Back to blog
Stytch Talks With Jordan Burris: “The Future of Multi-Factor Authentication (MFA)”
Auth & identity
Company
Mar 15, 2023
Author: Stytch Team
As traditional passwords become increasingly unreliable, more app developers have decided to enhance their sign up and log in flows with layered multi-factor authentication (MFA), which requires two or more verification steps to confirm a user’s identity. But not all MFA is created equal, and there are many different ways apps can implement it to protect their users and stave off the latest online threats.
To explore the nuances of MFA and how it fits into the current digital landscape, Stytch’s co-founder and CEO Reed McGinley-Stempel sat down with Jordan Burris, VP and head of public sector strategy at Socure, the preeminent platform for identity verification. As former chief of staff for the White House’s federal chief information officer, Jordan led cybersecurity efforts across two presidential administrations, and he’s a leading expert on issues of identity management and digital trust.
Missed the live webinar? You can find a full recording of the event on Stytch’s YouTube channel.
In the latest installment of Stytch Talks, Jordan and Reed tackled everything from the state of the password and advances in biometrics to how new AI tools are emboldening modern hackers. Below, we share seven key takeaways from their discussion and the Q&A, along with actionable strategies to help you take full advantage of MFA.
1. Passwords should be considered “pre-breached” in today’s cybersecurity climate, which is why we need stepped-up auth measures like MFA.
According to recent studies, over half (52%) of global companies have experienced a cybersecurity breach in their operational history, with each attack carrying an average price tag of $4.35 million.
These stats are scary, but their root cause is entirely avoidable. The vast majority of data breaches (80% in total) can be traced to compromised credentials — that is, weak or reused passwords that can be easily intercepted by hackers and used to take over legitimate accounts. In fact, industry experts at the Open Worldwide Application Security Project (OWASP) advise app developers to treat all passwords as “pre-breached” and to supplement them with stronger security measures like MFA to protect their data.
Research by Microsoft has shown that layered MFA flows can successfully block up to 99.9% of all password-based cyberattacks.
That’s because most hackers prefer cheap, high-yield strategies, like using >pre-programmed bots to run automated brute-force or credential-stuffing attacks. By asking for additional credentials that a bot cannot easily provide — like an SMS passcode or biometric verification — MFA requires human intervention, raising the cost and complexity of an attack.
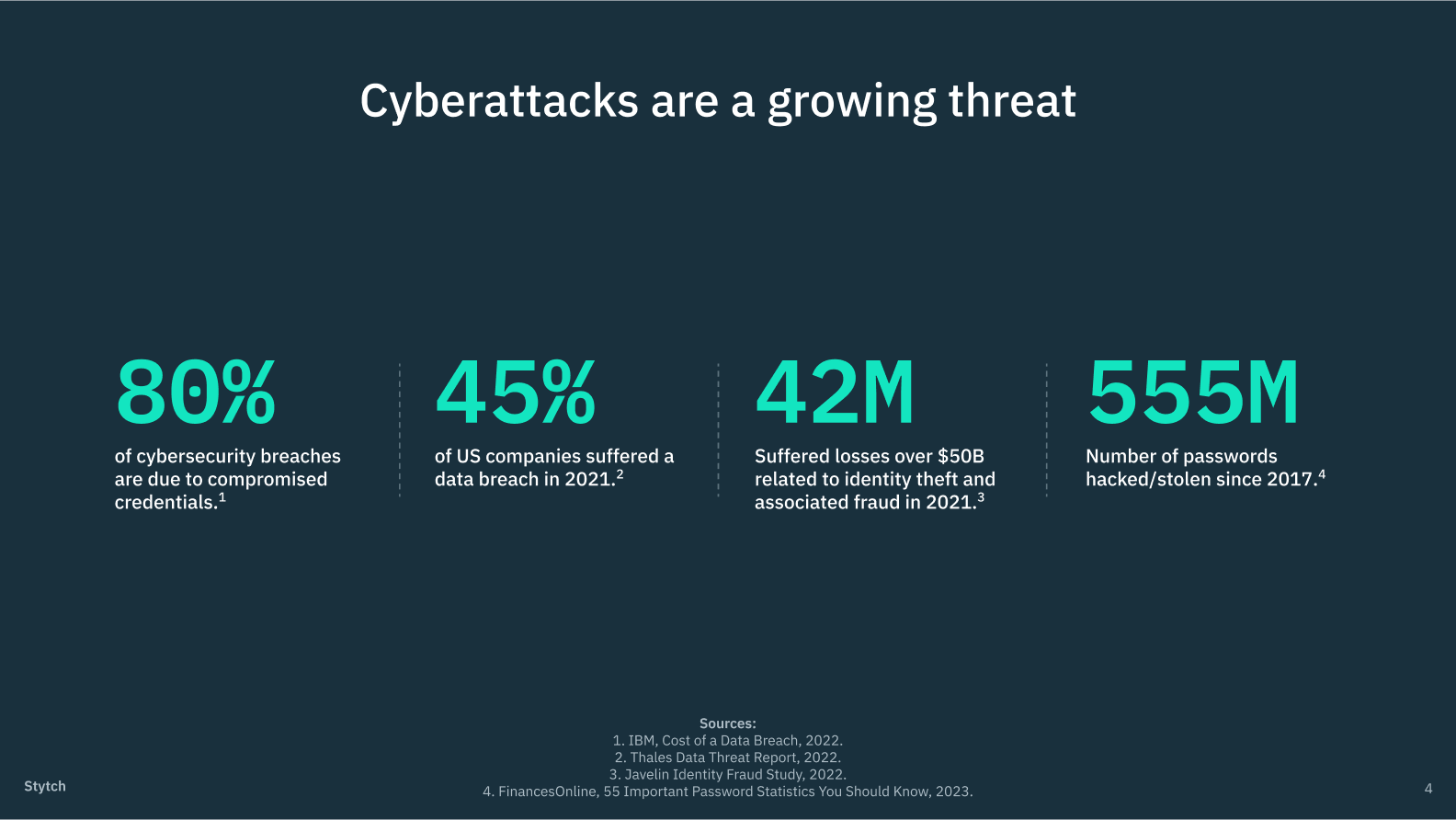
2. The most popular MFA methods are also the least secure, and companies need to find ways to make robust factors easier to adopt.
There’s no one-size-fits-all when it comes to MFA. Which factors a company decides to include in their flow (and when) will largely depend on criteria like their user demographics and the sensitivity of their data. That said, some forms of MFA are inherently more secure than others, and there’s often a tradeoff between strength and usability.
