Back to blog
Keycloak alternatives for enterprise authentication and identity management
Auth & identity
Jan 26, 2024
Author: Alex Lawrence

Open-source identity and access management (IAM) systems are designed to securely authenticate and authorize individuals, providing them with the appropriate level of access to resources within an organization. Keycloak is one of the most reputable open-source IAMs, with comprehensive features including single sign on (SSO), catering to the diverse needs of modern applications across web apps, mobile apps, and even SaaS apps.
Yet, despite its open-source nature and single sign-on advantages, Keycloak isn’t perfect for every developer and business use case. For instance, it requires significant expertise and effort to set up and maintain, making it less user-friendly for smaller organizations with limited resources.
This limitation has paved the way for several “closed-source” alternatives that offer a more streamlined, low-lift approach to IAM. In this article, we’ll briefly overview the benefits and challenges of open-source auth solutions like Keycloak, then dive into the world of closed-source alternatives offering more user-friendliness, support, and maintenance features.
Keycloak and the pros and cons of open-source IAM
Keycloak is an open-source identity and access management solution developed by Red Hat. It primarily focuses on providing robust, customizable, and scalable user authentication and authorization. Keycloak not only supports standard protocols like OpenID Connect, OAuth 2.0, and SAML but also enables businesses to manage their users’ access to different resources, applications, and services.
Additional benefits of Keycloak include:
- Single sign-on: Users can securely access multiple applications with a single set of login credentials. Single sign on eliminates the need to remember multiple passwords, making it convenient for users and reducing the risk of password-related security breaches.
- Identity brokering (social identity providers): Keycloak allows users to log in using their existing social media accounts like Google, Facebook, or GitHub. This feature simplifies the registration and login process for users, reducing user friction and increasing convenience.
- User federation: Keycloak can integrate with various user stores and directory services, making it easier to control access and manage users across different systems. Additionally, Keycloak’s support for various programming languages and frameworks makes it easy to integrate with different technology stacks.
Despite its capabilities in managing identities and user provisioning, Keycloak’s complexity, heavyweight architecture, and not-so-user-friendly API have been points of contention for developers leading some to seek alternatives. Moreover, recent security vulnerabilities have exposed some cracks beneath the surface, underscoring the need for more rigorous and time-consuming maintenance, especially in a self-hosted setup. Let’s drill into these a bit further.
Complexity and expertise
Open-source identity solutions like Keycloak offer extensive flexibility and customization, essential for modern applications and web apps. However, this often leads to complexity, presenting a challenge for many smaller businesses lacking an IT team specializing in identity and access management (IAM). Implementing and maintaining these solutions demands a deep technical understanding as well as continuous upkeep outside the realm of smaller team capabilities.
Self-hosting
Keycloak’s open-source nature necessitates self-hosting, meaning businesses are responsible for managing servers, databases, and network infrastructure for their access management system. In addition to continuous system operation and regular backups, businesses must also scale their internal resources to meet their growth needs. For companies with restricted IT resources, this can be both time-consuming, expensive, or flat-out infeasible.
Security vulnerabilities
Self-hosting also requires vigilant security management, and without the appropriate skill sets in this area, organizations can become vulnerable to breaches. With Keycloak, addressing security vulnerabilities relies heavily on the user community. When a vulnerability is identified, it’s critical for organizations to promptly update or patch their systems themselves (contrast this with closed-source solutions where security updates and fixes are typically managed by the provider).
Recently, a substantial security vulnerability was discovered in Keycloak that allowed a malicious actor to create nefarious Keycloak authorization request URLs to circumvent the redirect URI validation. Depending on the client configuration, an attacker could exploit this vulnerability to steal a victim’s authorization code or access token. This vulnerability highlighted one of the notable drawbacks of Keycloak – the burden of security management is often shouldered by the user minus a dedicated security team.
Aside: Stytch makes it easy for B2B SaaS businesses to build secure Enterprise-grade multi-tenant SSO, with support for OIDC and SAML. Plus, Stytch offers responsive support, and a hosted solution that’s easy to maintain as your company scales, making it a great alternative to Keycloak. But there are lots of options…more on that below.
Closed-source alternatives
Closed-source identity and access management (IAM) solutions represent a model where the source code is proprietary, held and maintained by the company that develops it. Unlike open-source options, these solutions do not provide the end-user with the ability to view, modify, or distribute the original code. In return, businesses and users get the comfort of ‘outsourcing’ the most complex aspects of IAM.
Advantages of closed-source IAM
Closed-source IAM solutions bring their own unique set of advantages. At a high level, these benefits often involve:
- Seamless updates: With a dedicated team of developers, closed-source IAM solutions often provide timely updates to fix bugs and improve functionality. In contrast, open-source solutions may rely on community support for updates, which can sometimes lead to delays in addressing issues.
