Back to blog
Stytch's guide to passwordless authentication
Auth & identity
Sep 16, 2021
Author: Stytch Team

Thanks to new tools and technologies, passwords are finally being replaced with more secure and convenient passwordless authentication flows like email magic links, SMS passcodes, OAuth logins, push notifications, and biometrics. These modern strategies enable developers to choose the most appropriate authentication options for their use case and user base.
One recent survey found that 75% of users feel overwhelmed trying to keep track of their proliferating passwords. A separate survey found that the majority of respondents would prefer authentication methods for their personal and professional accounts that don't involve a password—users are increasingly interested in going passwordless, but as a developer, it can be hard to know what passwordless authentication flow is right for your application.
The old refrain is that there’s a tradeoff between security and usability, but that no longer applies to authentication -- removing passwords can boost both security and the user experience. 81% of all internet breaches involve weak or stolen passwords, which is why the Open Web Application Security Standard (OWASP) now recommends that all passwords should be considered to be “pre-breached”.
As you begin designing your authentication flow, there are a myriad of passwordless options to consider due to recent innovations in authentication technology. In this guide, we examine many of the common passwordless methods to help you choose the right solution for your application. With each option, we’ll consider how the user experience, security, ease of implementation, and accessibility measure up, with the aim of striking the ideal balance between protection and ease of use.
The (r)evolution of authentication
While passwords have historically been the most common way to authenticate users, innovations over the past 15 years have yielded new authentication types that improve security and usability.
Historically, the dominant choice for authenticating users has been to have them demonstrate possession of secret knowledge (think passwords and PINs). This is the something-you-know authentication factor, and it presents many security and UX challenges.
Over the last decade, however, the rise of programmatic SMS/email, hardware keys, biometrics, and other authentication factors has created two new authentication categories:
- Something you have—authenticating by proving possession of something (e.g. a mobile phone, email inbox, or hardware key)
- Something you are—authenticating by proving a biological trait (e.g. a fingerprint or FaceID)
As a result of these innovations, we’re seeing major shifts in how companies choose to onboard and log in users.
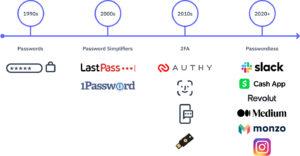
- In the 1990s, as the internet went mainstream, passwords were the dominant form of authentication.
- In the 2000s, as users opened more and more accounts, password managers—which encrypt and store online login information—were introduced to help them handle this something-you-have authentication methods increasingly complex landscape.
- In the 2010s, as online technologies advanced, alternative auth methods—often referred to as “two-factor authentication”—embedded low-friction, secure hardware (like biometrics and YubiKey) and software (like APIs for programmatic text and email) into the user experience.
- In the 2020s, as we begin to embrace passwordless authentication, resourceful companies like Revolut, Medium, and Square Cash are leading the charge. Others like Slack, Instagram, and Craigslist have also started incorporating passwordless options, even if they haven’t fully discarded passwords yet.
Authentication types and tradeoffs
These new factors open up new UX possibilities, but they can also be a challenge for teams as they consider how best to tailor each to users’ individual, situational needs without compromising on protection or usability.
Each factor presents different tradeoffs. Let’s consider the relative advantages of each method of passwordless authentication, starting with those under the something-you-have umbrella.
Something-you-have authentication methods
SMS one-time passcodes
Designed with mobile phone/device owners in mind, short-messaging service (SMS) passcodes allow users to log in to applications using their phone numbers.
When a user requests access to an application or website, an authentication flow texts a one-time, numeric code to their device, which they can then enter—instead of a password—to log in. Thanks to the prepopulating, “autofill” feature on Android and iOS, users do not even need to enter the string manually.
SMS passcodes:
- Help balance security and usability, because logins that tie users to a specific phone number are more secure than password-based authentication options. In fact, SMS messages are the most used second factor to access financial and personal websites.
