Back to blog
The FIDO alliance and a passwordless future
Auth & identity
Feb 2, 2023
Author: Gedney Barclay

Stytch is thrilled to announce that as of 2023 we are now part of the FIDO alliance. In this article, we’ll discuss what FIDO is, why they’re important in the world of authentication, and why we joined.
What is the FIDO Alliance?
The FIDO Alliance is a nonprofit that began developing and improving security protocols to reduce the overreliance on passwords. In 2009 PayPal discussed its proposal for using biometrics as an alternative way to authenticate users, instead of using passwords. These conversations inspired a new industry standard for passwordless access using public-key cryptography and local logging technologies. In 2012, the FIDO alliance (Fast Identity Online) was formed.
Why is FIDO authentication passwordless?
We’ve written about the advantages of passwordless auth at length at Stytch – including the weaknesses of passwords, how to introduce passwordless options to password-familiar users, an overview of passwordless auth methods by business vertical, and more. But in a nutshell, passwords…
1. Aren’t secure enough
According to Verizon’s Data Breach Investigations Report, passwords or compromised user credentials have been the cause of over 80% of breaches. With the sophistication of phishing attacks and credential stuffing techniques, passwords as a security technology are no longer enough to protect our accounts and information. Even with newer developments with two-factor or multi-factor authentication, they're simply too easy to compromise.
2. Create friction for users
One of the reasons passwords are so insecure is that they’re hard to remember, and most users don’t receive good guidance about how to make passwords secure. Account creation and password reset flows tend to be long and convoluted, meaning users bounce from sites or abandon carts far more than they would if there were an easier way to sign up or log in. With passwords proving to be a let-down in both security and user experience, it’s easy to see why an alliance formed to create a better alternative.
How FIDO pursues a passwordless future
Since its founding, the alliance has pursued its passwordless mission by:
- Technical specifications: FIDO develops open and interoperable tech specs for passwordless solutions to make it as easy as possible for companies to wean themselves off of passwords and pursue more secure, user-friendly alternatives.
- Certification: FIDO runs certification programs that maintain quality and oversight of passwordless adoption.
- Standardization: Once mature, FIDO submits their technical specifications to standards development organizations to get their specs standardized and popularized in the dev community at large.
FIDO passwordless authentication technology – how it works
While we’ll be publishing a deeper dive into the ins and outs of this technology later on this quarter, at their core all FIDO technologies rely on public key cryptography to both identify users and keep their information secure.
