Back to blog
Balancing security and adoption: preventing account takeover fraud with multi-factor authentication
Auth & identity
Feb 1, 2023
Author: Stytch Team
Since 2017, hackers have stolen 555 million passwords on the web. As a result, most security professionals consider passwords to be “pre-breached” when designing identity and access management for their applications – when you onboard a user, you have to presume that the password they’re using is either already compromised or likely to become implicated in a future data breach (after all, 45% of US companies suffered a data breach in 2021 and this figure continues to rise). In today's digital landscape where we have to assume that a user’s password is or will soon become compromised, multi-factor authentication (MFA) is a necessity for protecting against account takeovers and fraud.
However, as an engineer, it can be challenging to determine which MFA options for your application strike the right balance between security and user adoption. Effective MFA adoption is dependent upon consumer access and usability, which is why we continue to see the popularity of less secure options like SMS passcodes far outpace phishing-resistant options like hardware keys or device-tied biometrics. In this post, we'll take a closer look at the different MFA options available, their relative security, and how to increase user adoption.
To ground this discussion in real-world data, we'll draw upon Coinbase’s recent "Authentication Matters" article which shines a light on MFA types and the associated account takeover fraud. In this article, Coinbase provides detailed statistics on the cryptocurrency exchange’s customer adoption rates of different MFA options and the associated account takeover rates. It’s rare and commendable for a company to offer this level of transparency, and we believe that this data can be valuable for other engineers considering which MFA options to support and how to promote user adoption to prevent account takeover.
Coinbase’s case study: why the most popular MFA option isn’t the most secure
Coinbase’s data provides a great case study on both MFA adoption and security. Coinbase stores cryptocurrency on its exchange, which makes it a uniquely valuable account for hackers to target due to both the monetization potential and the irreversibility of cryptocurrency transactions on-chain. In other words, a hacker can make a lot of money off of a stolen Coinbase account. As a result, Coinbase requires all users to have MFA, but they provide multiple options:
- SMS one-time passcodes (OTP)
- Time-based one-time passwords (TOTPs)
- Push notification via their app
- Physical security keys (e.g. YubiKey)
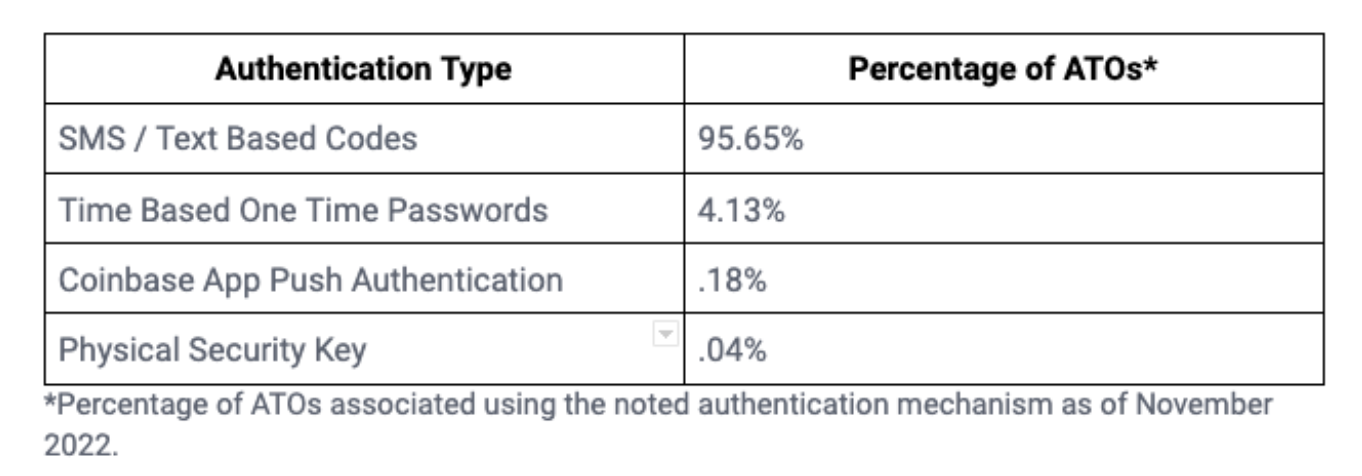
And their experience with both adoption and account takeover fraud rates illustrates the relative benefits and drawbacks of these various methods. For example, Coinbase discovered that their most popular 2FA option with users (SMS passcodes) is also the least secure – 95% of users opt for SMS, but this also accounts for 95% of successful account takeover attacks.
