Back to blog
What is a common indicator of a phishing attempt?
Auth & identity
Nov 27, 2023
Author: Alex Lawrence

A phishing scam is one of the oldest tricks in the online fraudster playbook: pose as a trusted source or person of authority to gain access to someone’s personal, financial and/or business accounts.
A nightmare for many individuals and businesses, phishing scams were recently cited as the most common type of cybercrime by the FBI’s Internet Crime Complaint Center, with more incidents than any other type of computer crime.
Let’s take a look at what phishing scams, generally referred to as phishing attempts or phishing attacks, are made of, how they look, and how to get ahead of them before the damage is done.
An intro to phishing
Phishing’s origins trace all the way back to AOL in 1995, when Khan C. Smith, a well-known spammer and hacker (where’s his Hollywood star?), apparently invented the term when using the aptly-named hacking tool “AOHell” to impersonate AOL staff and “phish” for passwords among them.
Today, in our increasingly digital, AI-fueled world, phishing attempts have evolved to deploy across a much wider array of channels, so for businesses and individuals, understanding what constitutes a common indicator of a phishing attempt is more critical than ever.
Let’s unpack the various makings of a phishing attempt, with an eye on how to better identify and protect against these attacks.
The anatomy of a phishing attempt
The lasting success of phishing attempts speaks to the inventiveness and sophistication of the modern hacker. Today’s phishing attempts are intricate, highly manipulative methods no longer limited to emails – they can occur via text messages, social media, and even phone calls.
