Back to blog
Stopping an account takeover before it takes a toll
Auth & identity
Jul 23, 2024
Author: Alex Lawrence

There are few things worse than waking to the realization that your organization’s defenses have been breached. An account takeover attack, where cybercriminals gain access to login credentials to steal funds or information, is a serious threat to businesses and individuals. These attacks often lead to fraudulent transactions, unauthorized shopping from compromised accounts, financial loss, stolen personal information, and reputational damage.
This article delves into how these attacks occur, their evolution in the AI era, and how developers and organizations can protect themselves and their end users from the consequences.
Understanding account takeover fraud
Account takeover (ATO) fraud is a type of cybercrime where attackers gain unauthorized access to a user’s online account and carry out harmful activities. With every breach, the ramifications are not just financial; they extend to identity theft and a host of other malicious activities that permeate our online and offline lives.
Account takeover attacks can have a significant impact on both businesses and consumers, leading to financial losses, reputational damage, and loss of customer trust. Preventive measures, such as constant vigilance, comprehensive security strategies, and adaptive cybersecurity approaches, are crucial to mitigate these risks.
As we increasingly shift everything online, the threat of ATO has grown exponentially. The evolution of these attacks in the AI era has made them even more sophisticated and harder to detect. Cybercriminals now have a plethora of tools at their disposal, enabling them to execute large-scale attacks with unprecedented ease. Let’s dig a bit deeper into how they work.
The anatomy of an account takeover
As mentioned, the genesis of a successful account takeover starts with stolen or compromised user credentials due to the prevailing problem of weak passwords. Account takeover techniques such as credential stuffing, phishing, and malware are commonly used by cyber attackers to gain control of legitimate accounts. When cybercriminals gain unauthorized access by means of exploiting these weak passwords, it can lead to a cascade of malicious activities, including identity theft, fraudulent transactions, and even blackmail. Hint: We don’t actually need passwords anymore. Curious about going passwordless? Learn more here.
Attackers have multiple means of obtaining user credentials through data breaches, phishing attacks, or purchasing them on the dark web. Once inside a compromised account, the potential for damage multiplies as attackers can access sensitive information such as personal details, credit card numbers, and social security numbers. The core of an ATO attack lies in the unauthorized access to sensitive user data and the subsequent exploitation of this access for various malicious purposes.
The challenge of detecting account takeovers
Identifying account takeovers isn’t easy. For one, fraudsters often hide behind a customer’s positive history and mimic normal login behavior, using techniques including phishing, credential stuffing, and malware, making it difficult for traditional security measures to identify the threat. Unfortunately, the shift of our lives online and the widespread reuse of passwords has made the account takeover a lucrative method for cybercriminals.
Compromised accounts can lead to significant consequences for businesses, including financial losses, additional security measures, and reputation damage.
Fortunately, studying the modus operandi of cybercriminals in executing account takeovers as well as the hurdles in identifying such attacks can inform the development of effective counter-strategies.
Common methods used in account takeover attacks
Phishing remains one of the most common methods used in ATO attacks. Cybercriminals trick victims into providing their login details through scams executed via channels such as SMS, emails, scam websites, chat conversations, malicious phone applications, and phone calls.
Cyber attackers gain unauthorized access to a legitimate bank account to steal funds or information, using techniques like phishing, malware attacks, and bot-driven automation.
These attacks often involve legitimate yet rigged web pages containing malicious code to harvest user credentials, including login credentials, to aid the attacker in gaining unauthorized access.
Other methods include credential stuffing, where cybercriminals use breached credentials from one site on multiple other sites to gain unauthorized access. Malware-based ATO attacks involve infecting the user’s device with malicious software that can capture keystrokes and intercept user credentials. Comprehending these methods forms the foundation for devising strong countermeasures against ATO attacks.
Aside: As hackers develop more sophisticated social engineering techniques, breach-resistant passwords can provide a crucial guardrail. What’s breach resistant? A strong, secure password that’s hard for bots to guess. Stytch’s built-in zxcvbn strength assessment tool is a simple way to ensure that passwords created adhere to NIST password guidelines. Plus Stytch integrates with HaveIBeenPwned to track compromised credentials and trigger a password reset if needed. Learn more.
Account takeovers in the AI era
AI and machine learning now play a substantial role in facilitating ATO attacks. They have enabled more sophisticated techniques for compromising user credentials, increasing the prevalence of account takeovers, which skyrocketed globally by 155% in 2023. Cybercriminals often purchase stolen credentials on the dark web to carry out account takeover fraud. Let’s take a look at how AI can make ATO attacks more potent and harder to stop.
