Back to blog
Bot mitigation software: A fraudster's foil in an automated world
Auth & identity
Dec 22, 2023
Author: Alex Lawrence
We talk a lot here at Stytch about how malicious bot traffic has become a significant threat, constituting an increasingly large portion of web traffic. Given that bots make up around 40% of all internet traffic (and growing), bot mitigation software should be at the forefront of any security team’s conversations, no matter the industry.
In this article, we’ll go a little bit deeper than usual into bot mitigation software, exploring its necessity, functionality, and benefits in safeguarding digital applications and businesses from bot traffic.
But first, some background on bad bots and their methods of attack.
Types of bot attacks: what you should know
To best understand the role that bot mitigation software can play, it helps to first understand the nature of common bot attacks. In our AI-infused era, the types of modern bot attacks are many, and inevitably scammers will find novel ways year after year to deploy software that circumvents new security measures and bot detection software. Nevertheless, let’s cover some of the more common types of bot attacks that persist.
DDoS attacks and credential stuffing
DDoS attacks, where bots flood a website with traffic to render it unusable, are a common threat. Bot detection and mitigation software employs DDoS protection to filter out this malicious traffic. Similarly, credential stuffing attacks, where bots attempt to gain unauthorized access using stolen credentials, can be stopped by identifying and blocking bots before they can breach security – a strong argument for improving authentication with measures such as device fingerprinting, strong CAPTCHA protocols, and ‘unphishable’ authentication (we cover several of these in practice at the end of this article).
Payment fraud and account takeover
Likewise, payment fraud and account takeover are significant concerns for online businesses, particularly of the financial services ilk. Bot detection software plays a crucial role in preventing these types of attacks by detecting and blocking bots attempting to perform unauthorized transactions or access user accounts.
Content scraping and price scraping
Bots can also be used to scrape content from websites or apps, including sensitive data like pricing information. This can lead to competitors gaining an unfair advantage or users receiving incorrect pricing. Bot detection software helps prevent this type of data theft by detecting and blocking bots attempting to scrape information.
Web scraping and API abuse
Web scraping is another form of data theft where bots gather information from websites or APIs for malicious purposes. Bot protection and bot detection software can detect and block these scraping attempts, preventing sensitive data from falling into the wrong hands.
Credit card and bank credential fraud
Bots attempt ATO attacks to gain control over user accounts for financial exploitation. Services like Stripe and Plaid, which offer API endpoints for credit card and bank account verification, are frequent targets of these types of attacks.
SMS toll fraud
In SMS toll fraud, unauthorized individuals or bots manipulate messaging services to send large volumes of SMS messages to premium-rate numbers owned by the fraudsters. Often, these messages are sent without the owner’s knowledge, leading to unexpected and excessive charges on their phone bill. SMS toll fraud is more prevalent in international mobile networks due to varying regulations and oversight across countries.
Compute resource fraud
Compute resource fraud is where bots exploit platforms offering computational resources. These bots, controlled by fraudsters, leverage free tiers of cloud-based services or computational platforms to mine cryptocurrencies, conduct data processing tasks, or even host illicit content. The inherent open-access nature of platforms like AWS, Github, and Heroku make them attractive targets for this type of fraud.
The impact of malicious bots

It’s well-documented that bad bot traffic can cause significant financial losses, reputational damage, and many other potentially catastrophic outcomes for businesses. And the chances are only increasing: According to Sift’s Q2 2023 Digital Trust & Safety Index, account takeover (ATO) bot attacks spiked by a staggering 427% in Q1 2023, compared to all of 2022.
How bad bots break things
Here are some of the many negative outcomes we’ve seen as a result of bot attacks in recent history:
- Financial losses: Depending on the severity of the attack, malicious bots can cause financial losses for businesses by disrupting their operations, stealing sensitive information, or extorting money to stop the attack. For individuals, bot attacks can result in identity theft or unauthorized access to personal accounts.
- Damage to reputation: A successful bot attack can damage a business’s reputation and erode trust with customers. For example, if a website is repeatedly taken down by DDoS attacks, customers may lose confidence in the company’s ability to protect their data and seek services elsewhere.
- Wasted resources: Dealing with bad bots also wastes valuable resources for businesses. Employees may have to spend time identifying and mitigating the attack, resulting in a loss of productivity. In some cases, businesses may have to invest in additional security measures or hire outside help to protect against future bot traffic and attacks.
- Disruption of services: Without proper bot detection, bots can disrupt various online services, including e-commerce sites, social media platforms, and financial institutions. This can cause inconvenience to users and result in lost revenue for businesses that rely on these services.
- Spread of misinformation: Bots can be used to spread fake news and misinformation, causing harm to individuals and society as a whole. This can also damage the credibility of reputable sources and make it difficult for people to distinguish between real and fake information.
- Legal consequences: Depending on the severity of the attack and its impact, businesses may face legal consequences for not adequately protecting their systems against bot traffic and bot attacks. This can result in fines, lawsuits, and damage to their reputation.
