Back to blog
What is a reverse proxy?
Auth & identity
Jan 11, 2024
Author: Alex Lawrence

A reverse proxy is an integral part of modern web architecture, often misunderstood due to its behind-the-scenes operation. Unlike a traditional proxy server, which serves a user seeking resources from the internet, a reverse proxy stands in front of web servers and intercepts requests directed to these servers. It is a type of proxy server that operates in the opposite direction of that which a forward proxy does.
In this article, we’ll peek behind the curtain for a more detailed view of the reverse proxy’s role in enhancing security, scalability, and load times – and why you might consider implementing them as part of a holistic security and UX strategy.
The role of reverse proxies in modern web architectures
The primary function of reverse proxies is to act as a gateway between the internet and backend web servers. By doing this, they efficiently manage and route incoming traffic and streamline communication between the user and the server. This mechanism not only improves performance but also enhances security, making reverse proxies a critical component in protecting web applications.
But what is a reverse proxy in the framework of modern web operations? In essence, a reverse proxy serves as an intermediary, or gatekeeper, for requests from clients (internet users) seeking resources from servers. When a request is made to a web application, the reverse proxy intercepts this request before it reaches the backend server, allowing it to perform load balancing, caching, and SSL encryption, among other functions, which are crucial for a streamlined user experience and enhanced security.
What is a reverse proxy vs. a forward proxy?
Understanding the distinction between reverse and forward proxies is crucial in comprehending their respective roles in network infrastructure. A reverse proxy server, as discussed earlier, is positioned between the client and backend servers. In contrast, a forward proxy server sits between the client and external servers on the internet.
The concept of a forward proxy
A forward proxy, also known as a proxy server, sits in front of client machines. Its primary function is to manage outgoing traffic from these clients to the internet. This setup is particularly useful in scenarios where multiple clients on an internal network need to access external resources. Forward proxies can also provide anonymity and content filtering for clients.
Contrasting a reverse proxy server and a forward proxy server
While a forward proxy serves as an intermediary for outgoing requests from a network to the internet, a reverse proxy deals with incoming requests from the internet to a web server. The reverse proxy makes decisions on how to handle these incoming requests, directing them to the appropriate backend server. This key difference underlines the distinct roles these two types of proxies play in network architecture.
Proxy servers in network security
Both forward and reverse proxies play pivotal roles in network security. Forward proxies protect client machines from direct exposure to the internet, while a reverse proxy safeguards backend servers from direct access by external threats. This dual-layered approach is fundamental in maintaining a secure and efficient network.
Key functions of a reverse proxy server

As mentioned, reverse proxies perform several essential functions that significantly improve the performance and security of web applications. Let’s look at each in a bit more detail.
Load balancing
One of the primary roles of a reverse proxy server is load balancing. Reverse proxies can distribute incoming traffic among multiple backend servers, allowing for better utilization of resources and improved performance. In an environment with multiple servers, the reverse proxy distributes incoming traffic among all the servers. This distribution ensures that no single server is overwhelmed, maintaining optimal performance and reducing load times. Load balancing is especially crucial for high-traffic websites, as it prevents server crashes and ensures high availability.
Enhanced security
A reverse proxy server adds an extra layer of security to web applications. By masking the identity of backend servers, they protect against direct attacks. Additionally, a reverse proxy server can perform SSL encryption, ensuring that sensitive data transferred between the client and the server is secure. This encryption is vital for protecting against security risks such as data breaches and DDoS attacks. Reverse proxies can also filter and block suspicious requests, preventing malicious attacks from reaching the server.
SSL encryption
Reverse proxies can handle SSL encryption/decryption, relieving the backend servers from this computationally intensive task. This not only improves performance but also allows for easier management of security certificates. SSL encryption also adds an extra layer of security by encrypting data in transit, which protects sensitive information from potential threats.
Web acceleration and caching
A reverse proxy significantly improves website performance through caching. They store copies of frequently accessed web pages, allowing these pages to be served quickly to users without overburdening the backend servers. This caching mechanism, known as web acceleration, is instrumental in reducing load times, thereby enhancing the overall user experience. A reverse proxy can also compress data, further enhancing performance by reducing the amount of data that needs to be transmitted.
Content filtering
Content filtering is when a reverse proxy inspects and manages data passing through the server, filtering out harmful or inappropriate elements. This helps block potentially harmful requests, protecting the server and network from security risks. Content filtering also allows blocking or permitting traffic based on various factors to enhance security and ensure data integrity.
