Back to blog
Do passkeys live up to the hype?
Auth & identity
Oct 27, 2022
Author: Gedney Barclay
The dream that propels most people working in identity and access management (IAM) is the search for a frictionless yet secure way for users to authenticate themselves online. Legacy forms of authentication like passwords are friction-heavy and contain major security holes. Passwords specifically create significant negative externalities on both businesses and consumers, ranging from account takeovers to lower conversion at sign-up and login. Given the significant UX and security issues that legacy authentication methods pose for both companies and their customers, it’s no surprise that many in the IAM space believe that passwordless authentication will play a key role in the future of identity and access management.
But passwordless authentication can mean many things — passwordless technologies include one-time passcodes (SMS/Email), email magic links, social logins (e.g. Google/Facebook/Apple/etc.), and biometrics like facial and fingerprint verification. To date, all of these authentication methods have gained considerable adoption, yet many apps continue to offer passwords as an authentication option to users. These technologies have reduced our reliance on passwords and many users prefer them, but they still haven’t managed to kill the password.
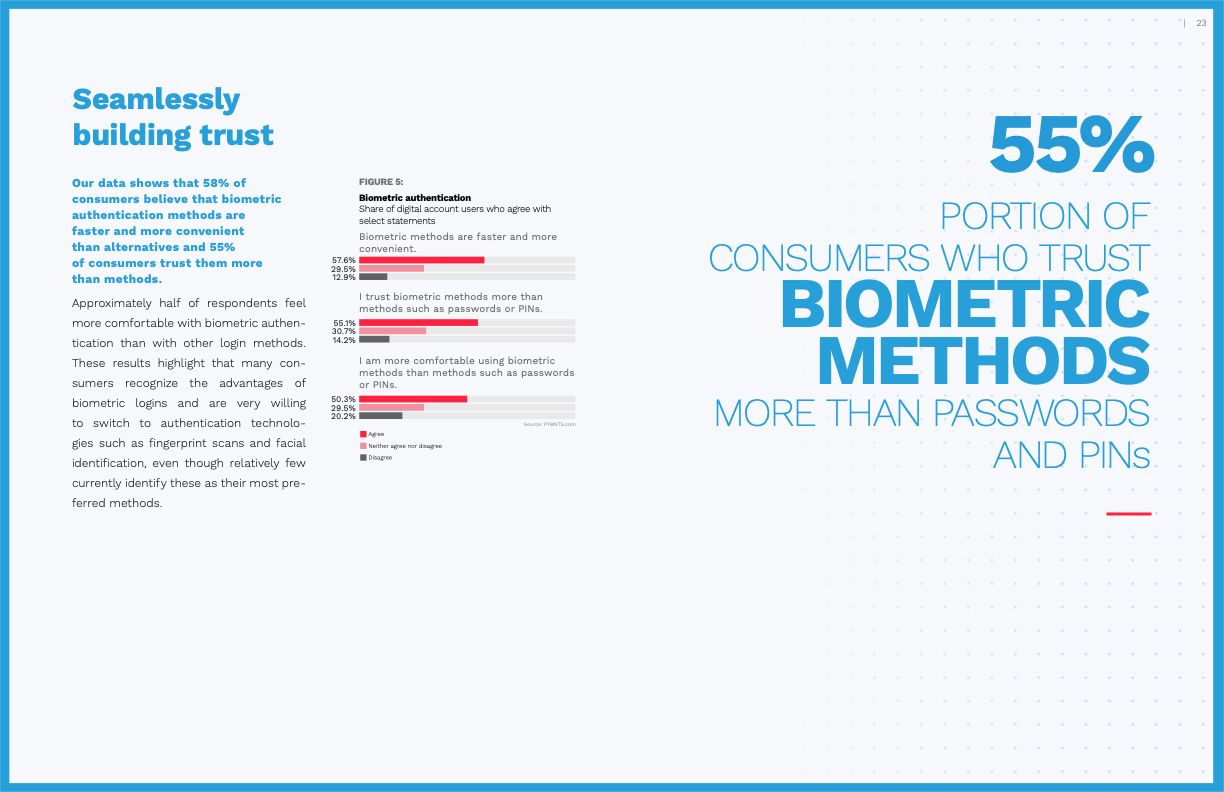
Of the above technologies, studies continue to find that biometrics are the most enticing to both consumers and businesses — they’re fast, simple, secure, and familiar given the reliance of Apple, Microsoft, and Android devices on biometric-based authentication. In a recent PYMNTS and Mitek study, 55% of consumers trust biometric authentication methods more than passwords and PINs (31% remain undecided and only 14% prefer traditional methods like passwords).
