Back to blog
Anti-spoofing tools and techniques
Auth & identity
Oct 17, 2024
Author: Alex Lawrence

Anti-spoofing tools and techniques
Catching and/or preventing user agent spoofing these days is harder than ever in our high-tech digital environments. Despite the challenge, making investments towards stronger anti-spoofing measures to protect your applications and data will pay enormous dividends in the overall security of your application's business systems.
When spoofing is being used with emails, some authentication protocols can help with anti-spoofing by validating the legitimacy of the email sender. Examples include Sender Policy Framework (SPF), Domainkeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC), which play a crucial role in anti-spoofing efforts by validating the legitimacy of email senders and safeguarding users' credentials.
But how can you better spot fake data packets, manipulated user agent properties, and unauthorized access attempts before they find a way into your application? In this article, we’ll overview preventative anti-spoofing measures, their role in security, as well as recommend some practical solutions to help you combat them.
Understanding anti-spoofing
Anti-spoofing technology should be part of any modern, sophisticated security solution. It is specifically designed to identify and block spoofing campaigns online, which can take various forms (and are always evolving). Attackers often use spoofing techniques, such as IP address masking via VPNs, proxies, and botnets, to gain access to business networks, circumventing security measures and posing serious threats to sensitive information. The primary goal of anti-spoofing technologies is to prevent unauthorized access by confirming the legitimacy of incoming data and separating the welcome from the wicked.
On a technical level, anti-spoofing technology protects networks by identifying the techniques malicious actors use to impersonate requests made by legitimate devices.
Common types of spoofing attacks
Spoofing attacks seek to replicate trusted sources to deceive victims and access sensitive information. Recognizing various spoofing attacks is crucial to understanding the anti-spoofing measures needed to combat them.
- IP spoofing is a common technique where bad actors send packets from multiple different IP addresses to mask their identity and location. This technique is often used in Denial-of-Service (DoS) attacks to overwhelm a target system with traffic, causing disruptions. This also can be in the form of IP address masking via VPNs, Proxies, or compromised machines in a botnet.
- User agent spoofing is a technique where attackers change the
User-Agentheader in HTTP requests to disguise the type of client they are using (e.g., making a bot appear as a legitimate browser). - Header spoofing is a technique that involves manipulating HTTP headers to fake different aspects of the request, such as language preferences, encoding, or security headers.
- Session token spoofing is a technique where an attacker steals or forges session tokens to gain unauthorized access to an application.
Easily-integrated, holistic solutions are necessary to protect against various spoofing attacks, combining anti-spoofing measures to safeguard organizations from unauthorized access on multiple fronts and maintain the integrity of their systems.
How anti-spoofing technology works
In anti-spoofing, filtering mechanisms are employed to detect spoofed packets or device attributes. These mechanisms often utilize rules set on network gateways like firewalls or routers to identify and block malicious data by examining incoming packets. Ingress filtering is a common method used to check packets with conflicting source IP addresses, ensuring that incoming packet traffic is legitimate. Source address validation ensures incoming IP packets match legitimate network ranges.
Packets originating from the internal network are automatically dropped if they present conflicting source IP addresses, illustrating how rules at network gateways like firewalls or routers are used to enhance security. Packets can also be filtered out by passive request properties leaked by the senders machine using more advanced techniques like TLS fingerprinting
Modern anti-spoofing technology implements packet blocking by recognizing and blocking code that matches known spoofing patterns. Device fingerprinting technology, an increasingly powerful tool in fraud prevention, plays a vital role in this process by collecting various device attributes to create a unique identifier, which helps in recognizing and blocking fraudulent activities.
As noted, spoofing tactics are constantly evolving. These days, AI and machine learning are increasingly used to process complex data and adapt to new spoofing tactics. A layered strategy to identify and stop spoofing attempts early should combine multiple methods to enhance effectiveness.
Anti-spoofing for network security
Continuous monitoring and auditing of network traffic and user activities help identify potential spoofing attacks. Intrusion detection and prevention systems look for unusual patterns in network traffic that might indicate a spoofing attempt, while device and browser fingerprinting enable businesses to detect and respond to potential threats effectively, even when users try to conceal their identities.
Implementing these measures often involves a trade-off between security and user experience, making it challenging to achieve high security without inconveniencing users. However, the benefits of enhanced privacy and protection often outweigh these challenges. A solution like Stytch that can easily integrate into your existing system through modular APIs and SDKs makes the most sense for many businesses looking to streamline resources.
Stytch fraud prevention solutions for anti-spoofing
Stytch offers one of the industry’s strongest user-agent deception detection engines, capable of spotting automated attacks and spoofing attempts.
