Back to blog
What Is device fingerprinting? Guide and implementation techniques
Auth & identity
Aug 12, 2025
Author: Stytch Team
Hackers and scammers have many methods to draw upon to take over user accounts and access sensitive information. Whether they’re stuffing credentials, using brute force attacks, phishing, or sending spam, they’re almost always making use of bots at some point in their process. The sophistication and potential scale of these techniques is evolving daily.
In the modern cybersecurity context, device fingerprinting is vital for fraud detection and prevention and a necessity for almost every kind of application.
What is device fingerprinting?
Device fingerprinting is the process of collecting key information about your user's browser, hardware, operating system, and network and generating a unique identifier for each device. It builds on browser fingerprinting (including canvas fingerprinting) to enable desktop and mobile device fingerprinting based on additional hardware and network attributes.
This allows you to identify bad actors with high confidence, based on their device characteristics.
Unlike cookies, which are stored client side and can be tampered with and leaked (due to a lack of security awareness on the end user’s side), device IDs are stored in a server-side database. This database of device fingerprints allows you to compare the fingerprint of a current device against previous ones, thereby verifying whether a user is accessing the app from the same device.
If the same user logs in from several devices or matches suspicious usage patterns, or if fraud is otherwise suspected, the application can block them or give additional authentication prompts to verify their identity.
This can be used to re-enforce traditional authentication flows (including passwordless methods like TOTPs, passkeys, and multi-factor authentication) to drastically reduce the chance that someone is impersonating a user by providing information to advanced fraud prevention tools.
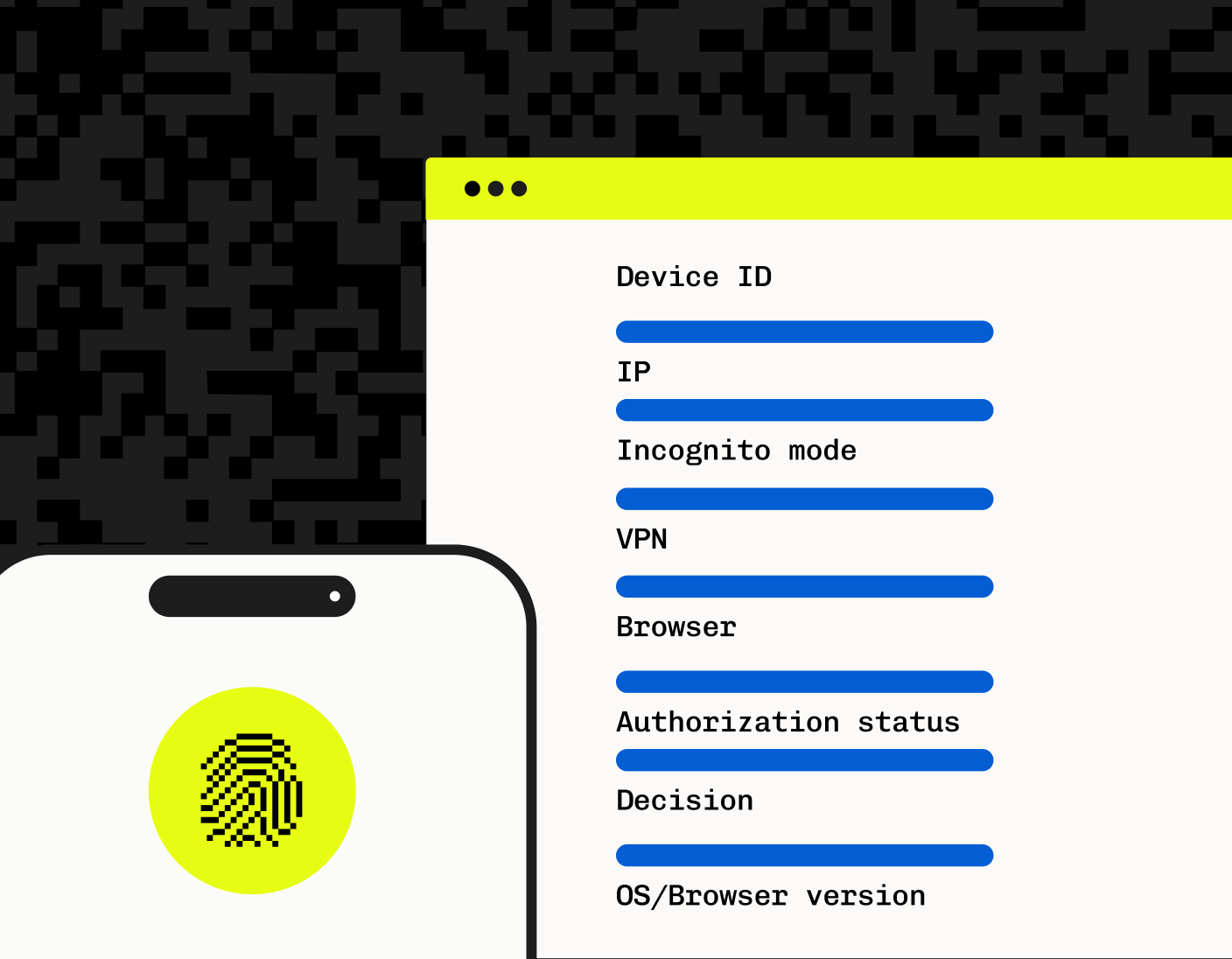
How does device fingerprinting work?
When a user accesses a website or app, certain kinds of information about a user’s device have to be processed in order for the website to load and display properly. This includes things like the screen size (so that content can be rendered to scale), supported HTML5 features, installed plugins, language, the browser version, and operating system. These attributes can be combined and hashed into a device ID that can be used by fraud mitigation systems to work out whether a device has been seen before or is associated with suspicious activity.
After this ID is stored, the next time someone logs on claiming to be that user, the app can compare the device fingerprints to see if the user is logging on from the same device or a new one. If it’s a new one, depending on how suspicious the login attempt is, the application can either block the user or ask for further verification.
What separates device fingerprinting from browser fingerprinting?

Device fingerprinting is a kind of browser fingerprinting that collects additional data points, such as IP addresses and TLS configuration. Rather than just passively reading browser attributes, it also uses active JavaScript code on the client side to generate highly unique and stable fingerprints.