Nevertheless, the goal has always been the same throughout its history: in order to succeed, a phishing attempt must trick individuals into providing sensitive data like login credentials, credit card details, or personal information.
A blend of understanding human psychology and behavior coupled with technological mastery is table stakes for any would-be phishing attacker. Let’s drill down on what phishing looks like, and how it’s done.
An example of a phishing attack
Email is a primary vehicle for phishing attempts, and has been one of the more common and persistent techniques throughout history. A seasoned social engineer will find particular success with the text-heavy, often personal nature of emails and the inbox. Here’s an example of how one such attack might go down in your own inbox.
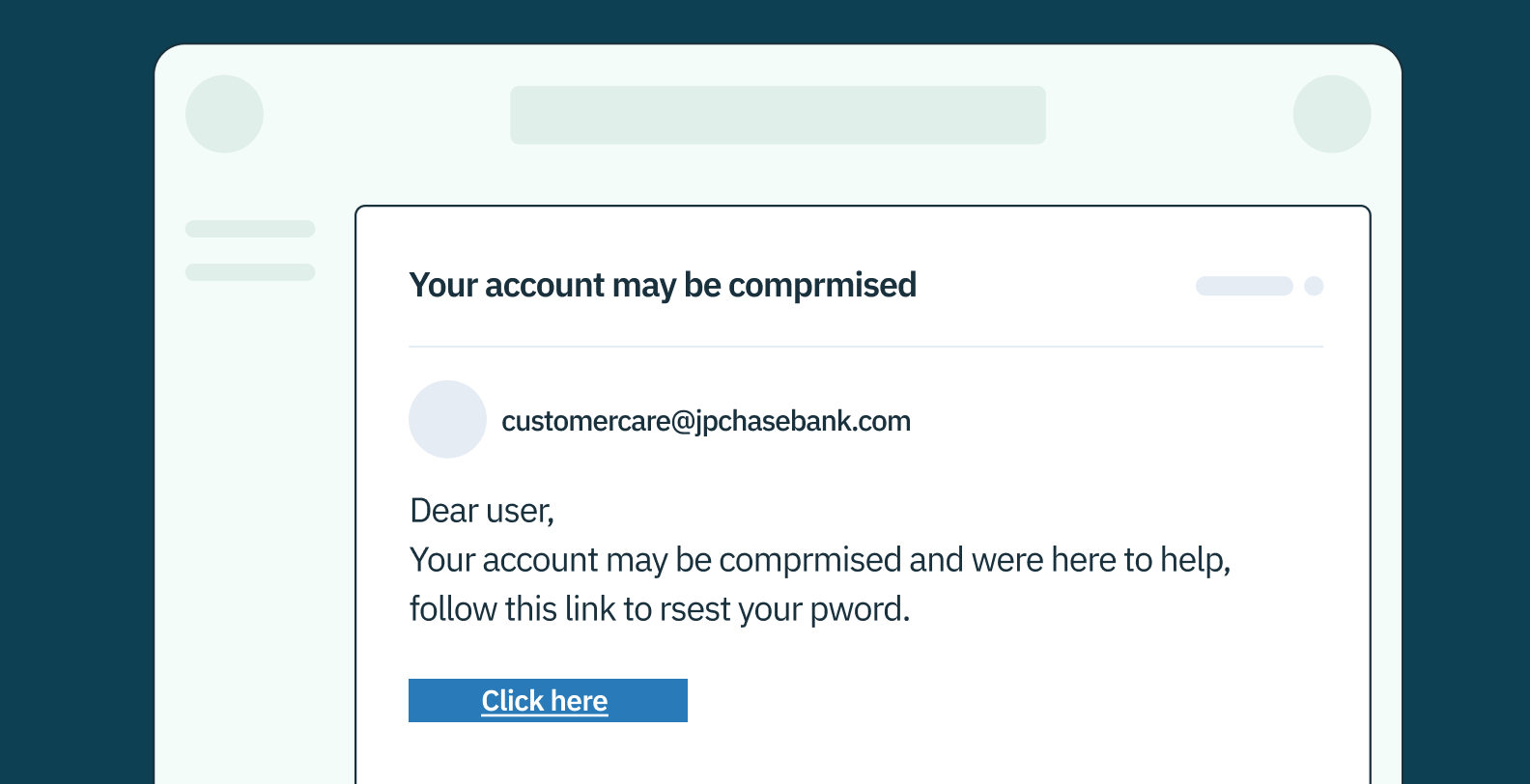
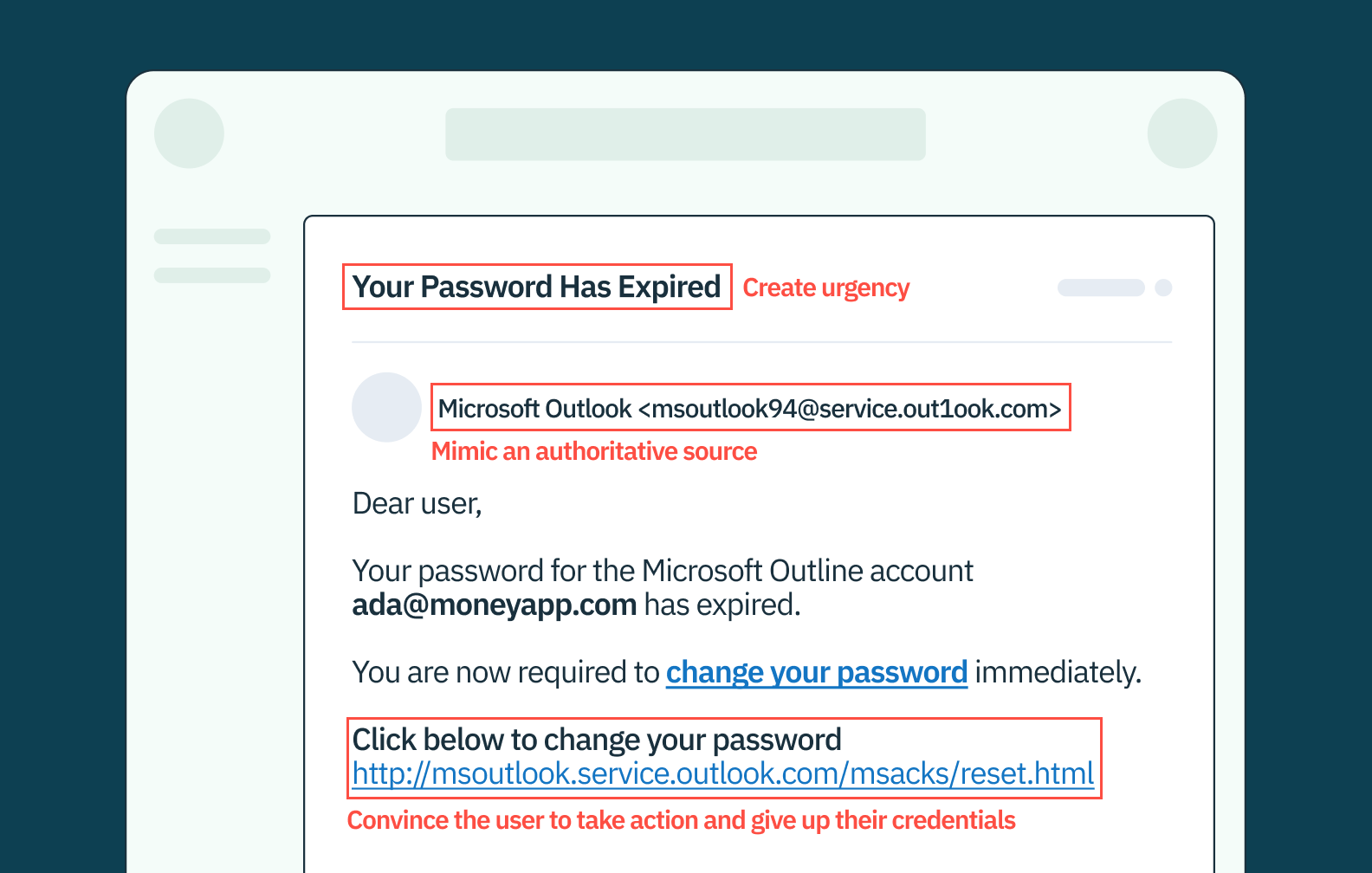
Imagine receiving an email from “Microsoft Outlook Support,” with a subject line “Urgent: Password Expiration Notice.” It appears legitimate, featuring the Microsoft logo and a professional design. The message warns that your Outlook password has expired and urges immediate action to avoid account lockout. This is a classic phishing tactic, where the scammer mimics an authoritative source, Microsoft, to create a sense of urgency and legitimacy.
The email contains a link, deceptively designed to look like an official Microsoft URL, leading to a fake password reset page. This page, again skillfully mimicking the source, prompts you to enter your current credentials and set a new password. In this telltale step, by entering your details, you unknowingly hand over your login information directly to the attacker. And just like that, you’ve been phished.
