Back to blog
Stytch’s guide to adding passwordless options for password-based auth flows
Auth & identity
Aug 17, 2022
Author: Stytch Team
Adding passwordless options to your password-based auth flow is a quick, seamless way to boost security and user engagement.
At Stytch, we’re passionate about the power of frictionless, passwordless authentication, and we believe it’s the way of the future. But we also realize that each application and user base is unique, and not everyone is ready to ditch passwords for good. For that reason, we offer a full suite of Customer and Identity Access Management (CIAM) solutions including both password-based and passwordless options to help you provide the most secure and high-converting auth flows to your customers.
Luckily, adopting passwordless auth isn’t an either/or proposition.
You can easily add passwordless options to your existing password-based flow — whether as one option among many or as a primary or secondary factor in a multi-factor authentication (MFA) flow — and still enjoy all of the associated UX and security benefits. As an added bonus, if or when you do decide to go fully passwordless, you’ll already have all the right pieces in place.
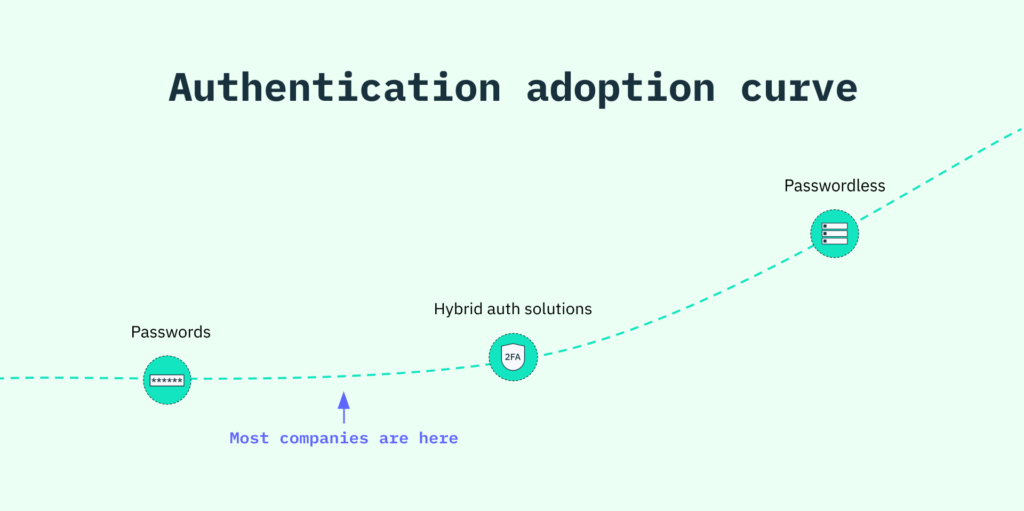
In this guide, we navigate the first step forward on the authentication adoption curve and share how you can shift from an exclusively password-based flow to a hybrid password/passwordless flow, with a glimpse into some of the most common transitional auth models in use today.
Finding the right path to passwordless
No two journeys on the authentication adoption curve are alike. You may be eager to implement a passwordless solution as your primary authentication factor, or you may merely want to include one as a parallel or secondary factor.
For those early in the passwordless adoption curve (or just starting to consider a change), we offer a modern Passwords product that enhances the security and UX of your current password-based flow. Among other innovations, our API scans the web for breached credentials and bakes smooth, passwordless Email Magic Links into the password reset template.
If you are ready to try passwordless, there are many passwordless solutions on the market. Each comes with its own distinguishing features, and identifying which method is right for your app often depends on your specific industry, audience, and target user experience.
Below, we explore some of the ways you can position a passwordless method within your flow — and which methods would be a good fit — to help you determine the best path forward.
Want to go passwordless with your auth?
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Passwordless as a parallel option
In some cases, you may want to offer several primary authentication options, covering many bases at once and increasing the likelihood users will sign up for and engage with your app.
For instance, you could consider presenting high-converting, passwordless auth methods side-by-side with your current password-based flow:
OAuth (aka Social Logins)
OAuth logins allow users with accounts on platforms like Google and Facebook to sign up for and log in to your app using those existing credentials.