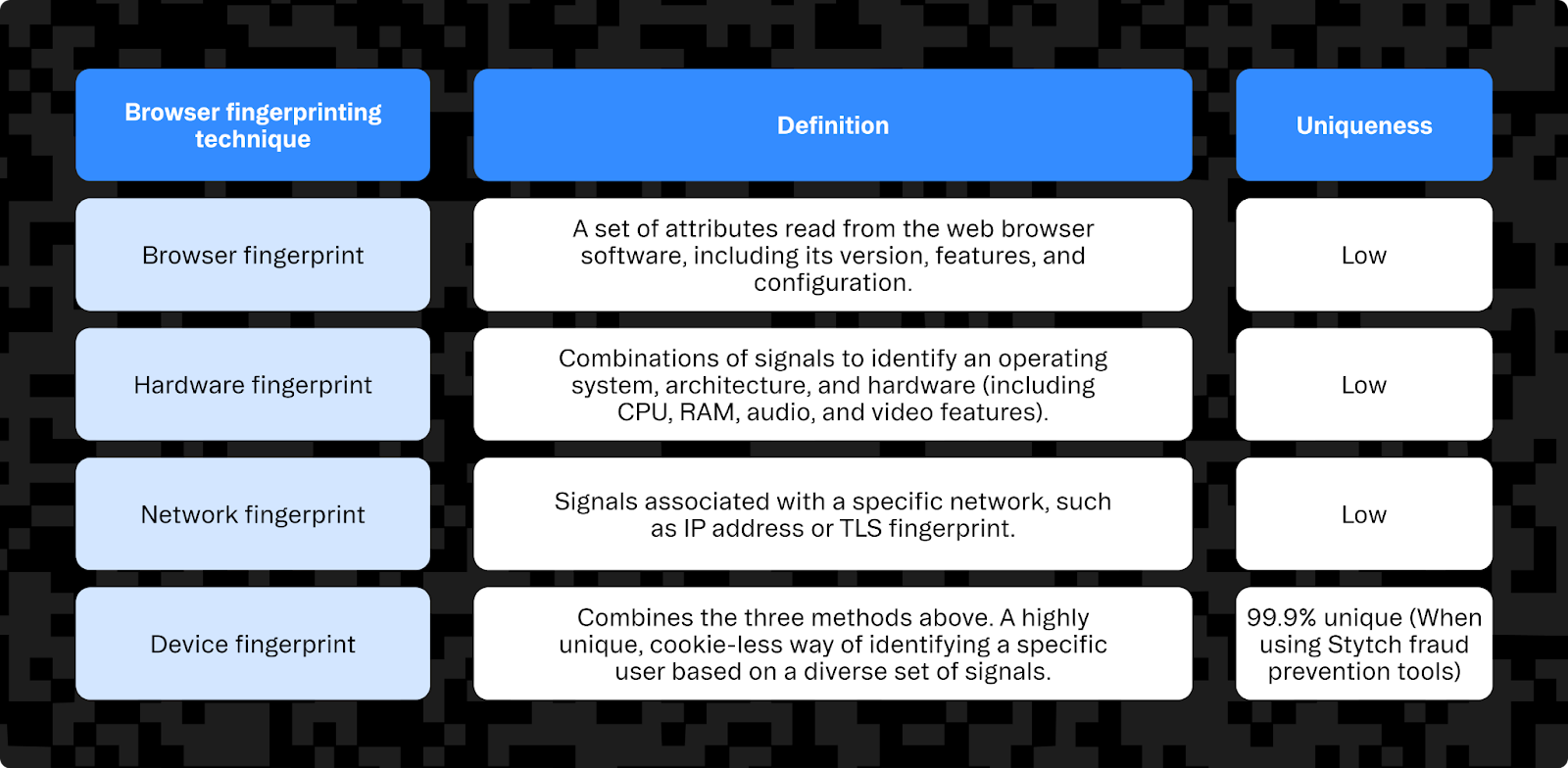
Device and browser fingerprinting can be performed on any kind of desktop or mobile device, but the collected attributes can vary depending on the device. For example, while a native app can detect whether a mobile device has been jailbroken (iPhone) or rooted (Android), a mobile web browser typically cannot.
Want to stop fraud? Get Device Fingerprinting from Stytch.
Detect good AI agents while stopping bots and fraud • Pricing that scales with you • No feature gating
How can I implement effective device fingerprinting?
The more data a device fingerprint tracker collects, the more unique that device ID will be. While it may be easiest when implementing device fingerprinting to just track a few core attributes, insufficient data will render your device fingerprints easier to imitate and thus ineffective for categorizing risk and taking action.
It’s important to consider how easy it might be for a hacker to tamper with the data you collect. Hackers can easily change the user agent string their browser sends, or use a VPN to change their IP address, time zone, etc. Relatively simple factors like these are also easy for hackers to “spoof” or imitate by analyzing the fingerprint of other devices and then contriving or faking those data points on their machines. This is why it's vital to collect data that is harder to fake without detection, such as touch hardware, and video and audio capabilities.