Technical capabilities of reverse proxies
Reverse proxy servers are uniquely versatile in handling web traffic. In order to perform load balancing, caching, SSL offloading, and more of the benefits they offer, there are several key technical features that come into play within modern web architectures.
Handling client IP addresses
One such feature involves managing client IP addresses. By intercepting incoming requests, the reverse proxy can either forward or mask the client’s IP address, depending on the configured settings. This ability is crucial for addressing both privacy concerns and appropriately routing traffic. It allows for granular control over access to specific resources, as well as identifying and blocking potential threats.
Communication with multiple origin servers
A reverse proxy is capable of communicating with multiple origin servers, enabling it to distribute incoming requests across several servers and ensure that no single server is overwhelmed. This distribution not only balances the load but also provides redundancy, contributing to high availability and reliability of the web application. A reverse proxy can also act as a failover mechanism by routing traffic to backup servers in case of server failures.
Traffic routing and server responses
Traffic routing is another standout capability. It evaluates incoming requests and determines the most appropriate server to handle each request. After the backend server processes the request, the reverse proxy then forwards the server’s response back to the client. This process is seamless, and from the client’s perspective, it appears as if they are communicating directly with the server. This not only helps to improve the performance of the web application but also enhances security by keeping the backend server hidden from direct communication with the client.
Limitations of reverse proxies
While the benefits are compelling, reverse proxies are not a catch-all solution for every security and performance challenge – particularly in dealing with specific types of threats. The below are some of their most noticeable shortcomings.
Inadequate bot detection and fraud protection
Reverse proxies, while effective for basic traffic management and security, fall short in detecting sophisticated bot and fraud activities. They typically analyze surface-level traffic attributes such as IP addresses and request counts, which are not sufficient to identify advanced threats that mimic legitimate user behavior (more on how to target these in the next section).
Vulnerability to a single point of failure
If a reverse proxy server fails, it can bring down the entire web application. To avoid this issue, redundancy measures such as using multiple reverse proxies or implementing failover mechanisms need to be in place. Regular maintenance and updates are crucial to ensure that reverse proxies are functioning properly and securely.
Limited visibility into encrypted traffic
As more and more websites use encryption (HTTPS) for enhanced security, reverse proxies may have limited visibility into the encrypted traffic, making it difficult to detect and mitigate potential threats. This limitation highlights the need for additional security measures that can decrypt and inspect encrypted traffic without compromising privacy.
Complexity in configuration and maintenance
Troubleshooting and maintaining a large number of reverse proxies can be challenging, especially in distributed environments. Their configuration and maintenance can be complex, requiring specialized knowledge and resources, and incorrect configuration can lead to vulnerabilities or performance issues, underscoring the importance of proper setup and ongoing management.
Potential performance impact
While reverse proxies generally improve performance, they can become bottlenecks if not scaled appropriately. As a single point of entry and exit for traffic, a reverse proxy must be capable of handling the volume of requests it receives. Failure to scale the reverse proxy in line with traffic demands can lead to reduced performance and increased load times. This challenge can be addressed by using load balancers or implementing distributed reverse proxy systems.
Furthermore, while reverse proxies can improve the performance of a web application by caching frequently accessed content, they may not be effective for websites that have constantly changing content. In such cases, other optimization techniques like minification and compression should be utilized to improve response time.
Reverse proxies and device fingerprinting

While reverse proxies provide clear foundational web security and performance enhancements, they are not a complete solution. Their effectiveness is greatly amplified when paired with advanced auth solutions like device fingerprinting. This synergy is crucial for a comprehensive defense against sophisticated cyber threats, especially in the context of dynamic web content.
The one-two punch
Because advanced persistent threats and targeted authentication-level attacks may require additional security measures, merging reverse proxies with device fingerprinting can be a smart way to embed more nuanced security policies into your apps.This potent security combo enables real-time, detailed traffic analysis, improving the detection and response to specific bot behaviors and fraud tactics not captured by reverse proxies alone.