This phishing example showcases the common attacker’s strategy: posing as a trusted entity, prompting urgent action, and leading you to a malicious site where you inadvertently compromise your own security.
Want unphishable MFA for your app? Switch to Stytch.
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
The telltale signs of phishing attacks
Phishing attacks often begin with a deceptive email or message from a seemingly ‘legitimate’ organization or individual. Using a technique called social engineering, phishing messages are designed to instill urgency or fear, prompting the recipient to respond with the requested information or click on malicious links. These links often lead to fake websites that mimic legitimate ones, tricking victims into divulging sensitive information.
So what is a common indicator of a phishing attempt? It’s usually a predictable cocktail of markers. All phishing attack methods share some traits, and while phishing attacks can be highly personalized and quite convincing, there are several common indicators of a phishing attempt that individuals can look out for:
- Suspicious sender: Check the sender’s email address carefully. If it’s an unfamiliar or misspelled address, it could be an indicator of a phishing attempt (or, it could just be your grandpa who still uses AOL).
- Urgency or fear tactics: As mentioned, phishing messages often use urgent or fear-inducing language to prompt quick action. Persuasive messages, often masquerading as a person of authority, fall under the common technique of social engineering and are indicators of a phishing attack.
- Requests for sensitive information: Legitimate organizations will never ask for sensitive information like passwords or credit card details via email. If an email asks for this information, it’s most likely a phishing attempt.