Device fingerprinting implementation JavaScript example
To see how basic device fingerprinting works in practice, take a look at the following example:
// Note this code is for example purposes only and not for production use. You should never copy and paste security-related code into your project without fully understanding and vetting it for your use case.
async function getBrowserFingerprint() {
// Collect data from the web browser to build the browser fingerprint
const canvasFingerprint = getCanvasFingerprint();
const fingerprint = {
cookiesEnabled: navigator.cookieEnabled,
localStorageEnabled: !!window.localStorage,
sessionStorageEnabled: !!window.sessionStorage,
screenSize: `${screen.width}x${screen.height}`,
language: navigator.language,
browserPlugins: Array.from(navigator.plugins).map(p => p.name),
cpuCount: navigator.hardwareConcurrency,
memoryGB: navigator.deviceMemory || 'unavailable',
canvasFingerprint: canvasFingerprint,
};
// Submit the fingerprint data to the back-end server, which will add additional server-side data and generate a fingerprint hash
try {
const response = await fetch('http://localhost:3000/fingerprint', {
method: 'POST',
headers: {
'Content-Type': 'application/json'
},
body: JSON.stringify(fingerprint)
});
const result = await response.json();
// Print the returned fingerprint data to the console.
console.log('Fingerprint Hash:', result.hash);
console.log('Match:', result.match);
console.log(Threat Score:', result.threat);
} catch (err) {
console.error('Fingerprinting Error:', err);
}
}
// Function to generate a canvas fingerprint
function getCanvasFingerprint() {
const canvas = document.createElement('canvas');
const ctx = canvas.getContext('2d');
ctx.textBaseline = 'top';
ctx.font = "16px 'Arial'";
ctx.fillStyle = '#f60';
ctx.fillRect(125, 1, 62, 20);
ctx.fillStyle = '#069';
ctx.fillText(Canvas Fingerprint', 2, 15);
ctx.fillStyle = 'rgba(102, 204, 0, 0.7)';
ctx.fillText(Canvas Fingerprint', 4, 17);
return canvas.toDataURL();
}
// Run browser fingerprinting on page load
getBrowserFingerprint();This code snippet uses the user’s device information, including their userAgent, screen resolution, and time zone to create a hash that can be used to identify the device. While these attributes may suffice for some basic device fingerprinting applications, they’re fairly easy to alter or obfuscate.
Once you start implementing device fingerprinting at a more advanced level, you'll have to deal with more complex signals, as well as harden your client-side logic against attacks.
Device fingerprinting best practices
One of the surest ways to make your device hashes more unique and harder to hack is by simply collecting a larger variety of data points.
To have the most effective device fingerprinting strategy, you'll need to combine a variety of signals, including some that are harder to tamper with, like WebGL rendering or AudioContext timing. You can also detect more detailed information about a device’s browser, like its installed plugins and fonts as part of your fingerprinting.
However, adding the wrong data points can reduce the stability of your device hashes. As a silly example, you wouldn’t want to include the current timestamp in a device hash, because it will change constantly even without explicit user action. You should focus on stable data points that don’t change, even if a user does things like change Wi-Fi networks or upgrade their browser.
If certain kinds of user data are important to your device fingerprinting solution, you can deny access to users logging in through a VPN or incognito browsers. However, note that this can introduce friction for users who prefer navigating online this way, so make sure you know your user base before doing anything that will make it harder for people to use your product.
Signing and encrypting device IDs help reinforce device fingerprints’ integrity by making them much harder to access and to fake. It’s a lot more challenging for fraudsters to reverse-engineer legitimate device fingerprints if those fingerprints are securely stored.
Advanced device fingerprinting techniques
It’s important to note that a “device fingerprint” is only as unique as the information collected. Obviously, there’s more than one person in the world on a MacBook Pro using Safari — so the more diverse data points a device fingerprint is based on, the harder it is for an attacker to blend in with benign traffic. This is why Stytch uses device, network, and browser data points to make sure the device fingerprints you generate have enough granularity to stop bad actors.
This is also why leveraging device fingerprinting to prevent fraud is not just about what information is collected, but how that information matches or doesn’t match contextually with a given user. Machine-learning algorithms can assess the full context of all traffic to your app or website to better understand user and device behavior and to identify patterns and suspicious devices based on a combination of factors or correlations. This kind of computing can augment your device fingerprinting and keep it agile and responsive to new hacking and spoofing methods.