The necessity of bot detection and mitigation software
Given the extensive damage that uncontrolled bot activity can cause, implementing bot management, detection, and mitigation software has become a priority for many businesses. Here are some of the reasons why it should sit as item #1 on your bot management security roadmap, now.
The prime targets: applications and businesses
Recent research from Barracuda Networks suggest that bad bots account for nearly 30% of all bot traffic in 2023 from January to June. Moreover, according to Barracuda, account takeover (ATO) attacks – including attacks against APIs – are increasing. The data suggests that APIs, or application programming interfaces, remain under-protected and easy to target through automated attacks.
Applications and the businesses that offer them will always be among the most vulnerable to bot attacks given their distributed nature and inherent security gaps. Bot protection software is essential in this context.
Integrating bot detection and mitigation software in web applications and mobile apps is crucial to protecting sensitive data and maintaining functionality. This integration is especially important for mobile apps dealing with financial transactions, personal data, and other sensitive information.
Protecting web traffic from bot traffic inflow
People like us use the web and applications every day, browsing and scrolling for just about every aspect of our lives. But these days, we’re not alone out there: nearly HALF of the internet is comprised of bots, making bot mitigation excruciatingly hard.
Differentiating between bots and humans is a significant challenge, but bot detection tools and bot mitigation software hold some promise here. They can analyze traffic patterns and user behaviors on web or mobile apps to identify and block malicious bot traffic, ensuring that only legitimate users have access to a website or an app. This not only protects the website from potential harm but also ensures that genuine users have a seamless and secure experience without bot traffic that can distort the flow of code and information.
Virtual waiting rooms and sensitive traffic inflow management are two useful additional systems designed to protect websites from bad bot traffic without adversely impacting legitimate web visitors. This approach ensures that bot mitigation security measures do not become a barrier for real users.
How bot detection works at a high level
Bot management and detection software functions by scrutinizing incoming traffic to a website or application. It analyzes various attributes such as IP addresses, device characteristics with mobile apps, and behavioral patterns to identify potential bots. It can also block malicious bots at the door with various sophisticated authentication solutions (more on that below).
Flushing out bad bot traffic
Bots that accurately mimic human behavior pose a particular challenge. Advances in online behavioral analysis as well as leading-edge bot management threat intelligence can often distinguish them from legitimate users. Bot management software tools can help keep users and applications safe from emerging threats as well as credential stuffing, account takeovers, and web scraping which continue to be pervasive.
In addition to behavioral analysis, IP addresses are also closely monitored to identify and block bot traffic. Blacklisting known malicious IPs can effectively filter out a lot of bad bots, but it does not solve the problem entirely. Bot operators are continually changing IP addresses to evade detection, making it challenging for traditional methods like blacklisting to keep up.
As such, more advanced techniques are being developed by bot management software companies that go beyond just relying on blacklists. Some use machine learning algorithms to analyze and identify bot patterns, while others employ browser fingerprinting techniques to track user behavior over time and distinguish them from bots. Others implement bot traffic control mechanisms at the web application firewall (WAF) layer. Additionally, solutions like CAPTCHA tests can help filter out bad bot traffic by requiring users to prove they are human through visual or audio challenges.
A balance between security and performance
While the primary goal of bot management software is to mitigate threats, it’s essential to find a balance between security and performance. Overzealous bot detection can result in false positives, causing legitimate users to be blocked from accessing the site or application.
One way to ensure this balance is through customization options within the bot management software. This allows website owners and managers to fine-tune their settings and thresholds to fit their specific needs. For example, some companies may want to prioritize security over performance, while others may prioritize user experience and allow for a higher tolerance of bot traffic.
In addition, regular monitoring and analysis of bot traffic can help optimize the settings and thresholds used by the software to strike the right balance between security and performance. It’s also important to regularly update the software and stay informed about emerging bot threats to ensure continuous protection.
The future of bot management
Bot management software will continue to evolve and adapt to keep up with these changes. In the future, machine learning algorithms will become even more sophisticated and effective at identifying and mitigating bots. This will help reduce the need for manual intervention and customization, allowing the software to autonomously protect websites and applications.
Additionally, as bot attacks become more complex and difficult to detect, there will likely be an increased focus on proactive measures rather than reactive ones. This could include implementing strategies to actively prevent bots from accessing a website or application in the first place, rather than just mitigating their impact after they’ve already caused damage. This is where a strong authentication strategy coupled with technology to prevent bot-driven fraud can be the ace up your sleeve.