- Generic greetings: Phishing attempts often use generic greetings or no greeting at all, whereas legitimate organizations will address the recipient by name. “Hey, send me your Amazon credentials – it’s your birthday and I’m phishing for ideas based on your purchase history,” said no client, ever.
- Poor Grammar and Spelling: Grammatical errors and spelling errors can be common indicators of a phishing attempt. Most legitimate organizations take care to proofread their emails before sending them (yes, we all produce phishy writing sometimes). But while minor grammatical and spelling errors can occur in any communication, phishing emails often contain grammatical errors that are uncharacteristic of professional correspondence.
- Fake URLs: Phishing messages often include links that appear legitimate but actually lead to fake websites. Hovering over a link can reveal the true URL and help identify a phishing attempt.
- Suspicious attachments: Email attachments in phishing emails pose an added threat and can contain malware that, once downloaded, infects a device and compromises its data. These email attachments might be disguised as invoices, legal documents, or other seemingly important files. This is why it’s crucial to be cautious with email attachments, particularly from unknown or suspicious sources.
The role of social engineering in phishing attempts
Phishing scams are not just technology hacks; they also exploit human psychology. Social engineering is the deliberate and manipulative use of persuasive messages to influence the behavior of someone online. Through social engineering, a victim might be influenced to break certain standard security procedures with a sense of urgency, exploiting their natural human curiosity.
For example, a phishing email may claim that there has been suspicious activity on the recipient’s account and urge them to click on a link or provide personal information to verify their identity. By preying on human emotions and our natural vulnerabilities, social engineering allows scammers to trick individuals into divulging information or unwittingly downloading malicious software.