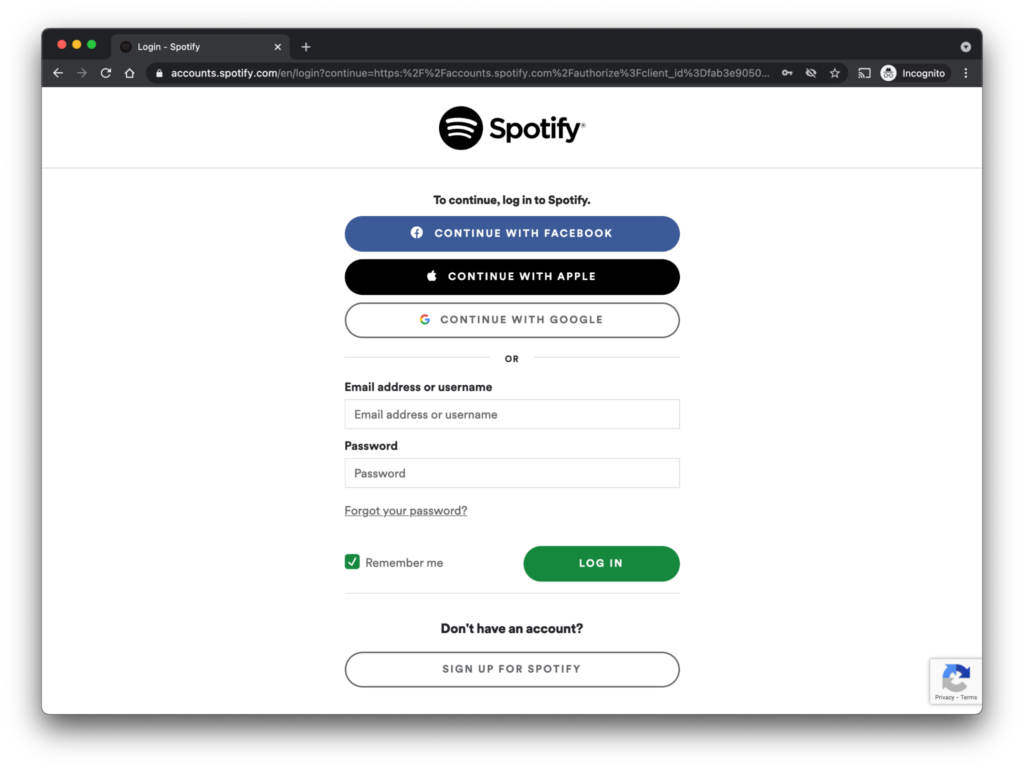
Spotify, for instance, gives users the choice of entering a classic username-and-password combination or using OAuth to sign in through their Facebook, Apple, or Google account.
OAuth offers several UX and security benefits, including:
- Leveraging trust and credibility by authenticating users through popular, established platforms they’re already familiar with.
- Removing the friction and risk of making users create and recall another set of credentials — or, worse, re-use existing passwords.
- Giving users flexibility and control over their authentication experience.
OAuth is a good choice for apps that want to provide maximum flexibility with minimal risk. Make sure to look for account deduplication measures, which top providers like Stytch will build into their solutions to avoid vulnerabilities arising from multiple access points.
It’s worth noting that 70% of our new customers sign up for an account via OAuth versus other available flows, making it one of the highest converting methods we’ve seen.
Email Magic Links
While Email Magic Links work well as a primary auth factor, they’re often used as part of a password-reset flow. That’s because, in many cases, conventional password-based logins already include a user’s email address — so it’s a quick, painless process to send a link they can click to instantly verify their identity and log back in.
For example, companies like Instagram still put passwords first — but they rely on Email Magic Links to remove friction from their critical reset flow.
