Back to blog
What is a SAML service provider? How to integrate your app with enterprise Single Sign-On
Auth & identity
Apr 17, 2025
Author: Stytch Team

A SAML service provider is a key component of enterprise single sign-on authentication, allowing businesses to integrate your app into their existing authentication system. SAML enables the link between an identity provider and different service providers by sharing authentication information in a standardized format.
Adding SAML support to your enterprise app or service can greatly broaden its potential user base, and it is a key requirement for many businesses seeking new SaaS tools. This article explains SAML and what you need to implement a SAML service provider.
What is SAML?
The SAML (Security Assertion Markup Language) standard defines how an identity provider (IdP) and a service provider (SP) communicate using XML markup. It is not a mechanism of authentication, but the language used to send and receive authentication information between systems.
By enforcing a standard of communication, SAML allows different services to exchange authentication and authorization data, which is used to implement enterprise single sign-on (SSO).
SAML Service Provider (SP) vs Identity Provider (IdP)
The two services that communicate using SAML are the identity provider and service provider:
- A service provider is any app you are logging into using single sign-on where authentication is handled by an identity provider. They receive authentication and authorization information from the identity provider in the SAML format. Access control is performed by the service provider using information provided by the identity provider.
- The identity provider handles the authentication of the user, storing their identity and login data and, having successfully authenticated it, communicating it to the service provider using SAML. It only supplies information to the service provider, and while this can include authorization decisions, it is generally up to the service provider whether a user authorized based on the SAML data.
To exchange data using SAML, both the service provider and identity provider must specifically support it. While SAML is a legacy standard, it is still widely used in modern authentication tools and systems.
If you are targeting a business use case, adding SAML service provider functionality to your software product is vital; many established organizations will already be using SAML-based single sign-on with a variety of other products, so being “plug and play” with their existing infrastructure will drive adoption.
When do you need SAML?
Organizations need their employees to be able to securely log in to a variety of services using SSO. To meet this requirement, your products can act as a SAML service provider so that they are able to connect to your clients' identity providers and integrate with their authentication infrastructure.
Popular enterprise identity providers that are used to manage access to different tools and platforms include Okta, Microsoft Entra (formerly Azure Active Directory), and Google Workspace.
Some example scenarios of using SAML for enterprise SSO include:
- Salesforce (SP) + Okta (IdP): Employees at a company use their Okta credentials to log in to Salesforce so that they don't need to remember a separate password.
- Slack (SP) + Azure AD (IdP): A global enterprise enables employees to access Slack using their Microsoft work accounts via Azure Active Directory, providing seamless logins across their Windows domain and mobile devices.