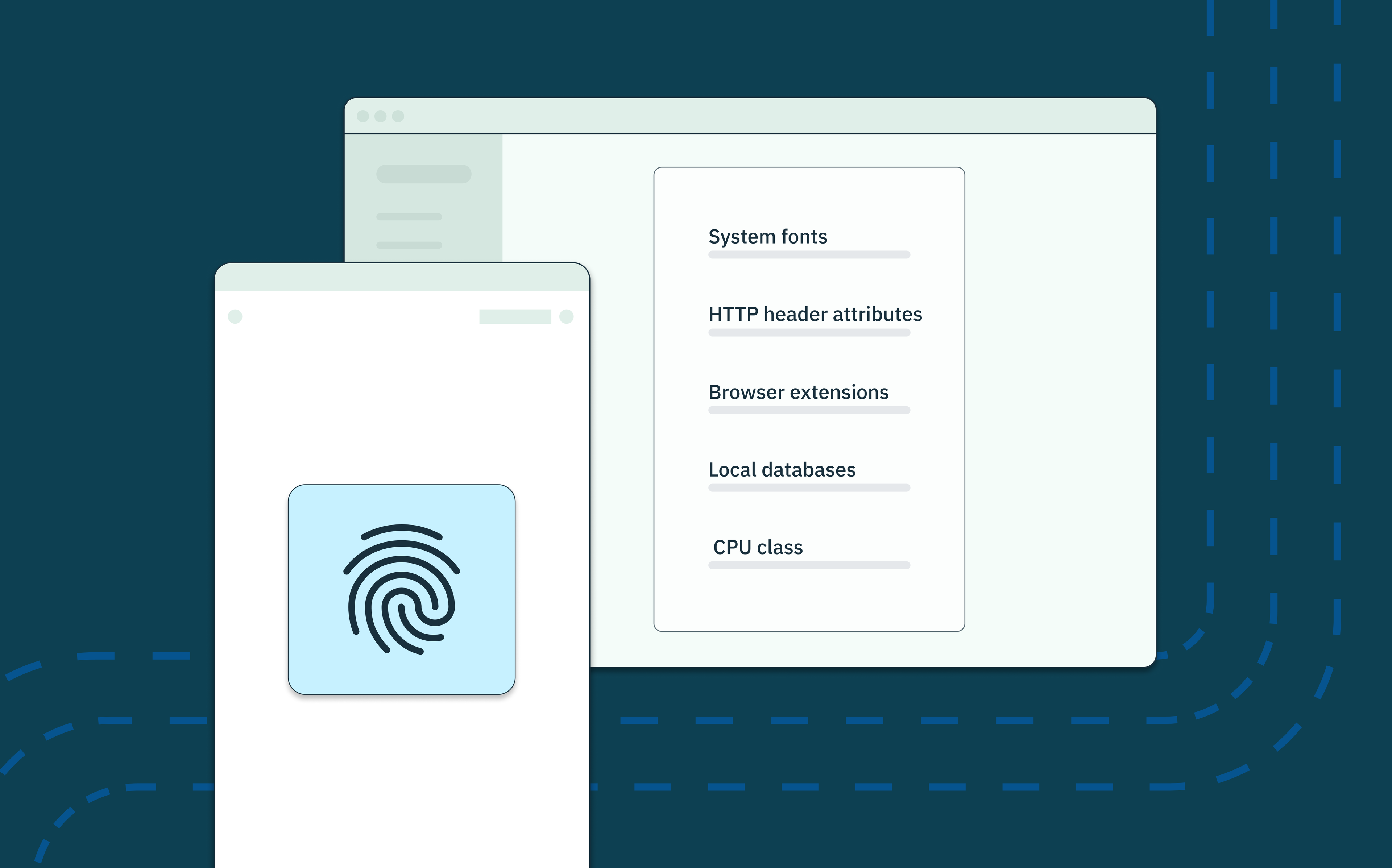
Device fingerprint insights go beyond limited pieces of traffic information such as IP addresses, number of requests and request headers to catch and thwart fraudsters or bots attempting to mimic the actions of real users.
How Stytch can help
As is now clear, reverse proxies should only be part of your broader security strategy. Stytch offers a holistic fraud prevention toolset to augment reverse proxies by shoring up your authentication defenses – including device fingerprinting.
Stytch Device Fingerprinting identifies unique characteristics of a user’s device, such as the operating system, browser version, screen resolution, and even unique identifiers like IP addresses, helping safeguard against different types of attacks and potential breaches. By combining these elements into an identifier, there’s enough entropy to ensure that the identifier is unique to each device.