Users are highly supportive of biometric authentication, but it’s still not a ubiquitous experience. While many consumers use facial recognition on their mobile banking app or their fingerprint to log into their laptop, these biometric forms of authentication are still not supported by most applications. The technology exists and is familiar to users, so the question remains why it isn’t the primary option when we sign up for and log in to the hundreds of other online accounts that we manage. The answer has to do with some existing limitations to how biometric-based authentication works today.
Fortunately, solutions aimed at fixing those current shortcomings are on the horizon. In May 2022, the Fast ID Online Alliance (FIDO Alliance) announced a major development in passwordless technology that would make biometric authentication significantly better suited for consumer use cases: passkeys. Passkeys aren’t necessarily a new technology, but they solve some of the major UX obstacles with existing biometric authentication technology and have support from the major tech platforms (Apple, Google, Microsoft) to drive widespread biometric adoption. So, are passkeys worth the hype? And if so, what might the path to passkey adoption look like for business and consumers?
Working in this space requires a blend of eternal optimism and severe skepticism. We know the future holds better authentication experiences, but we’ve also been repeatedly subjected to hyped authentication technologies that ultimately failed to move us beyond passwords. Fortunately, passkeys appear to be the real deal. It will take time for businesses and consumers to adopt them, but the architecture provides a significant leap forward in the feasibility of wide-scale biometric authentication adoption.
Current gaps in WebAuthn and the case for passkeys
Passkeys are a new evolution built upon an existing passwordless technology called Web Authentication API or “WebAuthn.” To understand the promise of passkeys, it’s important to understand where the initial capabilities of WebAuthn technology have fallen short of consumer expectations. In March 2019, WebAuthn was declared a W3C web standard. At the time, WebAuthn received its own fair share of hype and was a critical stepping stone on the path to passkeys. It promised to smooth the user experience of biometrics by making user enrollment more intuitive and supporting cross-device and cross-platform biometrics.
However, +3 years later, it’s fair to say that WebAuthn’s adoption has been minimal, particularly in B2C use cases where there’s a higher emphasis on user experience. A major reason for WebAuthn’s limited adoption is that the technology has been sidelined into a secondary authentication method rather than being offered as a true primary method to users signing up for or logging into an account. There have been two main problems with WebAuthn as a primary authentication factor:
- UX: UX experience of WebAuthn as a primary factor - either for "passwordless" or "usernameless" scenarios - has been pretty rough. The WebAuthn W3C group has put together a document that goes into far more detail. One of the items out of that discussion was a standards change that was merged in a few months ago. Now it's up to browser vendors to implement that change over the coming months and years.
- Lock-out risk: The second problem with WebAuthn is that device-based authentication has been historically risky for consumer users long-term. It's unreasonable to expect an individual to have access to their phone, YubiKey, or laptop over a period of years. In the B2B space, this isn't as big of a deal. Getting an IT admin that works for your company to reset your access and issue a new credential is not a complex problem. However, this is a major hurdle in the B2C space. Devices get lost or stolen, and then the service operator needs to build out an alternative recovery method that needs to be as secure as WebAuthn (ideally, without infringing on the user's privacy, as regulated by Know Your Customer (KYC) mandates).
