Back to blog
What Is Anonymous Visitor Identification? How to Identify Visitors to your Website or App
Auth & identity
Dec 3, 2024
Author: Stytch Team

An anonymous (unidentified) visitor to your website could be a regular user with legitimate interest, but hiding behind that same anonymity are also malicious actors and bots. Anonymous visitor identification is the process of associating traffic to your website or app to a particular entity, classifying what kind of visitor it is, and identifying its intent.
This article explains why it is important to identify website users and explores the processes and technologies you need to implement to make sure that as many visitors as possible are correctly identified. This will let you take the right actions to protect your online assets from hacking attempts, fraud, account abuse, and other malicious activity — without disrupting your regular users.
Good traffic or bad traffic? The importance of identifying anonymous website visitors
The first thing that usually comes to mind when "anonymous user identification" is mentioned is online marketing. Ad platforms rely heavily on classifying and identifying users to target ads at the most relevant audience and track potential customers. However, while capturing sales leads is important, the stakes are much higher when it comes to fraud prevention and protecting your app from malicious web traffic and multiple attack vectors.
Every CAPTCHA you encounter when browsing the internet is just the tip of the iceberg of determining whether you are a real user. Significant technical efforts are undertaken in the background to figure out where you are located, what browser you’re using, what pages are you likely to view and in what order, and more.
Website owners are also interested in all this information because it’s costing them money to keep their service online. While a simple static web page may cost a fraction of a cent to serve to the end user, the cost is much higher for more complex pages with lots of assets. If your service includes AI-powered features or other kinds of resource-intensive functionality, the cost you incur for every website visit increases dramatically.
This makes anonymous visitor identification — and more specifically, the blocking of unwanted users — an important strategy for making app security and resource-intensive services viable.
Mitigating risk by blocking malicious actors
Another reason for blocking malicious actors and bots is the additional risk that they bring. The more malicious actors can see and understand about your service, the more likely they are to find a way in and potentially cause issues. Here are some examples of fraudulent and risky activity that malicious users may engage in:
- Account hijacking: Using stolen credentials or brute-force attacks to take over another user's account. This can be done manually, but it is more often performed by automated bots. This can then lead to further exploits, such as laterally moving through your infrastructure using privileged accounts, or using the details of the stolen account to further defraud the owner.
- Trial and product abuse: Human users will often try to hide or change their online identity to sign up for multiple product trials or extend the period they can access a website for free. For example, they may use multiple email addresses to sign up for new trial subscription periods or new browser sessions to get past article limits on a news website.
- Attack vector research: Malicious users will generally try out new exploits in different ways to see if they can cause a breach and then take advantage of it.
Differentiating between valuable and harmful traffic
Determining whether traffic is "bad" or "good" isn't just about identifying synthetic users; not all bots are bad, and not all humans are virtuous. Some bots are welcome, such as those for search engines and other indexes that make your website discoverable to others online. Blocking access to these bots would be detrimental to your website, as it would effectively make it invisible to the greater internet.
Conversely, some malicious activity in your app will come from real people; for example, fraudulent activity as part of a phishing campaign; and while it's important that offenders are identified and blocked, the mechanism that does so cannot be too sensitive and risk causing trouble for real users.
For these reasons, anonymous visitor identification must be a multi-stage process to make sure it is as accurate as possible. It should also be part of a larger authentication and security process to prevent data breaches and protect your product reputation.
Methods of online anonymity
There are legitimate reasons why privacy-conscious users will want to limit their digital footprint. However, these methods of online anonymity are also used by bad actors, creating an ever-evolving balancing act of thwarting your visitors' online privacy measures (in the name of protecting your infrastructure) while respecting the wishes of your real users and not driving them away with invasive identification practices.
Common ways that visitors may mask their traffic to your website or app include:
- Throw-away email addresses: Single-use email addresses are used to create multiple accounts, but they may be used legitimately by privacy-aware users who do not want to share their actual details with every service they sign up for.
- Private web browsers/incognito mode: Web browsers that provide disposable sessions that do not record the browsing history or share data and cookies have become standard across all operating systems, and they are commonly used by regular users.