Most apps opt for factors like SMS one-time passcodes that are both familiar and easy to use, resulting in higher conversion rates. Unfortunately, they’re also the easiest to circumvent, as they’re vulnerable to both phishing and SIM-swapping attacks.
Want unphishable MFA for your app? Switch to Stytch.
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Stronger factors like time-based one-time passcodes (TOTPs) require users to download a third-party app, introducing friction and the potential for drop-offs. And the strongest WebAuthn factors either force users to buy physical hardware (like YubiKeys) or cannot be implemented across devices (like native biometrics).
Coinbase recently discovered (and publicized) that 95% of their users opt to log in via SMS passcodes, but passcodes also account for 95.65% of their account takeover volume—compared to 4.13% with TOTPs, 0.18% with push authentications, and just 0.04% with a physical security key.
While optionality will continue to be crucial, companies interested in providing the best protection will find ways to make it easier to adopt more secure factors like TOTPs and passkeys.
3. Emerging AI tools are enabling more sophisticated phishing attacks, making more advanced unphishable MFA more important than ever.
New, AI-powered chatbots like ChatGPT, which saw 100 million users within two months of launching, are empowering hackers to be bolder and more prolific.
Historically, hackers have used obvious typos in phishing emails, as a way of ensuring respondents are gullible and thus more likely to unwittingly carry out a fraudulent action. That’s because phishing is a predominantly manual method, requiring hackers to interact live with their victims. If conversations can be delegated to a convincing chatbot, hackers can target more sophisticated users with little to no human cost, allowing them to widen their net and increase the volume and scope of their attacks through automation.
As phishing gets more sophisticated, it’s on companies to adopt unphishable MFA practices that render these more sophisticated fraud attempts a moot point.
4. A top priority is pairing enhanced MFA flows with innovative identity verification tools, to protect users across the access lifecycle.
As the focus continues to be on adopting stronger MFA, equally we need to be looking at what we’re doing from an identity verification and fraud risk management standpoint.
As the focus continues to be on adopting stronger MFA, equally we need to be looking at what we’re doing from an identity verification and fraud risk management standpoint.
One of the most pressing needs in cybersecurity is supporting authentication with next-level identity verification strategies — essentially, pairing strong MFA factors from Stytch’s product suite with strong fraud-detection and ID-verification tools from Socure’s. Without the former, you get legitimate user accounts that can be easily breached. Without the latter, you get heavily protected accounts with fake or fraudulent identities behind them.
In other words, an identity verification flow confirms that a user is the actual individual they claim to be — avoiding gaffes like 2022’s messy Twitter Blue rollout, where any internet troll could claim an “official” Twitter profile under any real/stolen or fictitious identity.