AI and machine learning in ATO attacks
Fraudsters now use automated technologies to test millions of credentials on thousands of websites. Automated password cracking systems have replaced traditional ‘brute force’ attacks with more sophisticated methods. For instance, machine learning algorithms can now analyze vast datasets to generate accurate variations of passwords, greatly increasing the success rate of ATO attempts.
Generative AI can also create convincing written text that mimics human language patterns. The sophistication of the technology now infuses messages with the appropriate jargon, tone, and structure that align with the targeted individual's expectations. For example, an AI can generate emails that appear to come from a bank, employer, or family member, including personalized details that increase the credibility of the message.
AI hasn't only created more convincing phishing emails and texts – deepfake technology is also being employed to manipulate voices and visuals, enabling cybercriminals to impersonate individuals and authorize fraudulent transactions using voice or video. On social media, AI-powered bots mimic human behavior more convincingly, leading to the creation of fake accounts en masse and automated social engineering attacks.
Modern ATO attacks in action
In late 2020, a major Account Takeover (ATO) attack using credential stuffing and phishing targeted high-profile Twitter accounts of celebrities and corporations. Cybercriminals used credentials from previous data breaches and phishing tactics to deceive Twitter employees and gain access. They tweeted links to fraudulent cryptocurrency sites, promising to double the money sent to a Bitcoin address. Within hours, they collected over $100,000 from victims. This incident highlighted the severe risks of credential stuffing and phishing on social media.
Undoubtedly, the growing sophistication and severity of modern ATO attacks emphasizes the need for advanced protection measures.
Taking charge: Solutions to detect and prevent ATO
As a first (and cost-effective) step in mitigating the frequency and impact of account takeovers, implementing a strong password policy is essential. At a base level, Stytch recommends the following:
- Encourage users to create passwords that are long and memorable rather than focusing solely on complexity. Length provides more entropy, making passwords harder to crack.
- Discourage the use of easily guessable patterns or common words, and instead, promote the use of passphrases composed of random words.
- Instead of regularly prompting users to change their passwords, which can lead to weaker password choices, emphasize the creation of strong, unique passwords from the start.
- Encouraging the use of password managers can help users generate and store complex passwords securely. A strong password policy should also avoid forcing users to remember too many different passwords, reducing the likelihood of unsafe practices like password reuse.
Educating users about common attack methods and implementing security measures are crucial steps to prevent account takeover. This includes promoting strong password hygiene, cautioning against sharing sensitive information, and providing guidance on recognizing and reporting suspicious activities.
Beyond instilling strong password policies, Stytch offers several solutions to reinforce authentication at the organizational level, along with proven fraud prevention tools that can meaningfully shift your account security from reactive to proactive.
Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) adds an extra layer of security by requiring additional verification beyond the password. MFA often uses a combination of something you know (like a password) and something you have (like a phone) to verify identity, increasing security for user accounts. Time-based one-time passwords (TOTP) are a common MFA method that requires a new code for each login session.
Implementing MFA can prevent a successful account takeover attack, which involves the theft of login information leading to fraudulent transactions and unauthorized shopping from compromised financial accounts.
Stytch’s ‘unphishable’ MFA provides enhanced security beyond traditional MFA by ensuring multifactor authentication can’t be bypassed or phished. MFA can include biometric verification methods such as fingerprint or facial recognition, adding an extra layer of security. Stytch provides a flexible MFA suite, incorporating best-in-class methods like SMS one-time passcodes and email verification. These solutions ensure that user credentials remain secure and prevent unauthorized access.
