Back to blog
The importance of investing in unphishable authentication
Auth & identity
Oct 13, 2022
Author: Stytch Team

If you follow business news outlets, you’ve likely heard about the data breach that infiltrated Uber’s security in mid-September. It’s only the most recent in a string of similar security incidents that have impacted companies like Twilio, Okta, Microsoft, Samsung, Cisco, and other companies just this year. The common thread in all of these attacks? The use of phishable authentication factors, or sensitive user credentials that hackers can intercept and use to break into an account. In this post, we explain how these data breaches happen and how you can rely on unphishable authentication methods — like WebAuthn — to stop them from happening to you.
How phishing attacks bypass traditional MFA
Now, you may be asking, didn’t Uber use multi-factor authentication (MFA) to protect its sensitive data? And the answer is probably yes. But MFA can still be vulnerable to phishing attacks, which use social engineering tactics — like an email that mimics a password-reset flow or a push notification granting access — to trick employees into divulging their credentials. While phishing attacks often target passwords (something a user knows), they can also undermine auth methods that are typically used as secondary factors in an MFA flow, like SMS one-time passcodes, push notification, or email magic links. In fact, any factor tied to a user’s phone number or email address (something a user has) can potentially be rerouted at the source and compromised by a determined hacker.
What unphishable MFA does differently
