Back to blog
AI agent authentication methods
Auth & identity
Nov 10, 2025
Author: Stytch Team
As AI agents move from POC to production and start interacting with real data, most systems have converged on OAuth for securely delegating access to those agents. Rather than handing an agent a raw API key, they've come to rely on standard OAuth flows so users can explicitly authorize the agent to act on their behalf. Whether that agent is accessing calendar data or initiating financial operations, OAuth provides a standard and highly-secure way to issue scoped, revocable tokens. You see this pattern emerging everywhere: from SaaS integrations to native LLM-based apps built on tools like the OpenAI Apps SDK, to integration standards for AI-powered tools like the Model Context Protocol (MCP).
This guide explains the different AI agent authentication methods available (including M2M scenarios) and how OAuth became the industry standard for securing AI agents.
Why did OAuth win?
The convergence on OAuth wasn’t planned, but it was, in fact, inevitable.
In the early days of AI integrations, developers tried everything: static API keys, custom-generated tokens, and other ad hoc methods. These approaches worked well enough for simple service accounts (machine-to-machine tasks, that is), but they failed to provide a secure, scalable, or auditable way to handle delegated access.
As soon as platforms started exposing AI agents as first-class integrations, they all ran into the same problem: letting an agent access user data in third-party apps the platform doesn’t own. The consistent answer has been OAuth, where agents authenticate as OAuth clients, obtain scoped tokens, and call APIs on the user’s behalf. This pattern is now common across SaaS ecosystems, app marketplaces, and AI-native frameworks.
What’s interesting is that OAuth was originally designed around human users in a browser, redirecting them to a consent screen and then issuing tokens. But the underlying model was always more general: a “client” acting on behalf of a “resource owner,” with an authorization server mediating trust. That abstraction maps perfectly onto AI agents. The user still goes through a familiar consent flow, but now the “client” is an agent (or its host), and the tokens it receives represent delegated authority for that agent to act.
Even MCP, the open standard for agent-tool communication, didn’t reinvent a method; it built OAuth 2.0 (& more recently OAuth 2.1) directly into its foundation for authentication, which reinforced that OAuth is still the most relevant approach, even as it extends to authorization for non-humans.
But why? OAuth 2.0 solves the four critical requirements for delegated agent access that other methods failed to solve.
- User consent flow: OAuth has a built-in, standardized way to ask the user for permission (e.g., “Do you allow AI Assistant to read your Gmail?”). The user explicitly authorizes the agent.
- User-scoped tokens: The agent receives a token that is tied specifically to the user who gave consent. It inherits that user’s permissions, and no more.
- Instant revocation: The user (or their organization’s administrator) can go to their “Connected Apps” settings at any time and click “Disconnect.” This immediately invalidates the agent’s token, cutting off its access.
- Delegation audit trail: It creates a clear audit trail. Instead of a log that just says “An API key was used,” you get a log that says, “Agent X, acting on behalf of User Y, deleted file Z.”
Its latest draft, OAuth 2.1, further supports the above by merging more security best practices. It makes modern defenses like PKCE (Proof Key for Code Exchange) mandatory and removes older, insecure flows, making it a perfect fit for agentic patterns.
In short, OAuth 2.0 solves the practical problems:
- It handles both use cases: Delegated access (with the Authorization Code flow) and M2M service accounts (with the Client Credentials flow).
- It’s interoperable: The flow is the same whether an agent is connecting to Google, Microsoft, or your own app!
- Tokens are short-lived: Unlike static API keys that can live for years, OAuth 2.0 access tokens often expire in an hour, dramatically reducing the window for an attacker if one is leaked.
- It has built-in rotation and revocation: Refresh tokens allow agents to get new access tokens without the user having to log in again, and users or admins can immediately revoke these tokens whenever they need to.
- It enables granular scopes: You can give an agent permission to
read_calendarbut notdelete_calendar.