- Feature built-in redundancy, meaning that if programmatic SMS provider fails in the delivery process, we dynamically fail over to back-ups that can pick up the slack and quickly get the job done.
- Allow flexible integration options, since Stytch’s flexible APIs make it simple to use this method as a primary factor or as a two-factor authentication choice to strengthen security.
While SMS passcodes are a great fit for many applications, they do carry their own unique risks. For certain high value accounts such as cryptocurrency wallets, fraudsters will go to extensive lengths to try to convince cellular networks to allow them to steal a legitimate user’s phone number. While this is a real risk, the effort and cost involved for fraudsters to mount this attack is significant, involving careful curation of an individual’s sensitive personal information and sometimes even outright bribery -- the difficulty involved in this attack is why it’s primarily been targeted at very high-value accounts like Coinbase wallets.
The response to this small risk should not be to discard SMS passcodes entirely. Instead, you should consider the value of the account you’re protecting and choose your passwordless options and any multi-factor authentication requirements accordingly. Large fintechs like Square Cash and Revolut effectively use SMS passcodes to protect even high value accounts by layering other 2FA methods alongside it such as biometrics or PINs.
Email magic links
Put simply, magic links let users log in to an application or website by entering a registered email address, clicking once on a submit button, and receiving a “magic” URL in their inbox, by clicking on the link they can instantly authenticate and log in. This action establishes that they have access to the email inbox. One click is all it takes to log in.
Email magic links can:
- Reduce user friction by removing the hassle of remembering and storing passwords. It’s a simple, one-and-done login or authentication process, making it more likely that users will follow through with whatever they aim to do—whether that’s paying a bill, buying a product, or submitting a document.
- Protect your application and users by eliminating credential stuffing attacks on your login flow and preventing account takeovers.
Authenticator app time-based passcodes
By requiring users to prove they actually have the device they are using to access a website, applications like Google Authenticator provide an extra level of security for critical and highly sensitive services. Differing from SMS passcodes, this type of passwordless authentication asks users to confirm control of their device within a certain time frame rather than requesting a phone number to gain access, which avoids the sim swapping vulnerabilities present with SMS.
Authenticator app passcodes:
- Help facilitate secure transactions by requiring users to demonstrate control of their devices to execute sensitive transactions.
- Offer the security features power users want -- if your application handles sensitive data, many sophisticated users will require authenticator apps in order to feel comfortable using your service.
Push authentication
Push authentication is a passwordless method that asks users to authenticate through notifications sent to an app on their mobile device. The one-tap feature enables users to quickly approve a notification, thereby gaining instant access to an application or website. They can just as easily reject a notification they do not recognize or one they did not initiate, which prevents unwanted parties from accessing secure content.
Push authentications:
- Increase user retention by eliminating the need for users to remember or store passwords to access secure websites or applications.
- Facilitate secure transactions in a manner similar to authenticator apps.
WhatsApp one-time passcodes
Another authentication solution that lets users avoid the traditional password, WhatsApp passcodes enable users of the popular messaging app to log in to secure applications from anywhere, at anytime. By integrating your authentication flow with WhatsApp, you can leverage a network of more than three billion existing users.
WhatsApp passcodes:
- Increase the difficulty and cost of attacks like account takeovers.
- Provide your users with a viable, alternative authentication option if regular text-message delivery is delayed or otherwise affected by a service outage.
OAuth logins
OAuth logins—which leverage industry standards like OAuth 2.0 and OpenID—help engineers easily integrate single sign-on options from popular social platforms and other third-party providers (e.g. Apple sign-in).
OAuth logins:
- Help increase user sign-ups. In fact, most apps report a 20%+ conversion rise in sign-ups when popular OAuth options like Google, Facebook, Apple, Microsoft, and others are introduced. Newer OAuth features like Google’s One-Tap functionality offer even more eye-popping conversion boosts (Pinterest reported a ~50% improvement in web sign-ups and a ~125% improvement in mobile sign-ups when they incorporated this feature).