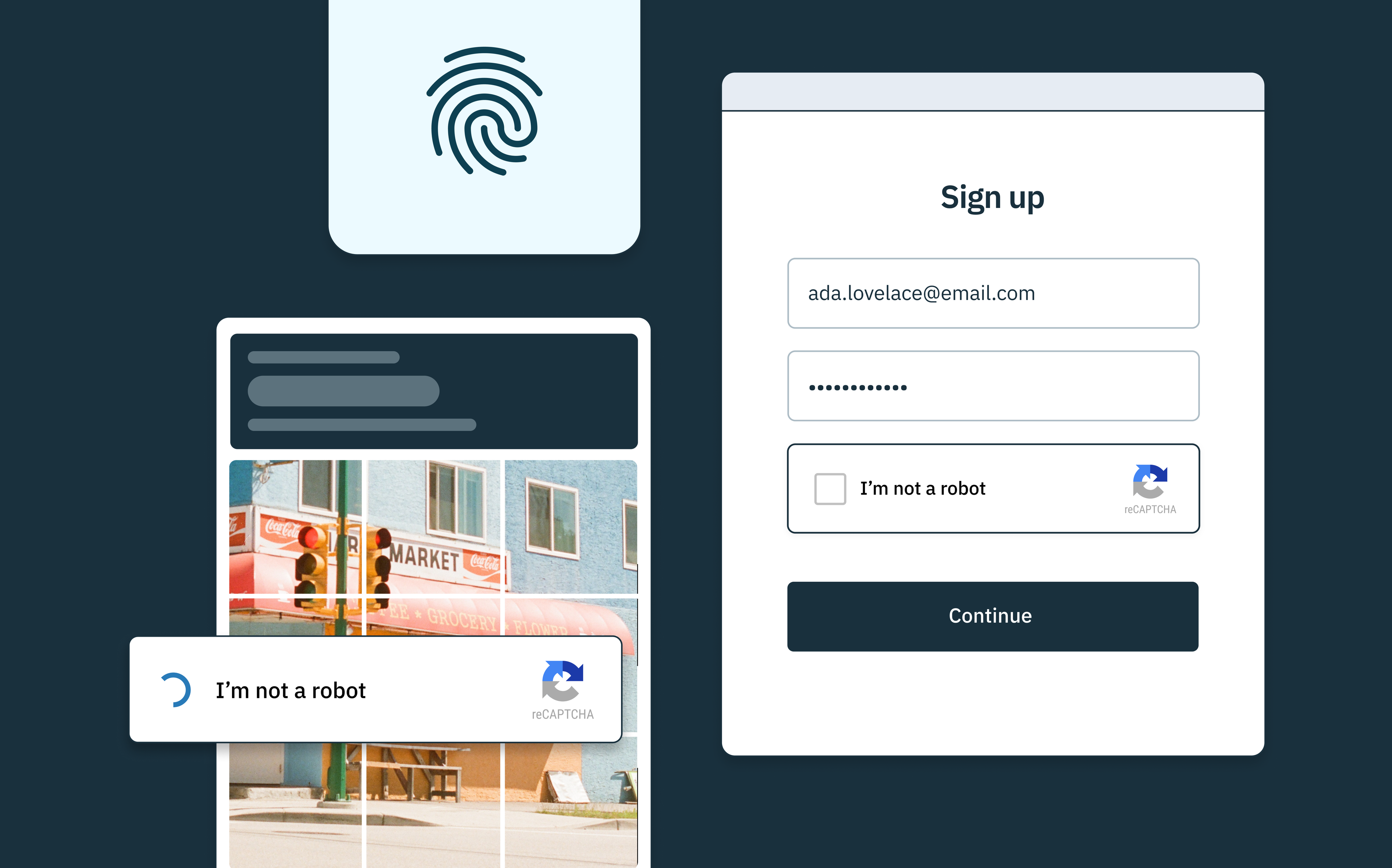
A step beyond traditional CAPTCHA, Stytch’s Strong CAPTCHA uses complex challenges that are easy for humans but difficult for bots and fraudsters to solve, effectively distinguishing between legitimate users and automated systems. Strong CAPTCHA works by loading an incredibly thin remote client that allows your user to solve the CAPTCHA, but ensures that bot farms are incapable of attacking your app.
To learn more about how these or other solutions work, reach out to an auth expert to start a conversation or get started on our platform for free today.
Prevent fraud with Stytch
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.