Back to blog
Stytch Talks with Brian Hale: rethinking user sign-up and login to unlock growth
Auth & identity
Company
Sep 29, 2022
Author: Stytch Team
Earlier this month, Stytch’s co-founder and CEO Reed McGinley-Stempel sat down with Brian Hale, VP of consumer product and growth at DoorDash, to discuss how companies can turn their authentication strategies into critical drivers of growth.
Hale shared how his aha moment came in 2014, when he was leading a product growth team at Facebook (now Meta). They began experimenting with logins after noticing that legitimate users were being shut out from the platform due to bugs in the security flow. It occurred to them that, if auth could serve as a negative growth lever, it could also be mobilized as a positive one.
McGinley-Stempel had his own aha moment while working at Plaid with Stytch co-founder Julianna Lamb. As part of the auth team, they met with both security and growth stakeholders and realized that the platform’s biggest conversion snag (the password) was also its greatest fraud vector.
Their main takeaway? When product and security teams work together, they can better identify elements in their sign-up and login flows that are standing in users’ way — and move quickly to fix them with lower-friction solutions.
Below, we recap the actionable tips their discussion brought to light, from merging growth and cyber-security elements in your organizational structure to taking the right authentication steps to meet your users’ needs.
Uniting product and security teams toward a common goal
Building an auth-as-growth strategy starts at the organizational level by aligning your product and security teams around a shared purpose.
Typically, product teams are focused on expanding a platform’s customer base — letting “good” users in through simple sign-up flows — while security teams are focused on preventing cyber attacks and keeping “bad” users out with robust login verifications. That’s why these teams are usually seen as at odds: You can’t boost security, the thinking goes, without adding extra friction, compromising the user experience, and tanking conversion rates.
But while their immediate interests may differ, product and protection teams’ fundamental goal is the same: attracting and retaining the right users. In an ideal scenario, they’d work in tandem to find the best possible balance between UX and security.
Business leaders can make that happen by building a company culture based on trust, investing in cross-departmental relationships, and maximizing opportunities for collaboration.
At the team level, product and security managers can help by holding regular one-on-ones with their counterparts and proactively sharing their roadmaps. That ensures no one is caught off-guard or derailed by a new initiative — like an SMS verification flow that interrupts the user journey or a product A/B test that interferes with the password processing system.
When your product and security teams work together, you can shift your approach from putting out auth fires and addressing growth regression after the fact to developing a broader authentication strategy that supports growth across the board.
Optimizing CAC and LTV through auth best practices
There’s no one-size-fits-all solution when it comes to authentication. The strategy that works best for your app will all come down to your users and their unique preferences and behaviors.
That said, Hale noted there are dozens of tangible, actionable auth levers that can have a big impact on your conversions at sign-up, to bring down customer acquisition costs (CAC), or at login, to boost your lifetime value (LTV). Some standout ideas he shared include:
Offer both phone number and email as account identity options.
This can be a generational issue, as young people are increasingly turning to SMS and other mobile communications over email addresses to set up their accounts. It can also help ease geographical and cultural divides, as email access is not universal across the globe. Hale estimates that including both phone and email options can expand an app’s reach by 5%.
Tailor your passwordless path to your users and your product.
Authentication isn’t black-and-white, and there are many paths along the passwordless adoption curve. If your products are multi-platform, if you use an email-based auth system that travels across devices, or if you have an older, more traditional user base, eliminating passwords abruptly may end up creating more friction and harming rather than helping your growth efforts. Luckily, it’s easy to add passwordless options to a password-based flow and ease the transition if you’re not yet ready to ditch credentials for good.
If you can’t eliminate passwords, eliminate as much friction as possible.
Stytch has always been passwordless-first, but we recently introduced a Password product. That’s because we recognize that different apps have different considerations, but they still need easy, low-friction waysto authenticate their users.

