Back to blog
Build vs. buy: what to consider when setting up an auth flow
Auth & identity
Feb 24, 2022
Author: Julianna Lamb
Deciding whether to build new software and features in-house or buy an API or SDK solution from a third-party vendor is a question engineers face on a regular basis. When it comes to your authentication flow, that choice can have major implications for security—not to mention your user and developer experience and the resources you’ll dedicate to implementation and maintenance.
Below, we review the criteria product and engineering teams should keep in mind when putting an authentication flow in place—and examine why turnkey solutions are becoming a popular way to boost efficiency, enhance security, and optimize user engagement and conversion.
The pros and cons of build vs. buy
There are many factors your engineering team might consider when weighing whether to build an authentication flow in house or turn to third-party specialists, but here are the top four:
Opportunity Cost
Rolling your own auth means you control the process and can custom-build to your app’s needs. But you’re also going to spend a lot of time and effort doing it. While buying a readymade solution may seem like a high upfront cost, creating that same solution in-house—along with a robust sandbox environment to support and secure it—is more expensive than you might think.
In addition to the initial build, you’ll have to factor in engineering costs around maintenance and upgrades as bugs emerge and industry trends evolve.
On top of that, engineering projects often go over time and budget. An early study found the average overrun to be 27%, with one in six companies overshooting estimates by 200% or more. That is valuable time that could be spent focusing on building your roadmap.
Complexity
Any authentication solution introduces unique challenges and takes significant effort to architect and implement, which can take focus away from building your core product. This is especially true of novel solutions such as session management, biometrics like WebAuthn, and high-converting flows like Google One Tap.
In other posts, we lay out the many steps that go into building auth solutions like SMS one-time passcodes and email magic links—and that’s if you only implement one. You’ll need to repeat the process if you want to leverage the significant security benefits of multi-factor authentication (MFA).
Authentication providers can save you time, resources and headaches by ensuring you get a secure solution right out of the box. Edge cases with provider integrations can be costly over time. But some providers, like Stytch, also wrap in access to particularly tricky (but valuable) options like route-based (or just-in-time) authentication, which lets you stagger verification factors according to the sensitivity of a user’s actions, introducing extra friction only when it matters most.
Security
Dealing with app security can be a burden for engineers and open your site to potential risks and threats. To assess your appetite for taking on this risk and security management in house, ask yourself:
- How sensitive is the user data your app handles?
- What are the possible consequences of a data breach?
- Does your team have the time and capacity to respond in real time and troubleshoot as security vulnerabilities arise?
Depending on your answers, you may want to partner with a company dedicated to handling these very issues. Top authentication providers—who are used to managing high-stakes flows, including for large-scale financial institutions—are SOC 2 Type II certified, run frequent security audits, and take proactive steps to keep up with the latest threats.
Auth expertise
Tech moves fast—really fast. Building innovative user experiences and authentication flows often requires inside knowledge across a variety of verticals, each with its own endpoints and edge cases. It also takes staying current to new innovations and technologies in the auth space.
You can designate a member of your team to keep up with shifting industry best practices and continually update your auth. Or, you can turn to a third-party provider that’s steeped in these details and navigates the ins and outs of key edge cases for you.
How a turnkey auth solution can boost your business
In recent years, and with rising numbers of reliable, easy-to-integrate APIs and SDKs on the market, many engineering teams have decided to buy auth solutions instead of build them from scratch. Some of the reasons your company might choose to partner with a third-party authentication partner include:
Efficiency
Opting for a pre-built solution takes the heavy lifting off your engineering team, gets your auth up and running quickly, and allows you to focus on optimizing your core product.
Savings
Authentication providers are often able to consolidate their resources and offer solid solutions at lower cost due to increasing economies of scale.
Simplicity
With an auth provider, your team gets a quality solution right out of the box. You can even choose between APIs and SDKs depending on how far in the weeds you want to get with integration and customizations.
Security
Partnering with experts means your team can offload the anxiety of safeguarding your data and let your authentication partner worry about the details.
Support
Auth providers are tuned in to the latest industry best practices and keep their products up to date to drive better performance and conversion rates for partnering apps.
Stytch tops the list
Once you’ve decided to go with a third-party solution, the question then becomes, what is the best authentication provider for your app?
There are a few reasons Stytch stands out and offers the best auth solutions on the market:
Flexibility
Because of the way we’ve structured our direct APIs and customizable SDKs, Stytch works entirely in the background to secure your app. Your team owns everything with the UI and UX, so users get an experience that’s 100% on-brand.
Easy integration
We don’t need to tell you that clear, accurate docs can make or break an integration. Stytch is built by developers for developers. We get our partners fully integrated in a matter of days, and our team is always available to jump on a call or chat.
