Back to blog
Multi-factor authentication: how to choose the right approach for your business
Auth & identity
Aug 24, 2022
Author: Stytch Team
Multi-factor authentication (MFA) is a key tool for companies looking to elevate users’ account security, helping to mitigate credential stuffing attacks and prevent account takeover fraud. Sometimes used interchangeably with the term two-factor authentication (or 2FA), MFA involves a layered approach to confirming a user’s identity to ensure they have permission to access a protected digital system (e.g. a website, application, network, etc.) or perform a specific protected task within that system.
As its name suggests, MFA requires users to successfully present two or more identity credentials, called authentication factors, in order to gain clearance. Implementing MFA is now a critical step for any company serious about their Customer Identity and Access Management (CIAM) program.
MFA often (but not always) occurs at initial login. Sometimes, however, the authentication factor prompts are dispersed throughout a user’s digital experience, only requiring 2FA when the user attempts to take a particularly sensitive action such as change their payment details. This latter implementation, where authentication friction is only introduced at the appropriate time in the user’s session, is referred to as “just-in-time” or step-up authentication. Finally, there’s also a type of step-up authentication called “adaptive MFA”, which requires users to go through a MFA step when a specific behavioral change on the account suggests a higher risk of account takeover (for instance, if it’s a new device or a suspicious IP address).
Typically, the user's credentials – whether a password, username, or some other type of secret key – will serve as the "something you know" factor, while a second factor of authentication that is unique to that individual, such as a fingerprint, retina scan, or one-time passcode generated by an authentication app, will serve as the "something you have" factor. The combined use of these two factors makes it much more difficult for an unauthorized user to gain access to an account, as they would need to have both the user's credentials and the second factor of authentication.
There are a number of different ways to implement MFA, and the specific method(s) used will depend on the type of system being accessed and the level of security required. For example, systems that require a high level of security, such as financial or healthcare applications, may use MFA that combines multiple factors, such as something you know, something you have, and something you are. In this case, the "something you are" factor would typically be a biometric, such as a fingerprint or iris scan.
The growing importance of secure multi-factor authentication
Today, supporting multi-factor authentication is necessary for most applications that safeguard even remotely sensitive data due to the prevalence of credential stuffing and account takeover attacks. Account takeover risk stems from the greatest weakness in online security: the human element. A Verizon Data Breach Report found that 82% of all data breaches can be traced back to the human element involved in online security – specifically, the weak and inadequate passwords that users often re-use across multiple sites.
Weak passwords have introduced two major security threats that nearly every application finds themselves playing whack-a-mole to prevent: 1) credential stuffing attacks and 2) account takeover. Credential stuffing involves fraudsters trying to validate whether a username or email and password pair are valid for a particular site and involves sending significant bot activity to applications’ login forms.
Account takeover is an attack vector where hackers execute the final step to actually take control over online accounts that belong to another user. Account takeover attacks typically have a financial motive where the attackers intend to use the stolen account to defraud the user directly (e.g. draining funds from a bank account) or the business (e.g. making an e-commerce purchase that the business will ultimately need to refund to the original user).
One method for reducing account takeover risk is to require users to create passwords on your site that haven’t previously been exposed in a data breach (this is made possible by built-in breach detection in Stytch’s Passwords product), but another popular way to protect user accounts involves layering on additional security with multi-factor authentication. Fortunately, there are numerous secure options to choose from that can help you eliminate the vast majority of account takeover risk in your application.
When deciding to integrate MFA into your application, there are a few questions to ask yourself:
- Will you make MFA optional or require it for all users?
- Will you offer multiple MFA options so that users can choose what best fits their needs? How many and which options will you provide?
- Will you layer on?
Add MFA to your login flow with Stytch
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
What MFA is right for you?
While you can theoretically use any authentication method for two-factor authentication, there are strengths and weaknesses associated with each one.