- Comprehensive customer support: Closed-source identity access management providers often offer robust customer support, helping businesses navigate any challenges quickly and effectively. This can be especially useful for troubleshooting technical issues or receiving guidance on utilizing the features of the solution effectively.
- Hosted/cloud support: All the infrastructure is taken care of in the cloud and will auto-scale as your business / application grows. This eliminates the need for businesses to invest in their own infrastructure and IT resources, reducing overall costs. Additionally, hosted/cloud support allows for easier access to the solution from anywhere with an internet connection.
Early closed-source IAM systems were often rigid and focused solely on securing access, but modern closed-source IAM solutions are designed with flexibility and integration in mind. They have adapted to include features like single sign-on (SSO), multi-factor authentication (MFA), and federated identity management, catering to a wide range of business requirements and user scenarios.
Developer experience
Closed-source IAM solutions provide a significant boost to the developer experience by offering customized authentication systems tailored to specific needs. They recognize the diverse requirements across various development environments, be it mobile, frontend, or backend. With their user-centric API designs, these solutions offer intuitive and easily integrable APIs, ensuring seamless implementation of authentication mechanisms. This attention to API design reduces the complexity and time involved in integrating IAM functionalities into various applications.
Furthermore, these IAM solutions support multiple programming languages and offer comprehensive SDKs, catering to a wide range of development platforms. This versatility allows developers to work in their preferred language and environment, enhancing productivity and ease of use. Whether it’s handling complex security protocols for enterprise applications or integrating social login features for mobile apps, closed-source IAM providers equip developers with the tools and support needed to create secure, efficient, and user-friendly authentication experiences.
Greater reliability and security
A closed-source identity access management solution is often seen as more reliable and secure – and for good reason. Closed-source IAM solutions are often built and maintained by teams with a dedicated focus on security. This means that additional measures, such as regular security audits and vulnerability testing, might be in place to ensure the system’s integrity. The controlled development environment ensures that any changes or updates to the system undergo rigorous testing before release. This contrasts with open-source solutions, where updates can be contributed by a broad community, potentially introducing instability or security risks.
Advanced authentication methods that uplevel security practices further add to the appeal of closed-source solutions. They include biometric authentication, risk-based (or step-up) authentication, and adaptive authentication techniques that verify user identity with factors such as location, device status, and behavior. These methods not only enhance security but also improve the user experience by offering convenient yet secure access to applications and services – increasingly table stakes in today’s CX-driven world.
Adherence to compliance and industry standards
Closed-source solutions, given their controlled nature, are naturally a good fit within the guardrails of industry compliance standards and therefore tend to appeal to businesses operating in particularly stringent industries. Many closed-source IAM providers design their solutions to comply with industry standards and regulations. This is crucial for sectors like finance, healthcare, or government, where compliance with data protection and privacy regulations is non-negotiable. Closed-source IAM solutions ensure that their products adhere to these standards, instilling peace of mind for businesses in these industries.
Future proof by design
So as not to be outsmarted by the tricksters and scammers lurking within application ecosystems, closed-source IAM providers invest heavily in research and development, ensuring their solutions are equipped to handle emerging security threats and evolving business needs. This forward-looking approach means that businesses using closed-source IAM can be more confident in their ability to adapt to future challenges in the digital landscape and prepared to tackle threats head-on. With their regular updates and support, closed-source IAM solutions provide a long-term solution for managing identity and access within an organization and a notable stability in weathering change.
Finding the right closed-source access management system
With numerous closed-source IAM providers in the market, it can be challenging to find the right one for your organization. When evaluating different solutions, consider factors like cost, functionality, scalability, and support services, as well as how the solution integrates with existing systems and whether it aligns with your organization’s security requirements. The below is an overview of some top choices with pros and cons to help guide you.
Auth0
Auth0 has emerged as an adaptable identity provider, catering to a diverse array of applications, including web apps, mobile platforms, and federated systems. Their solution provides a flexible and scalable approach to managing identity and access, making it a potentially good choice for businesses of various sizes. Auth0’s extensive support for different protocols and integrations with popular platforms like AWS, Azure, Google Cloud, and Salesforce makes it a versatile option for organizations operating in various sectors.
Pros:
- Wide application support: Auth0 excels in its support for various applications, from web-based to mobile environments. It also offers integration with popular identity protocols like SAML, OAuth, and OpenID Connect.
- Scalability: With an extensive set of features and integrations, Auth0 can handle the needs of growing organizations without compromising on performance. It has various pricing plans to suit the needs of businesses at different stages of growth.
- Developer resources: Auth0’s extensive documentation makes it easy for developers to find resources on the technology they’re looking for. It includes SDKs for various programming languages, making it accessible for developers of all backgrounds.