- Burner/virtual devices: Virtual machines can be used to further anonymize users by isolating activity, and malicious users may employ multiple devices to defeat security measures or impersonate multiple users. However, there are legitimate reasons to use virtualization or own multiple devices, particularly in the sought-after software development space.
- Public WiFi or hijacked networks: Public WiFi networks (like the one at your local coffee shop) or hijacked networks (where a hacker may have gained unauthorized access to a business’s private WiFi network) can be used to perform malicious activity, hiding it amongst the legitimate traffic of other users on the network and making it hard to determine the source.
- Privacy VPNs, proxies, and TOR: These methods all mask the source of traffic by routing it through a shared service. While all of these methods can be used to mask the source of malicious traffic, privacy VPNs in particular are often used by legitimate users to secure their connections while using public networks.
Increasingly, consumer-focused web browsers are integrating technologies such as VPNs, private web browsing, and virtualization as part of their value proposition. This is creating an arms race between privacy features and website and app owners who want to know who their visitors are and what their intentions are. Significantly, the proliferation of privacy features in web browsers means that anonymized traffic is becoming the majority.
How can anonymous visitors be identified?
This constant push for privacy makes confident identification a long complicated checklist to determine whether a visitor is a human or bot and whether they've previously been identified as a potential threat. These determining factors include:
- The visitor’s IP address: IP addresses are no longer a reliable way to identify individual users, since they can be spoofed. And many legitimate users connect using public WiFi or cellular service. However, in some egregious cases, traffic from some IP addresses may be 100% illegitimate and can be outright blocked.
- Device and browser fingerprinting: Device and browser fingerprinting technologies exploit various web browser features (including canvas fingerprinting) that can identify a specific user. However, these can usually be blocked at the cost of reduced browser functionality for the end-user.
- Sessions, cookies, and tracking pixels: Browsing sessions can be uniquely identified using cookies or other unique identifiers embedded in the session. These methods can be easily mitigated using private browsing settings.
- Visitor behavior: A user's behavior when using your app or website can quickly give away whether they are a bot (especially if your site is protected using CAPTCHA or ReCAPTCHA). It can also uniquely identify the user based on their usage patterns.
- Login and email tracking: A logged-in user, or a user following a unique link from an email, can be readily identified.
- Geolocation: A user's location can be used in conjunction with other information to narrow down the source. However, this can be easily spoofed by the web browser, and geolocation based on IP address can be unreliable.
Anonymous visitor identification is an ever-evolving space, and new ways to identify anonymous visitors are constantly being devised (and circumvented). This makes developing your own visitor identification solution a monumental and ongoing task. Usually, reliable and effective anonymous visitor identification requires the combination of multiple data points.
Why WAFs aren’t enough for anonymous visitor identification
Traditionally, web application firewalls (WAF) have been the bulwark against bot attacks. These security gateways block visitors based on rigidly defined conditions like IP address ranges of known VPN providers, browser version strings, location data, request frequency, and other factors.
Popular platforms that provide WAF functionality include open-appsec, AWS WAF, Imperva WAF, and Cloudflare. Unfortunately, these tools do not provide the mechanism for actually identifying anonymous visitors. This impacts security and accessibility: relying solely on WAFs to protect your application means continually tweaking firewall rules that are not specific enough to exclude advanced programmatic attacks, and may block real users from accessing your products.
Intelligent tools that can adapt in real-time are required to precisely detect and block malicious traffic down to the individual device.
Stytch: advanced device fingerprinting for anonymous visitor identification
Device fingerprinting is the most effective tool for anonymous visitor identification — but it is a complex process that must leverage an ever-broadening array of technologies to keep up with new anonymization techniques. Implementing your own device fingerprinting involves designing and implementing a secure, automated system that complies with evolving regulations in different regions, and committing to the ongoing maintenance and security patching of your system.
Stytch Fraud and Risk Prevention combines device fingerprinting with machine learning, providing highly accurate anonymous visitor identification. Our device fingerprinting solution integrates directly with your applications, detecting the source of anonymous traffic, and detecting bots (both good and bad) as well as malicious users.