Device fingerprinting and user privacy

While Stytch Device Fingerprinting is tailored for fraud prevention, other companies also use device fingerprinting for other purposes like targeting online advertisements or personalizing consumer experiences. Some privacy regulations like Europe’s General Data Protection Regulation (GDPR) allow device fingerprinting for fraud prevention, but they’re stricter when it comes to using the same techniques for marketing or e-commerce use cases. This includes the requirement to obtain explicit consent from users whenever collecting their information, including when using device fingerprinting.
We find the best way to do this is to explain to users:
- Exactly what data an app is collecting and why
- Who that data will be shared with
- How that information is being used, and how it will not be used
- All the additional steps and investments your company is making to actively protect your server-side databases and user information
The end goal with disclosures like these isn’t about checking a box; it’s about engendering trust. A transparent, clear disclosure about precisely how you handle your customers’ data responsibly is as important as the tool itself.
How does device fingerprinting help prevent fraud?
By allowing websites to affiliate device data with their users, device fingerprinting helps you monitor for irregularities or suspicious user activity and intervene sooner if there is a risk of fraud or account takeover.
For example, if a user who consistently logs in from one time zone with the same default browser language suddenly logs in from a different region with a different language, you can take additional steps to verify the user to protect their account. This action can mean something as unobtrusive as requesting additional authentication methods, or it can mean a more robust response like revoking access tokens or invalidating session cookies.
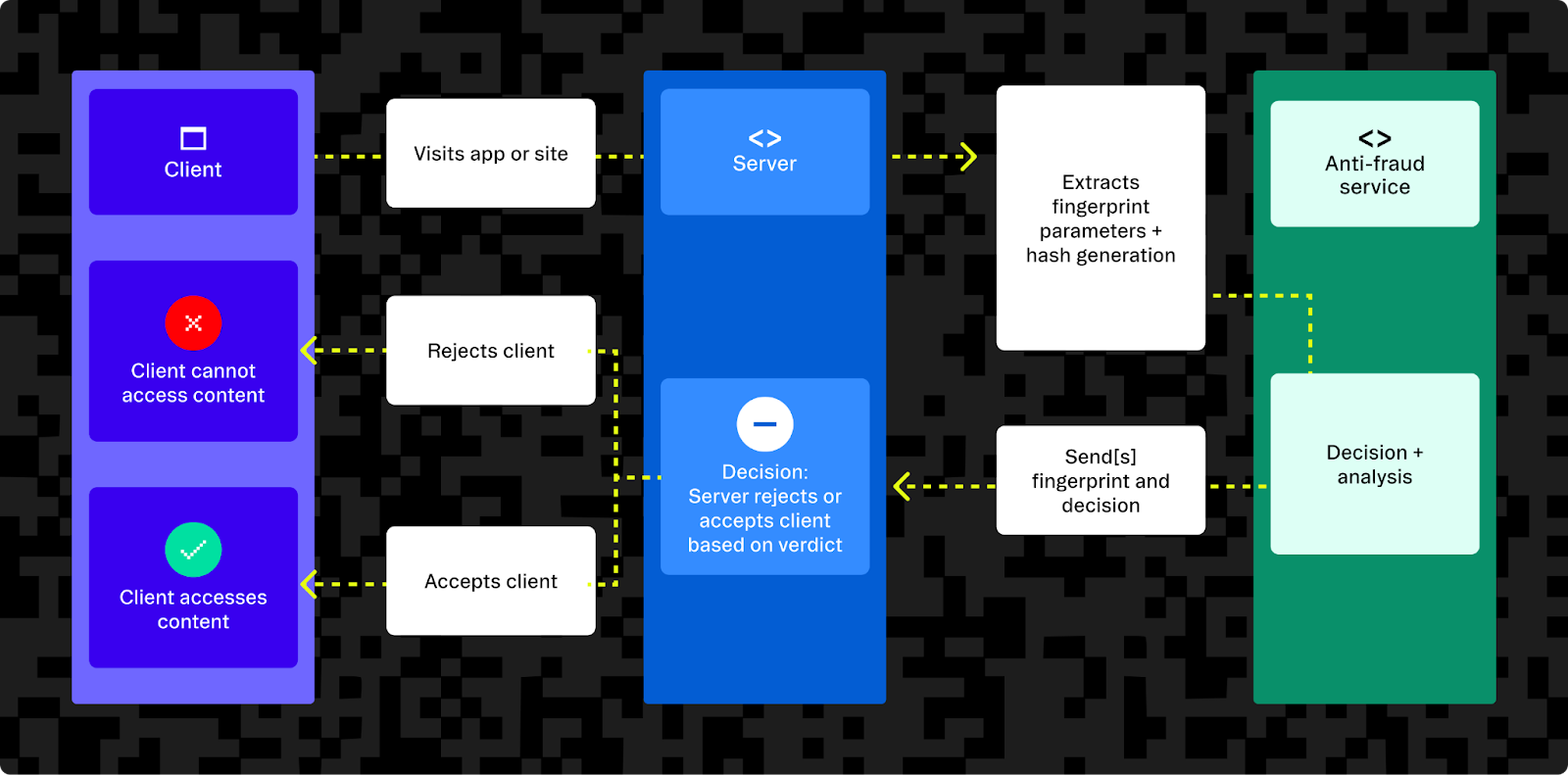