Cons:
- User-first data model: Auth0’s data model is user-first by design, meaning individual user records are simply associated with organizations. This multi-tenant architecture is limiting and inflexible as it makes it difficult to deduplicate user accounts safely, enforce org-specific auth requirements, and selectively authenticate into one organization and not another.
- Cost: While Auth0 has a free trial and flexible pricing plans, its services may be too expensive for smaller businesses or startups. It may require additional costs for certain features and integrations.
- Complexity: Auth0’s extensive set of features and customization options can be overwhelming for organizations with limited IT resources or technical expertise.
- Security challenges: Unfortunately, in the past few months, Auth0’s parent company Okta has had some heavily publicized security breaches, casting doubt on the solutions overall reliability.
Amazon/AWS Cognito
Part of the Amazon Web Services suite, Amazon & AWS’ Cognito offers a convenient identity management and access control solution, especially for those already within the AWS ecosystem. Overall, AWS Cognito is a strong choice for businesses already utilizing AWS services and looking for a comprehensive IAM solution with strong security features and cost-effectiveness.
Pros:
- Seamless AWS integration: Offers tight integration with other AWS services, ensuring a smooth operation within the AWS environment.
- Scalable and flexible: Provides scalability and flexibility to support a wide range of business needs, from small startups to large enterprises.
- Simple setup process: Easy-to-follow setup process makes it accessible for users with varying levels of technical expertise.
- User-friendly interface: Intuitive interface makes managing identities and access control simple and straightforward.
- Cost-efficient: Offers a pay-per-use pricing model, making it cost-efficient for businesses of any size.
Cons:
- Limited features & customization: May not have as many features compared to other IAM solutions in the market. Some advanced customization options may not be available for certain use cases.
- Learning curve: Users may need some time to familiarize themselves with AWS Cognito’s specific terminology and capabilities.
- Dependency on AWS ecosystem: Being tightly integrated with AWS means it may not be the best option for businesses using a mix of different cloud services.
- Security concerns: As with any cloud-based solution, there is always a risk of security breaches and vulnerabilities.
Google Firebase
Google Firebase is a popular choice among mobile app developers, offering a suite of tools that include robust user authentication capabilities. Firebase not only provides user authentication capabilities but also offers a variety of tools that simplify the development process, enhancing efficiency and productivity. Developers are drawn to Firebase for its real-time database, analytics, crash reporting, and plethora of other features, all wrapped up in to one intuitive package.
Pros:
- Easy integration: Seamless integration with other Google services like Analytics and Cloud Functions.
- Real-time database: Firebase’s real-time database allows for efficient data syncing across devices.
- Scalability: Firebase can handle large amounts of data and traffic, making it a great choice for apps with high user engagement.
- Cloud messaging: Firebase’s Cloud Messaging service allows developers to send notifications and messages to users across multiple platforms.
- App development tools: Firebase provides a plethora of tools for app development, including machine learning, cloud storage, and A/B testing.
- Cost-efficient: Firebase’s free tier is quite generous, and the pay-as-you-go pricing model allows for cost control based on usage.
Cons:
- Limited control over server-side code: Firebase is a backend-as-a-service (BaaS), so developers have limited control over server-side code.
- Limited query capabilities: Firebase’s database querying capabilities are limited compared to traditional databases, which may be a drawback for more complex apps.
- Data migration challenges: Transitioning to or from Firebase can be a daunting task due to the unique structure of its NoSQL database. This can pose challenges in data migration and may require substantial effort and resources.
- Pricing model: While Firebase’s free tier is generous, the cost can quickly escalate once the application starts scaling or requires more advanced features. This could potentially make Firebase an expensive choice for startups or small businesses on a tight budget.