The devil’s in the details
Without a modicum of legitimacy, phishing messages and emails would rarely find a victim. To appear authentic, they often replicate the logos, color schemes, and overall layout of communications from genuine organizations. This effectively lowers the guard of potential victims and makes them more likely to divulge sensitive information or click on malicious links.
Links in phishing emails often lead to websites that are clones of legitimate sites, designed to steal login credentials or personal information. These sites may have URLs that are subtly different from the authentic ones – a tactic known as clone phishing. With phishing, the devil’s truly in the details.
Spear phishing
Phishing has evolved over time, from more broad attempts at scale using generic language, to highly personalized messaging targeting specific individuals of higher potential value to an attacker.
Spear phishing and whaling are advanced phishing techniques that target such specific individuals or organizations. These methods are more personalized and hence, more difficult to detect.
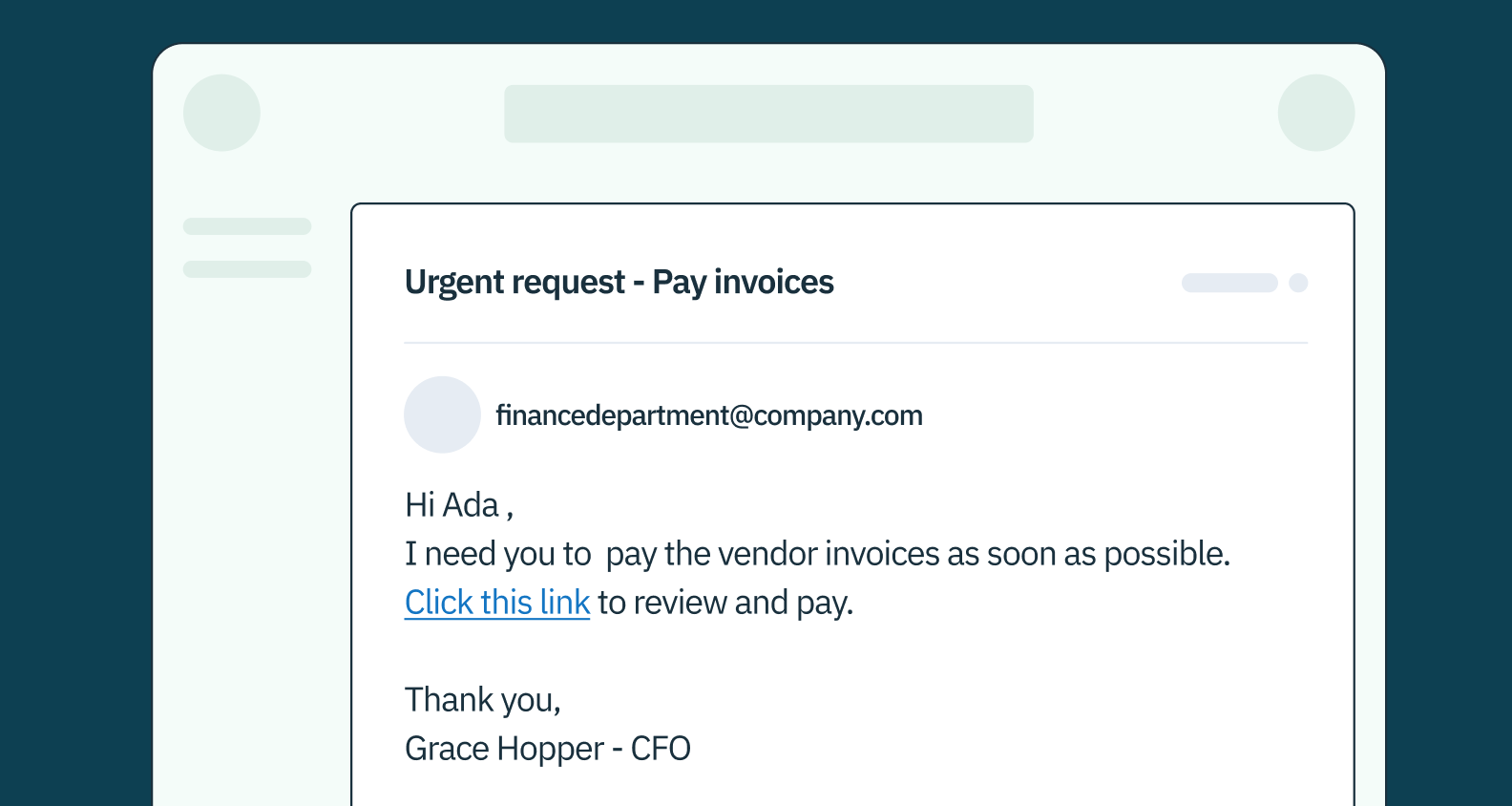
Spear phishing attacks are tailored to their targets. They may include specific information about the victim, such as their job title, workplace, or personal interests, gleaned from online research or previous data breaches. These emails may appear to come from a trusted colleague or superior, making the request seem more legitimate. As a result, spear phishing attacks have a higher success rate than a generic phishing attempt.
Whaling
Whaling attacks are a form of spear phishing attack directed at high-level targets (whales), such as senior executives. These attacks are thoroughly researched and often mimic the tone and language used in official business communication. The goal of a whaling attack is often to gain access to high-value information or to authorize financial transactions fraudulently.
Whaling attacks are highly sophisticated and require a great deal of planning, making them even more dangerous than other phishing attempts.