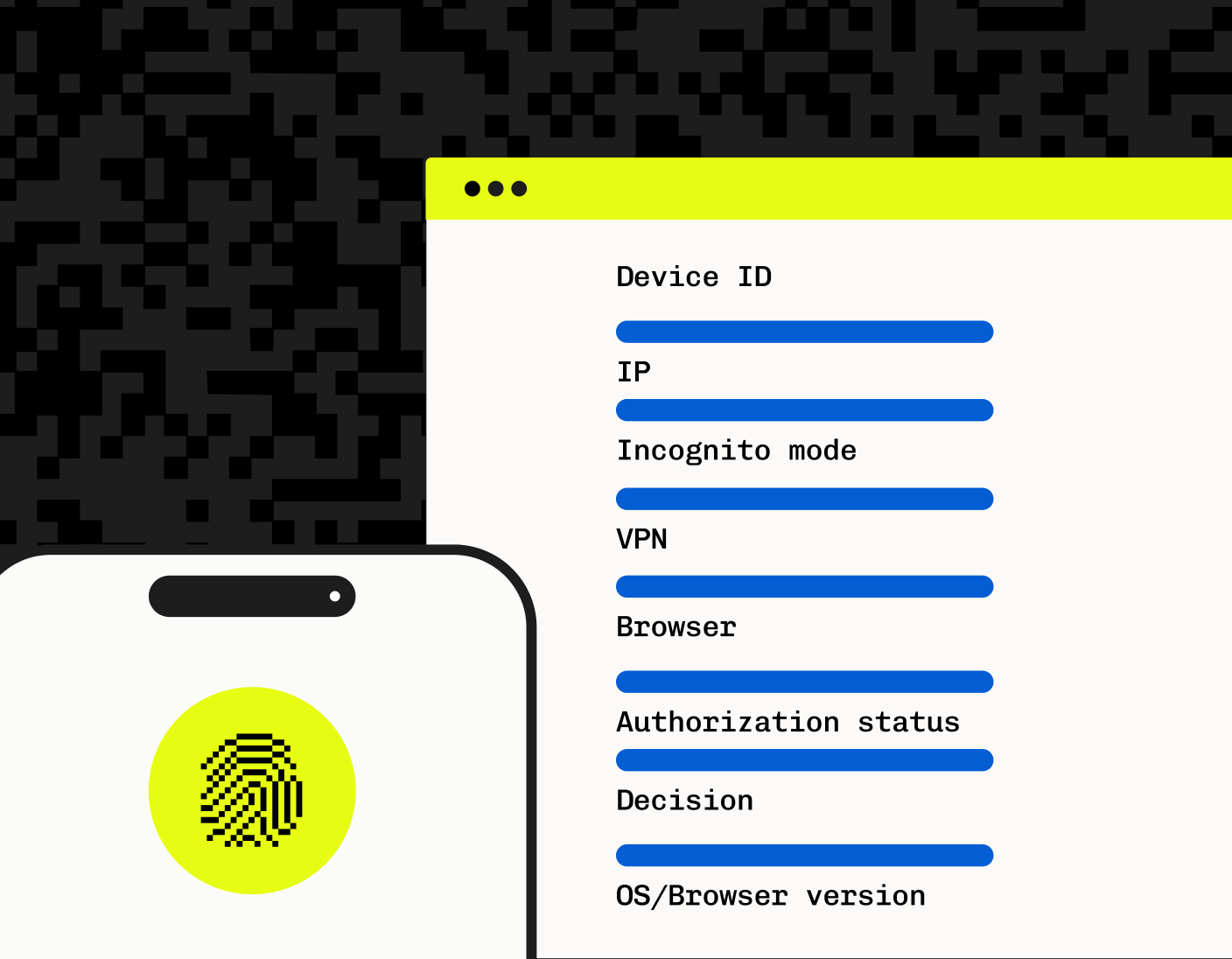
Stytch Device Fingerprinting (DFP) is designed to provide robust protection against identity spoofing by creating stable, consistently repeatable identifiers for each user device. At its core, DFP employs a heavily obfuscated JavaScript fingerprinting script to gather and analyze device signals securely. This allows for the precise creation of telemetry IDs that can identify and block fraudulent actors. It ensures that requests are genuinely made by the claimed browser, maintaining integrity and security. This combination of industry-standard and proprietary signals means that each device can be accurately identified and monitored.

Stytch Device Fingerprinting solution also leverages ML-Powered Device Detection to detect and categorize new threats, device types, and spoofed attributes in real time.
By employing Stytch Device Fingerprinting, applications can enhance their detection capabilities against any spoofing techniques, ensuring comprehensive security measures and a seamless user experience.
To learn more about Stytch DFP and it’s powerful ability to identify devices across your web traffic to prevent spoofing, get in touch with an auth expert, or get started using Stytch, today.
Build Fraud Prevention
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.