When upgrading a password-based flow, aim for the low-hanging fruit first — like tedious, multi-step password-reset flows. There are several ways you can improve this process:
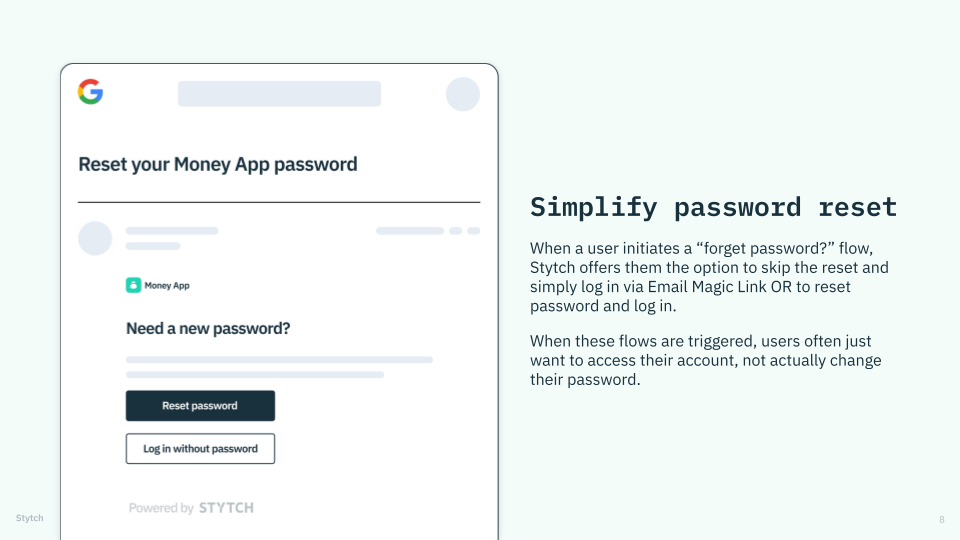
- Make the reset a secondary, optional flow: most users don’t actually want to create (and remember) a complicated new password; they just want to log in and access their account. Ease their pain by logging them in via an Email Magic Link — which still proves possession of an inbox — and let them be on their merry way.
- Don’t wait for users to click the reset button: if you see a user has tried and failed to log in several times, save them the trouble and proactively send them a login link via SMS or email to let them in.
- Take over the screen with an automated SMS: even better, if you can, send users an SMS that automatically populates the reset code in your app. That way, a user won’t have to navigate away from your platform to regain access to their account.
Once you’ve streamlined your reset flow, you can always strengthen your security posture by adding components that don’t add extra friction. For example, Stytch integrates with HaveIBeenPwnd to check if a password has previously been compromised in a data breach — and, if so, prompts the user to reset their credentials.
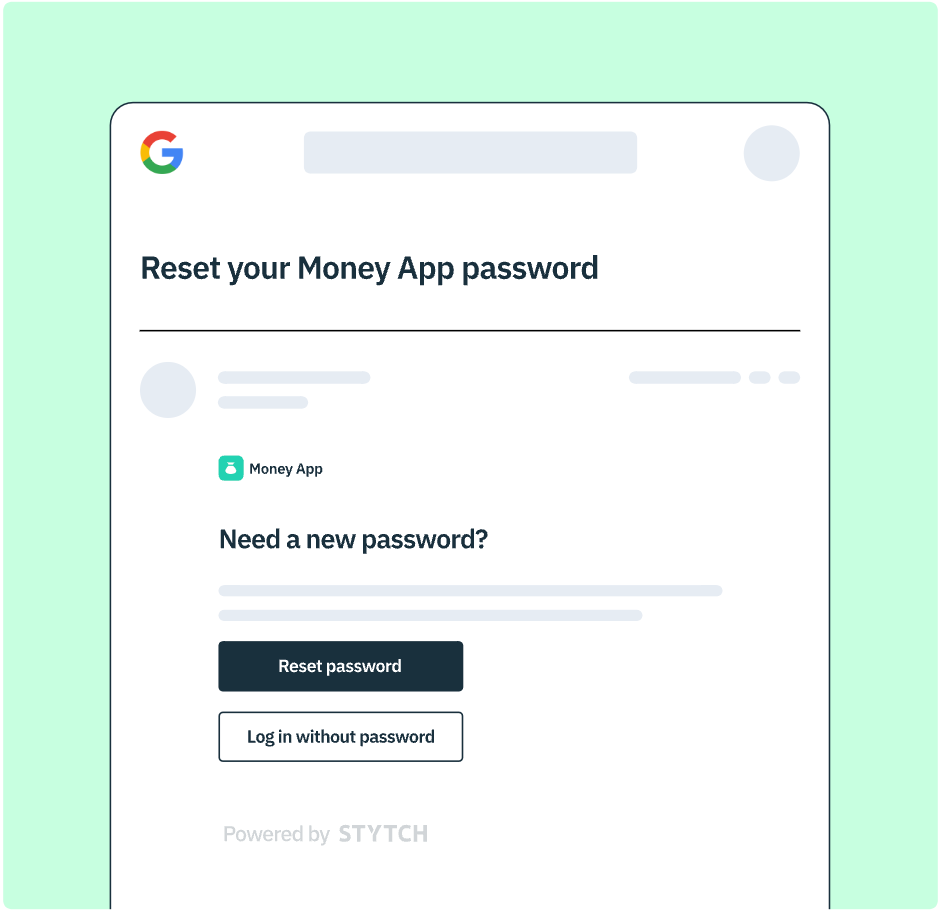
Stytch offers users the option to skip password reset and simply log in via Email Magic Link OR to reset their password and log in.
Don’t block good users for mistakes bad actors would never make.
