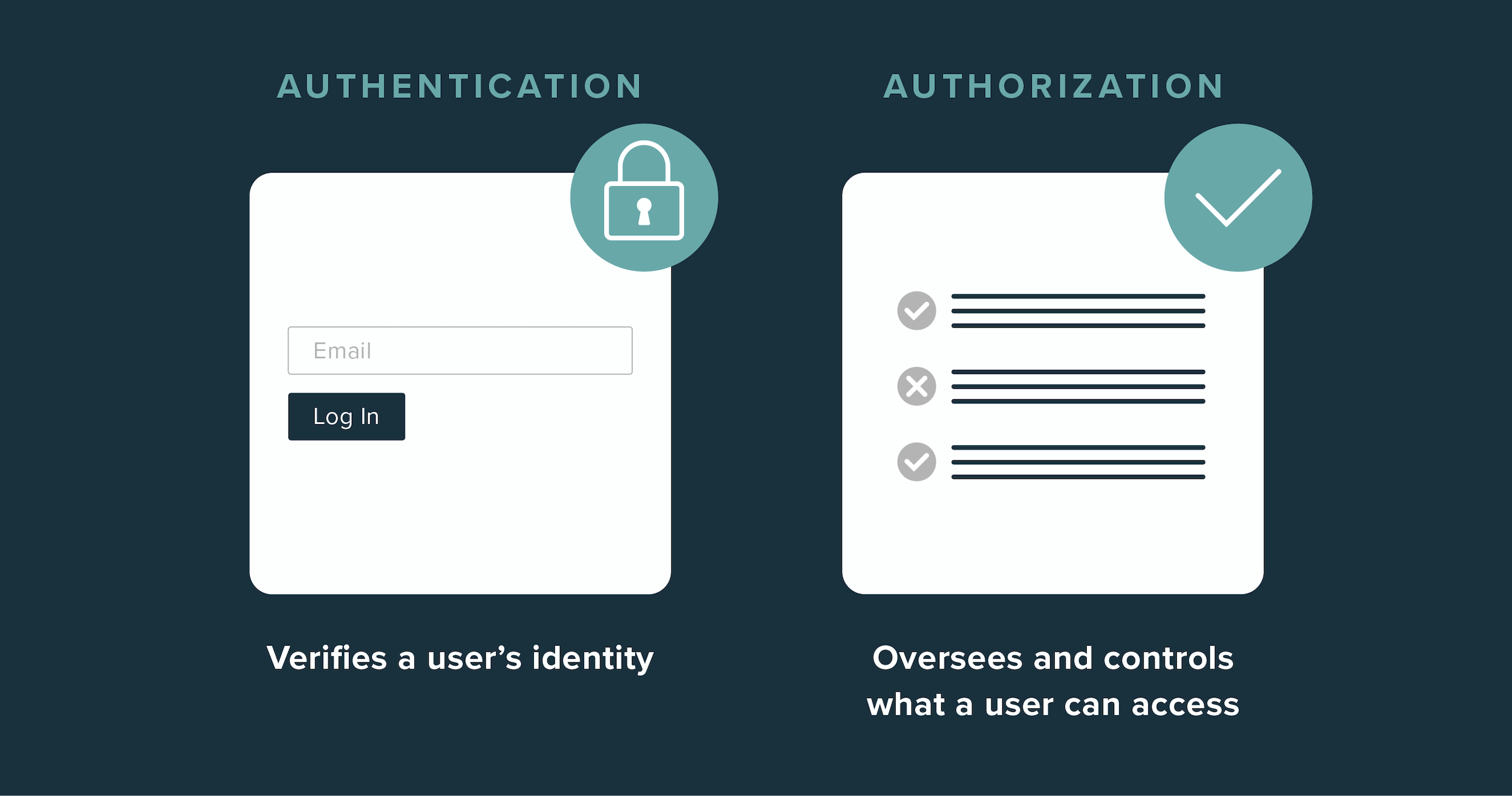
IAM enables access to an asset based on the identity of the user, device, or thing (such as an application or API) that is trying to access it.
The process starts with identifying individual users (e.g., employees and customers) and devices (e.g., smartphones, laptops, and servers) that could potentially access data, systems, and other assets. Each individual or device is assigned one identity.
Enterprises then manage these identities through a centralized service, which may be on-premise or cloud-based. Managing identities includes adding users, modifying their information as their responsibilities change, and removing their privileges when they are no longer authorized. Every identity will be granted access to assets based on the roles associated with the individual and/or group.
Authorizing identities is typically an automated process based on the user’s location, role, job title, and other information. For example, a customer will have different authorization than an employee, and a vice president will likely have more access to more systems than a manager. Customer IAM (or CIAM) involves authorizing access for customers based on their identity, while workforce IAM typically applies to an organization’s employees, partners, and vendors.