- Your app (SP) + Your client’s SSO IdP: Your SaaS application needs to integrate with whichever IdP your clients are using. Implementing a SAML service provider accomplishes this, allowing their employees to log into your app using their existing work accounts.
You can implement SAML authentication in your application yourself; however, development teams are increasingly relying on authentication as a service (AaaS) to handle all of the authentication in their applications. This approach simplifies the process of making your application a SAML service provider while providing increased security and reducing development and hosting overheads.
Consumer-focused apps that don't target business use cases are less likely to require SAML, instead relying on social logins to authenticate users using their accounts from popular platforms (for example, Google or Facebook). Embedded logins are becoming increasingly popular for this, keeping users within your application and giving your full control of their login experience.
What happens when a user logs into a SAML service provider?
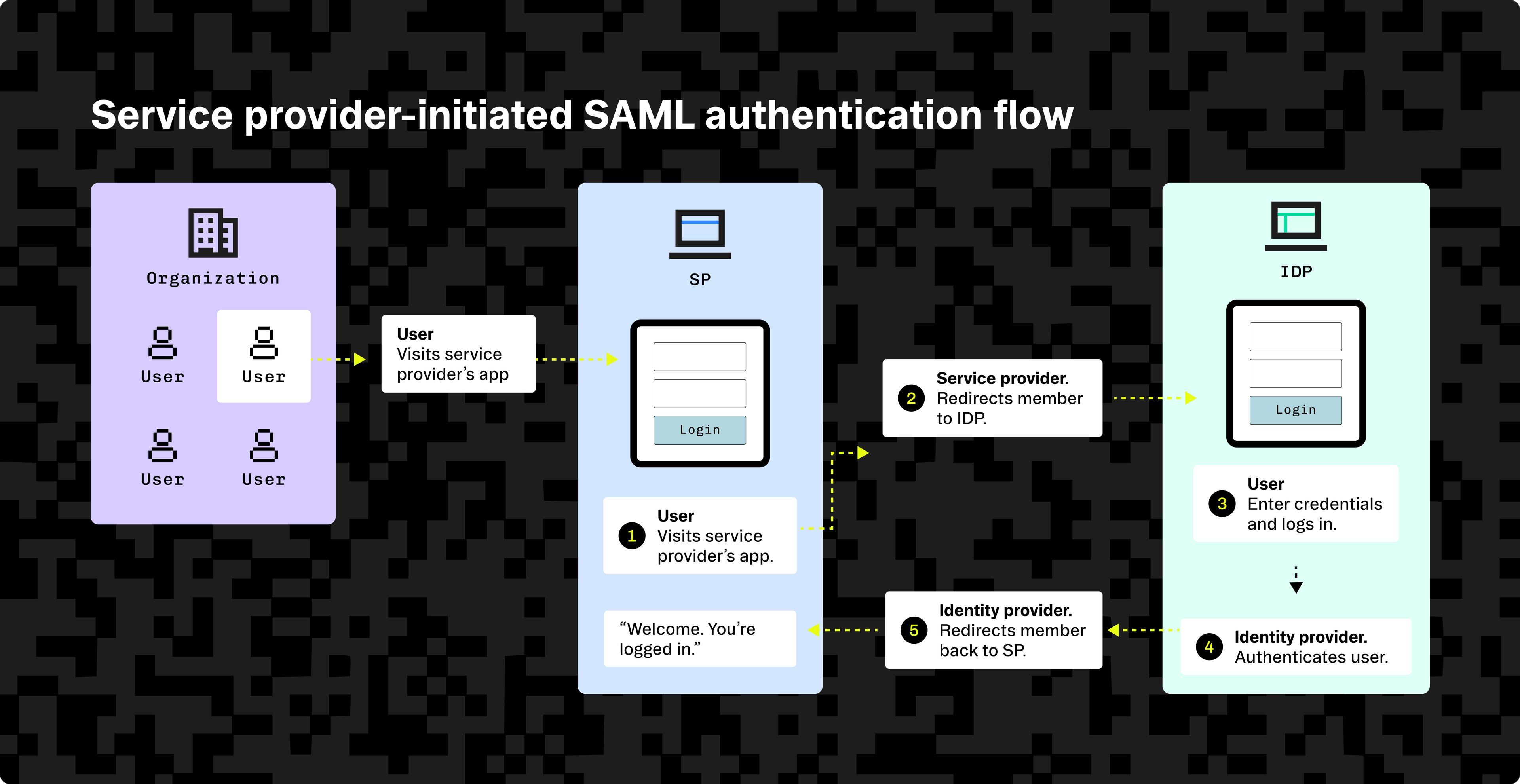
SAML is an open standard format based on XML that allows identity providers and service providers to exchange authentication info. It achieves this using the following elements:
- Metadata: SAML metadata is exchanged to establish trust between service providers and an identity provider, and it includes information such as supported bindings, security certificates, and endpoint URLs.
- Assertions: Messages from the identity provider containing the information the service provider needs to identify a user.
- Bindings: The mechanism used to transmit messages; for example, HTTP POST requests/redirects, HTTP artifacts, and SOAP (a lightweight transfer protocol).
- Protocols: The SAML standards being used to communicate data. There are several different protocols targeting different use cases (such as different authentication flows).
SAML profiles describe how all of the above are combined for a specific use case; for example, web-browser SSO. There are two authentication flows that can be implemented with SAML:
- SP-initiated: The user accesses the service provider, and the application initiates the authentication flow, redirecting to the IdP.
- IdP-initiated: The user logs into the identity provider service directly, which then navigates to the service provider once they are authenticated.
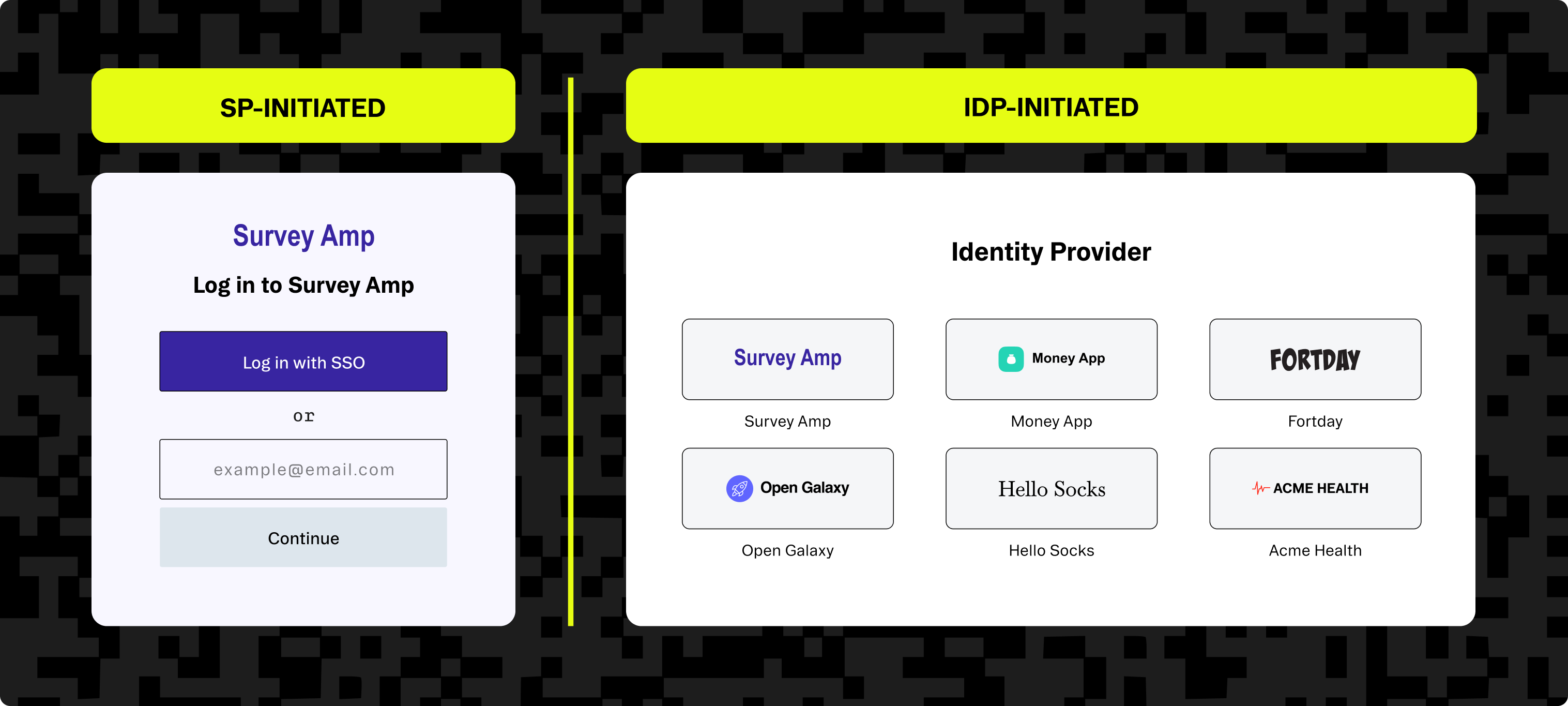
SAML service providers as part of an enterprise authentication solution
SAML-based authentication is usually mixed with other security technologies in enterprise environments. It is important to understand the different authentication and authorization technologies and their terminology so that you are clear on what you need to do to become a SAML service provider and how your customers will use this functionality.
SAML vs SSO
While SAML is often used to implement single sign-on, it is not synonymous with it and is not the only available SSO technology.
SAML vs OIDC
OICD (OpenID connect) is a modern alternative to SAML for transmitting authentication information. It uses JSON instead of XML and is less complex to configure. As SAML is still widely used in enterprise and supported in new tools, OIDC does not replace SAML — they are simply alternative technologies, and tools may support one or both.
SAML vs OAuth