- Balance security and usability by preventing users from creating a new password for your site that they might reuse and repeat across many services—this minimizes your risk of account takeover and credential stuffing attacks.
- Flexible integration options -- Stytch allows you to integrate these options through either our front end SDK or our direct API if you’d like to fully own the UX.
Something-you-are authentication methods
The something-you-are category of authentication includes biometrics, including voice and facial recognition, and fingerprint scans.
Native app biometrics
You were likely first introduced to the concept of biometric authentication on your mobile devices when iOS and Android introduced the concept of fingerprint and facial recognition for native applications built on top of their operating systems. This method has become a popular way for banks, brokerages, and other sensitive applications to layer low-friction step-up authentication into user workflows.
WebAuthn
In the something-you-are category of authentication are biometrics, including voice and facial recognition, fingerprint impressions, and iris scans. WebAuthn (aka “Web Authentication”) falls partially under this umbrella, though it also supports something-you-have authentication methods like hardware keys as well. This passwordless authentication solution allows desktop and mobile browsers to verify users with built-in device biometrics as well as distinct, specialized hardware keys like YubiKey.
WebAuthn:
- Can use biometrics to ensure a user demonstrates both possession of an original device and a unique biometric trait through face or fingerprint ID.
- Offers your users best-in-class security by doubling down on verification while also minimizing user friction.
- Allows you to easily integrate strong hardware authentication like YubiKey to protect sensitive applications and use cases.
What happens after authentication?
The above authentication methods detail how you can prove who a user is -- however, once a user has been successfully authenticated, you’ll likely want do a few things:
- Keep the user logged in as they navigate different parts of the app
- Occasionally escalate them up for additional verification (and friction) if they try to take a particularly sensitive action (like withdrawing funds or altering their account information)
- Continually check throughout the user’s interactions whether they have sufficient permissions to take the action they’re attempting
Most of the above boils down to session management and how you manage your user’s logged-in experience. Session management regulates interactions between web-based applications and individual users. Stytch Sessions allow your users to easily implement sessions in a way that provides fine-grained control.
Stytch Sessions:
- Offer countless advantages over JSON web tokens (JWTs) in terms of security and control.
- Make performing route-based authentication simple, allowing you to precisely control the level of authentication that any sensitive action requires
- Provide improved session security by allowing you to easily revoke sessions and protect against unauthorized access.
What authentication is right for your project?
Designing an authentication flow can seem overwhelming given the UX and security issues involved. When we help developers think through what's right for their authentication flow, there are three main questions we ask (you can always join our Slack community for more guidance):
1. What type of account data does your application protect?
There's a big difference in the level of authentication you need if you're a fintech/healthtech app, for instance, versus a news digest app.
For more sensitive applications like fintech + healthtech, we frequently recommend multi-factor passwordless authentication, which allows you to both balance UX and security. Square Cash, Monzo Bank, and Revolut are great examples of companies that weave together multiple passwordless options in order to protect their users.
2. Do users primarily engage your application via mobile, desktop, or both?
Conversion rates vary across these channels. For instance, SMS one-time passcodes perform extremely well on mobile due to their autofill capabilities but create slightly more friction on desktop than email verification. Companies that Square Cash and Hippo Insurance provide users with the option to choose what’s most convenient for them.
3. What's your current reset password flow, if any?
Some teams are hesitant about moving to passwordless authentication until we ask this question. Then they realize that they already allow users to log in without a password. The majority of reset password flows only require a user to demonstrate ownership of an email address or phone number—making them essentially passwordless. If you require a user to supply additional information during a password reset (e.g. some banks require the last 4 of your SSN), this can help in determining what level of user authentication you deem sufficient in allowing users to access your application.
Interested in learning more?
Build auth with Stytch
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
At Stytch, we worry about authentication so that you don't have to. If you want to discuss your specific authentication needs, sign up for a free account and chat with our team.
If you’d like to dive deeper into the topic of authentication, you can join the Stytch Slack community here.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.