Understanding the two AI agent authentication scenarios
Before talking about the different AI agent authentication methods, it’s important to clarify the two distinct scenarios you’ll run into:
1. Delegated access | 2. Service accounts | |
|---|---|---|
Description | ||
Description | An agent acts on behalf of a specific user. | An agent authenticates as itself for system-level tasks. |
Example | ||
Example | An AI assistant accessing your personal Google Calendar to schedule a meeting. | A background job that processes and anonymizes all customer data every night. |
Requires | ||
Requires | User consent and authorization. | No user-specific context or consent. |
Actions are attributed to… | ||
Actions are attributed to… | The user who delegated access. | The service or system itself. |
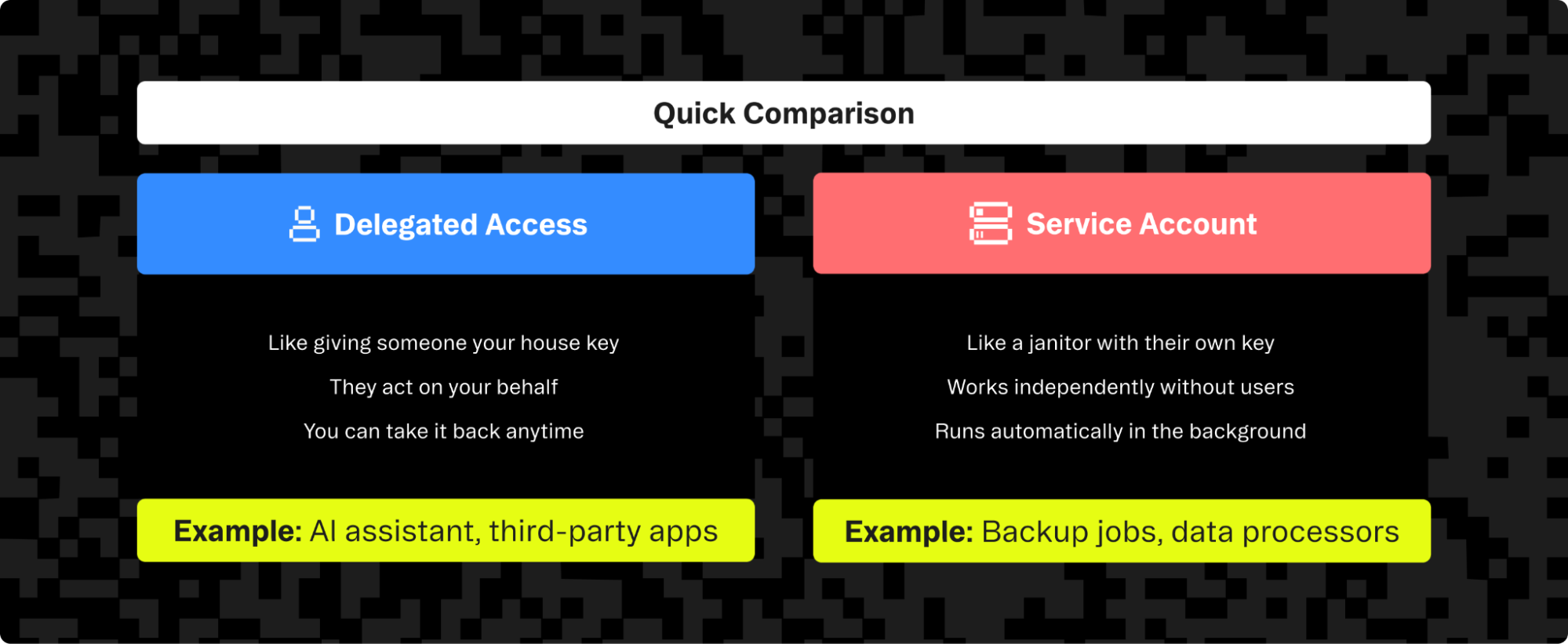
In both cases, OAuth has become the most robust and secure option.
AI agent authentication methods explained
If you need to grant agents access to user data — delegated or not — there is a high chance you will be using OAuth as the most practical protocol. Every major platform requires it because it’s the only standard that handles consent and user-specific permissions.
Key OAuth flows for agents
Below are the two primary OAuth flows used by AI agents.
Authorization Code Flow + PKCE
This is the flow for user-delegated access. The user is redirected to a login and consent screen. After they approve, the agent receives an authorization code, which it securely exchanges for an access token. PKCE is a security extension (and mandatory in OAuth 2.1) that prevents a specific type of interception attack.
Client Credentials Grant
This is the flow for service accounts (M2M). The agent authenticates using its own client_id and client_secret to get a token that is not tied to any user. It’s a direct, machine-to-machine request. This is the modern, secure replacement for static API keys. You can learn more about implementing this flow with Stytch’s M2M auth guide.
When you actually need it | Works for delegated access? | The catch | |
|---|---|---|---|
Authorization Code + PKCE | |||
Authorization Code + PKCE | Delegated access, where the agent acts on behalf of a user | Yes | Initial setup complexity requires user consent flow |
Client Credentials Grant | |||
Client Credentials Grant | Service accounts where the agent acts as itself (M2M) | No | Only for non-user-specific operations |
API keys | |||
API keys | Never — use Client Credentials Grant instead, as it’s more secure | No | No rotation, no revocation, easily leaked, no audit trail |
Advanced OAuth extensions for AI agents
As you build more complex systems, you may also encounter these OAuth extensions.