Unphishable MFA offers industry-leading security by relying on asymmetric or public-key cryptography. That means valuable data, like factors that grant access to a server, are encrypted using both a public and a private key. While the public key is stored on the server, the private key can only be activated by a specific user. To gain entry to an account, both keys must be triggered, with the private key sending a customized message to the public key to grant access. To break it down, this two-part MFA flow is immune to remote phishing attacks because it:
- Requires physical interaction with a specific device, meaning there’s no text-based secret code or password for a hacker to intercept.
- Generates unique keys for every exchange, so they cannot be reused across multiple platforms.
- Binds a user’s login to the site of origin, so they cannot be used on a fake or replica site.
- Does not store or send private-key data over a public network.
Add unphishable MFA to your app – switch to Stytch
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
The evolution of WebAuthn
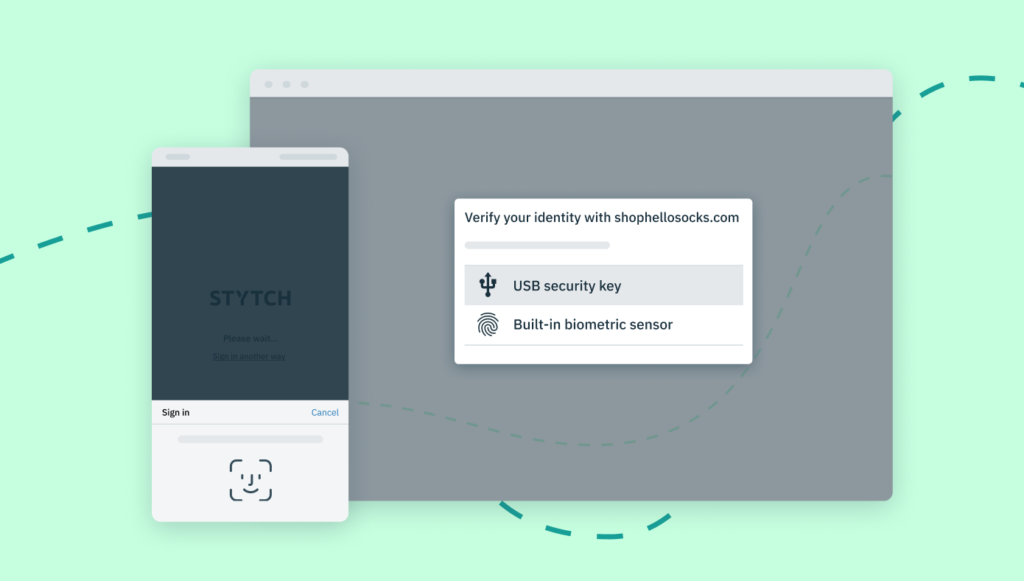
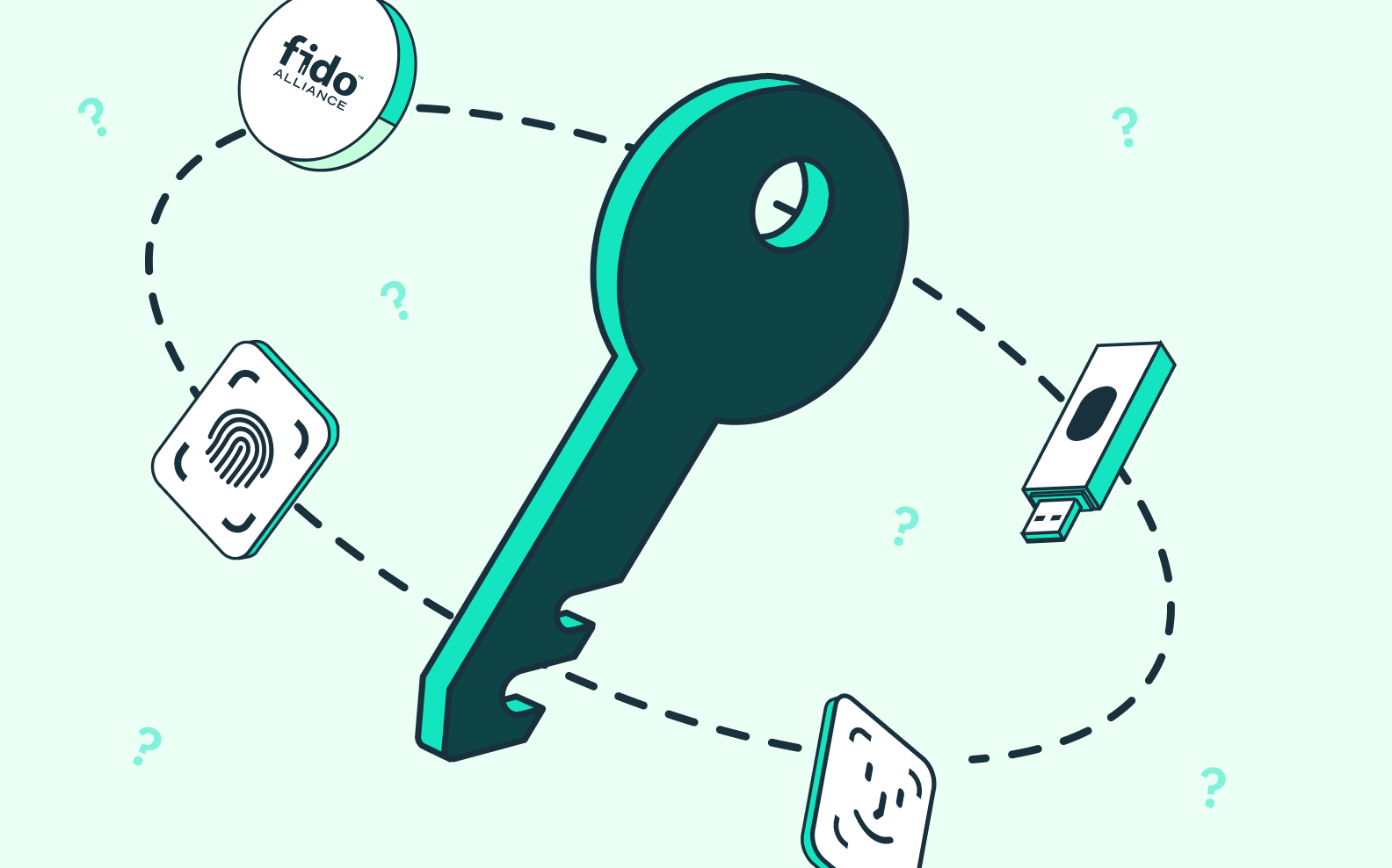
WebAuthn is one of the leading forms of unphishable MFA. It encompasses three different categories of device-based authentication factors that can be used to verify a user’s identity:
- Built-in biometrics like TouchID and FaceID. These auth factors fall into the something-you-are camp. They involve the unique attributes of a user’s body, including fingerprints, retinal scans, and facial features.
- External hardware keys like Yubikey. These auth factors fall into the something-you-have camp. They involve a physical security key that is inserted into a user’s device.