To make this tangible, imagine you’re a user signing up for an account with HomeDepot in order to buy paint:
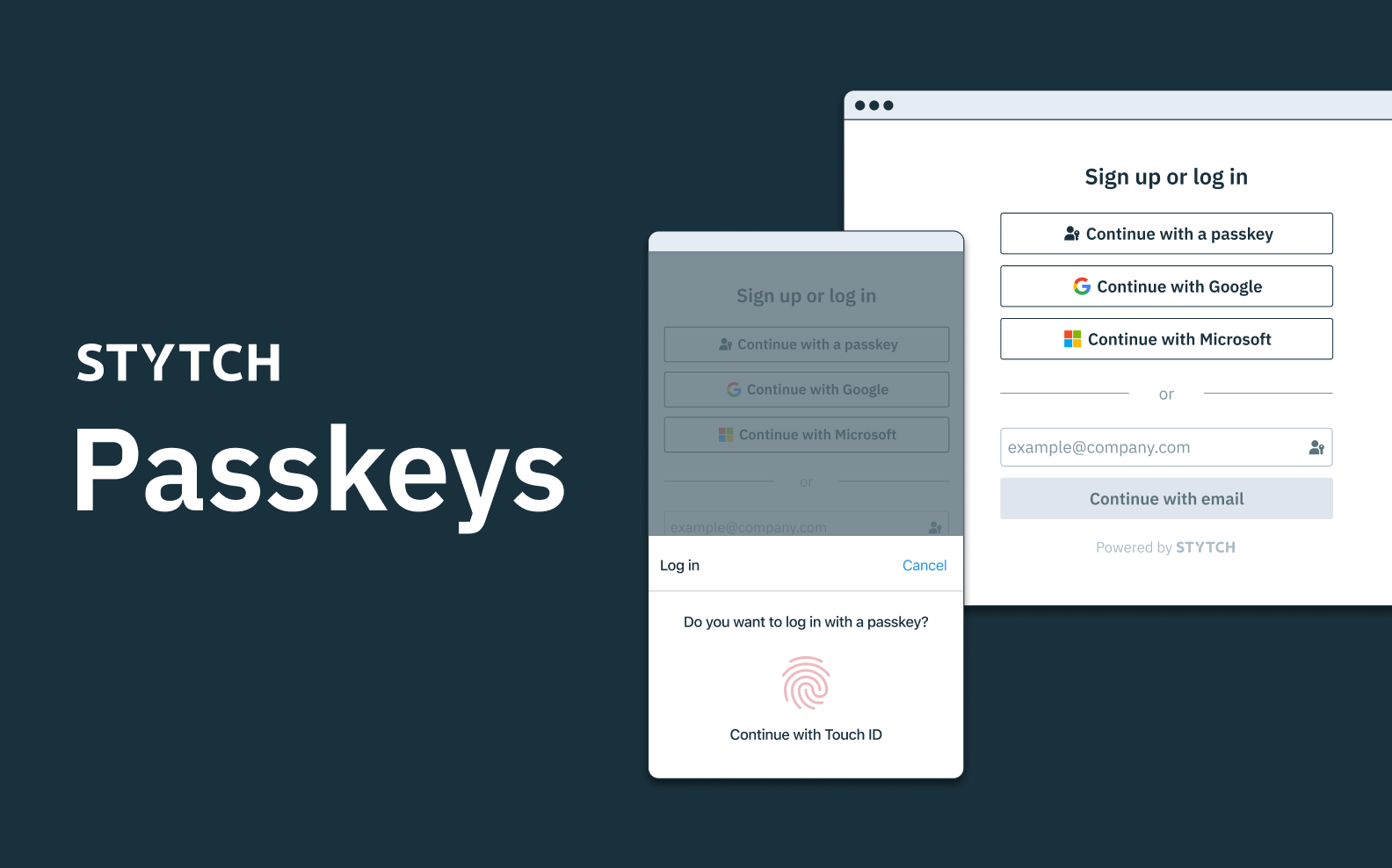
- You start your search for paint on your mobile device and find a few colors you’re excited about. You create a HomeDepot account in order to complete the order. You see a FaceID icon and think “Great! No password needed — I can just use a biometric to sign up.