Built-in redundancy
With service-based auth flows via email and SMS, communication providers can be a point of failure, effectively shutting down your login flows and user acquisition with any downtime. Stytch monitors uptime and latency, routing to multiple providers to ensure your users always have a high quality experience.
Better UX and conversion
As a passwordless solution, Stytch doesn’t sacrifice user experience for security. We keep friction low and track performance metrics with our SDKs, so we can identify where users might be falling off your auth flow and work with you to boost conversion.
Scalability
As your app expands, more users will demand more flexible authentication options. Stytch takes a one-stop approach to auth, with a variety of solutions wrapped into a single cost.
Key takeaways
While the buy or build debate is never simple, some careful consideration can easily tip the scale when it comes to authentication.
Ultimately, you may decide that it’s worth letting a third-party auth provider own the costs and hassles of managing your flow, so you can focus your time and resources on your business.
Learn more
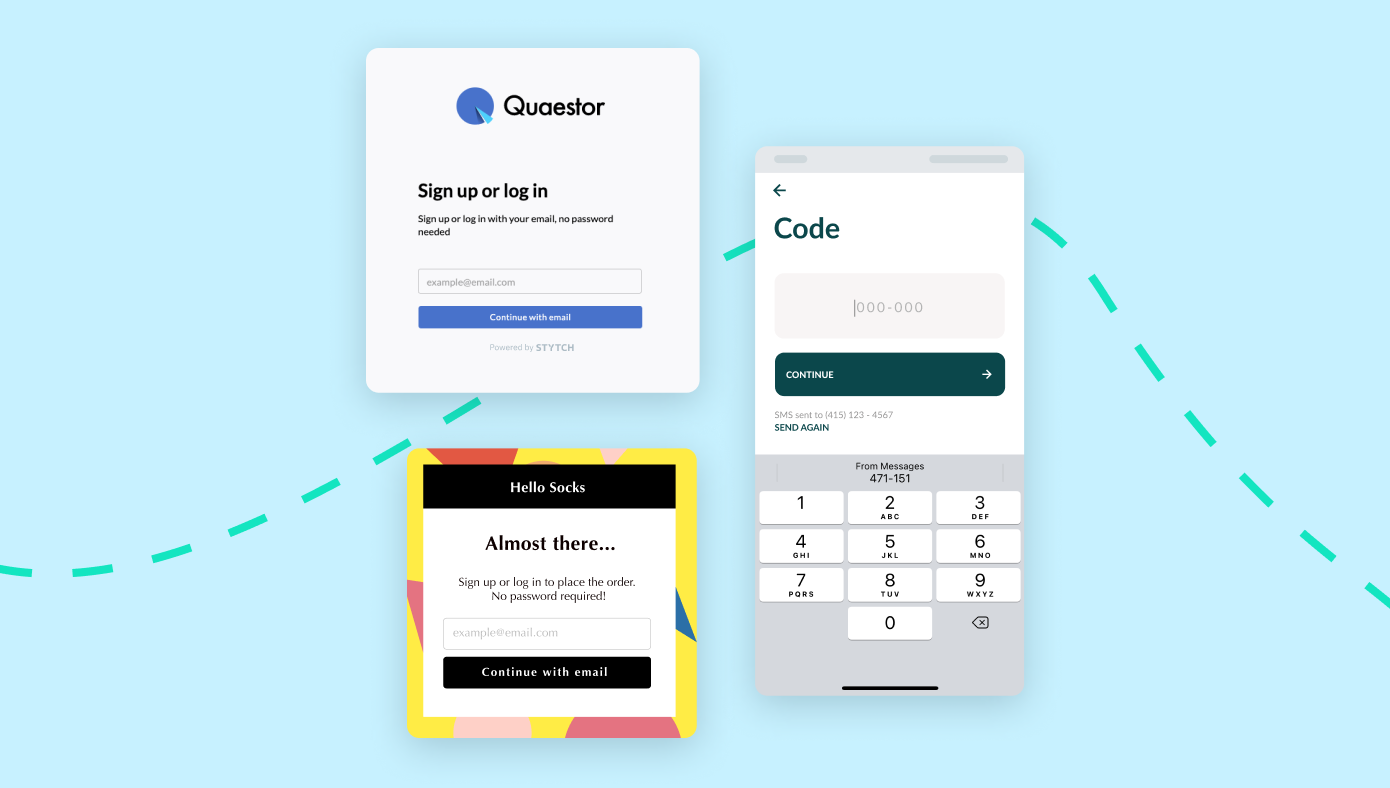
Our passwordless solutions make authentication simple, with easy-to-integrate APIs and SDKs that are fully customizable to your brand.
Build auth with Stytch
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.