Stytch’s Device Fingerprinting: Leading-edge bot detection

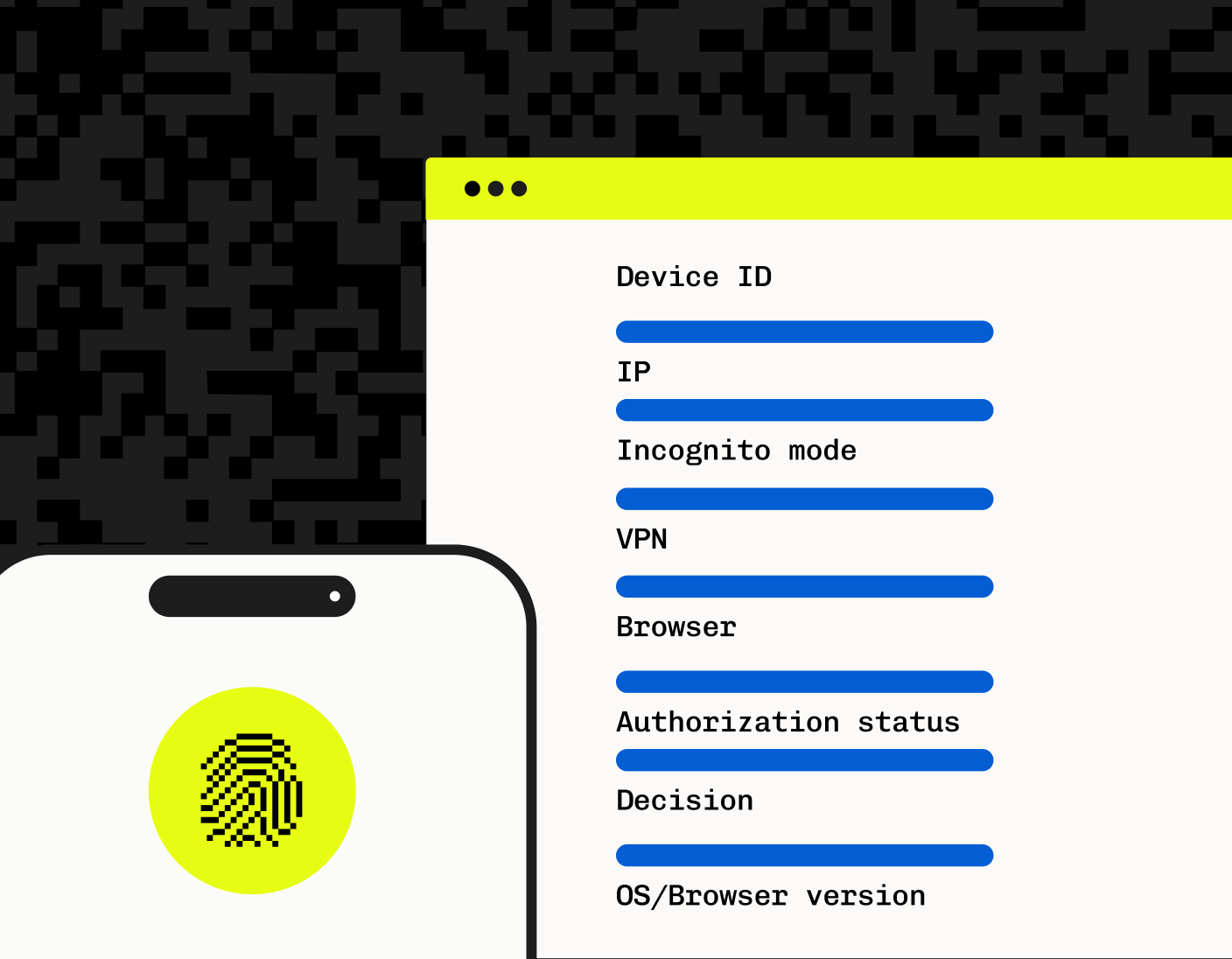
Stytch’s Device Fingerprinting (DFP) can protect against automated attacks by aggregating various attributes of a user’s device into a unique identifier, ensuring a high degree of accuracy in distinguishing legitimate users from fraudulent actors. The use of attributes like browser type, screen size, operating system, and timezone, combined into a single identifier, provides a unique ‘fingerprint’ for each device, effectively detecting and blocking bad bot traffic.
In-depth defenses
One of the key strengths of Stytch’s solution is its defense-in-depth approach, which obfuscates the fingerprinting process. This approach makes it tamper-resistant to reverse engineering and spoofing attempts by sophisticated attackers, addressing a common vulnerability in many DFP solutions. This level of protection is crucial in today’s digital landscape, where attackers continually evolve their techniques to bypass security measures.
Among other DFP solutions, Stytch’s DFP product stands out by integrating a mix of industry-standard and proprietary signals into stable identifiers. This capability, coupled with multiple security measures to prevent reverse engineering, ensures that Stytch’s device fingerprints remain reliable across various challenging scenarios such as incognito browsing, webviews, VPNs, and changes in user agent or IP addresses. Features like 99.9% unique signals to the device, clear action recommendations (ALLOW, BLOCK, CHALLENGE), and multiple fingerprint types tailored for different use cases further enhance its effectiveness.
An innovative approach to bot mitigation
The core of our DFP solution, a JavaScript library coupled with a Web Assembly binary, is a testament to Stytch’s innovative approach. This setup not only gathers and sends signals efficiently but also processes these fingerprints on the backend to provide actionable telemetry IDs. These IDs come with clear recommendations, simplifying the decision-making process for businesses in real time.
To learn more about Stytch’s DFP or other innovative solutions we offer to help protect your business and applications from the many threats present today, reach out to an auth expert, or get started on our platform for free.
Prevent fraud with Stytch
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.