Device fingerprinting also helps prevent what’s known as “first-party fraud,” in which bots do things like create new accounts in order to abuse a website using spam or purchase scarce assets (think of limited-edition Nike shoe drops or Taylor Swift’s Ticketmaster fiasco). This is different from “third-party fraud” because the accounts involved haven’t been stolen or compromised. They were created in order to commit fraud, so you won’t get help from the account owner.
By giving you a better sense of which traffic is a genuine user and which is fraudulent or bot-driven, you can better protect your users and ensure they have the best possible experience when using your products.
Add device fingerprinting and fraud protection to any website with Stytch
As part of a comprehensive auth platform, Stytch device fingerprinting goes the extra mile for customizability and security: we collect device data from multiple sources and use advanced techniques to create a cryptographically-secured fingerprint for each user’s device. This allows us to provide a higher level of security than other solutions while still offering the same flexibility and developer-first experience that comes with any of our products.
Adding Stytch device fingerprinting to any website or web app is as easy as adding the Stytch library to your project. Below, Stytch browser fingerprinting is used as part of a user-authentication flow:
<html>
<head>
<script src="https://elements.stytch.com/telemetry.js"></script>
</head>
<body>
<button id="login" onclick="login()">Click here to log in!</button>
<script>
function login() {
var publicToken = "PUBLIC_TOKEN"; // public token from Stytch Dashboard
GetTelemetryID({
publicToken: publicToken
}).then((telemetry_id) => {
var request = new XMLHttpRequest();
request.open('POST', 'https://www.example.com/login', true);
request.setRequestHeader('X-Telemetry-ID', telemetry_id);
request.send(null);
});
}
</script>
</body>
</html>This code implements device fingerprinting alongside Stytch authentication, which also adds behavioral pattern analysis and adaptive MFA to your app. This helps detect and stop malicious behavior and block bad bots (including emerging AI agents that may be up to no good). Every visitor is given a threat score and recommended action, with which you can use to block, deny, or challenge their session.