The kinds of mistakes humans make when entering passwords are extremely predictable — and not at all the same tricks hackers and password-stuffing bots use when trying to breach accounts. That means you can account for common user errors without opening yourself up to fraud.
For example: If someone submits the correct password with the caps lock on or includes an extra character that’s immediately adjacent to the enter key, that’s not the type of error that an attacker in possession of a leaked list of passwords would make. In all likelihood, this is a good user, and it’s clear they know their password, so let them in, and don’t punish them for trying.
Want to make your login flow more user-friendly? Switch to Stytch.
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Find the right balance of auth options to meet users where they are.
You want to offer multiple ways into your app — which may include passwords, OAuth Logins via Google, Apple, and Facebook, or any number of auth factors — but your goal is to reduce friction. You don’t want a “login soup” where users forget which factor they signed up with, open a new account, and are forced to repeat the onboarding process.
Keep things simple with a maximum of four or five auth options, and let your specific industry and audience determine your selection. Make sure you’re also partnering with an auth provider, like Stytch, that de-duplicates accounts whenever possible.
Growth-oriented auth in action
Consider some visual examples that demonstrate how these levers work in practice to inspire your own growth-oriented auth strategy. For example:
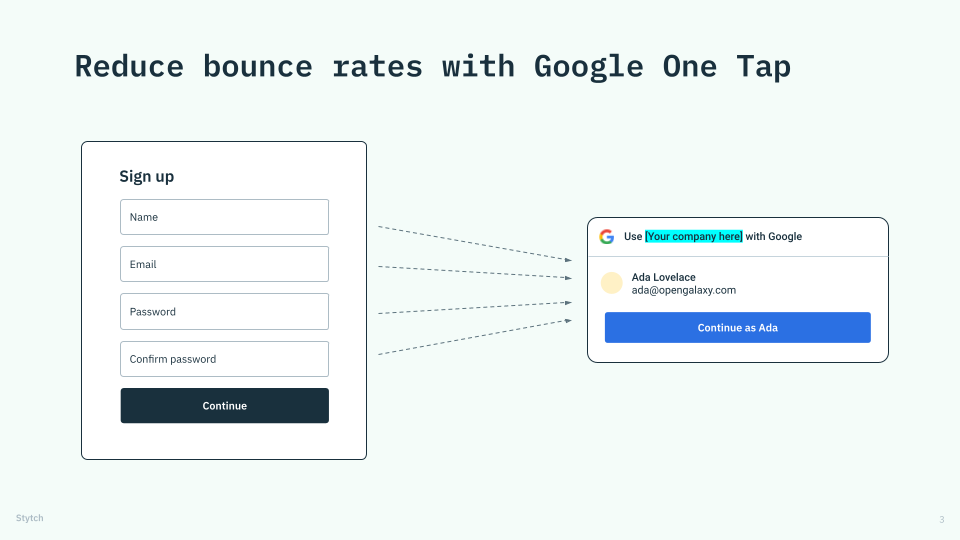
Companies like DoorDash use Google One Tap to optimize their sign-up flows, boost top-of-funnel growth, and reduce CAC.