One instance where this relationship matters is the account recovery process. Authentication can only take users so far if they lose all of their identifiers (their email inbox, the device that was hosting their biometric data, etc.) and they need an easy, secure way to verify their identity and regain access to their accounts.
That’s why prominent organizations like the FIDO Alliance are making identity verification and binding a top priority in their upcoming cybersecurity initiatives.
5. Biometrics is the future of phishing-resistant MFA, but that means little if people won’t use it.
Biometric factors like fingerprints and facial recognition allow for high-security, low-friction logins, giving them an edge over other auth methods. But biometrics also faces steep challenges when it comes to both user trust and implementation.
Currently, over half of users (around 58%) trust biometrics more than they do traditional usernames and passwords — but many in the remaining 42% feel strongly that biometric technology violates their privacy and puts their personal data at risk. To bridge these adoption gaps, more education and transparency is needed for users to understand how and why biometric data is used and when it’s shared. Advances are also needed to address situational hurdles, like shared devices used by multiple members of a household.
From an implementation standpoint, biometric auth has historically been locally bound to a specific device, disrupting the user experience and hindering universal use. Fortunately, innovations like passkeys are making it possible to store and sync biometric data through the cloud, so it’s accessible and interoperable across different platforms and devices. That said, it will be some time before these tools can be widely implemented and adopted.
In the meantime, a more practical and comfortable solution is to give users and developers a choice in their auth journeys and to ensure the technology used in cybersecurity is as open and inclusive as possible.
Optionality must be paramount. Biometrics is achieving broader adoption, but at the end of the day, not everyone is going to have the technology or the components to facilitate it, and we have to continuously be looking for other methods that provide strong phishing resistance.
Optionality must be paramount. Biometrics is achieving broader adoption, but at the end of the day, not everyone is going to have the technology or the components to facilitate it, and we have to continuously be looking for other methods that provide strong phishing resistance.
6. For a glimpse into best-in-class MFA, look to high-stakes sectors like fintech and government.
Because they have a lot to lose in a data breach, high-risk sectors like fintech and government are great spaces to find examples of MFA best practices in action. Some of the best practices to look for include:
- Optionality: Though MFA factors vary in terms of security strength, any MFA is better than no MFA at all. That’s why companies like Coinbase (in the example above) offer users several different paths to log in, so they’re sure to find factors that meet their needs and comfort level.
- Future-proofing: Young fintechs like Robinhood tend to be more tech-forward than legacy banks, building advanced factors like TOTP authenticator apps into their log in flows, rather than just SMS and email passcodes. One reason for this could be the irreversible nature of crypto transactions, which places a greater fraud liability on newer companies that trade heavily in digital currencies.
- Mandatory (but flexible) MFA: While choices are good, safe choices are better. On the SaaS side, B2B apps like Stripe and Gusto often require MFA, either at initial login or as part of a route-based or just-in-time auth flow. These platforms tend to deal with high-value use cases like payroll, payments, and invoicing with bank accounts attached, so they’ve thought a lot about optimizing both security and adoption
7. The secret to building your MFA flow? Just get started.
Our panelists had a few helpful tips on how to implement MFA efficiently and effectively. Most notably: act decisively, and don’t get mired in analysis paralysis.
"The reality is, you just have to start. That sounds simplistic, but it’s about picking an application, segmenting the infrastructure, and recognizing that zero trust isn’t a destination, it’s a journey. Focus on things you can control, whether that’s protecting your most valuable assets first, or starting with something newer, and develop the muscle memory of understanding what it’s going to take to incorporate better security practices. That’s how you get learnings you can use to drive efforts at scale."

"The reality is, you just have to start. That sounds simplistic, but it’s about picking an application, segmenting the infrastructure, and recognizing that zero trust isn’t a destination, it’s a journey. Focus on things you can control, whether that’s protecting your most valuable assets first, or starting with something newer, and develop the muscle memory of understanding what it’s going to take to incorporate better security practices. That’s how you get learnings you can use to drive efforts at scale."