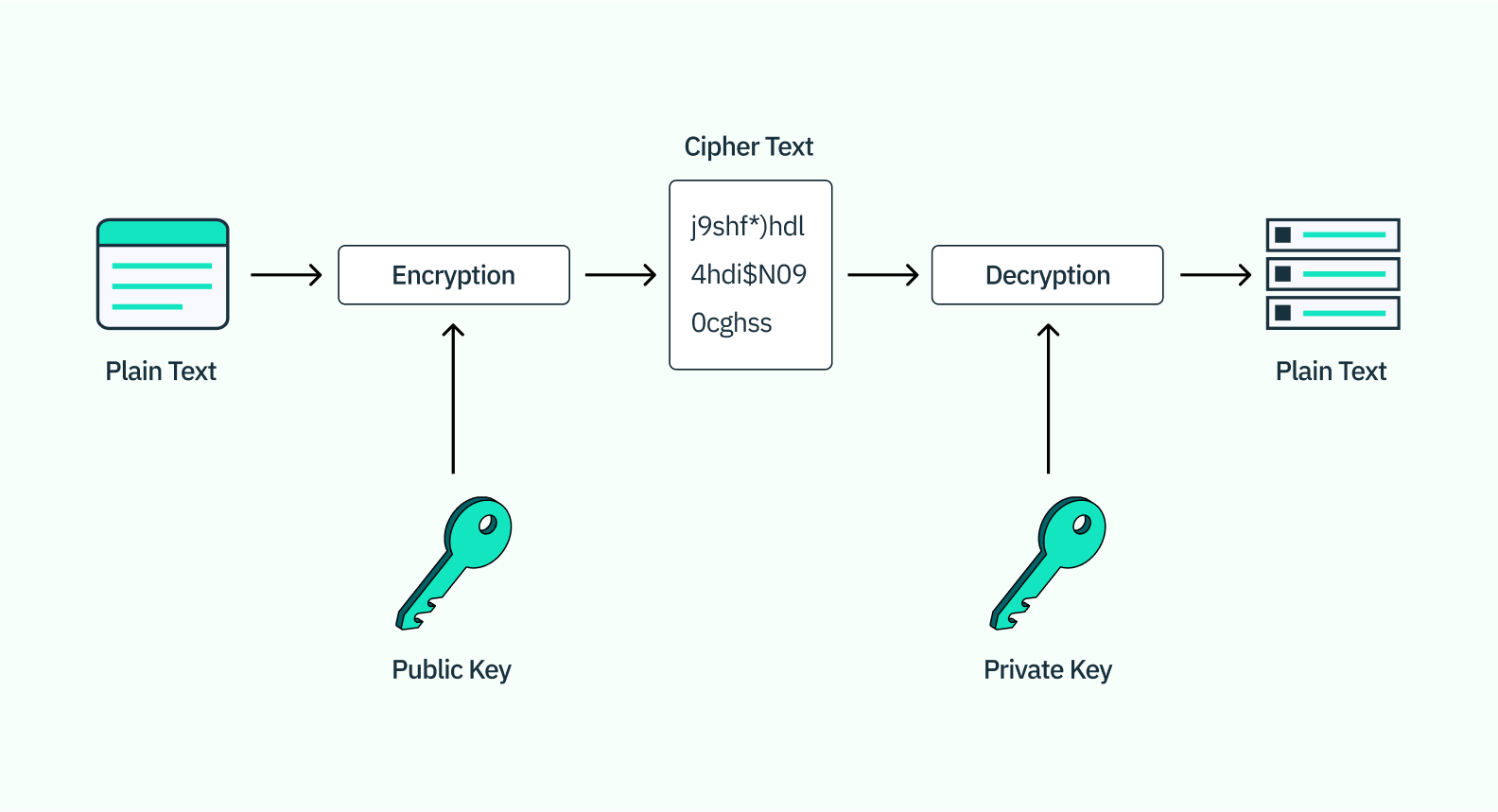
Public key cryptography
Public key cryptography is an encryption scheme built around the relationship between two unique keys—a public key that encrypts the data, and a private key that decrypts it. What makes this kind of cryptography more secure is that while the public key is stored on the server (and thus fairly easy for others to access), the private key is stored either on the user’s device or on a hardware security module like a USB or biometric scanner. When a user authenticates, the private key sends a message with a unique signature to the public key, which then decrypts access to the server.
WebAuthn
After developing some initial standards and specs based on public key cryptography, FIDO wanted to find a way to make their passwordless methods more widely available. To do this, they started to work on new technical specifications that enabled FIDO authentication methods to be called directly in browsers and platforms via APIs. The most well-known of these API-based specs is called FIDO2: Web Authentication, or WebAuthn. Initially released in partnership with the World Wide Web Consortium (W3C) in 2019, WebAuthn has quickly become one of the most important advances in popularizing passwordless authentication because of its ability to be easily adopted and integrated by a much wider community of web browsers and applications.
Want passswordless auth for your app? Switch to Stytch.
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Common WebAuthn applications
While you might not be familiar with the inner workings of FIDO2 or its technical specifications, you have probably encountered FIDO specs in the wild in one of three main ways:
In-device biometrics
If you’ve ever used your phone or computer’s thumbprint reader to log into an app or website from that device, you’ve used in-device biometrics. In-device biometrics – sometimes also referred to as a “platform authenticator” – verify both possession of the user’s original device and biometric proof in the user’s facial ID or fingerprints. That strength though is also its weakness: because in-device biometrics are by definition device-specific, they are somewhat limited for users who live their online lives on multiple devices.
Yubikey
Yubikeys are a small piece of hardware you can plug into a number of devices that exchange public and private key information with various apps on that device. They are referred to as “cross-platform authenticators” because, unlike platform authenticators that are tied to a particular device, the hardware key can be moved from one device to another and retain your authentication method. Similar to device biometrics, Yubikey's strength is also its downside: if you lose your key, there is no backup, and it can be very difficult and time-consuming to regain access to all of your accounts that relied on Yubikey for authentication.
