Back to blog
What is whaling phishing and how to prevent whaling attacks
Auth & identity
Jul 3, 2024
Author: Alex Lawrence

While many fraud attempts are indiscriminate in nature (think brute force attacks like password spraying), fraudsters can also be more discerning in an attempt to reap bigger rewards. In the case of whaling phishing, their goal is to stick it to the person at the top.
Whaling phishing is a type of cyberattack that targets high-level executives like CEOs and CFOs. The primary objective of a whaling phishing attack is to steal sensitive information or execute financial transfers. Unlike regular phishing, it uses personalized tactics to trick these individuals into revealing this information or making unauthorized transactions.
In this article, we’ll explain what whaling phishing is in more detail, how it works, and how you can protect your organization from these sophisticated, exec-level attacks.
Whaling phishing attacks explained
Unlike a general spear phishing attack which targets a specific person, group, or organization, whaling phishing attacks are a type of spear phishing attack that’s even more specific to who they target: high-level executives such as CEOs and CFOs. The goal of a whaling attack is to trick said power players into believing the communication is legitimate, often through means like email spoofing and content manipulation.
How do whaling phishing attacks work?
Whaling phishing attacks are meticulously crafted, involving cybercriminals pretending to be trusted contacts to manipulate these executives into revealing confidential information or authorizing financial transactions. In a whale phishing attack, the attackers use sophisticated social engineering tactics, email spoofing, content spoofing, and even voice spoofing to create emails, texts or calls that seem legitimate, often leading to phishing attempts. These attempts can include:
- Impersonation of a trusted contact through the sharing of personal details or references to ongoing projects to enhance their credibility.
- Fake urgent payment requests requiring immediate attention.
- Less commonly, links to spoofed websites that look real designed to collect sensitive information. These are more prevalent in general spear phishing due to the flags they raise at the executive level.
Whaling phishing is more of a theatrical art than science: Like an actor studying his character, a cybercriminal will invest considerable time and effort in researching their target to understand their behavior and online presence. They gather information from social media, corporate websites, and press releases to understand the target’s role, responsibilities and professional history. This extensive research enables them to craft convincing messages that appear to come from trusted sources within the organization.
Who's at risk?
Unlike broad-spectrum phishing attacks, whaling targets specific individuals with significant access to valuable data and resources – the very top of the pecking order at any given organization. In addition to C-suite executives, senior managers, finance and IT personnel, as well as HR staff are common targets of whaling attacks if the access to sensitive information warrants the attempt. These individuals have elevated privileges to access critical business systems, making them lucrative targets for attackers seeking financial gain, data theft, or other malicious purposes.
Recognizing a whaling phishing attack
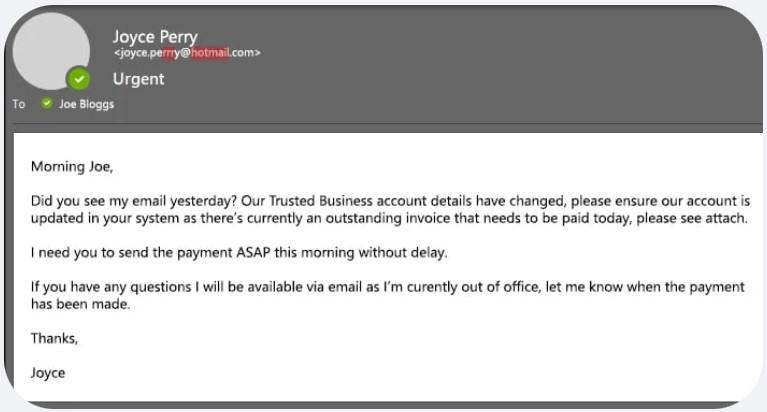
One of the most common pathways to a successful whaling attack is via business email compromise of sensitive data to trick whaling attack victims. As with phishing and spear phishing attacks, recognizing whaling emails can be challenging due to their sophisticated nature, but certain red flags can help identify them. These emails often reference specific events, projects, or personal details to make them appear legitimate. They might come from a sender address that is slightly altered, such as changing a single letter in the domain name, making it look almost identical to the legitimate address.
The path to business email compromise is often achieved through alarmist and urgent language, compelling the target to take immediate action, such as transferring funds or providing confidential information. An executive might see terms like “Request,” “Follow Up,” or “Fwd:” to create a sense of familiarity and urgency. Subtle errors like slight misspellings or odd phrasing can also be indicators of a whaling email.
Differences between whaling and other phishing attacks
Unlike some spear phishing attacks, whaling attacks usually avoid using malicious URLs or attachments, making them harder to detect compared to standard phishing attacks. The lack of obvious red flags like malicious links or attachments allows whaling emails to bypass traditional security measures, making them a more effective and dangerous form of social engineering attack in many cases.