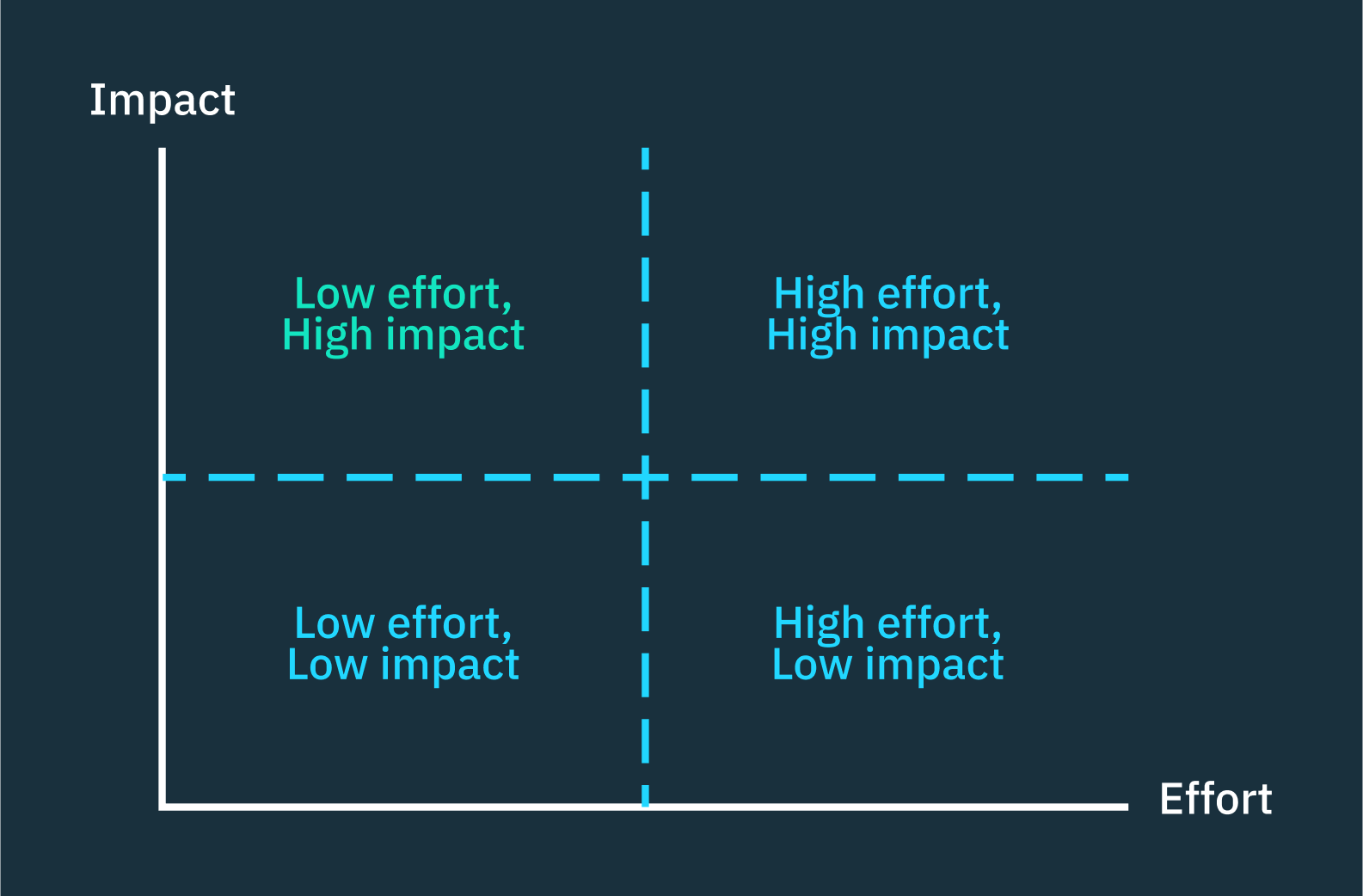
Something we think a lot about is the 2x2 matrix for prioritization and trying to figure out what’s in that quadrant of low effort/high impact. Are there certain routes in your application that keep you up at night?
Something we think a lot about is the 2x2 matrix for prioritization and trying to figure out what’s in that quadrant of low effort/high impact. Are there certain routes in your application that keep you up at night?
The bottom line
MFA is playing an increasingly important role in fighting off evolving cyber attacks, but its success largely depends on how it’s implemented. Learning the ins and outs of different factors, how they match up against the latest threats, and how they affect your specific user base can help you minimize friction, maximize security, and create seamless digital experiences.
Want to learn more about the latest in MFA?
Reach out reed@stytch.com or jordan.burris@socure.com to continue the conversation — or check out Stytch’s flexible suite of authentication solutions to optimize your MFA flow.
Related Articles

Company
May 2, 2023
Stytch Talks with Enzo Avigo: Building a high-performing B2B sign up flow
Auth & identity
Company
Sep 29, 2022
Stytch Talks with Brian Hale: rethinking user sign-up and login to unlock growth
Auth & identity
Aug 24, 2022
Multi-factor authentication: how to choose the right approach for your business
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.