Typically, when you ask users to sign up for your app or website — via a homepage, blog post, or anywhere else — you ask them to complete various steps, like providing a name, email, password, password confirmation, and maybe even an email verification.
If you’re looking to reduce bounce rates along this multi-step flow, Google One Tap allows you to piggyback on an active Google/Gmail session on the user’s browser and collect and verify their information with a single click.
Companies that have A/B tested multiple authentication factors have found Google One Tap to be their most successful experiment by a long shot. For example, Pinterest saw a 47% jump in desktop conversion rates (and a 126% jump on Android), while Reddit doubled their new user sign-ups and returning user conversion rates.
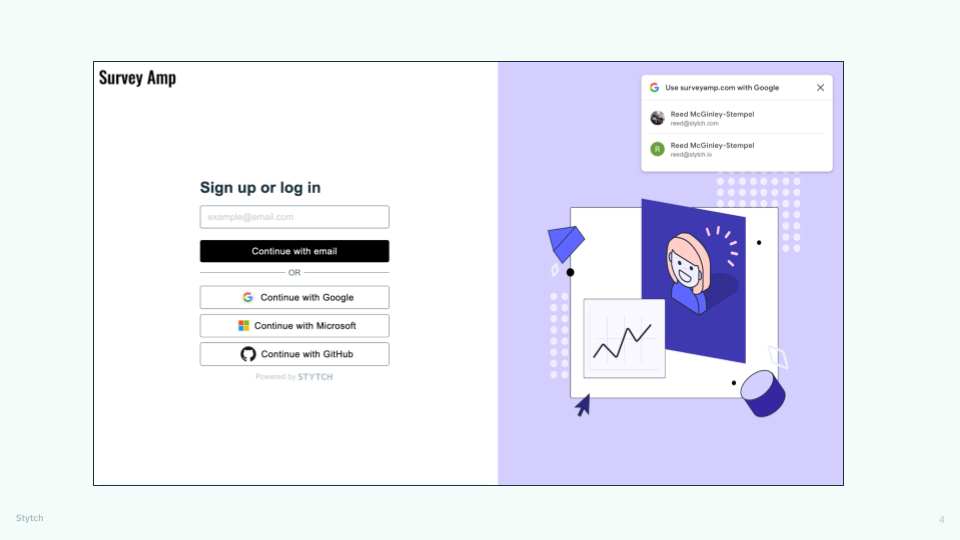
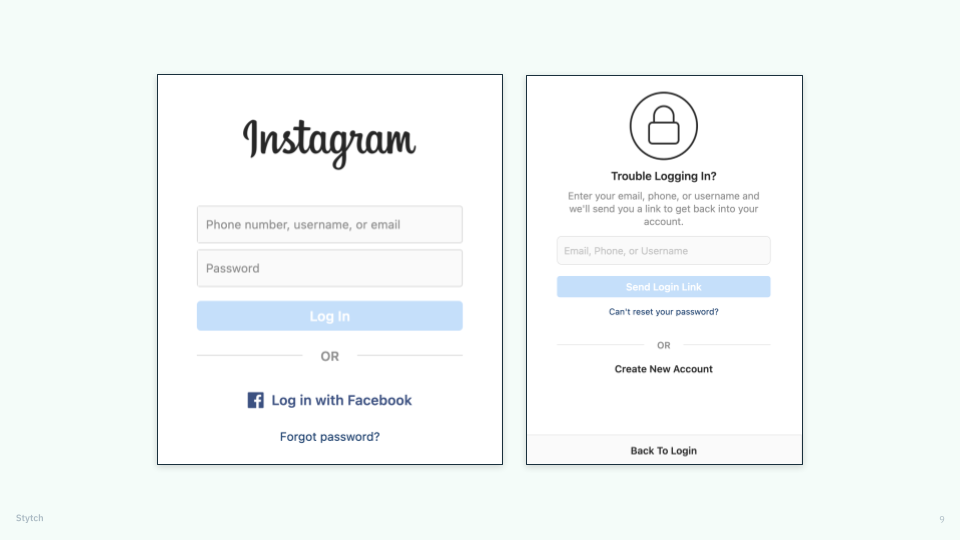
Companies like Instagram simplify their password-reset flows to optimize login processes and reduce bounce rates.