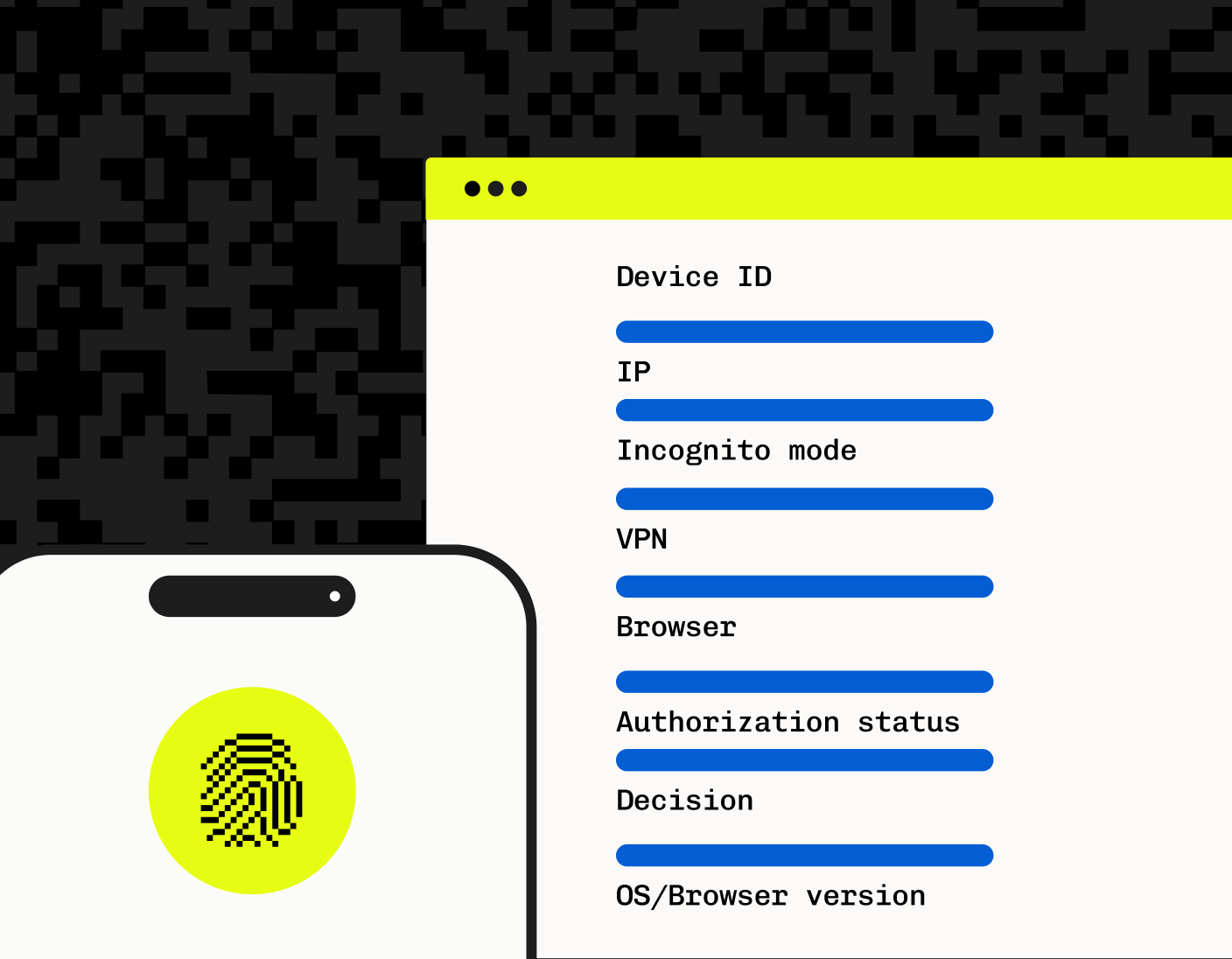
Device Fingerprinting
Behavioral analytics establishes a baseline of ‘normal’ user behavior to detect deviations that may indicate a potential account takeover (ATO) attack, such as irregular login times or unusual transaction patterns. AI-driven algorithms analyze these anomalies in real-time, helping to detect potential threats early. A robust, real-time fraud detection solution is crucial for identifying emerging attacks and sophisticated fraud techniques, swiftly alerting users to suspicious activities like unfamiliar login attempts or unauthorized changes to account settings.
Stytch’s Device Fingerprinting (DFP) tags unique characteristics of devices and behaviors that are hard to reverse engineer to make it easier to distinguish humans from bots. The feature assigns a globally unique identifier for each device, enabling granular control over individual user device responses. Stytch’s device fingerprinting helps block bot activity by distinguishing it from legitimate traffic and using Strong CAPTCHA for validation.
Device classification in Stytch automatically categorizes devices based on trust levels and authorization status, allowing you to customize the actions your organization wants to take. DFP also offers stable identification across incognito browsing, VPNs, and changes to user agents or IP addresses.
To start implementing Stytch authentication and fraud prevention, check out our docs and start building for free today. Or, to learn more about how these or other solutions work, reach out to an auth expert anytime.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.