- On-Behalf-Of (OBO) token exchange: The gold standard for chained delegation. This allows an agent (acting for a user) to interact with back-end services that sit several layers deep, behind other services’ APIs, all while securely maintaining the original user’s identity and permissions. (Note: Microsoft’s Azure AD has a proprietary OBO implementation that differs from the IETF RFC 8693 standard.)
- Rich Authorization Requests (RAR): Allows for extremely fine-grained permissions. Instead of a broad scope like
purchase_flights, which would allow an agent to book unlimited flights, an agent can be given a more limited permission, for example, to “purchase one flight from SFO to JFK, today, with a spending limit of $500.” - Client-Initiated Backchannel Authentication (CIBA): An auth flow without browser redirects, often used for “decoupled” authentication (e.g., getting a push notification on your phone to approve a login).
- Dynamic Client Registration (DCR): This automates the setup process. Instead of a developer manually registering an agent with a service (like Google) to get a
client_id, DCR allows the agent to programmatically register itself. This is highly beneficial for a future where autonomous agents might discover and need to connect to new services on the fly. - Client ID Metadata Documents (CIMD): A draft IETF OAuth extension where clients use an HTTPS URL as their
client_id. This URL points to a JSON metadata document that authorization servers can fetch on demand, meaning you no longer have to maintain per-client registrations (manually or via DCR). CIMD is now being adopted in MCP so MCP clients and servers can discover each other dynamically and connect securely.
What to avoid in AI agent authentication
Many teams are tempted to take shortcuts, especially for prototypes, which is understandable, considering the time and the cost. But these shortcuts almost always lead to massive security risks when real data is involved.
API keys
Always avoid these when working with AI agents, even for prototyping. It’s tempting, given that you only need minutes to set up an API key in contrast to deploying an OAuth flow. However, they’re easily leaked in shared code notebooks or forgotten config files and are almost always connected to live data, even at the prototyping stage. They also can’t help you if you need delegated access, as they have no concept of users, consent, granular scopes, or revocation (beyond deleting an API key entirely).
Passwords
Just don’t. Your agent can’t receive a 2FA code, and using app-specific passwords is just a less secure version of an API key. Using a user’s real password for an agent breaks every security model and likely violates your terms of service. Worse, it also exposes credentials to catastrophic risk. If the agent service is breached, all your users’ passwords are stolen. If the agent’s prompts are logged, your password could inadvertently or deliberately be used as training data, permanently embedding it in a model.
Session cookies
These are designed for browser-based authentication, not programmatic API access by an agent. They don’t provide a consent flow, scoping, or audit trail needed for proper delegation.
Magic links
What email address would your agent use? Magic links are designed for human users who can check their inbox and click a link. An autonomous agent can’t monitor an email account or interact with a browser in the same way. Even if you tried to automate email checking, you’d be building a fragile, insecure workaround that completely defeats the purpose of proper authentication. Magic links also lack the scoping and delegation semantics that OAuth provides.
Embedding credentials in code or prompts
Never store passwords or tokens in code or configuration files, or even worse, in a prompt. This is a critical vulnerability that exposes your systems to attackers.
Making the right choice
The decision is simple.
You should use OAuth for:
- Any delegated access to external systems
- Any scenario where an agent acts on behalf of a user
- Any time production or sensitive data is being touched
- All MCP implementations
- Multi-tenant systems
- Any situation requiring explicit user consent and permission scoping
In short, for any real-world application of AI agents, use OAuth 2.0. It’s specifically built to handle the critical security, consent, and delegation requirements of modern AI systems.
The practical path: OAuth with Stytch
While OAuth is the clear standard within the different AI agent authentication methods, implementing it correctly is notoriously difficult. Your application must become a fully compliant OAuth 2.0 authorization server, which inevitably means building and maintaining a lot of aspects and workflows — token life-cycle management, consent screens, secure storage, scope and permission models, audit logging, compliance certifications (like ISO27001, SOC2, GDPR, and HIPAA), and an MCP authentication and authorization server if you’re supporting MCP.
This is a massive engineering effort that distracts from your core product.
Stytch abstracts all this complexity. Our Connected Apps product is an all-in-one suite for agent-specific workflows, handling everything from consent screens and token management to instant revocation and audit logs.
This means that you get a future-proof, compliant, and secure auth system in days, not months.
Interested in building secure agentic integrations without rebuilding your auth layer from scratch?
Contact us for a demo or sign up.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.