Users on your login screen are typically those with the highest intent, since they’ve already signed up for your platform and are now returning to complete a specific action or to make a purchase. As noted earlier, the key to keeping those users happy is to make it easy for them to access their accounts — especially when they forget their credentials.
Instagram defaults to sending users a login link via email or SMS but also offers options for creating a new password or account — so they only have to navigate a reset flow if it’s what they really want.
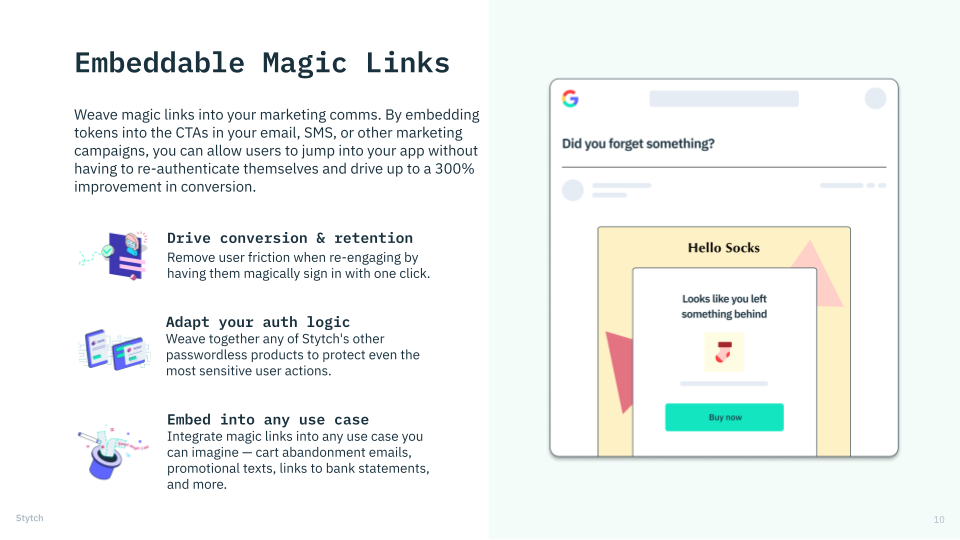
Companies like 1-800 Contacts embed authentication tokens into their marketing materials to eliminate friction and increase LTV.
If you’re sending frequent marketing communications to users via email or SMS, you can build an authentication token into your call-to-action button via an Embeddable Magic Link. When it’s clicked, simple device fingerprinting allows you to ensure it’s by the user who owns that inbox or phone. You can then send them straight to their account — rather than a logged-out state — bypassing login friction and enhancing their overall experience. We’ve found this can increase engagement and conversion rates by as much as 300%.