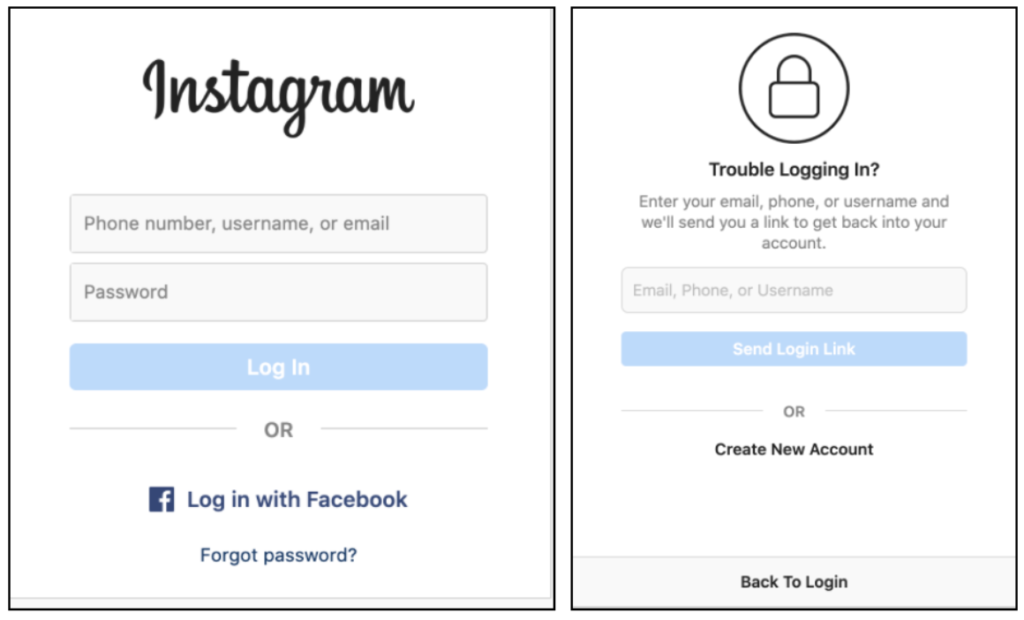
Of course, by using magic links as a reset measure, you’re embedding a passwordless auth flow into your app — so why not just offer it outright as a parallel primary option?
Some of the advantages of Email Magic Links include:
- Higher conversion rates, since all users have to do is click on a link to log in.
- Stepped-up security, since the added verification layer prevents cyber attacks from bots and other bad actors.
- Smoother reset flows, since users don’t have to come up with (and remember) yet another convoluted password to re-engage with your app.
Magic links are a good option for apps with high email penetration among their user base. Stytch even offers Embeddable Magic Links that weave the authentication process seamlessly into your marketing campaigns and other customer communications, boosting conversion and engagement rates even further.
One-Time Passcodes
Like Email Magic Links, One-Time Passcodes (OTPs) can be used as a primary auth factor or as part of an MFA flow. Users are sent a unique passcode via SMS, email, or WhatsApp, which they then enter in-app to access their account.
ESPN, for instance, uses an email-based OTP flow as part of its password-reset process:
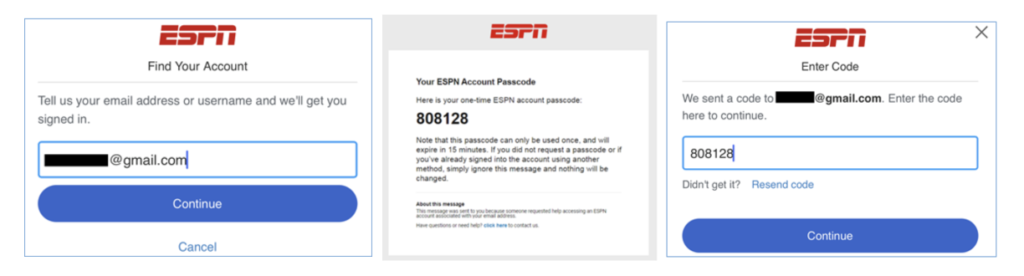
Passcodes share many of the benefits of Email Magic Links — and, for mobile apps, they may even be faster, since they make use of a device users already have in their hands.
Now, iOS and Android phones also have auto-fill capabilities for incoming passcodes, so users can onboard and log in with a single tap (and without ever leaving your platform).
Passwordless as a secondary factor
Including a passwordless solution as a secondary factor (2FA) means you can keep your current password-based approach as is. Adding a step to your initial login flow — or later in your user access journey to protect higher-risk actions — just means you offer an added layer of security.
In addition to those listed above and below, there are several passwordless methods you can use as a secondary or supplementary factor, including:
Time-based one-time passcodes (TOTP)
TOTP works well as a two-factor auth option in circumstances where you need added reassurance of ironclad security — like moving large volumes of money or handling personal payroll records.
It requires users to establish they’re holding a particular device, generating a passcode that’s based on the current time, as well as a shared secret between the server and an authenticator app like Google Authenticator.
That means TOTP allows you to:
- Avoid common phishing attacks by removing users’ phone numbers from the equation, using an app on their local device instead.
- Limit auth windows to a narrow window of time, usually about 30 seconds.