A particular MFA type’s user adoption rate being correlated with account takeover rate isn’t surprising in a vacuum, but it is more of an indictment of SMS 2FA when you consider Coinbase’s attack surface and hackers’ incentives. The majority of customers’ funds on Coinbase (57%) is held in accounts that are protected by a 2FA option other than SMS (either TOTP, push notification, or a physical security key). From a hacker’s perspective, they are most incentivized to target user accounts that hold larger amounts of crypto if the effort to attack those accounts is similar.
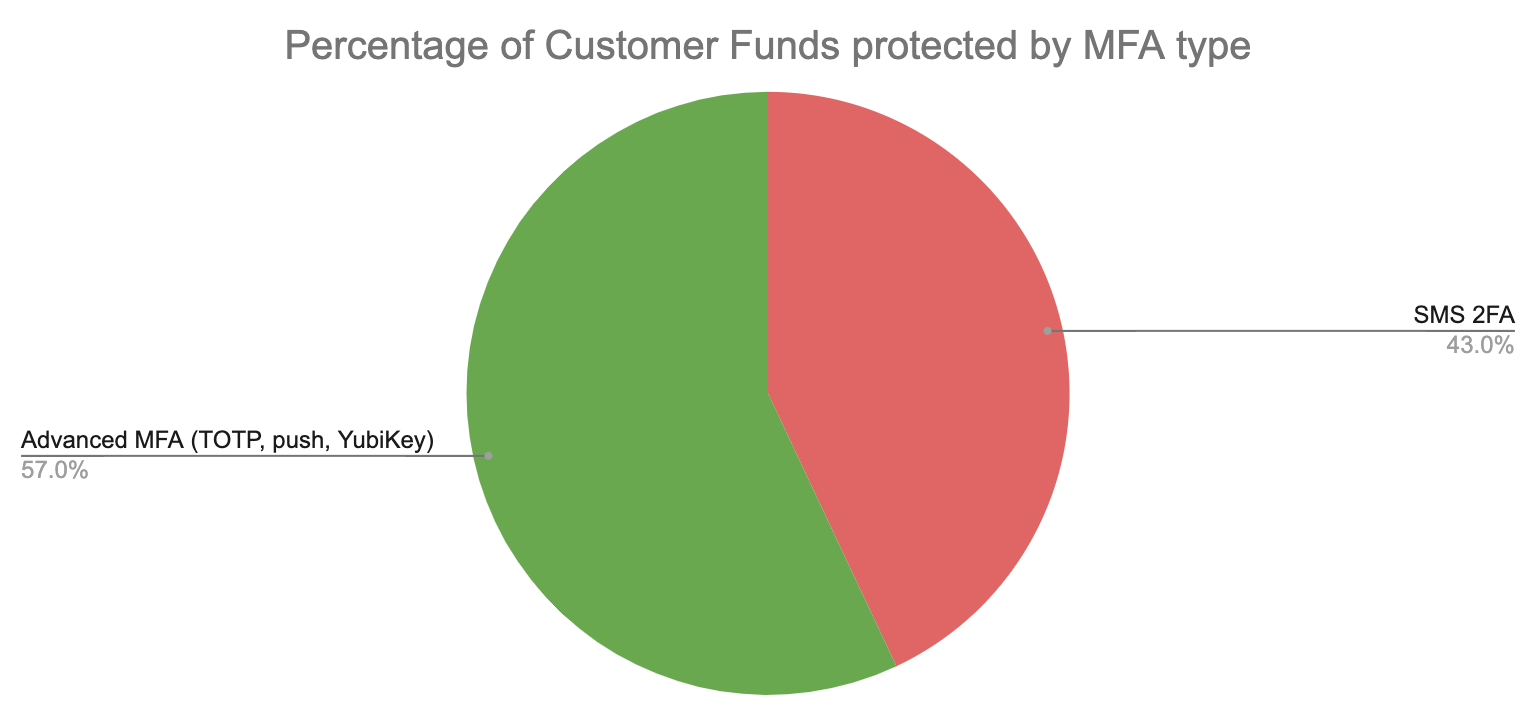
However, these larger accounts are seldom stolen by attackers because of the increased effort involved in breaking the MFA types that these customers use. Coinbase found that for these accounts using advanced MFA (TOTP, push notification, or security keys), only 5% of all account takeovers were successfully executed against these users. And of these rarer account thefts, 86% are concentrated on TOTP and push notification MFA, which unlike security keys, are not “phishing-resistant."
Despite most Coinbase customer funds being protected by advanced MFA, only 5% of those accounts are stolen due to the increased effort involved in attackers’ trying to break those MFA methods. Meanwhile, SMS 2FA protects only 43% of Coinbase customer funds but comprises nearly all (95%) of account takeovers.