Stytch: a growing force in CIAM and IAM
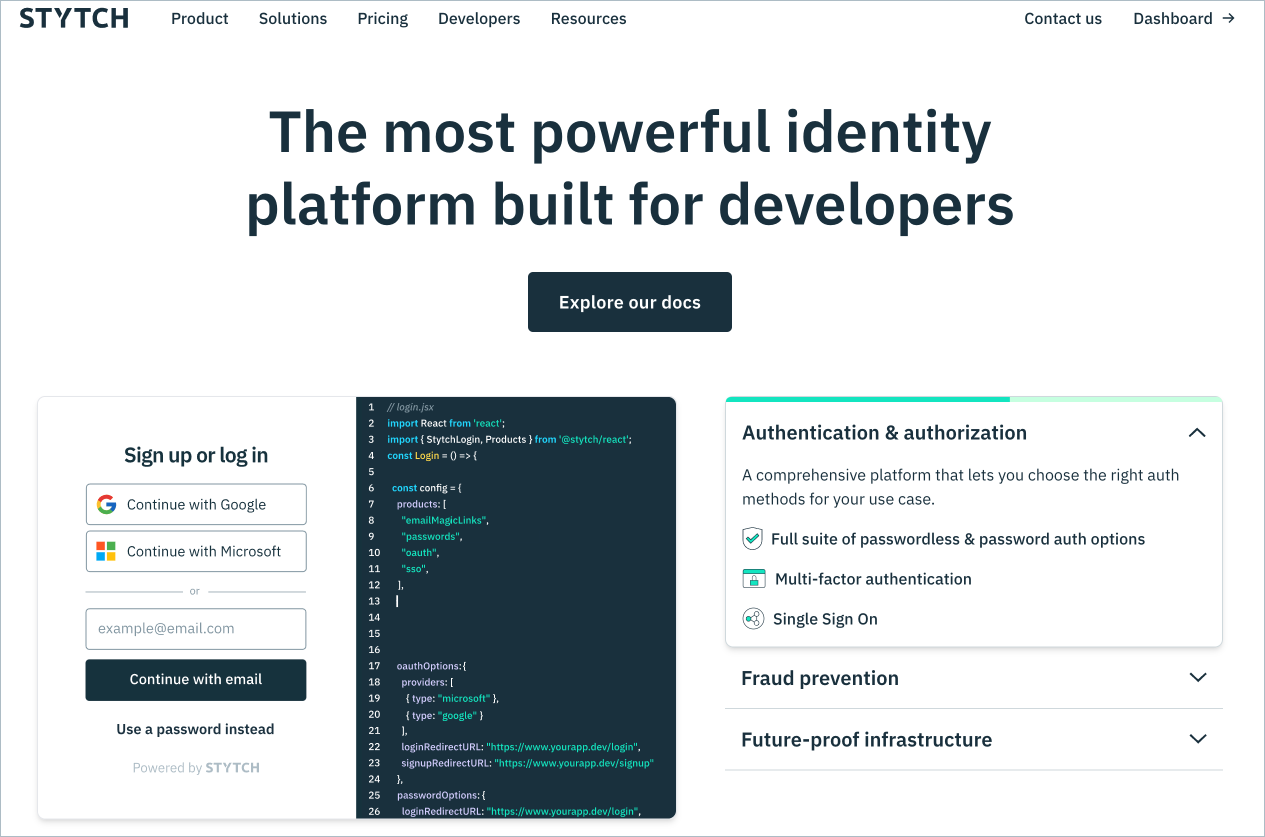
Stytch has a distinctively modern and flexible approach to identity management, providing a seamless user experience with features like passwordless logins and two-factor authentication across multiple devices. Its focus on simplifying user access while ensuring security makes it one of the strongest contenders in the IAM landscape.
Stytch’s highly intuitive user interface makes it easier for businesses to implement and manage identity solutions. Additionally, its customer support is noteworthy, providing timely assistance, which is a significant advantage over open-source options.
Why Stytch stands out
Stytch offers distinct B2B and B2C authentication solutions that cater to the unique requirements of each business & application model. Within the B2B SaaS authentication space, Stych stands out for its unique data model that, unlike open-source models such as Keycloak, focuses on organizations rather than individual users.
This organization-first approach streamlines authentication management, offering a more intuitive system for B2B SaaS applications. It enhances flexibility and customization with per-organization auth settings, allowing seamless integration with various single sign-on (SSO) providers, including OIDC and SAML, and identity management controls like RBAC and JIT Provisioning. This results in a more efficient, business-aligned authentication process, significantly improving the developer experience in multi-tenant environments.
Stytch is the only auth provider with a true API-first architecture that enables you to build the exact end-to-end auth flow you need, whatever your stack. Stytch supports multiple standalone and modular options for how to integrate authentication — directly with Stytch’s APIs, leveraging Stytch’s frontend, backend, and mobile SDKs, or using out-of-the-box pre-built UI components. With a comprehensive set of powerful auth and identity primitives, Stytch offers the most composable toolset for developers to build enterprise auth systems for their SaaS applications.
Stytch also offers native fraud detection tools like Device Fingerprinting, which identifies unique characteristics of a user’s device, such as the operating system, browser version, screen resolution, and even unique identifiers like IP addresses, helping safeguard against different types of attacks and potential breaches. By combining these elements into an identifier, there’s enough entropy to ensure that the identifier is unique to each device. The Device Fingerprinting Dashboard allows you to deep dive into individual fingerprints to understand the various devices that are querying your service.
To learn more about how these or other Stytch fraud prevention solutions work, reach out to an auth expert to start a conversation or get started on our platform for free today.
Build auth with StytchRead the Docs
Build auth with Stytch
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.