- Authenticate offline, which may be significant for users in areas with poor or limited connectivity (like an airplane) who still need immediate access.
Inserting a secondary, passwordless factor like TOTP into your authentication flow means you can provide extra security — without the extra friction.
Passwordless as a primary factor
Going passwordless-first is as simple as making any of the above passwordless flows your primary (or even your only) authentication measure. In fact, virtually all of the passwordless auth products we offer through Stytch’s platform — including Email Magic Links, SMS and Email Passcodes, and OAuth Logins — can be mobilized as your sole factor.
Forward-thinking companies are also finding ways to innovate on frictionless, biometrics-based methods and make them the only auth solution apps will ever need:
Biometrics
Biometrics are an element of WebAuthn — a cutting-edge web standard that authenticates users through desktop and mobile browsers using built-in biometric scanners (like fingerprint, face, and iris IDs) or specialized hardware keys like YubiKeys.
Historically, biometric data has been stored locally on a mobile device or laptop, making it impossible to access across platforms, relegating it to supplementary-factor status. But now, groundbreaking solutions like Apple’s new passkeys can back up the cryptographic keys that contain biometric data to the cloud — making them interoperable across devices (and viable for primary auth).
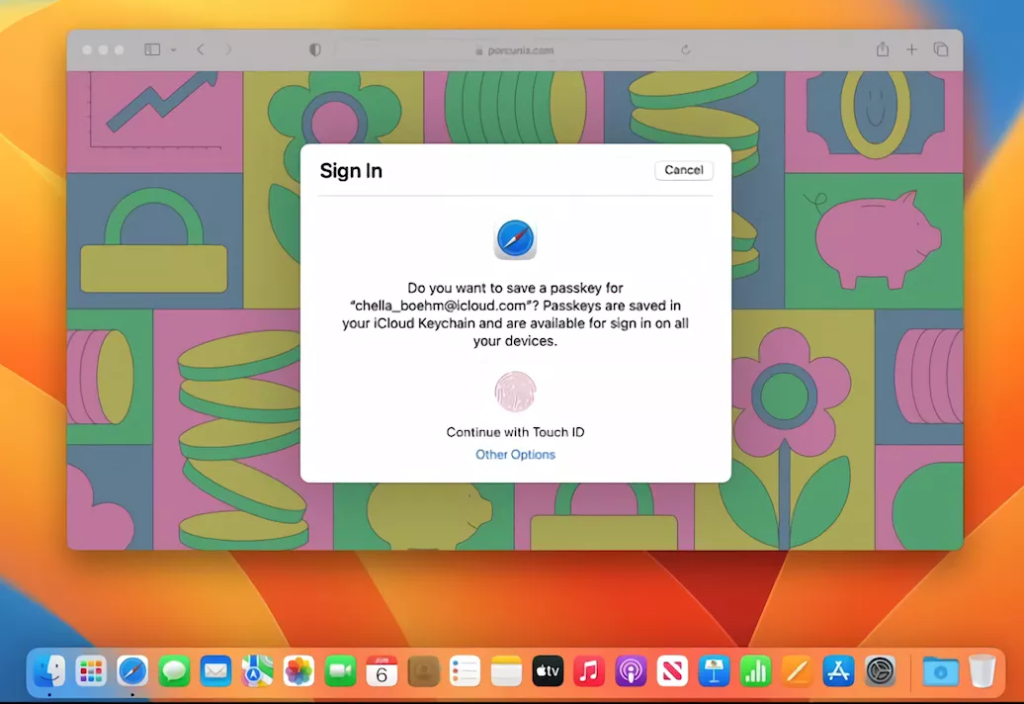
Biometrics are considered next-level auth for good reason:
- They’re pretty much unhackable, since a user has to prove possession of an original device and a unique biometric trait.
- They introduce zero friction, since all a user has to do is touch or look at their device to be verified.
- They fit neatly into any part of your auth flow, since they don’t require users to navigate away from your platform or app.
As cross-platform biometrics become increasingly available, our prediction is they will quickly become the gold standard for easy, high-converting authentication.
How will you go passwordless?
There are many creative ways you can add passwordless solutions to your app’s current authentication flow — and we love sharing them. Stay tuned for more content that covers the second half of the adoption curve and demonstrates how you can easily make the switch to fully passwordless auth.
To learn more about the ins and outs of passwordless auth — and find the method that’s right for you — join Stytch’s Slack channel or sign up to get started!
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.