Because whaling attacks specifically target high-profile individuals such as CEOs, CFOs, and other executives within an organization, they are highly personalized and crafted with detailed information about the target, with subtle details often gathered from social media profiles, company websites, and other publicly available sources. This level of 'personalization' distinct from more broad-based phishing attacks increases the credibility of the attacker and the likelihood of the target (generally a highly experienced and competent individual) falling for the scam.
Want MFA protection for your apps? Switch to Stytch.
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Consequences of whaling phishing attacks
The consequences of whaling phishing attacks can be severe and far-reaching. Financial loss is one of the most immediate and tangible impacts with large sums of money at stake. In addition to financial losses, whaling attacks can lead to data theft, severely compromising an organization’s data security and putting sensitive information at risk.
Operational disruption is another significant consequence as these attacks can impact the continuity of business operations, causing substantial downtime. The ensuing ripple effects can lead to loss of customer trust and potential legal liabilities.
Examples of successful whaling attacks
Over the past decade, several high-profile companies have fallen victim to successful whaling attacks, resulting in substantial financial and data losses. Here are a few noteworthy examples:
- In 2016, FACC’s CEO, Walter Stephan, was deceived into wiring $56 million to fraudsters through a sophisticated whaling attack.
- Similarly, in 2016, Belgian bank Crelan suffered a $75 million loss after cybercriminals targeted its CEO.
- Snapchat experienced a whaling attack in 2016 from a high-level employee disclosing employee payroll information due to a CEO fraud email.
It's important to note that in today's multi-device, AI-enhanced digital landscape, fraudsters don't rely solely on one method such as email and are increasingly deploying newer, more technologically savvy methods. A prime example of this occurred in 2019 when a UK energy company’s CEO was tricked into transferring $243,000 by a deepfake call mimicking his boss’s voice. And that was 2019 - imagine how easy it is now for fraudsters to utilize free or publicly available AI tools to conduct deepfake whaling attacks.
Rising sophistication in all forms of fraud must beget evermore savvy authentication solutions. As we move deeper into an AI-driven future, organizations must prepare for whaling attacks hiding in new digital disguises we can’t yet predict.
How to prevent whaling phishing attacks
With the knowledge that fraudsters will continuously evolve their methods, successfully preventing whaling phishing attacks requires, first and foremost, an executive team in the C-suite that is educated and aware of the current threats at play. Combining this awareness with strong anti-fraud and authentication measures for the executive team’s inner circle and most frequent collaborators can pack a powerful one-two punch against whaling phishing.
At a base level, a strong authentication and anti-fraud posture should include:
- Implementing authentication methods like multi-factor authentication (MFA), and more unique authentication methods (like passkeys or TOTPs) to add an extra layer of security.
- Enforcing strict password policies to ensure strong and unique passwords, or better yet going passwordless!
- In European setting, using Strong Customer Authentication (SCA) to further protect sensitive information in financial transactions is advised.
- Staying current with software and hardware updates to address security gaps.
- Regularly applying security patches to prevent unauthorized access.
Often, working with a 3rd-party provider that natively specializes in the above solutions is the easiest, most resource-efficient path with the lowest risk to business continuity.
Stytch fraud prevention solutions
Stytch offers a range of fraud and risk prevention tools designed to protect companies against various attacks, including whaling phishing, with strong authentication that encompasses an executive’s closest contacts and all employees below them. Two of these solutions, Device Fingerprinting and multi-factor authentication, can help enhance your organization’s overall security posture and earn customer trust.
Multi-factor authentication
As hackers develop more sophisticated social engineering techniques, phishing-resistant MFA in particular is becoming a crucial investment. Stytch’s ‘unphishable’ multi-factor authentication enhances protection against phishing, spear phishing and whaling phishing by requiring users (including those adjacent to executives) to verify their identity using multiple elements. This phishing-resistant MFA is built upon reliable WebAuthn measures like device-based biometrics and hardware keys.
Device Fingerprinting
Stytch Device Fingerprinting (DFP) creates unique identifiers for each user’s device, improving security and reducing whaling phishing attempts by distinguishing between legitimate users and potential threats. This technology aggregates various attributes such as: browser type, operating system, IP address, and other device-specific details to detect and block fraudulent activity. If a user posing as a company VIP is coming in with any suspicious device or browser characteristics, you can block them or force them to complete additional challenges, making it harder to spoof.
DFP integrates directly into your current setup, providing an additional security layer that is tamper-resistant to reverse engineering and spoofing attempts. By utilizing both industry-standard and proprietary signals, DFP ensures reliable identification across various scenarios, including incognito browsing and VPN usage.
Interested in learning more? Get in touch with an expert to see how Stytch fraud prevention solutions can help you navigate the stormy seas of whaling attacks and improve your organization's security from top to bottom.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.