Want unphishable MFA for your app? Switch to Stytch.
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Evaluating MFA options: Advantages and disadvantages of commonly used methods
When it comes to MFA options, there are several available, each with its own set of advantages and disadvantages. Every application is different, but most should be offering multiple MFA options to promote both maximum adoption and advanced security options.
When considering which options to offer, here’s some important considerations for each MFA method:
- SMS One-time Passcodes: This is the most basic form of MFA, where a user receives a one-time passcode via text message.
- Pros: This option is familiar and easy for users. It offers a particularly seamless experience on mobile due to the auto-fill capabilities on iOS and Android that allow a user to stay within the application experience when inputting the passcode.
- Cons: SMS 2FA is vulnerable to both reliability issues (it’s dependent on a single point-of-failure – the SMS provider – for the authentication) and security concerns. The major security shortcomings are phishing – where a user is deceived into sharing the passcode with an attacker – and SIM-swap attacks. A SIM-swap attack is a type of cyber attack in which a malicious actor convinces a mobile carrier to reassign a mobile number to a SIM card they control. Once they have control of the number, they can use it to reset the victim's password on any account that uses the phone number as a form of verification and gain access to sensitive information such as bank accounts, emails, and social media profiles. This type of attack is particularly concerning because it can bypass most two-factor authentication systems that rely on text messages.
- Time-based One-time Passwords (TOTP): This option uses an app like Duo or Google Authenticator to generate a time-based password (or passcode), eliminating the dependency on a customer's mobile carrier.
- Pros: TOTP isn’t dependent on mobile carriers, so there’s no deliverability issues or SIM-swapping concerns.
- Cons: This option requires users to have their mobile phone with them and can be a bit more complex to set up due to the need to download an application. Phishing also remains a key risk as a user can still be convinced to pass the code along to an attacker – this phishing risk is shared by SMS, TOTP, and Push notification and it explains why these three MFA methods account for 99.96% of all Coinbase account takeovers.
- Push Notifications: This option sends a push notification to a registered and authenticated device, which the user must approve before logging in.
- Pros: This option is convenient for users, but it requires them to have their device with them and have a stable internet connection. It’s been made more familiar for users through examples like Gmail promoting this method.
- Cons: From a security perspective, phishing is the primary concern here as a user can be tricked into clicking a push notification to grant access or may accidentally do so when on their phone. This method also requires users to have their device with them and have a stable internet connection (TOTP and hardware security keys do not require internet connection).
- Hardware Keys: This option uses a physical security key, such as a YubiKey, as the second factor of authentication. However, it can be more expensive and may require additional setup steps for users.
- Pros: This is considered the most robust form of MFA as it is phishing-resistant and requires a physical device to access the account.
- Cons: It’s more expensive and complex for users to initially set up a security key (for example, a YubiKey costs $50), which is why consumer adoption remains quite low.
- Biometrics: This option uses a fingerprint or facial recognition as the second factor of authentication.
- Pros: It is considered more secure than SMS one-time passcodes, TOTP, and push notification due to being resistant to phishing attacks, and it has the consumer benefit of being more familiar, convenient, and cheaper than setting up a physical security key.
- Cons: It requires users to have a device with a biometric sensor. Additionally, some users remain skeptical of biometrics due to the misunderstanding that their biometric data is accessed and stored by the application.
Effective MFA requires maximizing user enrollment
In conclusion, choosing the right MFA options for your application requires a balance between security and user adoption. By understanding the relative security and adoption rates of different MFA options, engineers can make informed decisions that protect their users while also ensuring maximum adoption. By studying examples like Coinbase, engineers can gain valuable insights into the effectiveness and uptake of different MFA options. While some MFA options are superior when it comes to security, the theoretical security model of any particular MFA method is useless if users find it too friction-heavy to enroll in that MFA option.
The pragmatic path typically involves offering multiple MFA options to your user base and explaining the security benefits of enrolling in more advanced and phishing-resistant MFA. At Stytch, we’re particularly excited about the promise of new authentication technologies like passkeys, which provide many of the usability benefits of conventional MFA like SMS 2FA while also providing the security benefits of physical security keys like YubiKey.
About Stytch
With multi-factor authentication from Stytch, you’ll get the security protection your application needs, to prevent account takeovers, with a UX that will delight your users. Stytch offers a suite of MFA solutions that offer maximum flexibility and security while maintaining a great customer experience. Check out our products, explore our Docs or talk to an auth expert today!
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.