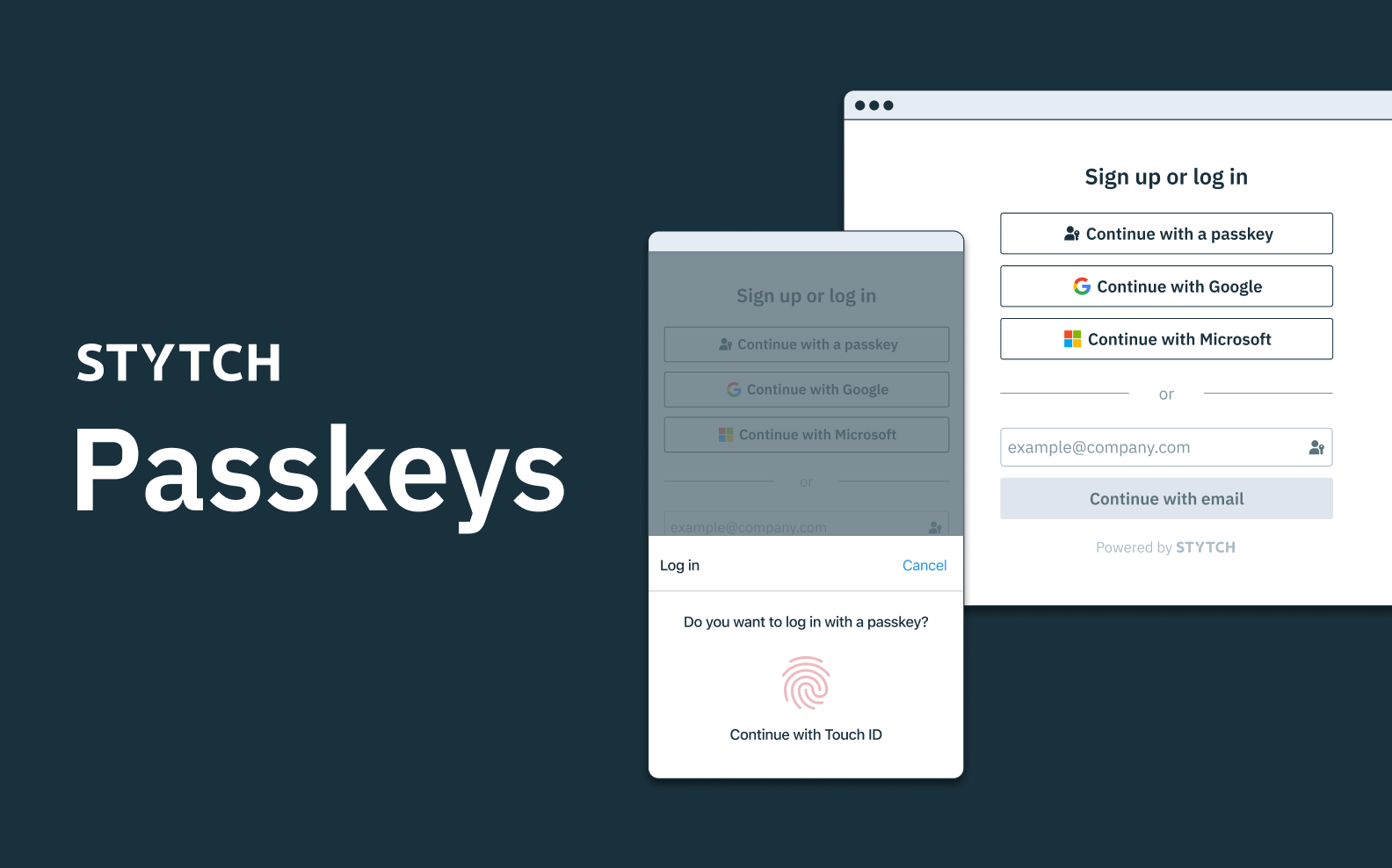
- Passkeys which are an adaptation of built-in biometrics combined with public key cryptography that makes them compatible across devices and even across operating systems.
While WebAuthn has seen relatively low commercial adoption to date, it’s set to ramp up in the coming years, thanks to three significant advancements:
- Passkeys are revolutionizing the WebAuthn user experience: With passkeys, users can now leverage the advantages of WebAuthn, without any of the drawbacks or impediments that made using it so cumbersome.
- The WebAuthn developer experience is improving. While WebAuthn has historically been fairly complex to integrate, major auth providers (like Stytch) have worked hard to enhance its usability, resulting in WebAuthn solutions that can be implemented in under an hour.
- WebAuthn is becoming more affordable. One of the key barriers to entry for WebAuthn has been cost, with incumbents like Okta and Auth0 treating it as a premium feature and charging at least $30K a year for access. But the auth market is expanding, and the pricing of top security products has grown more competitive. In particular, pay-as-you-go pricing models mean developers can now tap into WebAuthn for a few pennies per active user.
- Businesses are waking up to the value of unphishable MFA. Specifically, security and compliance teams are seeing the increasing prevalence and consequences of phishing attacks. These are the teams that spearheaded the widespread adoption of single sign-on (SSO) technologies years ago, and they’re catching on to the weaknesses in conventional SSO that newer solutions like WebAuthn can remedy. Soon, phishing-resistant MFA may be a similar requirement for signing an enterprise deal just like Single Sign-On support is today.
As the auth industry continues to advance — and with the introduction of adjacent technologies like Apple Passkeys that make the use of biometrics easier and more universal — we expect WebAuthn to become an even more popular way to neutralize the risk of remote phishing attempts.
Key takeaways
Adopting next-level authentication measures like WebAuthn isn’t just about keeping up with the latest security practices. It’s about protecting your users and your platform against real cyber attacks that are wreaking havoc on even some of the world’s biggest corporations. It’s as simple as investing in a comprehensive auth strategy that gives you access to a variety of robust solutions at once — and ensuring they include unphishable MFA factors that can defend your data against the worst that hackers can throw your way.
Discover the benefits of unphishable authentication
If you’re interested in learning how unphishable MFA factors might work on your platform, reach out to Stytch’s team to book a free consultation. You can also check out our Slack channel to join daily discussions on all things auth.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.