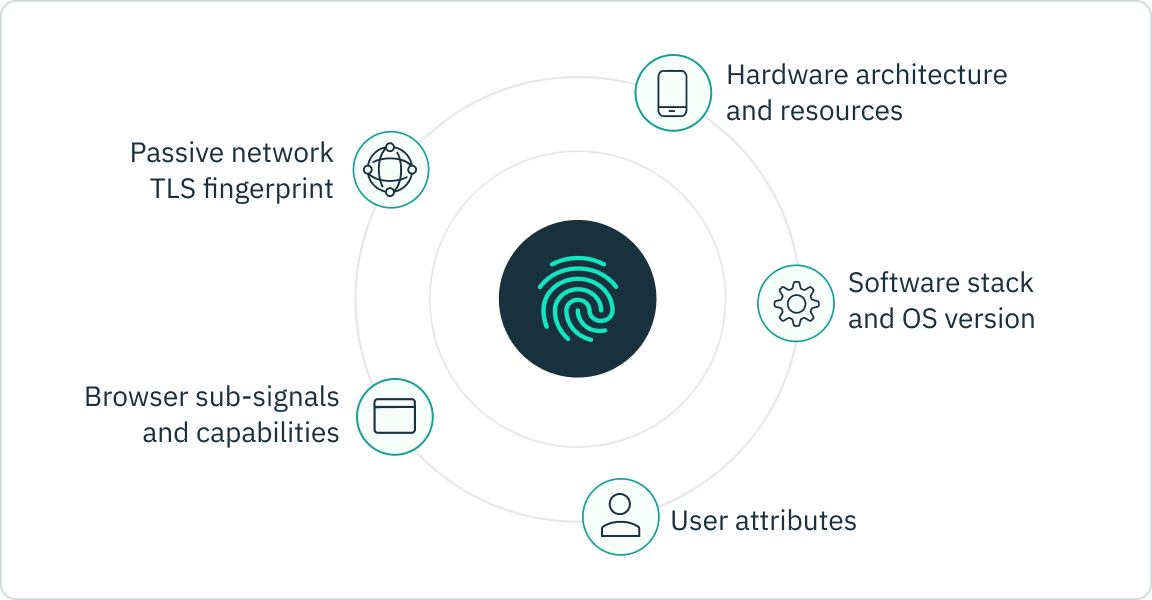
Once a visitor is identified, you can programmatically define access rules, filtering out unwanted visitors while ensuring that real, valuable users are not turned away at your doorstep.
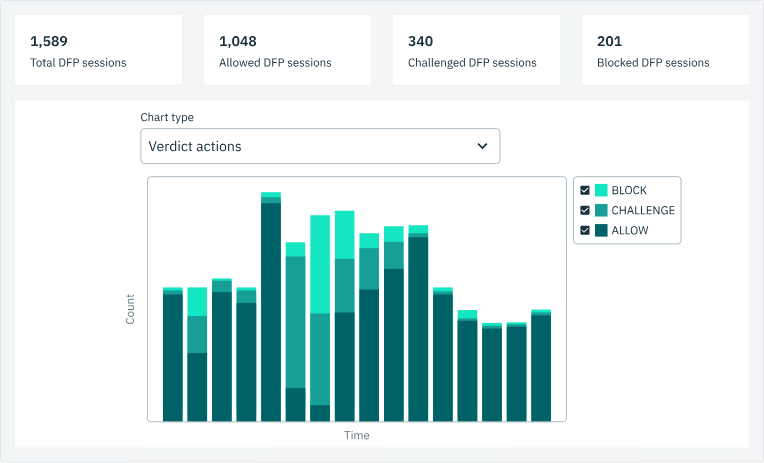
Everything in Stytch is reported on and observable, so you are always aware of any ongoing risks, and able to respond to maintain a strong security posture.
You can learn more about anonymous visitor identification with Stytch by contacting our auth experts — or jump right in and start integrating Stytch in your app.
Advanced Device Fingerprinting
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.