- A day later, you see the shipping confirmation while checking email on your laptop, and you realize you’re out of paint brushes. You go to HomeDepot.com to order a few brushes as well. When it asks you to log in, you click on the same biometric icon you saw in the mobile app
- However, laptops do not support FaceID, so HomeDepot asks you to go through the TouchID flow on your Mac. You enroll your fingerprint and you receive an error telling you an account doesn’t exist.
- You know that’s not right, but you’re not sure what’s gone wrong, and you’re in a hurry. You decide to create a password, enter all of the same information you provided yesterday (address, credit card info, etc.) and make the purchase with this same account.
You’ve now experienced the biggest shortcoming with WebAuthn today — it doesn’t handle cross-device or cross-platform authentication well. Instead of it saving you time, it actually led to confusion and required you to duplicate work while also creating multiple accounts for HomeDepot to manage on their side. In short, WebAuthn isn’t a great replacement for passwords for most applications today, unless their users are tech savvy and OK with the lock-out risk.
Luckily, passkeys build on over a decade of learnings like these to overcome these user challenges and become a major contender for preferred primary authentication factor. By enabling biometric authentication to work across all major devices and browsers, passkeys are likely to be a game changer for B2C WebAuthn adoption.
Want unphishable auth for your app? Try Passkeys from Stytch.
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
What are passkeys and how do they work?
Though passkeys are built upon WebAuthn, they improve on the older auth method in a few key ways. While WebAuthn pioneered the concept of a single-device passkey (i.e. a single hardware key or a biometric validation tied to your mobile device or laptop), “passkeys” as we’re discussing here refer to multi-device passkeys and introduce a few major UX and developer improvements:
- They are a drop-in replacement for passwords.
- They are cross-device, cross-platform, and cross-ecosystem.
- Enrollment and login credentials with a passkey leverages UX patterns made familiar by password managers.
- For higher security contexts, passkeys can discern between existing and new devices attempting to access an account.
Definitionally, there are a few different ways to describe passkeys depending on the audience you’re talking to:
- For consumers, passkeys provide a simple and secure way to sign up and log in to sites and apps without the need for a password.
- For the tech savvy, a passkey is a phishing-resistant, password replacement FIDO credential, usable across all of your devices.
- For the tech-and-authentication savvy, a passkey is a FIDO2 discoverable credential which requires user verification and is backed up to survive device loss.
If you’ve ever used a password manager like LastPass or 1Password, you’ll understand the value proposition of passkeys. Password managers provide a much better user experience than fumbling around to remember a unique password for each different online account. Passkeys work similar to this, but they don’t require consumers to pay to use them or remember a master password.
Instead, passkeys work by storing a key pair consisting of a public and private key in a user's primary device account (e.g. your iCloud account on your iPhone or Mac or your Google account on your Android or Chrome book). This key pair can then be used to sign up or sign in to applications without creating or remembering an additional password. The public key cryptography underpinning this technology isn’t new, but the way that multi-device passkeys leverage your logged in account across devices (e.g. iCloud, Google, Microsoft) to perform these cryptographic checks is novel.
Whereas prior uses of public key cryptography have typically only allowed for device-bound keys, multi-device passkeys allow for these keys to be synced across cloud accounts to enable use on different devices. What’s more, passkeys also incorporate bluetooth and QR codes to enable login via biometric passkeys on different operating ecosystems. So hypothetically, users could use an iCloud passkey on their tablet to log into an app on their Android phone, and vice versa.