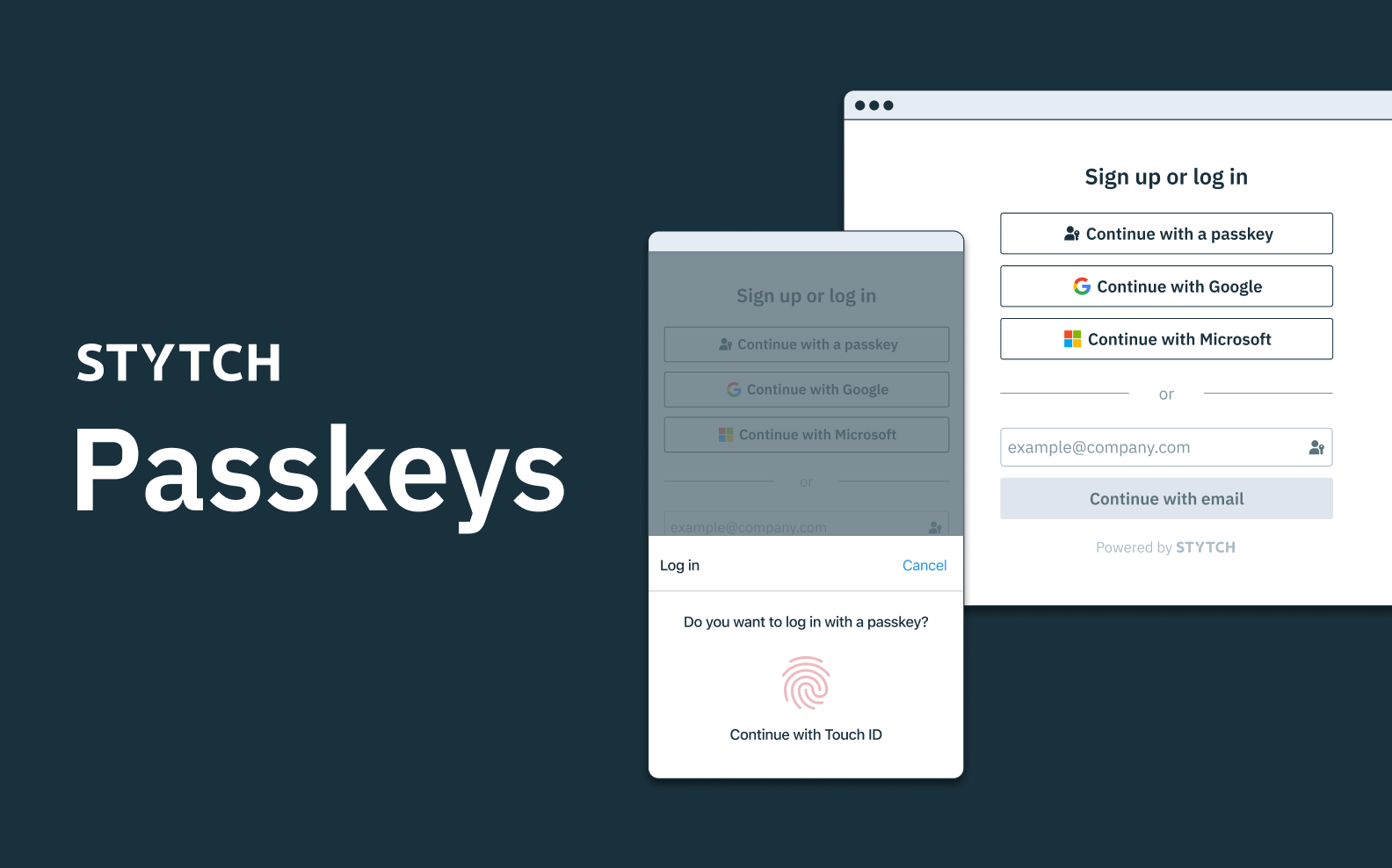
Passkeys
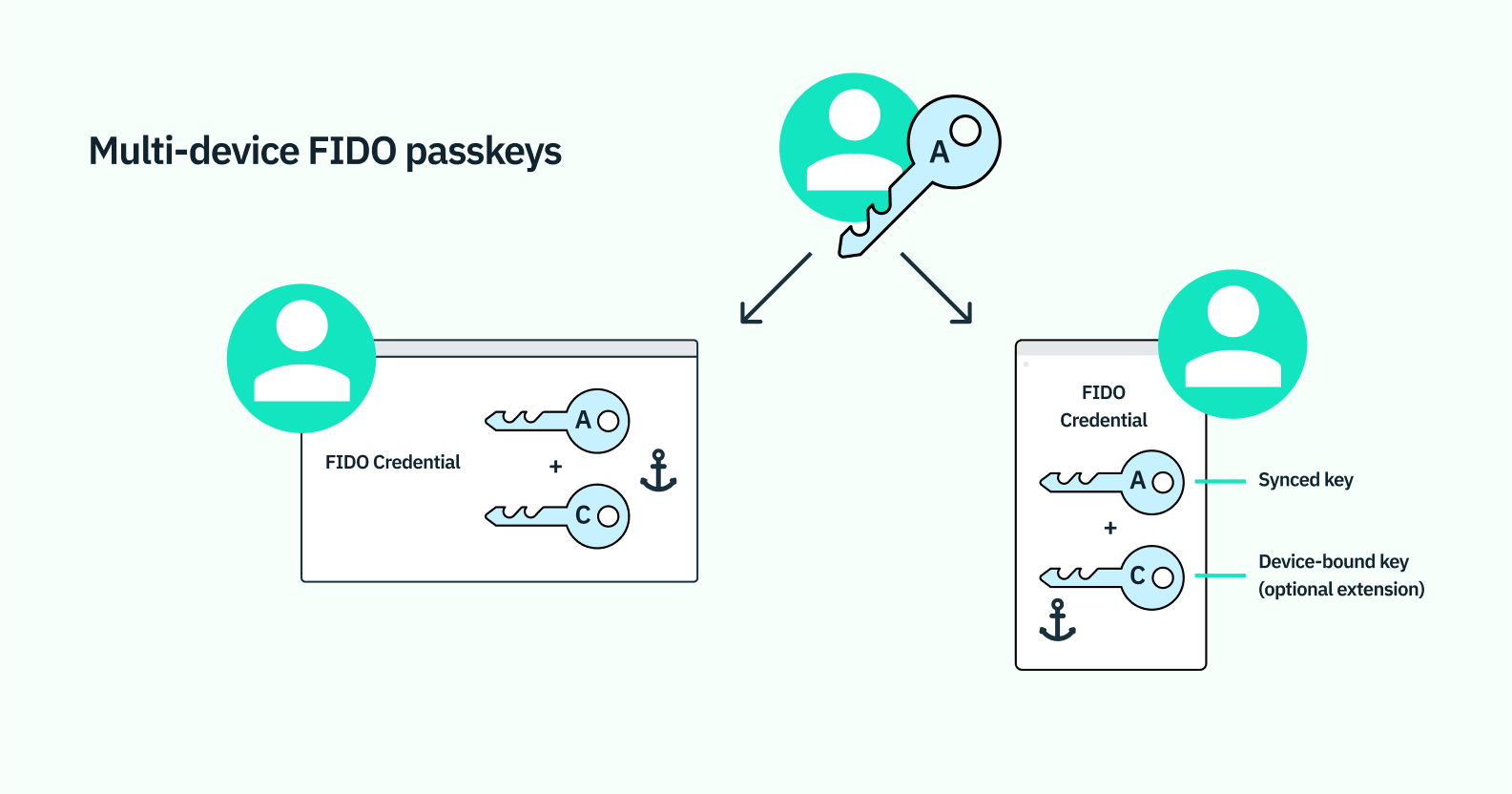
Passkeys are the most recent implementation and combine the power of in-device biometrics with the flexibility of something more like a password manager. Their power is that they leverage WebAuthn but are no longer device-limited. Whereas prior uses of WebAuthn have typically only allowed for device-bound public and private keys, multi-device passkeys allow for these keys to be synced across cloud accounts to enable use on different devices.
What’s more, passkeys also incorporate bluetooth and QR codes to enable login via biometric passkeys on different operating ecosystems. So hypothetically, users could use an iCloud passkey on their tablet to log into an app on their Android phone, and vice versa. While there are still some additional hurdles to be cleared on the road to widespread passkeys adoption, this latest breakthrough is the most promising of all of FIDO’s work to truly evangelize passwordless authentication methods on a massive scale.
Why Stytch joined FIDO
As a pro-passwordless platform from our inception, we’ve been impressed by the work FIDO has done to increase passwordless adoption. We’re particularly excited about everything they’ve done to make passkeys a reality, as it’s one of the new passwordless technologies we’re most excited about.
At the same time, we’re also excited to join FIDO because we think we bring a decidedly different approach to the alliance. Lots of FIDO members are passwordless only, and we consider ourselves an identity and access management platform that’s building the bridge to passwordless adoption. But we strongly believe that the bridge to passwordless is paved with, you guessed it – passwords.
Internet-based companies won’t pursue passwordless at the expense of customer comfort or experience – we shouldn’t ask them to take that kind of risk or leap. Instead, they need partners and bridge-builders to help them transition smoothly and profitably to a more future-forward user flow.
At Stytch, we’re trying to model that kind of partnership in a way that other FIDO members can follow, in a way that will make passwordless authentication feel more palatable and attainable, even for the most password-entrenched among us. We think we have a unique position to embrace the passwordless world through our pragmatic approach to meeting companies where they are and think joining the FIDO alliance will help us improve our ability to move companies into a passwordless future.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.