SAML and OAuth (Open Authorization) serve separate purposes: While SAML is primarily concerned with authentication (though it does have limited scope for authorization data), OAUTH deals only with authorization and provides a more extensive mechanism for in-house and third-party software to authorize without having to exchange identity data. While OAuth and OIDC are often used in tandem, SAML and OAuth can also be used together in enterprise SSO where external tools also require authorization.
SAML vs LDAP
LDAP (lightweight directory access protocol) are different technologies for exchanging data with different purposes that can be used in conjunction. LDAP is a protocol for managing user information, which may be stored on a system acting as an identity provider in a SAML-based SSO solution.
SAML vs SCIM
SCIM (System for Cross-domain Identity Management) is a standard protocol for synchronizing information about users and groups between services providers and identity providers. SCIM does not perform authentication or authorization, but it can complement SAML by ensuring that user and group information is propagated between services whenever changes are made.
Turning your app into an SSO-ready SAML service provider
A SAML service provider and identity provider are not the only way to implement SSO. When choosing how you will build your SSO integrations, you should consider what your enterprise customers expect and how your app functions.
- Your customers' identity providers: Assess which identity providers are already deployed for your target industry. Do the IdPs you need to integrate with (for example, Windows Active Directory) only support SAML, or do they support other authentication protocols that may be more suitable?
- Your authentication solution: Is there a readily available way to add SAML support to your existing authentication? Does it support other protocols that may be required in the future (such as OIDC for authenticating third-party SaaS apps, or SCIM for synchronizing data)?
Once you have set requirements, you can work on implementing the SAML standard in your apps. Doing this in custom code is a significant undertaking that comes with security risks, and even leveraging libraries such as node-saml and python3-saml requires care, as even small mistakes can result in a significant security vulnerability.
Building your own authentication and authorization infrastructure means taking full responsibility for its ongoing maintenance and security. This is why many development teams are turning to authentication platforms that provide advanced security mechanisms that help to stop sophisticated attacks from bots and malicious users, without having to hire their own in-house security experts.
By building your app with the Stytch authentication platform, you get full support for SAML, OIDC, SCIM, and OAuth for SSO. Stytch bridges the gap between compatible authentication components and user-facing services, as well as machine-to-machine authentication, for a single, comprehensive solution for all of your internal and customer-facing authentication requirements.
Protecting this is an evolving array of protection features, including device fingerprinting, bot detection, and AI-powered behavior analysis. Stytch also includes additional functionality including a web-based management dashboard, audit logging, and a variety of log-in methods to streamline your authentication process.
Contact sales or get started to find out how Stytch can secure your enterprise platforms.
Build with Stytch
APIs and SDKs for authentication, authorization, security and fraud prevention
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.