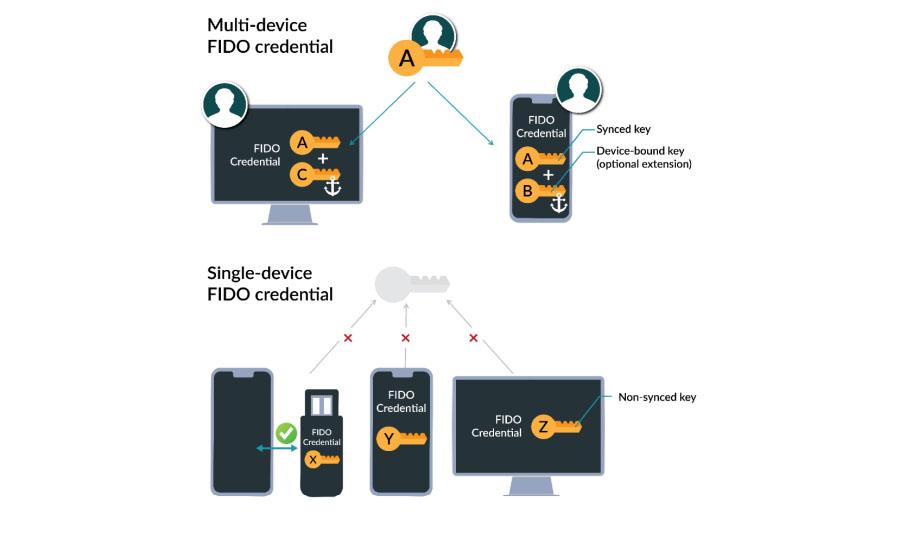
If we return to our Home Depot example, we can see how multi-device passkeys with biometrics make the user’s experience much more streamlined than WebAuthn:
- When a user is checking out on HomeDepot’s mobile app, they can choose to create an account in one click with their face ID on iOS or Android. At this point, their device generates a passkey and stores it on their device’s account.
- If that user needs to access the account again from their laptop, their credential will already be synced with their iCloud or Google account. All they need to do is use whatever biometric credential their laptop uses, and the same passkey from their phone will be used to log them in on their laptop.
- The user now has a fully biometric-only account that’s easy to navigate across different devices.
What will the path to passkey adoption look like for businesses and consumers?
In our opinion, passkeys offer the best chance to move us beyond passwords and into a more simple and secure biometric-based future. They’re fast, secure, familiar, and privacy-preserving (no biometric data is ever actually transmitted to the application verifying the user). While we believe the adoption curve for passkeys will be significantly steeper than WebAuthn, it won’t happen overnight. There are still some headwinds for universal passkey adoption, including:
- Device and operating system support: While Apple, Microsoft, and Android have announced support for the latest versions of their respective operating systems, it will likely take years to get all users to update to the latest OS.
- Application uptake: The UX and security benefits of integrating passkey support are clear, but it still requires an application to make the updates to integrate it into their sign-up and login forms. This also requires applications to think about how it changes their user model and any relevant account recovery flows to ensure their passkey rollout is frictionless.
- User uptake: While passkeys fix the remaining shortcomings in WebAuthn, users will continue to value multiple options when it comes to choosing an authentication method, and some will be hesitant to adopt a new biometric method. In the same PYMNTS and Mitek study cited earlier, researchers found that 73% of consumers reported being able to choose their preferred authentication method in an application increases their trust in the app. Moreover, 14% of users still explicitly prefer legacy authentication methods like passwords and PINs.
While it will take time and effort to weather these headwinds, passkeys present a major leap forward for passwordless technologies. Companies should incorporate passkeys into their identity and access management strategies and figure out where it fits on their roadmap. In the long-term, their customers and their IT/security teams will be grateful. At Stytch, we’re building a modern identity and access management platform, which includes support for passkeys. If you’re considering adopting passkeys, we’d love to share our learnings and help you create a strategy to roll out passkey support — get in touch to get started with Stytch today.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.