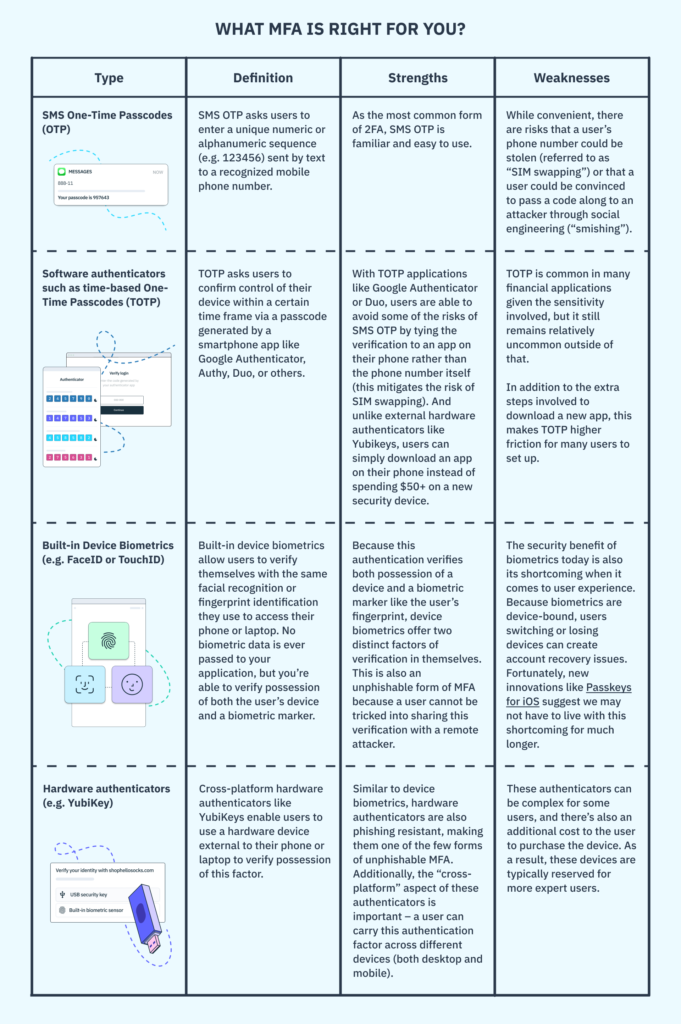
Unless you require it for your application, it can be difficult to convince users to enroll in two-factor authentication after they’ve already created an account. While there are versions of multi-factor authentication (e.g. Yubikeys and biometrics) that are more secure than common methods like phone number verification, our recommendation is to pursue a MFA strategy that allows you to enroll the highest percentage possible of your user base. This typically entails offering multiple options to users when enrolling in MFA.
Balancing security and user friction: step-up authentication
Organizations use various digital authentication methods to protect their sensitive assets. Multi-factor authentication describes the process of combining multiple authentication factors to increase the security of users’ accounts. Step-up authentication is a specific type of multi-factor authentication where the application implements an authentication strategy that requires an additional authentication level specifically when trying to perform high-risk operations on an IT system.
For example, customers can use the banking applications installed on their smartphones to view their profiles and check their latest account transactions. Of course, they must log in to their account using, for example, a username and password. However, suppose the customer tries to perform a risky operation, such as transferring a large sum of money to another account. In that case, the banking app requires an additional authentication method. Another method might be providing a one-time password (OTP) sent through email or text messaging, an authentication app, or biometrics.
As the previous example shows, step-up authentication requests additional identification information to verify a user’s identity when trying to accomplish sensitive actions. Requesting further information enables IT administrators to use different authentication levels based on the sensitivity of the resources.
You can contrast step-up authentication with another type of MFA called adaptive MFA – step-up authentication is a MFA strategy where particularly sensitive routes in an application require MFA while adaptive MFA is a strategy where only certain types of user characteristics (e.g. a suspicious IP address) require MFA. Both are individually helpful, but they become even more powerful when combined together into a comprehensive authentication strategy.
You can use step-up authentication to secure access to critical resources, such as updating payment information, transferring funds, and changing payment settings in an account to enable withdrawing funds to other accounts. You can also use the adaptive MFA scheme to verify users’ identities when:
- They fail to log into their account several times — for example, by providing an incorrect username and password.
- They access an online service from an unusual location, such as a foreign country, for the first time.
Removing the hassle of MFA with Stytch
Stytch offers a suite of different MFA options that are easy to integrate, so that you can provide the right level of optionality to your user base. From SMS to TOTP to biometrics and hardware keys, we offer every conceivable 2FA option that you and your users could need. Additionally, we make it easy to minimize MFA friction by only introducing these requirements when a user is accessing sensitive information (step-up auth) or when suspicious behavior is detected (adaptive MFA).
To get started, you can sign up for Stytch or request to talk to an expert to chat through your organizations’ specific needs.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.