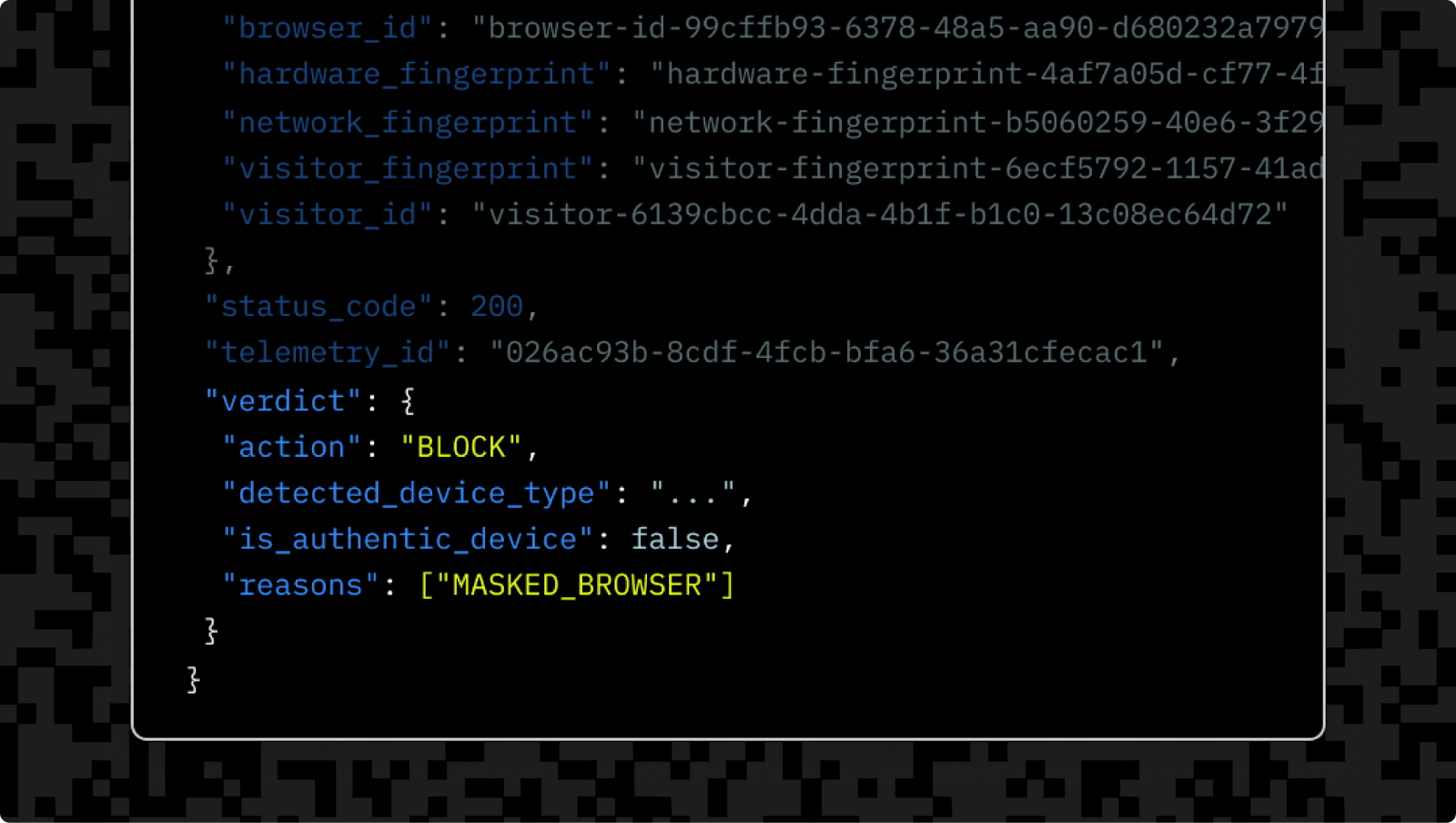
Fingerprinting for fraud detection is best left to the pros and typically not worth the DIY risk. Stytch generates trustworthy device IDs, keeps up with emerging threats and device fingerprinting countermeasures, and ensures compliance with privacy laws.
Get started with Stytch device fingerprinting for free, check out our docs, or book a demo today.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.