An IAM system will also incorporate auditing and reporting processes, as well as ways to regulate user access. While passwords and software tokens were often good enough to regulate access in the past, in recent years organizations have adopted more advanced IAM technologies, including multi-factor authentication (MFA), privileged access management, biometrics, and machine learning.
Ideally, the end result is that users can access the information they are authorized to access — and only that information — throughout their relationship with the organization.
Looking for an IAM provider? Try Stytch today
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Challenges, risks, and how to address them
IAM is a flexible tool that can help organizations stay ahead of ever-evolving threats and attacks. However, as with any security protocol, there are additional factors to consider both before and after implementing IAM.
Ultimately, the goal is to balance ease of use with the security and compliance needs of your organization. Some of the challenges and risks of IAM include:
- Establishing centralized authority for an IAM system (and the resulting policies, documentation, and access approval process) may require new governance entities and cross-unit collaboration.
- Understanding the enterprise’s needs requires a thorough examination of each audience (including their specific access requirements and risks), how to manage access across disparate business units, and how effectiveness will be measured, among other concerns.
- Onboarding (including birthright access given upon joining an organization) and offboarding necessitate changes in permissions; keeping up with these adjustments may require automation, auditing systems, and other resources.
- Cross-platform issues between applications (including cloud-based and in-house apps) may require SAML and other tools to bridge gaps.
- Managing cloud architectures such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform may be a challenge, as each provider can have their own unique policies, best practices, and security challenges.
- Evolving standards for IAM and related technologies, including open-standard platforms, requires ongoing vigilance to stay up to date.
- Additional systems may enhance security but also introduce risk; for example, biometrics is an advanced tool for authenticating identity, but storing biometrics data adds an additional concern.
IAM’s role in a security stack
The broad applications for IAM throughout an organization make it exceptionally useful. However, this enterprise-wide impact can also make it challenging to define responsibilities, establish clear guidelines, and ensure that IAM is being properly implemented—especially since it may not fit neatly within a traditional security stack.
Here are some things to keep in mind:
- IAM is not just for IT. Numerous departments need to be involved in determining what resources will be managed through IAM and which users in the organization will have access to each specific resource.
- Leaders must consider how IAM will be used to authenticate people as well as APIs, application keys, and similar items.
- Access guidelines must also be updated, maintained, and reviewed to protect valuable assets as users and resources change.
A critical part of compliance
IAM is a commonly used tool to help achieve compliance, given that it can regulate access to data (including vendor access), manage inactive accounts, restrict password access, and achieve other compliance-related mandates.
Many organizations are required to follow certain government regulations and guidelines, which may include:
- FERPA (Family Educational Rights and Privacy Act)
- GDPR (General Data Protection Regulation)
- Gramm-Leach-Bliley
- HIPAA (Health Insurance Portability and Accountability Act)
- NIST (National Institute of Standards and Technology)
- PCI-DSS (Payment Card Industry Data Security Standard)
- SOX (Sarbanes-Oxley)
- US state-by-state privacy laws
With IAM, companies can demonstrate that data is being used appropriately (including following least privilege, in which users only have access to necessary resources), meet their compliance goals, and provide information for auditors as needed.
Digital authentication methods
IAM gives an organization the flexibility to choose the digital authentication methods that best serve its purposes and goals. These digital authentication systems affirm a user’s identity and authorize their access to approved resources.
- Unique passwords are used more than any other type of digital authentication. They are often complex by design, with long combinations of upper- and lowercase letters, as well as numbers and symbols (which is why SSO is often employed to help users remember them).
- Pre-shared keys (PSK) are shared passwords that allow authorization to WiFi and other common resources. While they offer convenience, they provide a lower level of security and may not be changed as often given the impact on a large group of people.
- Behavioral authentication is an advanced technique (often involving artificial intelligence) that analyzes how an individual user is typing on their keyboard, interacting with a tablet or smartphone, or using their mouse. If the user’s actions do not match the approved patterns, authorization can be denied or revoked.
- Biometrics provide a higher level of security, as they rely on unique user characteristics including (but not limited to) their fingerprints, voices, and irises. However, organizations that collect and/or store biometric data must have a thorough understanding of the privacy risks, security concerns in the event of a data breach, and ethical issues.
Consider Stytch for your IAM needs
As authentication remains a primary concern throughout an enterprise, the benefits of IAM are clear. Stytch is an identity access management platform that provides a single, unified view of customer identity and activity across all channels and devices. It enables organizations to quickly and securely authenticate customers, authorize access to applications and data, and track and manage customer activity.
With our simple API and flexible SDKs, you get secure and high-converting authentication out-of-the-box but retain the ability to own the UX of your application. One of the key advantages of Stytch is the simplicity of our products. Our platform is easy to use for both administrators and end users and offers a comprehensive product suite that includes MFA and SSO capabilities. Sign up for a free account to get started, or contact support@stytch.com to discuss your IAM needs and learn more about how Stytch can meet them.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.