Combating phishing attacks
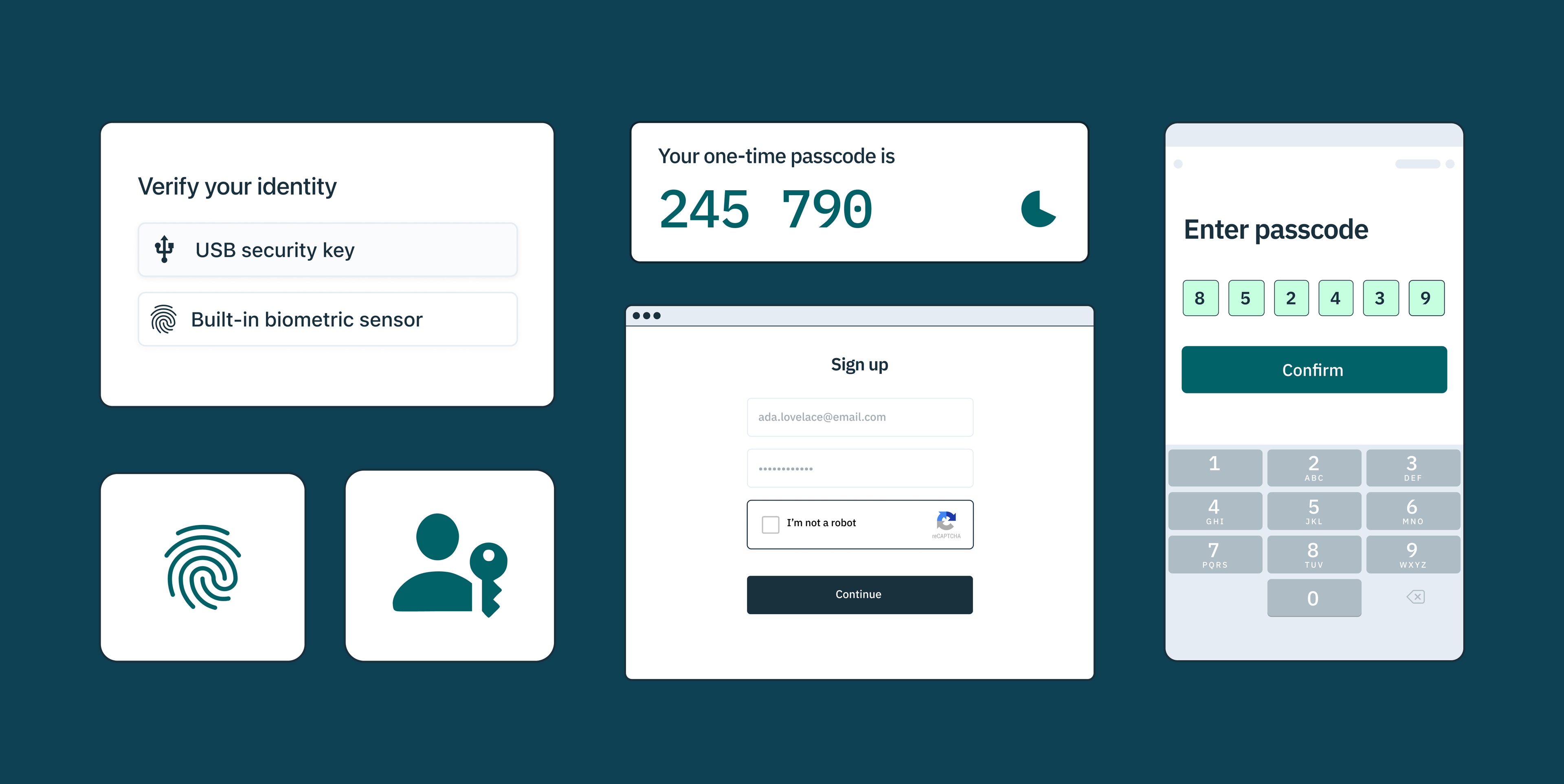
While regular training and awareness programs can help in educating individuals about the risks of phishing, fortifying your website or app’s authentication strategy and flows can greatly reduce phishing attempts and attacks before they even occur, with multi-factor, ‘unphishable’ authentication solutions and device fingerprinting at the helm.
“Unphishable” multi-factor authentication (MFA) from Stych helps prevent phishing attempts by requiring users to authenticate their identities using multiple factors: something they know (like a password), something they have (like a hardware token or registered device), and something they are (like a fingerprint or other biometric data).
Additionally, Stytch offers device fingerprinting, which identifies unique characteristics of a user’s device, such as the operating system, browser version, screen resolution, and IP address. This helps safeguard against OTP bot attacks and other potential breaches.
To learn more about how these or other solutions work, reach out to an auth expert to start a conversation, or get started on our platform for free today.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.