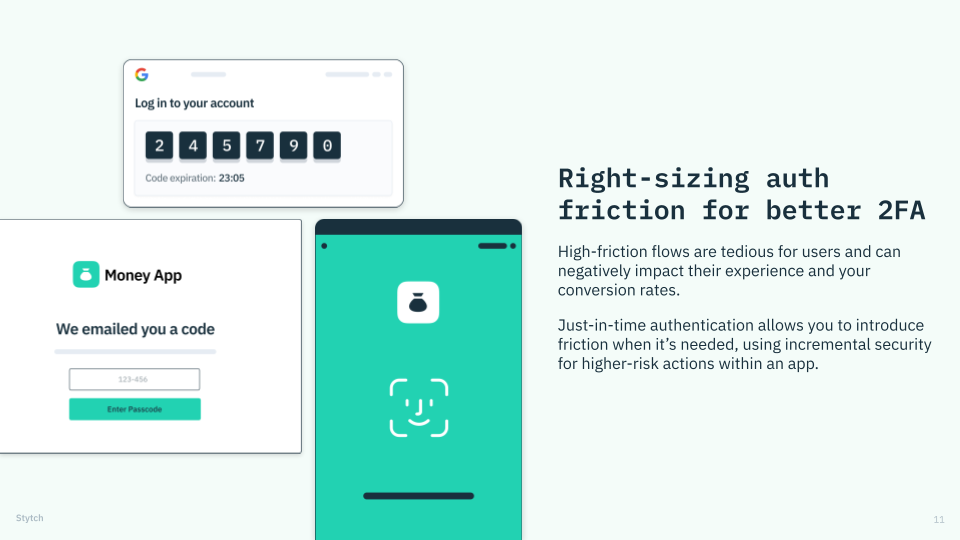
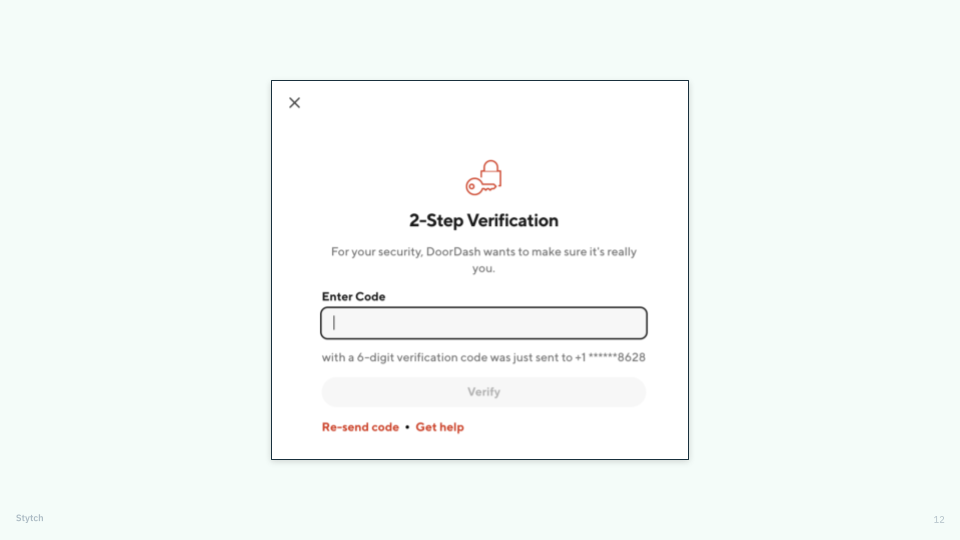
Companies like DoorDash use “just-in-time” authentication to introduce friction only when it’s needed.
Finally, instead of front-loading their apps with multi-factor authentication at every single sign-up and login (regardless of the risk posture), forward-thinking companies like DoorDash only ask users for additional authentication factors when they’re looking to carry out sensitive tasks — like changing a delivery address or updating payment details.
We call it “just-in-time” authentication, because it saves the stepped-up security measures (and, with them, the extra friction) for when they matter most.
As you assess and update your auth strategy, make sure you’re sizing up your platform both qualitatively and quantitatively, including metrics like bounce rates on key onboarding pages, the percentage of users completing your password-reset flows, and where exactly they drop off in their journey. You should also ensure you’re auditing your flows regularly and investing in the best tools and technologies to enhance your growth.
Key takeaways
Your sign-up and login flows shouldn’t be an afterthought — and they shouldn’t belong to a product or security team alone. They’re critical to your user experience and can have a substantial impact on critical business metrics like conversion rates, CAC, and LTV.
Ensuring key teams and stakeholders are aligned when selecting and implementing the best flows for your app will go a long way toward creating an auth strategy that not only protects your users but fuels your growth.
Ready to power your growth through frictionless auth?
Visit our LinkedIn Events page to watch the full webinar — or download a copy of the slide deck here.
If you have any questions, want to learn more about best practices, or are interested in walking through your security flow with an expert, reach out to the Stytch team to book a free consultation. You can also check out our Slack channel to participate in daily discussions on all things auth.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.